this week in security — january 1 edition
THIS WEEK, TL;DR
The worst hacks of 2022
Wired ($): Happy new year! Prrrffhhtt! 🥳 We can't look back at the year (or ahead) without looking at the worst, most disastrous hacks and attacks of the year, and Wired has you covered (including some you may have forgotten). It's impossible to ignore the biggest, perhaps worst of all — LastPass, which confirmed customer password vaults were compromised likely weeks earlier in its second data breach this year but only told customers of the breach days before Christmas. LastPass lost control of its customers' encrypted password vaults, which are now only as strong as the customer's master password (which may mean few protections for offline attacks). If ever there's been a good time to move to a different password manager, it's now — especially if you're still off for the next day or two. (And no matter how burned you might feel as a LastPass customer, password managers are still better than not using one at all.)
More: Ars Technica | The Verge | @astuyve | @epixoip | @kennwhite
Military hardware and fingerprints database for sale on eBay
The New York Times ($): Probably not the thing you'd want to end up on an online auction site for less than €200 — the fingerprints and iris scans of 2,632 people, including U.S. service personnel. But that's what happened when German security researchers bought a cache of military biometric capture equipment, last used in the summer of 2012 near Kandahar, but was never wiped. A decade on, and those service personnel still have the same eyeballs and fingerprints. This is precisely what folks were concerned about with the U.S. evacuation of Afghanistan last year, since the Taliban could use these U.S. devices to track down Afghans who worked with Allied troops (though in this case there was no Afghan data). Germany's BR also has a great interactive story on the devices.
More: Bayerische Rundfunk | Chaos Computer Club | @kashhill

Police seize on COVID-19 tech to expand global surveillance
Associated Press: Fantastic reporting by the AP looking at how COVID-19 surveillance and tracking technologies have been used for police investigations around the world — in some cases violating promises that they wouldn't be. The reporters found examples of phone tracking in Jerusalem, facial recognition in India, and mass surveillance in China — where we've seen a recent relaxation of COVID restrictions following weeks of protests and civil unrest — but also more liberal democracies like Australia, where spies down under were caught "incidentally" collecting data from the national COVID-19 contact tracing app. COVID created the perfect conditions for governments to spy, but is this level of surveillance the new normal?
More: @fbajak | @jsrailton tweets
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
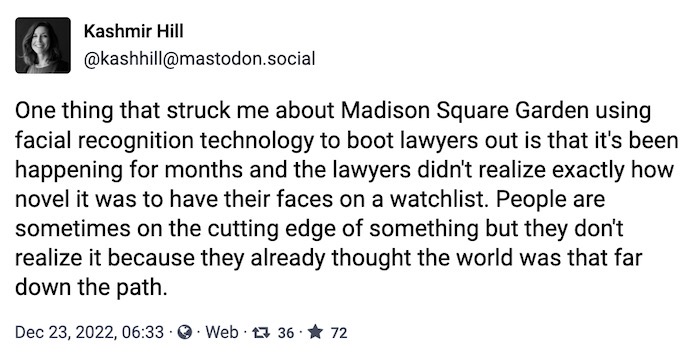
Facial recognition boots lawyer from MSG due to her workplace
NBC New York: A lawyer was kicked out of Radio City in New York, a Madison Square Garden-owned venue, when facial recognition installed at the venue spotted her, and flagged her as an attorney at a law firm involved in legal action against the venue's parent company. The attorney, who isn't involved in any cases related to MSG and doesn't practice law in New York, said the venue "knew my name before I told them." MSG admitted it used facial recognition and cited a policy that "precludes attorneys pursuing active litigation against the company from attending events at our venues until that litigation has been resolved." (Yes, the lawyers were on a facial recognition watchlist for months using photos from the law firm's website.) Now the attorney is fighting back by going after the company's liquor license. That's one way to get even.
Huge payout for Google Home eavesdropping bug
DownrightNifty: A security researcher netted $107,500 from Google after discovering a bug in the Google Home Mini, a smart speaker with a microphone and internet access. The bug allowed anyone within close proximity to plant a backdoor account, and then later issue commands remotely over the internet, including tapping into the device's microphone — a major privacy risk if in someone's home or office. (Proof-of-concept code available on GitHub for testing devices running older firmware.) Google fixed the bugs in April 2021, a few weeks after details of the bug were submitted. A really great write-up here, plus a tl;dr from Bleeping Computer.
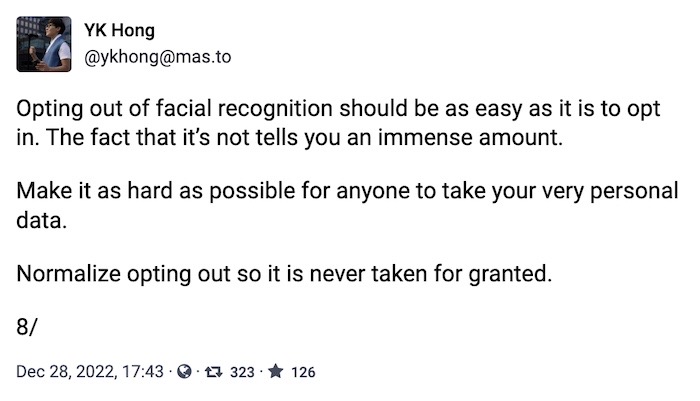
Opting-out of face scanning at U.S. airports
YK Hong: @ykhong has a good toot-thread on how to (and what it's like to) opt-out of facial recognition at airports. Face scanning was rolled out a few years ago under the guise of speeding up airplane boarding. But while many shuffle through without a second thought, it's possible to opt-out for Americans and permanent residents for those who don't want their face scans stored for years and prefer a manual passport check (you know, like how it was done for years!). Follow along with the thread for more. While it's an American's right to opt-out of airport face scanning, everyone's threat model is different, and doing so will require many to weigh up other associated risks, such as harassment from border officials or other threats to your data.
~ ~
OTHER NEWSY NUGGETS
$1.7 trillion and all I got was this lousy t-shirt: Admittedly, the federal government is getting a touch more than just a t-shirt as part of the $1.7 trillion spending bill passed by Congress this week... but not by much. CISA gets a 12% rise in its budget to counter cyber threats, and $1.7 billion is allocated for cybersecurity efforts, including the protection of civilian federal networks and also state and local governments. In addition, @jackhcable reports that Congress included a provision to study memory safety in the government, since so many exploited software vulnerabilities these days are memory-related bugs. Speaking of, if you didn't catch @lhn's piece on Rust, the memory-safe language taking over tech, this is a fantastic read. (via The Record)
Ring ring, hello? It's ransomware: Telecoms giant Intrado, which provides telephony for the bulk of the Fortune 500 and a ton of 911 call centers, reported an "incident" that now looks like ransomware. The Royal ransomware group has claimed responsibility and has published a cache of internal documents, including employee passports and driver's licenses. (via Bleeping Computer)
Arrested, seized, and doxed, but not forgotten: My TechCrunch colleague @carlypage and I looked back at the year in cybercrime, including high-profile arrests, doxes, site seizures, and convictions: featuring a popcorn can worth billions of dollars and the aftermath of stealing 100 million CapitalOne customer records. (Disclosure: I contributed this story.) (via TechCrunch)
Japan police secretly unlocking LockBit? Japanese media report (日本) that the country's national police agency has unscrambled over a hundred LockBit-encrypted networks this year. The police confirmed its ability in a statement but are "refraining" from specific details. LockBit is one of the most prolific ransomware groups, and recently blamed for the Australian Medibank breach, Foxconn, and Accenture. (via @campuscodi)
~ ~
THE HAPPY CORNER
Happy new year to all those who celebrate. It's 2023, and this is the happy corner.
A very different kind of "break glass" in emergency. (via Imgur)

And many congratulations to @rondeibert, director of Citizen Lab, the University of Toronto unit that investigates digital and nation-state badness, was awarded the Order of Canada this week. Citizen Lab does great work investigating spyware, censorship, and espionage.
If you have good news you want to share, get in touch at: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
Meet this week's cyber cat dogs: Emily (top) and Bailey (her dad, below). It's not often we get a father-daughter cyber duo here, let alone in the middle of a back-seat hacking spree. Many thanks to Rose B. for sending in!

Please send in your cyber cats (or their friends). Email me a photo and their name, and they'll be featured in an upcoming newsletter. Submitted before? Send an update!
~ ~
SUGGESTION BOX
It's good to be back! And I'll be back next Sunday with another edition as well. In the meantime, the suggestion box is open for feedback or feel free to drop me an email.
Hope you had a great holiday. Let's hope this year is a little easier...
See you next week,
—@zackwhittaker