this week in security — january 14 edition
THIS WEEK, TL;DR
X-Mode banned from selling phone location data, FTC orders data deleted
Federal Trade Commission: In a first of its kind settlement, data broker X-Mode (now known as Outlogic) is banned from selling or sharing sensitive location data with others. The FTC alleged X-Mode "failed to put in place reasonable and appropriate safeguards on the use of such information by third parties." X-Mode was caught collecting and sharing location data from Muslim prayer apps, for example, with U.S. military contractors. But the data collection was far broader: the data could be used to "track people’s visits to sensitive locations such as medical and reproductive health clinics, places of religious worship and domestic abuse shelters," the FTC said. Apple and Google banned X-Mode in its early days, yet this company pretty much blew up the wider data broker scene (and the exposure of it). Seems like the FTC is on a bit of a roll at the moment... now do stalkerware!
More: Politico | The Markup | TechCrunch | @kashhill | @BedoyaFTC
AI helps U.S. spies catch stealthy Chinese hacking ops, says NSA official
Cyberscoop: This week feds descended on Fordham University for the annual ICCS conference (where yours truly was in attendance — as media, obviously). Top of the agenda was NSA director of cybersecurity Rob Joyce chatting about how threat actors are using AI to improve their operations but also how NSA was using AI to catch them. “Machine learning, AI and big data help us surface those activities," Joyce said, noting that the models are better at detecting anomalous behavior of supposedly legitimate users (think session hijacks). Joyce spoke about recent activity linked to Chinese-linked operations aimed at U.S. critical infrastructure — likely in preparation of an expected eventual Chinese invasion of Taiwan — in efforts to "cause societal disruption and panic at a time and place of their choosing." Shoutout to Joyce, who was also at Shmoo this weekend (a very different con to Fordham).
More: NBC News | TechCrunch | @FordhamNYC
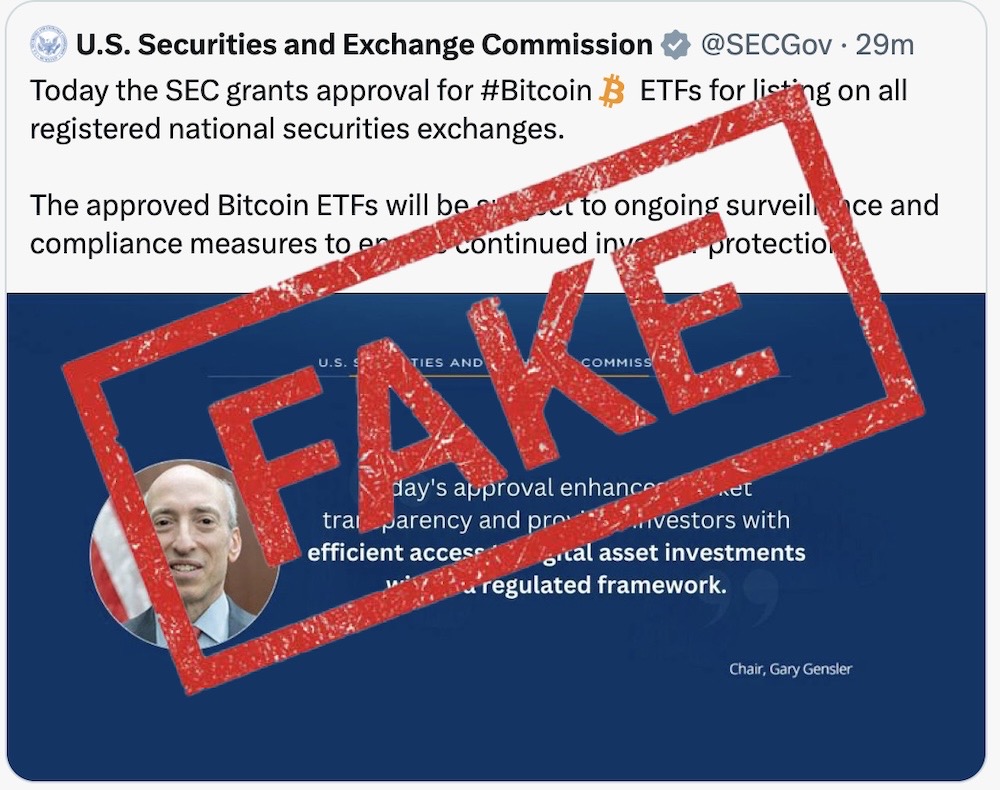
SEC's X account was hacked to post false bitcoin ETF announcement
Wired ($): OK, so let's talk about that hack — of course, the SEC's X account, which was briefly hijacked — supposably by outside hackers — to post a false announcement about news that the SEC announced only a day later. X, the artist site formerly known as Twitter, blamed the SEC for not using 2FA — which the SEC didn't deny, but might not have mattered given the X account was hijacked by way of a SIM swap. Confused? It is a messy one, but Wired has you covered. This matters because the SEC should have done a better job at securing its X account (take some of @RachelTobac's advice) since it's a federal regulator and what it says matters! But also clearly SIM swapping is a major problem and seemingly getting worse — yes, the cell networks are crap at this — so read this PSA by @SwiftOnSecurity, too.
More: Washington Post ($) | Wired ($) | CNN | Axios | CNBC | @zackwhittaker
Mandiant's X account hack linked to drainer campaigns
Mandiant: Speaking of hacked X accounts... Mandiant handled its scandal — for the most part — by posting its receipts on the very campaign that recently hacked the company's social media account. If you recall, Mandiant's X account was briefly hijacked and wrestled back. Mandiant said following its investigation that its X account password was likely brute-forced (read: weak) but also: "Normally, 2FA would have mitigated this, but due to some team transitions and a change in X’s 2FA policy, we were not adequately protected." Which seems to suggest Google's acquisition of Mandiant last year may have resulted in some "team transitions" (diplomatically stated) but the company also laid some of the blame with X, likely for its stupid decision to remove SMS 2FA from non-paying accounts last year. In any case, Mandiant dropped a highly detailed report on the wider campaign targeting cryptocurrency owners is worth the read.
More: Bleeping Computer | BankInfoSecurity | SecurityWeek
~ ~
THE STUFF YOU MIGHT'VE MISSED
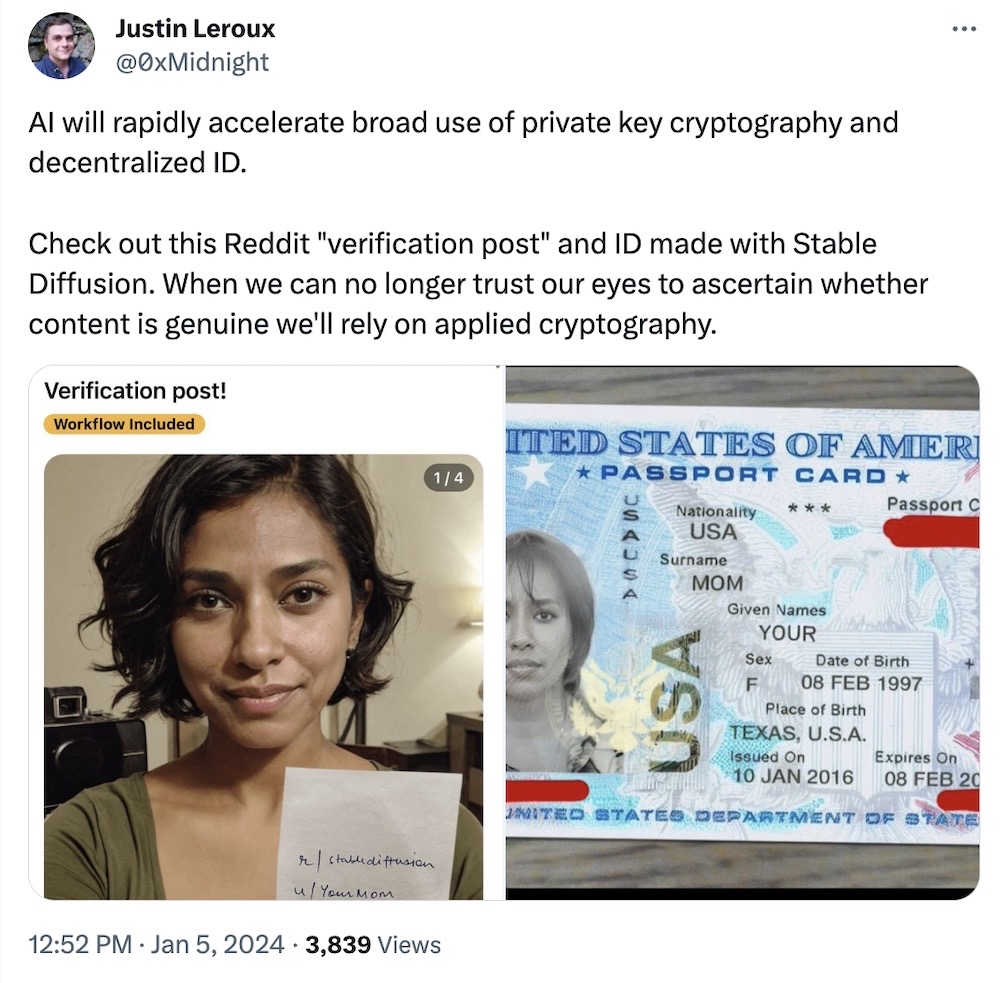
GenAI could make KYC effectively useless
TechCrunch: Generative AI — think computer-generated images — are getting scarily good, so much that it's only a matter of time before it's capable of fooling know-your-customer (KYC) checks. Those selfies you take with your passport to verify it's you can now be generated on the fly using generative AI tools like Stable Diffusion. I had some thoughts on this in a toot thread as it pertains to bad actors.
How CERT.PL scans Polish webspace for flaws using Artemis
CERT.PL: Here's a good blog by Poland's computer emergency response team on how it uses Artemis, an open-source security vulnerability scanner it developed to "look for website misconfigurations and vulnerabilities on a large number of sites." This is how CERT.PL alerts website owners to flaws that they can fix. Plenty of other countries also do this but it's good to see it posted publicly!
How the Post Office wrecked the lives of its own workers
Private Eye: It's hard to capture more than a decade's worth of reporting in a snapshot but... you might have heard recently about the U.K. Post Office scandal. It was a huge IT screw-up-then-cover-up that resulted in the U.K. Post Office wrongly prosecuting hundreds of its own subpostmasters (yes, it can do that because U.K. law is weird) claiming they stole money — when it was actually bugs in the machines all along. Probably the biggest mass-miscarriage of justice in British history. To get caught up if you haven't already, read Private Eye's special report as a free PDF (the layout is good for printing). It's well worth the read, and kudos to Private Eye for following this story from the very beginning.
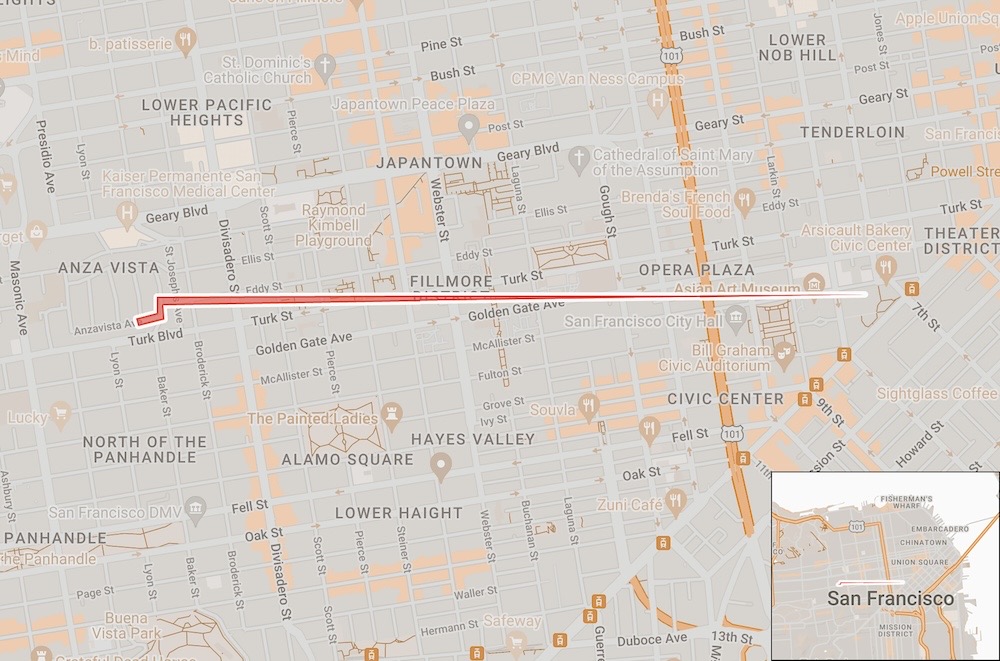
A geofence warrant typo cast a two-mile location dragnet over San Francisco
ACLU NorCal: Attorneys with the ACLU NorCal scoured years' worth of geofence warrants at San Francisco Criminal Court (in person!) — even by their count still "only a fraction of the geofence warrants used in San Francisco" — and their results are fascinating. One geofence error allowed police to return information on anyone who entered a near-two mile stretch across San Francisco, and another geofence warrant included four places of worship in a single city block. Google recently changed its policies on where its stores location data, but plenty of other companies are still susceptible to geofence warrant demands.
Hackers break into AI hiring chatbot
404 Media ($): Filed under dystopian a.f.: A group of hackers accessed the backend of an AI chatbot used by fast food giants to automate hiring and found the system able to deny applicants based on certain criteria. More from MrBruh on the specific flaw in question, and Eva on the data found within.
~ ~

~ ~
OTHER NEWSY NUGGETS
Supreme Court rejects X transparency bid: The top U.S. court will not hear a case (effectively ending it) brought by Twitter (at the time, now X) on whether it can publicly disclose how often feds seek information about its users on national security grounds. The lawsuit was filed post-Snowden back in 2014 in an effort to allow companies to disclose the specific number of national security requests it received in a certain period, rather than the broad numerical bands. The case was denied at the appeals level, and subsequently denied on that appeal. (via Reuters ($))
LoanDepot hack likely ransomware: Bad news for customers of yet another mortgage and loan company, this time LoanDepot says it was hacked and that resulted in "the encryption of data," which sounds a lot like ransomware. Almost a week in and little more than a peep out of LoanDepot's cyber status update. Hackers recently stole data on 14 million Mr. Cooper customers, First American was also hit by a hack, as was Fidelity National Financial in recent weeks. (via Bleeping Computer)
AirDrop leaks like a sieve, and China is scooping data up: News broke this week that Chinese authorities are exploiting a weakness in Apple's wireless sharing feature AirDrop, which can uncover the identity of AirDrop users. The bug has been known about for some time, per CNN. Cryptographer prof. Matthew Green dug into the anatomy of the AirDrop tracing attack (via CNN, @patrickwardle)
Internet of Insecure Wrenches, apparently: These days, it feels like if something has an Internet connection, it's a ransomware risk. Case in point: Researchers have found close to two-dozen vulnerabilities that can be used "to sabotage or disable" a popular line of network-connected wrenches that factories use to assemble sensitive instruments and devices." Worse, these bugs can be exploited by an unauthenticated attacker. (via Ars Technica)
New Ivanti (Pulse) Connect VPN zero-days: Not that you need another headache but Ivanti has mitigation advice for two zero-days under active exploitation in its Ivanti Connect VPN appliance (formerly Pulse Secure). Volexity says it's a China-backed hacking group behind the attacks (and Mandiant hints at it). There is a PoC as of Sunday, but no patches until later in January. Follow @GossiTheDog's thread on this for more. (via TechCrunch, CISA)
~ ~
THE HAPPY CORNER
At last, the happy corner, a small oasis on the internet with nothing but good stuff.
The Freedom of the Press Foundation does vital work for reporters. Now it's back with the results of stress-testing hardware security keys to see which will still work after a series of brutal real-world tests. Those tests include running them through a washing machine, running them over with a car, and seeing which falls foul of gravity the most. If you're a heavy duty user, you'll need to know which keys lasted!

A quick nostalgia throwback to the '90s when every Windows installer looked like this (including malware, if you were lucky).

Meet the world's best robot: the one that switches itself off.
And finally this week. This is probably the best Shmoocon swag so far (but haven't managed to snag myself one just yet).

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Shadow (aka Black Hat Black Cat). According to her human, Shadow loves nothing more than to hack the box — so long as it's cardboard. Many thanks to @CryptoSecEd for sending in!

Keep sending in your cyber cats! Email me a photo of your cyber cat (or non-feline friend) with their name they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
Another Shmoocon down... and only one more to go 🥲. Safe travels to everyone departing DC. Apologies if I missed you; I was only in for a hot second (due to my delayed departure)!
You can get in touch with me by email as always. I'll be back next week with all the news you might've missed and more.
Until then,
@zackwhittaker