this week in security — january 16 edition
THIS WEEK, TL;DR
Russia arrests 14 alleged members of REvil ransomware gang
Washington Post ($): And that was that... Russia has arrested 14 alleged members of the REvil ransomware gang at the request of U.S. authorities, the FSB put out in a statement this week. REvil has become known as one of the most high-profile and ruthless ransomware groups, targeting meat processing plant JBS, the attack on IT provider Kaseya that affected over a thousand downstream businesses, and — we now have it confirmed, that REvil was behind the Colonial Pipeline attack, which was previously attributed to REvil affiliate Darkside. The timing is not an accident, per @DAlperovitch — as Russia looks for brownie points at a time when the U.S. is keen to avoid a Russian invasion of Ukraine (more on that in a moment). Watch the raid here.
More: Wall Street Journal ($) | TASS | @vxunderground | @kevincollier
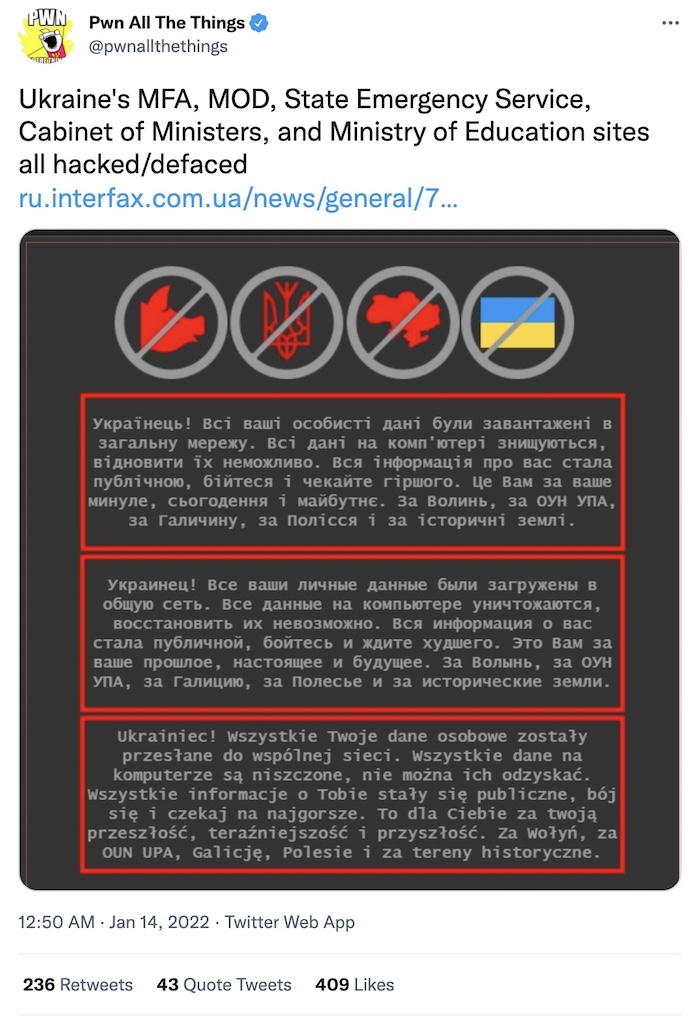
Ukraine suspects group linked to Belarus intelligence over cyberattack
Reuters ($): Mass defacement of Ukrainian government sites this week was blamed on a threat group linked to Belarus, dubbed UNC1151, a close ally of Russia. The defacements came with threatening messages at a time when Russia's military is building up on its border with Ukraine. The defacements were in broken Polish, which some pointed to an attempt at disinformation to suggest Polish culpability, but were quickly blamed on the Belarusian cyber unit. Microsoft also dropped a blog with details of the operation.
More: SecurityWeek | Microsoft MSTIC | @pwnallthethings
Largest darknet stolen credit card site closes
BBC News: It's the end of an era for the UniCC marketplace after it shut down after making more than $350 million during its time. UniCC was one of the biggest forums for sharing stolen credit cards. In its departing note, the marketplace's operators cited age and health for their closure. It's the latest carding site to shutter in recent years; many due to exit scams closely followed by voluntary retirement — and then police shutdowns.
More: Bleeping Computer | @joetidy
U.S. military links prolific hacking group to Iranian intelligence
CNN: U.S. Cyber Command has uncovered multiple open-source tools and malware linked to Iranian intelligence attacks on networks around the world. The Iranian hackers are known as MuddyWater, and the group is known for stealing data from telcos and other organizations across the Middle East. Iran denied the claim, but Cyber Command released details of MuddyWater's malware — and published IOCs on VirusTotal for network defenders to examine.
More: U.S. Cyber Command | @CNMF_CyberAlert
Amazon fixes security flaw in AWS Glue service
ZDNet: Amazon has fixed two vulnerabilities affecting its AWS Glue and CloudFormation services, which allowed an attacker to create resources and access data of other AWS Glue customers due to an internal misconfiguration within Glue's service. Orca discovered the bug. AWS confirmed in an advisory that its logs showed that no customer data was impacted by the bugs since Glue's launch in 2017.
More: Orca Security
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Europol ordered to delete vast store of personal data
The Guardian: Bad news for Europol after it was ordered this week by the European Data Protection Supervisor to delete much of the vast store of personal information it's said to have unlawfully amassed. The EU police body is accused of storing this data on a scale like the NSA collects signals intelligence, some four petabytes of it in total. Europol has six months to figure out what it can keep and what it must delete.
Moxie moves on, departs as Signal CEO
Signal: Moxie Marlinspike said he's departing as Signal's CEO. He's handing the reins of the end-to-end encrypted messaging app to Brian Acton, who serves on the Signal Foundation board, who will be Signal's interim CEO. For those who don't recall, Acton co-founded WhatsApp back in the day. Marlinspike will remain on Signal's board. Since founding, the app has exploded in popularity. You can read the full blog here.
New Chrome security measure aims to curtail an entire class of Web attack
Ars Technica: Hackers often use browser vulnerabilities as a point of initial access. Now Google is doing more than just fixing browser bugs. Somewhere around Chrome 101, the browser will be mandatory for public sites to seek explicit permission before they can access endpoints behind the browser. Ars has the detailed technical explainer.
Feds' spending on facial recognition tech expands, despite privacy concerns
Cyberscoop: Federal authorities are spending more on facial recognition tech, despite privacy (and public!) concerns. On December 30, the FBI signed a contract worth $18,000 with Clearview AI. Others, like ICE, are spending even more — hundreds of thousands of dollars — to get access to Clearview's data, which has faced scrutiny for scraping billions of photos from social media sites without their consent. More than 27 states and localities have passed some sort of ban on facial recognition use, per Cyberscoop.
~ ~
OTHER NEWSY NUGGETS
Apple fixes 'doorLock' HomeKit bug in iOS 15.2.1
Apple: Apple has pushed out a bug fix patch in the form of iOS (and iPadOS) 15.2.1, which fixes the doorLock vulnerability in HomeKit, Apple's smart home platform, which can render an iOS device essentially bricked through a denial-of-service condition triggered by HomeKit devices with extremely long names. Patch today!
North Korean hackers stole nearly $400M in crypto last year
Wired ($): $400 million is an eye-watering amount of cryptocurrency to steal, but North Korean hackers pulled it off, thanks to an entirely new generation of crypto startups and exchanges vulnerable to attack. That's according to data from Chainalysis. North Korea uses crypto thefts to fund its nuclear weapons program in the face of growing international standards. "The growth in stolen funds also tracks with the number of thefts last year; the seven breaches Chainalysis tracked in 2021 amount to three more than in 2020, though fewer than the 10 successful attacks that North Korean hackers carried out in 2018, when they stole a record $522 million."
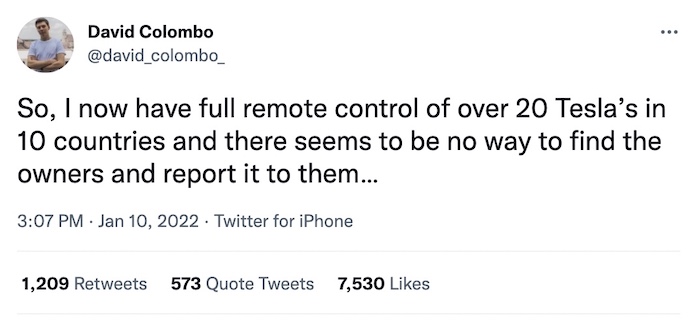
How a hacker controlled dozens of Teslas using third-party app flaw
Motherboard: This will be an interesting one to watch... a security researcher found flaws in a third-party open source app — which hasn't been named yet since the issue remains active — which allowed him to track and unlock at least two-dozen Teslas. Although some cars can be remotely accessed to honk the horn, see its current location and more, it's not believed the car's acceleration and steering can be remotely controlled.
Accellion claims no 'guarantee' of security in $8.1M breach settlement
SC Magazine: Accellion has reached an $8.1 million settlement in its class-action data breach lawsuit after about 9.2 million individuals were affected by the months-long breach of its file transfer system, which resulted in the vast theft of sensitive data. As @tarah notes, that's about $0.88 per user impacted for a settlement, which Accellion ultimately pinned the blame(!) on customers for being "solely responsible and liable for the use of and access to” the FTA software.
~ ~
THE HAPPY CORNER
And... scraping the barrel of good news this week, there's one nugget of goodness.
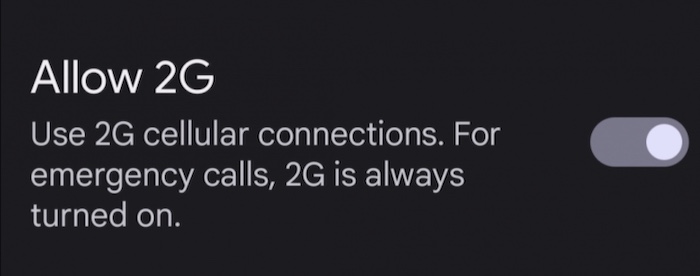
Last year Google quietly pushed a new feature to Android users allowing device owners to switch off 2G at the modem level. That's great news for folks who want to essentially 'opt-out' of stingray cell surveillance, which relies on the legacy 2G to operate. Cell site simulators ("stingrays") can intercept your location and communications by tricking your phone into downgrading from the more secure 3G and 4G to 2G. Switching off 2G essentially prevents that from happening. Now it's Apple's turn...
If you want to submit good news from the week, reach out! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week features Finn, whose human tells me that Finn was very well behaved on his first Christmas and didn't try to eat anyone's presents. Finn has also been a great distraction from Log4j in recent weeks. Way to go, Finn, what a good boy! Thanks to @rmzab for the submission!

Don't forget to send in your cyber cats (or their friends)! Drop me an email here with their name and photo, and I'll make sure they're featured in a later newsletter.
~ ~
SUGGESTION BOX
That's it for now — thanks for reading! The suggestion box is open as usual, or feel free to drop any feedback at this@weekinsecurity.com. Take care, and have a great week.