this week in security — february 9 2025 edition
THIS WEEK, TL;DR
Elon Musk's takeover of the U.S. government exposes millions of people's data
Wired ($): We start this week with a five-alarm fire across Washington DC as Elon Musk and his band of teenagers lackeys are well and truly in government, literally, plugging into sensitive systems across the U.S. federal government despite their highly questionable clearances. It's hard to keep up with the pace at which Musk's so-called DOGE took control of Treasury payments systems that disburse $6 trillion in federal payments and obtained access to HR records of federal workers at the OPM, in what is essentially the biggest compromise of U.S. government data in, well, ever. (For the "well, actually" crowd, their clearance is temporary but vast, and their vetting nonexistent; it's still a breach.) A federal judge blocked DOGE from its access following a multi-state led lawsuit, but way too late and the damage is already done. Wired's reporting has been incredible as new details about how Musk — the world's richest man — is taking over government to cut spending and headcount seemingly at any cost and regardless of fallout or consequence. Well, yet — all in good time.
More: The Atlantic ($) | Techdirt | TechCrunch | Associated Press | Cyberscoop | NPR | Krebs On Security

U.S. intelligence, cyber agency staffers offered deferred resignations
NPR: As part of the ongoing efforts by Musk to shrink the U.S. government, federal workers at U.S. intelligence and cyber agencies — including NSA, CIA and CISA — have all been offered deferred resignations and retirements, leading to concerns about U.S. cyber defenses... yeah, not great! Federal national security workers were largely exempt from the OPM's offer to let federal employees leave the workforce, but that seems to be changing. This is the same week that the new CIA director John Ratcliffe sent an unclassified email containing partial CIA employee names to the White House — which left former officials aghast at the security lapse. Will the last federal worker turn the lights and, for the sake of the federal enterprise, also power down the routers?
More: The New York Times ($) | NPR | The Record
Italy says dozens of EU citizens targeted with Paragon's spyware
TechCrunch: Let's switch gears to something a little ligh...oh come on! ...OK, here we go: it's nation state spyware time. It looks like Italy is in hot water after several people — all of whom are in some way critics or under the watch of the Italian government — were identified as having been targeted by the Israeli spyware Paragon. WhatsApp disclosed the campaign last week, revealing that Paragon's spyware (known as Graphite) was used to target around 90 people, including journalists. Paragon later cut off Italy from its spyware after the Italian government said it absolutely wasn't them who did the spying and instead alluded to the dozen or so other countries whose citizens were spied on, including Austria, Denmark, Germany, Greece and Spain, essentially pointing the blame at one of them (some of which are known customers of spyware makers). Who was it? Who knows — but we do know that Paragon confirmed this week the U.S. government is a customer. We'll see what comes of this; all eyes are on Paragon.
More: Reuters ($) | Haaretz ($) | The Guardian | Euractiv | BBC News | @sophieintveld
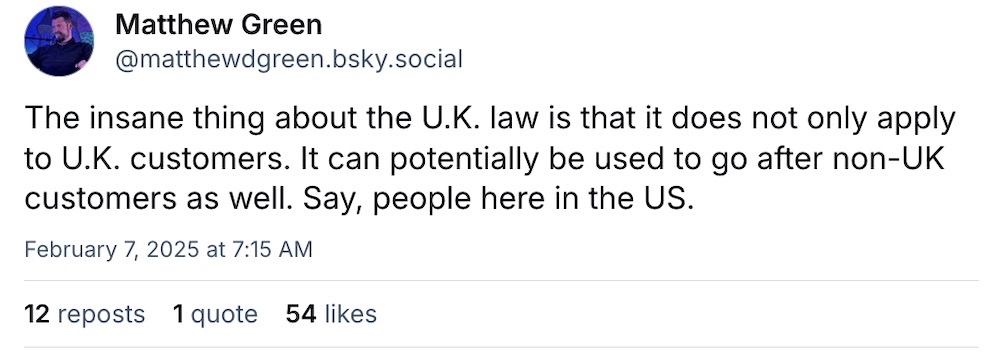
U.K. orders Apple to let it spy on users’ encrypted accounts
Washington Post ($): Sorry... but it looks like we're dusting off another iteration of Crypto Wars, this time, it's the British Edition. (I'm taking this one personally.) Last year, the U.K. government essentially secretly ordered Apple — by way of its Snoopers' Charter surveillance law — to grant U.K. authorities access to protected cloud backups around the world — regardless of which country they're in — setting a really, really dangerous precedent. It's not likely that Apple will allow access (since Apple's cloud backups are encrypted and only the user can unlock them) and would more than likely stop offering the service in the country, known as Advanced Data Protection. This is really not a good look from the (relatively new) U.K. government — the Labour Party has been hellbent on surveillance for years and clearly this is no different. And now China or any other authoritarian country can demand the same access by saying, "well, the U.K. did it — why can't we?"
More: @matthewdgreen posts | @mattburgess1 | The Register
~ ~
THE STUFF YOU MIGHT'VE MISSED
Meet the hired guns who make sure school cyberattacks stay hidden
The 74: A really deep dive story into the strategies — think, lawyers and crisis comms PR — that schools and districts use to hide cyberattacks that expose the personal information of students, parents and teachers. @mkeierleber also goes behind the scenes with how he investigated the story. Remember: the goal should be transparency, not "CYA." Plus, incredibly, bonus cybercat, and sprinkling of additional context from @douglevin.
Law enforcement hammered cybercrime in 2024, with ransom payments down
Intel471: New data and analyses this week shows how the cybercrime industry was hit by several law enforcement actions over the past year, including LockBit's takedown, arrests in the Com (aka where cybercrime meets physical violence), and several other cybercrime forums, hobbling the biggest criminal operators of recent years. Plus, per Chainalysis, data shows that while more victims were targeted by ransomware, fewer corporate victims actually paid (though some did, like Cencora's $75 million to hackers). On the government side, Bloomberg ($) reports that DHS' cyber cops stopped at least 500 ransomware attacks last year.
Android bugs fixed, including an actively exploited flaw
Cyberscoop: Google has fixed dozens of flaws in Android, including CVE-2024-53104, which Google says is under active exploitation. Specific details weren't given about how, exactly, but Google said the bug could result in a "physical" escalation of privilege. Based on that, it's likely the bug was used by a law enforcement-capable mobile forensics device, such as Cellebrite or the like, which can unlock some phones protected by a passcode.
~ ~
OTHER NEWSY NUGGETS
GrubHub delivers fresh hot data breach: U.S. food delivery giant Grubhub said hackers accessed the personal data of its customers and drivers after breaching internal systems, which it traced to one of its third-party vendors. No word on the number of affected individuals, although the data includes names, email addresses, phone numbers, and last four digits of the card number. (via TechCrunch)
Former Polish justice minister nabbed: Polish police arrested the country's former justice minister, alleging he allowed government funds to pay for spyware that was used to snoop on the country's then-opposition leaders, per local news. Poland's new-ish left-leaning government has been cleaning up from its past administration. See? Sometimes there can be consequences for bad actions. (via The Record)
Zyxel says replace routers hit by zero-days: In extremely bad form, router maker Zyxel told customers that they should replace routers affected by two zero-day bugs under active exploitation because the company says the affected devices are end-of-life. But... Zyxel appears to be selling affected models through Amazon, and there's no mention of the allegedly ended product on its end-of-life pages. Censys says there are 1,500 vulnerable devices on the internet (at least). Let's hope none of them are being actively ensnared by a Mirai botnet.. (via GreyNoise, Zyxel)
HPE alerts victims of Russian cyberattack: Hewlett Packard Enterprise alerted victims of its Russian government hack (back in 2023) that allowed the hackers access to mailbox data and other internal company data. Microsoft, whose cloud hosted HPE's mailbox data, was hacked at around the same time. (Disclosure: I wrote this story!) (via TechCrunch, DocumentCloud)
PowerSchool hack affects thousands of U.K. kids: The PowerSchool hack goes international. As North Carolina's attorney general investigates PowerSchool's massive breach, the school tech company confirmed that at least 16,000 school kids in the U.K. had their personal data stolen. That's on top of the likely millions of kids across North America who had their personal data stolen, too. PowerSchool still won't provide a number of affected folks — in what is likely one of the biggest breaches of school data of the year, despite the company continuing to say very little. (via TechCrunch)
~ ~
~ ~
THE HAPPY CORNER
And not a moment too soon... here's this week's happy corner. Let's see how Hello Kitty is doing; if anyone's a barometer for the state of the world, it's h... oh no.

Definitely a mood.
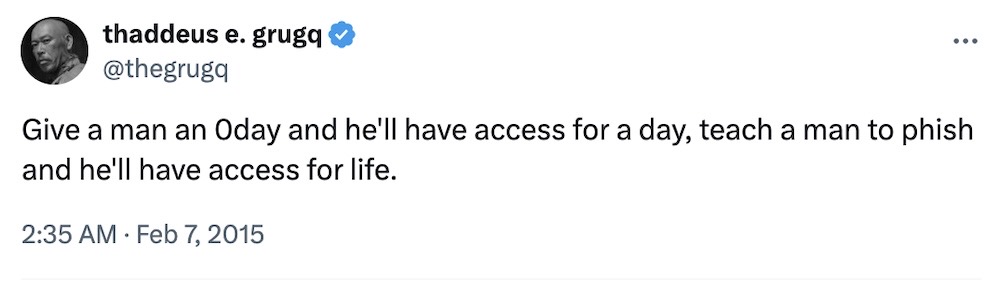
Incredibly, it's been ten years since this incredible tweet by @thegrugq. Nowadays we have phishing, smishing, quishing, vishing... or, as some call it... still phishing.
There is some actual good news... What Will Doom Run On? is back! Turns out you can run Doom on an Apple Lightning to HDMI adapter... because of course you can, thanks to its embedded Samsung-made chip. Very impressive. (Video at source.)
The world may be on fire, but one thing we can all do is lend our support to those who need it, especially the kids out there (since the adults have absolutely wrecked the place). With that, it's Girl Scout Cookie Season, and there are so many troops out there to support. If you can, buy from your local community troop! Erin Reed also has her annual list of trans Girl Scouts troops to buy from and meet their goals, as well as Troop 6000, New York's dedicated troop for kids in the shelter system. (He writes, while submitting a new online order for another metric ton of cookies...)
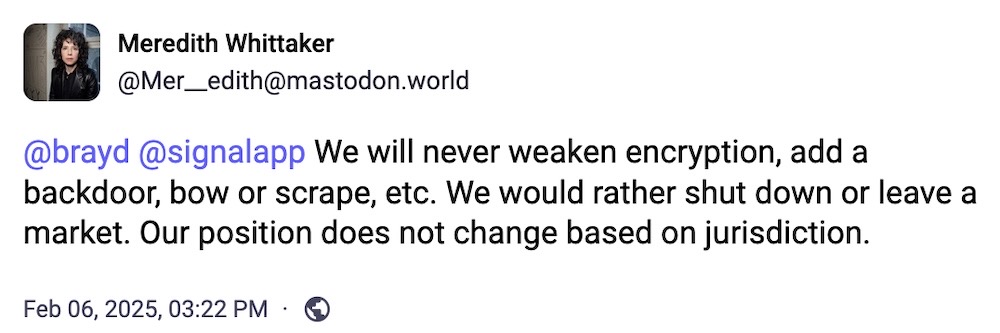
And finally, this week. Shout out to Signal's president Meredith Whittaker (no relation), for this reminder. In times like these, Signal is more important than ever — and remember to donate to help it help us!
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber-cat friend is Maple, whose human tells me that she is very cat-like but unfortunately doesn't like cats because she was once bullied by some bodega cats. Aww, Maple! Bodega cats can be super territorial but also very friendly when they get to know you! A+ rain boot game. Many thanks to Gabby R. for sending in!

Keep sending in your cyber cats! (or a non-feline friend). Drop me an email at any time with their name and a photo, and they'll be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
On that much needed lighter note — (honestly, a real highlight of my week) — I bid you good health and good day. Have a wonderful Sunday and week, and catch you next. Feel free to drop me an email with anything for the newsletter, including any good news you see, your cyber cats, and anything else you want to share.
Signing off from a snowy east coast,
@zackwhittaker