this week in security — january 15 edition
THIS WEEK, TL;DR
Royal Mail hit by outage, believed to be ransomware
BBC News: We start with the U.K., where it appears that the postal service may have been hit by ransomware. It's early days, and we don't know much. The Royal Mail said it's experiencing a "cyber incident" but doesn't seem to know what caused it (ahem!), and the service can't post anything overseas because of the incident — though domestic deliveries are so far unaffected. The BBC reports that back office software used at six Royal Mail sites are affected, grinding the service to a slow crawl. The postal service ships some 200,000 parcels abroad on average each day. It's not clear exactly who caused the incident (assuming it is ransomware), but, to be clear, nothing has been confirmed yet (or come close, frankly). Keep a close eye on this one, since most things revolve around logistics. The knock-on effect here could be significant — and costly.
More: Royal Mail incidents | @RoyalMail | @gossithedog
Microsoft fixes 97 Windows vulnerabilities, including one exploited zero-day
SecurityWeek: Microsoft dropped close to a hundred security fixes this week during its monthly Patch Tuesday release, including a zero-day that can escape a browser's security sandbox, but which Microsoft provided very few details. Microsoft also said that details about an SMB Witness Service flaw are also publicly known. This week also saw the last paid extended security updates for Windows 7 users before those security patches dried up for good, a decade after Windows 7 was first released. SAP, Intel, and Android also released security updates this week.
More: The Register | Naked Security
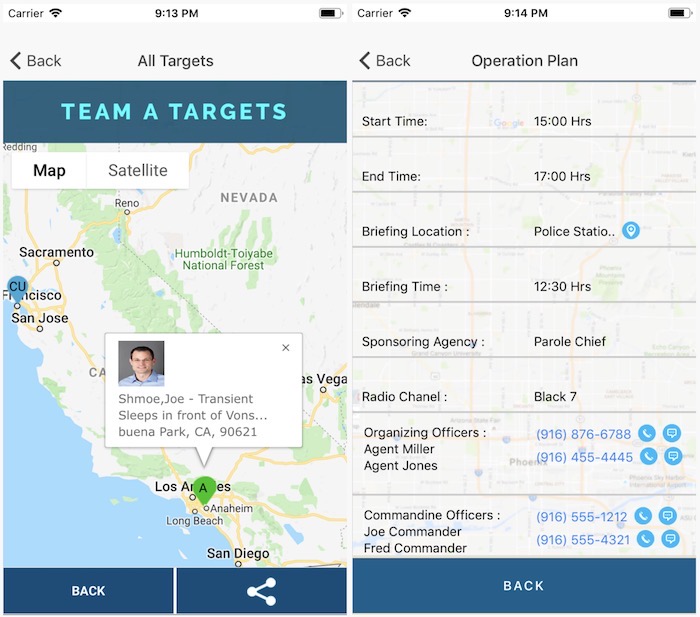
A police app exposed secret details about raids and suspects
Wired ($): This is absolutely wild reporting, one that starts with the obvious question: Why do the police need an app(!) for raiding people's homes? Then, ask, why wasn't the app more secure? That's the crux of this incredible story looking at SweepWizard, and a major API vulnerability that exposed private information about police raids — including names and locations of close to 6,000 suspects, mostly in California, and in some cases leaking biometric details, such as height, weight, and eye color. The app is made by ODIN Intelligence, which provides tech services to law enforcement. Absolutely brilliant reporting.
More: @mayawiley | @mattburgess
Identity thieves skirted Experian security to access credit reports
Krebs on Security: Rounding up this week's top news with another reminder of just how fundamentally broken the U.S. is — let's discuss credit for a hot second. The thing that arbitrarily decides whether you're allowed to buy that house, or simply exist on paper in order to get state services, like healthcare. That's because so many state and federal services rely on a person's credit file to verify their existence, rather than relying on the U.S. government, which has all that data anyway. (Don't even get me started on that.) So when those vast reams of scraped, privately-held data becomes available (even though it was collected without your consent or ability to opt out), or is breached, it makes the whole point of credit less valuable, important, or even helpful when bad actors can use that data to impersonate you. All of this to say, once again criminals have found a way to access U.S. credit reports by way of Experian, a credit giant with a long history of leaking or spilling Americans' private credit data. Yes, you can probably sense my exasperation at the sheer ass-hattery of this billion dollar credit industry that only exists to royally f**k up your day. There is some good news in all this — check the happy corner below for more.
Background: The Guardian (2015) | Krebs on Security (2022) | More: @kimzetter
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Bugs in Threema undermine its encryption claims
ETH Zurich: Threema, the end-to-end encrypted messaging app billed as a more secure alternative to apps like Signal and WhatsApp — and used by the Swiss army and the German chancellor, contains several flaws that undermine its security guarantees, like allowing impersonation attacks. Some mitigations have gone into effect. @kientuong114 has a great tweet-thread, and Ars Technica has more on the paper — and Threema's rather bad handling of the situation (which is a shame).
ChatGPT is enabling script kiddies to write functional malware
Ars Technica: Is ChatGPT, the internet's latest plaything, a cybersecurity threat? While the AI-enabled chatbot allows low-skilled wannabe-hackers to write relatively convincing phishing emails, fears for all-out AI cyberwar are probably a distance away.
Taking over a dead IoT company
Kevin Chung: When an IoT company called NYCTrainSign — which, as you might guess, made internet-connected NYC subway-style digital signs — went out of business, @kchungco explored why the company went bust, which included Chung buying the company's expired domain, allowing Chung to get full control of the signs still in the field. This is a fascinating blog post, with code and a website to also explore. (via @campuscodi)

Cyberattack against records vendor Cott Systems interrupts counties nationwide
Statescoop: An apparent cyberattack on a digital-records management vendor called Cott Systems is causing havoc across local governments, which rely on the company's systems to manage and automate digital workflows for government records. Cott serves some 400 local governments across 21 U.S. states. Several municipalities are locked out and are struggling to process records, like birth certificates and marriage licenses, by hand.
A government watchdog spent $15,000 to crack a federal agency’s passwords in minutes
TechCrunch: The Department of the Interior is a federal executive department that you might not think much about, but it manages the U.S.' public land and national parks, and a multi-billion dollar budget. Think "Parks & Recreation" at the national level, and you're not far off. And as you might expect, the department's cybersecurity isn't what it could be. As part of a previous engagement, the Interior's watchdog, a.k.a. its inspector general, found the department's passwords were really bad, like "Nationalparks2014!" bad. Worse, its two-factor was inconsistent, if not barely existent. So the watchdog spent a few thousand dollars building a password-cracking rig (technical details of which are in the story) just to prove how little effort it would take a reasonably-well resourced actor to break into the department's network. Sure, you might not think it stores a ton of sensitive data, but it doesn't look good if any federal government department suddenly gets hit by a nasty case of ransomware. (Disclosure: I wrote this story!)
~ ~
OTHER NEWSY NUGGETS
Top U.S. court won't block NSO spying lawsuit: The U.S. Supreme Court declined to intervene or block a case brought by WhatsApp against spyware maker NSO Group, which the messaging app giant accuses of exploiting a vulnerability to hack and spy on over a thousand WhatsApp users, including journalists and lawyers. NSO claimed it had "sovereign immunity," essentially saying it couldn't be sued as it was acting on behalf of a foreign government — which can't easily be sued in ordinary courts. The case bounces back to a lower court, which will now hear the case. (via Associated Press)
SEC sues law firm to identify hack victims The U.S. securities regulator is suing the law firm Covington to learn the names of close to 300 of the firm's clients whose information was accessed by criminal hackers in a previously undisclosed cyberattack, according to court documents seen by Reuters ($). The SEC asked a federal judge to force Covington to turn over the names, saying it's investigating possible securities violations associated with the breach. The "Hafnium" cyber-espionage group, associated with China — known to have targeted law firms — was blamed for the breach. (via Reuters ($))
PLCs hit by Stuxnet vulnerable to fresh flaw: The very same kind of ubiquitous programmable logic controllers (or PLCs) that were found inside Iran's Natanz uranium enrichment plant and were quietly hacked by the Stuxnet worm have a new set of flaws that allows their complete compromise. Red Balloon Security found the flaws in a Siemens PLC, which isn't easily fixable — so Siemens isn't going to bother. Even though these PLCs can only be exploited with physical access, Wired ($) notes that the Stuxnet worm also required physical access — which it obtained by way of a tainted USB thumb drive that wormed its way into the Iranian nuclear facility. All to say, be careful if you're running a... nuclear enrichment operation (or similar), I guess? (via Wired ($), SecurityWeek)
BART breached: Criminal hackers posted a huge trove of data stolen from the San Francisco Bay Area transit system, known as BART. The trove of data contains police reports, including specific allegations of child abuse and mental health record forms, reports NBC News. No services were affected by the apparent ransomware attack, which resulted in the theft of more than 120,000 files. (via @kevincollier)
Did the FBI hack this ISIS site? The feds are refusing to say how they obtained the IP address of someone they claim visited an ISIS-related terror site on the dark web. The feds charged a suspect with attempting to provide material support to ISIS, but it remains a mystery how the FBI apparently deanonymized the suspect's alleged internet activity. Could it be that the FBI hacked the ISIS site and captured the real-world IP addresses of those who visited? (via Motherboard)
CircleCi confirms breach, secrets theft: What was a terrible security incident was made slightly better by the immediate disclosure followed by transparent post-mortem of its breach. CircleCi warned customers to rotate "any and all secrets" after intruders broke into the company's systems by way of malware on an employee's computer, which stole the employee's session tokens used for maintaining persistent logged-in access to other systems. (It's a very similar breach to LastPass, in that regard.) In a refreshing change from the norm, CircleCi took the blame, shielding the employee, saying it was a "systems failure" that the malware wasn't detected. (via CircleCi)
~ ~
THE HAPPY CORNER
The happy corner is a little quiet this week. But a couple of things to note:
Earlier we discussed Experian, the credit giant caught once again fluffing its security. The fact that the U.S. government relies so heavily on these data-hungry companies to verify its own citizens is baffling — but it's long been the case. (Years ago when I moved to the U.S., I couldn't buy a health insurance plan via the government's Healthcare.gov portal without first having a credit report on file, requiring me to apply for a credit card before I was able to get health insurance. Welcome to America!) Thanks to @alng's dogged reporting on the bizarrity and backwardness of the government's reliance on third-party data, Login.gov, the login service for accessing federal government services, will soon verify new users using data directly from the government. That's a huge deal. (Look, this is one of those rare times you can say, "the government already has my data, there's no need to farm it out to some profit-hungry corporate giant for absolutely no reason.")
Some personal news from the internet's favorite lawyer: @kurtopsahl is stepping down from the Electronic Frontier Foundation after more than two decades at the non-profit. Opsahl is joining the Filecoin Foundation, and will stay on as EFF special counsel.
And finally: can you crack this OSINT challenge?
If you have good news you want to share, get in touch at: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's two-for-one cyber cat special is Franklin (front) and Schrödinger (back) watching their human work. Clearly workplace surveillance is getting really out of hand. A big thanks to Ingrid S. for the submission!

Keep sending in your cyber cats (or their non-feline friends!). You can email me a photo with their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And scene, for this week. Same time next Sunday? Thanks for reading! As always, feel free to drop any feedback in the suggestion box or email me any time. If you liked this newsletter, please share with a friend, colleague, or on your socials.
Have a great week wherever you are,
—@zackwhittaker