this week in security — january 21 edition
THIS WEEK, TL;DR
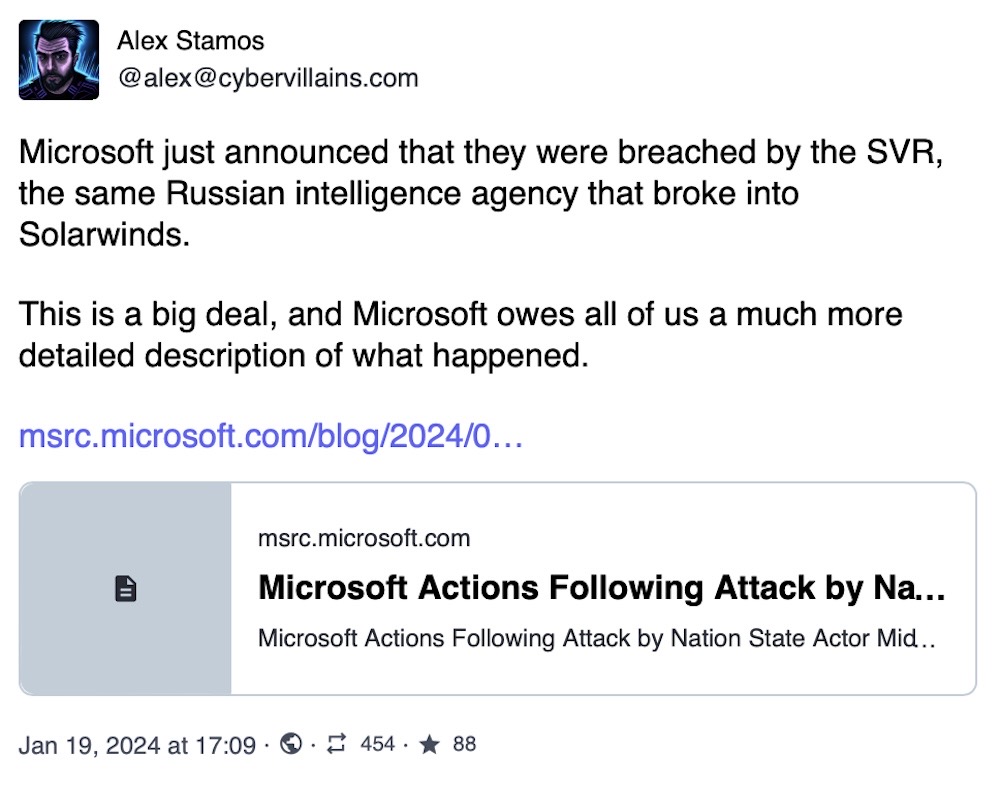
Russian SVR spies hacked into Microsoft executive, infosec emails
MSRC: Let's start with the late Friday breaking news: Microsoft was hacked (again), but this time by Russian spies in November 2023 targeting the email inboxes of executives and cybersecurity staff. Turns out the hackers wanted to know what Microsoft knew about them. To wit: "The investigation indicates they were initially targeting email accounts for information related to Midnight Blizzard itself," Microsoft disclosed Friday (also as an 8-K). Microsoft pointed the blame at hackers working for Russia's foreign intelligence agency SVR, specifically the same group that hacked SolarWinds, per Mandiant's @JohnHultquist — so not small fish by any means. But how the spies got in will require some further probing: Microsoft said the hackers used a "password spray attack to compromise a legacy non-production test tenant account and gain a foothold." How the hackers got from a test tenant to the corporate inboxes of senior Microsoft execs (and cyber and legal) is the big question. Microsoft's already on the CSRB's investigative watchlist for a separate breach of government emails last year, so more fuel to the fire.
More: Washington Post ($) | Ars Technica | TechCrunch | Bloomberg ($) | @GossiTheDog | @reverseics
Ivanti VPN zero-days under mass-exploitation
Volexity: This is not a drill: if you haven't applied mitigations for the recently disclosed Ivanti Connect Secure VPN zero-days, apply them immediately. It's getting messy out there and a ton of criminal actors (and some state-backed) are exploiting the bugs to break into corporations, deploy crypto-miners and more. CISA sounded the alarm for all federal civilian executive branch agencies to mitigate before the end of Monday. Ivanti still has not rolled out patches, though they're expected to start dropping beginning the week of January 22. No sign of ransomware attacks just yet, but Volexity says it fully anticipates that happening with proof-of-concept code in the wild.
More: Ivanti | CISA | The Register | GreyNoise | Mandiant
How cyberscams are drawing China into Myanmar's civil war
Vox: Good reporting here on Myanmar (Burma), whose democratic-ish government was pulled from power following a military coup in 2021, and the subsequent civil war created a hotbed of cybercrime, specifically "pig butchering" scams. These schemes work when scammers randomly contact targets by text message that try to lead the victim on, seemingly to new business or a love interest. (Sophos security researcher @thepacketrat has done a ton of research in this area.) It's in Myanmar's eastern states where much of those scams are carried out — usually in scam centers, which rely on human trafficking to find their "workers," who are kept in awful conditions, though some work willingly. Reporting in the country is difficult, but by the sounds of it, neighboring China has had enough of the scams. Could this be the slow undoing of the Myanmar junta? A report from the BBC in November has good background.
More: The New York Times ($) | The Record | @thepacketrat
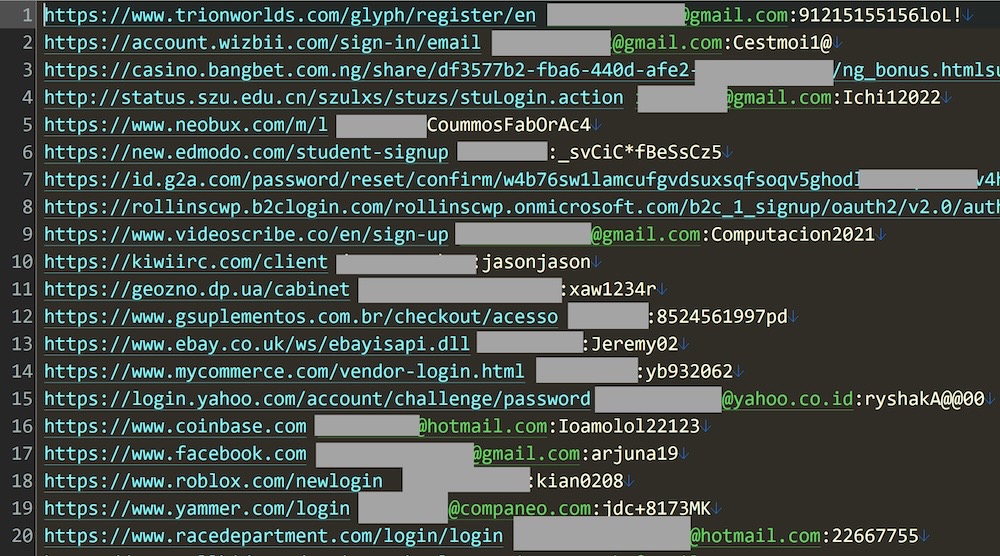
Researcher uncovers one of the biggest password dumps in recent history
Ars Technica: It's been a while since we've seen a massive password dump hit the internet but this week saw the biggest in recent history, amassing some 71 million unique credentials for logging into accounts for Facebook, Roblox, eBay and Yahoo. Data breach notification service Have I Been Pwned operator Troy Hunt said in a blog post this week that a batch of data, known as Naz.api, had been floating around on a popular cybercrime forum for months but was surprisingly still active data. Per Hunt, 65% of the addresses in the dump were already in Have I Been Pwned, meaning about one-third of that were new victims. Info- and password-stealing malware seem to be gaining popularity again. As always, you can check Hunt's site for pwnage.
More: Troy Hunt | Bleeping Computer | @dangoodin
FTC bans another location data broker from selling users' data
Federal Trade Commission: Another bumper week for the FTC after it banned InMarket (formerly CheckPoints) from selling or sharing the precise location data it collected from regular smartphone apps without users' explicit consent. The FTC accused the data broker of not telling consumers that their information was used for advertising and marketing, allowing the company to create data categories such as "Christian church goers" and "wealthy and not healthy," per the regulator. It comes just weeks after banning X-Mode for similar reasons (with potentially more enforcement action targeting the data broker industry to come). Separately... but worth watching: license plate-reading companies (think ALPR) were hit by a privacy class-action suit that could see parking companies have their data collection curtailed from harvesting license plate information and "using it to 'harass' drivers."
More: FTC | Austin American-Statesman | Bloomberg Law ($)
~ ~
THE STUFF YOU MIGHT'VE MISSED
Kaspersky detail new iOS exploit detection by analyzing shutdown logs
SecureList: Kaspersky has a new method of analyzing iOS mobile infections, including NSO's Pegasus. Tools like the Mobile Verification Toolkit are great for spotting possible infections from lists of indicators of compromise (such as domains and IP addresses). Kaspersky says it's also possible to parse shutdown logs, which can go back years, using new open source code it's published on GitHub.
New macOS password stealers caught evading detection
SentinelOne: Security researchers at SentinelOne say they have evidence of three active info-stealers (like passwords and session tokens) targeting macOS users. Worse, these malware variants are able to evade the in-built macOS anti-malware engine, XProtect. According to the findings, KeySteal, Atomic and CherryPie malware seem to be bundled in with tainted apps and dodgy torrent downloads.
9.8 million Indians had sensitive data leaked thanks to government web bug
Medium ($): A thread by @kmskrishna detailed how more than 9.8 million Indian residents had personal information exposed — including email addresses, phone numbers, passport and voter numbers, and Aadhaar numbers — by way of a bug in the Indian government's Ministry of Corporate Affairs. A blog post goes into more detail, including how it took the Indian government over 11 months to fix the bug. India long claimed its Aadhaar system is secure but can't stop leaking citizens' data.
Interview with Buttigieg campaign CISO on 2024 election challenges
Cyberscoop: Brilliant interview with @nohackme, the former CISO for Buttigieg's presidential campaign in 2020 (and first-ever CISO for a presidential campaign), with Cyberscoop on the challenges coming up this year with the 2024 federal election. Grab some coffee and your headphones, and take an hour to listen.
The human toll of ransomware
RUSI, Computer Weekly: Interesting research out of the University of Kent (my alma mater) explored the human impact of ransomware at an organization and human level. The study's results are simple, but sobering: "In the simplest terms, ransomware attacks are harming the mental and physical health of staff," write the researchers. "Working on a ransomware incident creates considerable stress and anxiety." The write-up is worth the read (and mandatory reading if you're a C-level executive reading this newsletter). Maybe think less about growth, growth, growth and figure out how to protect what you already have (and worked so hard for)?
~ ~
OTHER NEWSY NUGGETS
GitLab bug allows 2FA-less account takeover: Warnings are out about a GitLab account takeover bug with a perfect 10.0 vulnerability severity score. The bug, tracked as CVE-2023-7028, allows malicious hackers to silently take over an account (with no 2FA enabled) on a self-hosted instance. Another good reminder to always use 2FA! (via The Register, GitLab)
Meet the 'Walmart scheme': A scam dubbed the "Walmart scheme" has allowed scammers to cash in and extract money from victims, according to reporting by ProPublica's @craigsilverman. Per the reporting, Walmart's "lax oversight and poor employee training" made it easier for the scammers to operate. Gift cards were a big part of this, but "Walmart has a financial incentive to avoid cracking down," the reporting shows. (via ProPublica)
Each Facebook user is monitored by thousands of companies: That's right: a study conducted by Consumer Reports [PDF] shows that on average each Facebook user has their data sent to about 2,230 companies. The Markup, which helped recruit participants for the study and wrote about the findings, said much of the data collected includes a user's web activity outside of Facebook — which The Markup has shown can contain anything from people contacting suicide hotlines, buying groceries, filing taxes and booking medical appointments. (via CR, The Markup)
Gaza hit by 'longest' outage of conflict so far: Web monitors say a week-long internet outage in Gaza is the "longest" since the start of the Israel-Hamas conflict following an attack by Hamas on October 7. Palestinian ISP giant Paltel said "all telecom services" in Gaza are down, in part due to damaged infrastructure. Good reporting from @kevincollier about how eSIMs (digital SIM cards) are used by folks in Gaza to communicate, often by catching a roaming signal from nearby Israel or Egypt. (via Access Now, TechCrunch, NBC News )
BreachForums admin sentenced to 20 years: Conor Fitzpatrick, who created and ran the notorious BreachForums cybercrime site, was sentenced to 20 years of supervised release this week. Fitzpatrick, aka "pompompurin," was arrested in March after a long-running FBI operation. He was initially charged with computer crimes, but had additional charges tacked on when the feds found he was in possession of dozens of CSAM videos. (via Cyberscoop)
~ ~

~ ~
THE HAPPY CORNER
Onto the happy corner!
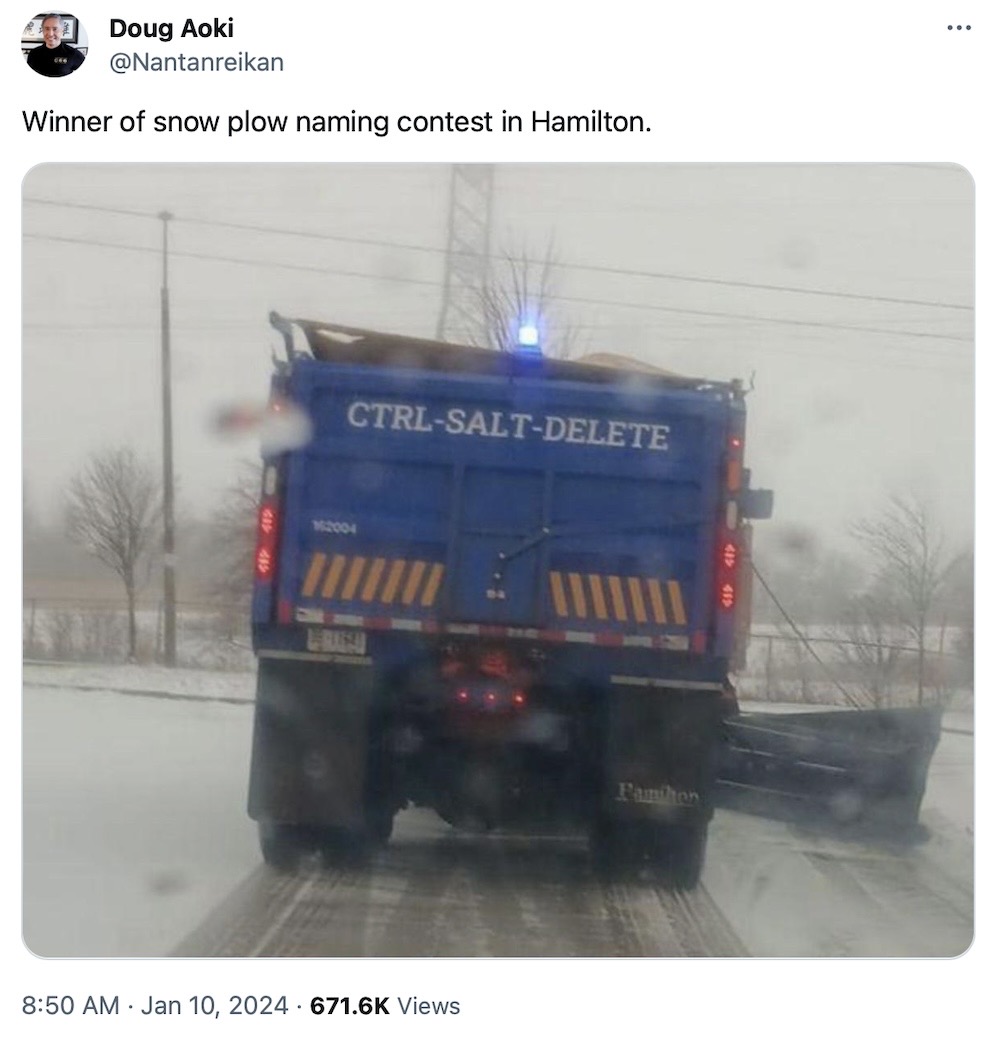
Shout-out to everyone who, like me, is stuck in freezing temperatures and several inches of snow and ice. At least we have this:
Meanwhile, there's a sassy hacker on the loose.
![Dgar toot: "To the person who hacked my account, I will find you. [Edit] No you won’t."](https://this.weekinsecurity.com/content/images/scraped_images/c9ee3bd8-c181-2a03-1070-fe1e0fc21552.jpeg)
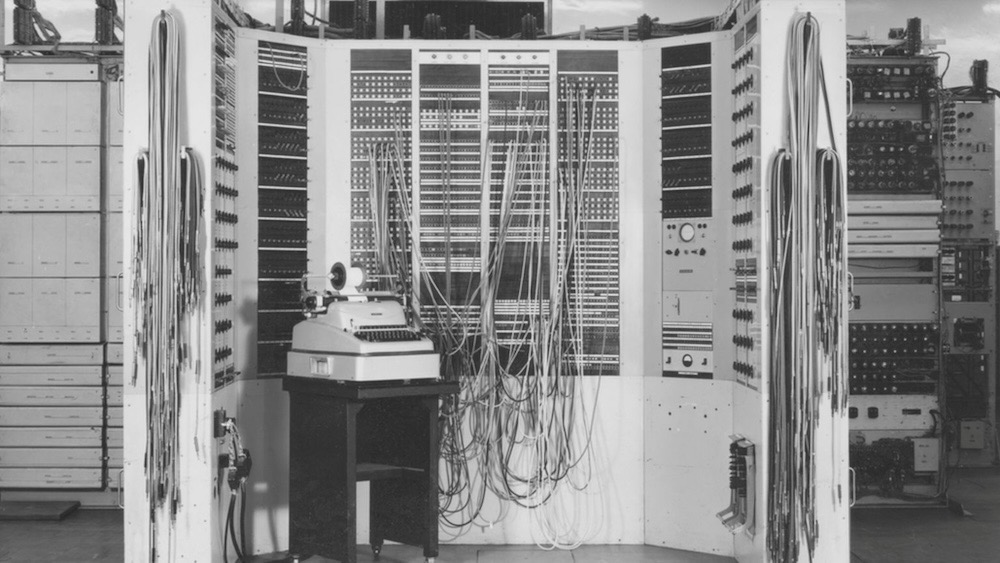
And lastly, this week. We're about 80 years late but we're finally seeing never-before-seen photos of Colossus, the U.K.'s secret code-breaking computer that helped the Allied forces win World War Two. GCHQ released the images this week of the Bletchley Park computer that cracked the Nazi's Enigma cipher. According to the BBC, eight out of the 10 computers were destroyed, and its engineers were ordered to hand over all documentation back to the government. Efforts to keep the computer's existence a secret was so successful that one former GCHQ engineer who worked on the computer said he had no idea about its wartime role.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
We're checking in this week with Tigrou, a repeat-submission cyber cat, on the charm offensive as usual. With cuteness like that, you could social engineer anything out of anyone. Many thanks to Fabian L. for sending in!

Send in your cyber cats! Email me a photo of your cyber cat (non-feline friends welcome!) with their name they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
Aaaand I'm outta here — but back with you, same time(ish) next Sunday with all of the usual round-up from the week. Judging how we left Friday, expect this week to be a spicy one...
As always, it's great hearing from you. You can drop me an email with any feedback (and cyber-cats!) you want to share. And thanks again for considering supporting ~this week in security~ on Ko-fi.
All my best,
@zackwhittaker