this week in security — january 22 edition
THIS WEEK, TL;DR
U.S. surveillance program captures millions of money transfers
Wall Street Journal ($): If you're drinking your morning brew reading this newsletter, now's the time to dramatically spit out your mouthful of coffee in utter aghast. Hundreds of U.S. law enforcement agencies have access to a massive database of 150 million money transfers between the U.S. and 20 other countries through a non-profit called TRAC, or the Transaction Record Analysis Center, which was set up by the Arizona attorney general's office as part of a settlement reached with Western Union back in 2014. Yeah, the feds pretty much strong-armed a bank into spying on us. It was only brought to light by Sen. Ron Wyden's office, which has been investigating TRAC in recent years. The ACLU says TRAC is "one of the largest government surveillance programs in recent history." The brightest sunlight brought to you by the excellent @dnvolz and @ByronTau.
More: Sen. Ron Wyden | Reuters ($) | ACLU | @ACLU tweets
U.S. airline exposed 2019 copy of the U.S. "No Fly List"
Daily Dot: More than 1.5 million names on the U.S. No Fly List, a list set up after the 9/11 attacks to ban terrorists and other known criminals from flying to (or within) the U.S., were exposed after U.S. airline CommuteAir left a huge amount of company data, including about employees, in an exposed Jenkins development server. CommuteAir confirmed the data spill — including the list itself, which had IRA members and the Russian arms dealer Viktor Bout, who was recently swapped in a prisoner exchange for U.S. basketball star Brittney Griner. The list itself was stored as NoFly.csv, the Daily Dot reported. The exposed data was found by Swiss hacker maia arson crimew, who was previously indicted by U.S. authorities for the breach at surveillance company Verkada. crimew posted a technical write-up of her discovery. The TSA is investigating the incident.
More: CNN | maia blog | @mikaelthalen tweets
T-Mobile hacked (again), 37 million customers' data stolen
TechCrunch: It's a day ending in "y" so it must be another T-Mobile data breach announcement. The third-largest U.S. cell giant with some 110 million customers said in an SEC filing this week about one-third of them had their "name, billing address, email, phone number, date of birth, T-Mobile account number" and some other subscriber data stolen by way of abusing an API. Details here are extremely thin. Was it an unauthenticated API, like it was the case with Australian telco Optus? We don't know, but its breach notice said the hacker didn't "breach our systems or our network," so maybe? Depending on how you count it, this is the eighth security incident involving data theft since 2018. Its most recent incident was last year when the Lapsus$ hacking crew broke in, stole source code, and gained read-access to customers' accounts.
More: T-Mobile | Associated Press | Krebs on Security
Police tech contractor ODIN Intelligence hacked, data exfiltrated
Motherboard: ODIN Intelligence, a police tech vendor I mentioned last week after its website was defaced by hackers who claimed to have stolen the company's data and deleted its backups, was really hacked. Some 18+ gigabytes or so of data was exfiltrated and provided to transparency collective DDoSecrets. There is a lot of data in here — including facial recognition scans and ALPR license plate tracking — but much of it relates to SweepWizard, the app ODIN develops for police to coordinate multi-agency police raids. Much of the data contained specifics about police raids, tactical plans, but also a wealth of data on individuals with no criminal record or who have not been charged with a crime. ODIN hasn't commented on the breach, but disclosed the incident with the California attorney general's office. You should also read Wired's ($) story, which first broke news of the company's massive security problems last week. (Side note: it's very clear that ODIN is trying to insinuate that Wired was somehow to blame for ODIN's massive security problems. ODIN has nobody to blame but itself for its shoddy cybersecurity, and for ignoring and dismissing Wired's findings.)
Archive: Wired ($) | More: TechCrunch | DDoSecrets (blog)
Ukraine says Russia is coordinating missile strikes with cyberattacks and psyops
The Record: Researchers from Ukraine's economic security council say Russia is coordinating kinetic military action and missile strikes with psychological operations (aka "psyops") — like cyberattacks and causing power outages — designed to confuse Ukraine's forces. It follows a report by Microsoft last year looking at how Russia's military operations are timed with cyberattacks and other non-kinetic action. It's a fascinating and interesting look at the hybrid war in action to understand Russia's military playbook. By examining this, Ukraine hopes to draw attention to how the world responds to cyber-war.
Background: Microsoft | More: Ukraine government | Lukasz Olejnik | @snlyngaas tweets
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Royal Mail confirms cyberattack, still mum on incident details
TechCrunch: During a U.K. parliamentary select committee this week, the U.K. postal service's CEO Simon Thompson told lawmakers that the Royal Mail "cyber incident" was in fact a "cyber attack." That distinction is important, given the postal giant spent a week waffling on its language all the while the company's spokespeople continued to decline to comment. The company didn't update its incident page for a week — except for the date. So much for transparency! Royal Mail continues to experience delays, reports the BBC. An alleged ransomware (though not yet confirmed) apparently took out the Royal Mail's customs label printing systems, causing the massive backlog.
Spyware seller Intellexa fined for holding up Greek inquiry
The Record: "Greek Watergate" continues on. As a recap, the Greek government is accused of using nation-state level spyware, dubbed Predator, to spy on journalists critical of the government. The country's data protection agency is investigating (as are EU lawmakers, given Greece isn't the only European government using spyware on the continent). In an interesting twist this week, the Greek data authority fined Intellexa, which sells Predator to governments, some €50,000 (about $54k) for deliberately holding up its inquiry. It's also told Intellexa to immediately turn over all invoices and receipts since it launched. Grab your popcorn.
Cognyte won bid to sell spyware to Myanmar before coup
Reuters ($): Sticking with spyware... Israeli spyware maker Cognyte was awarded a tender to sell intercept spyware to a Myanmar state-backed telco just months before a military coup took over the country in February 2021. Israel claimed to stop selling "defense technology" to Myanmar in 2017 following a Supreme Court ruling, which was subject to a rare gag order and cannot be reported. But, Reuters found that the Cognyte deal was allowed as recently as December 2020, just weeks before the coup. This was already at a time when things were tense in Myanmar following elections, with fears of an imminent military takeover. Cognyte's spyware can listen in on calls, view text messages, and sift through internet traffic to read emails and track people's locations. (For background, read Reuters' story from 2021.)
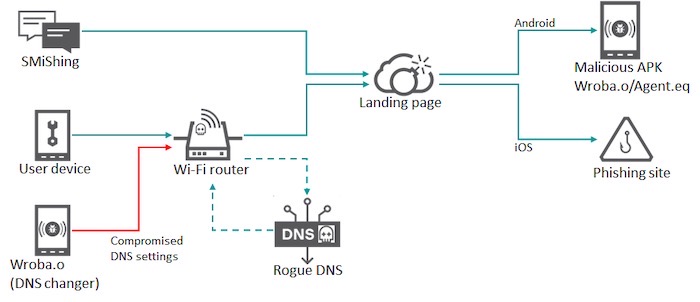
Hacker group uses DNS hijacking to redirect victims to malicious sites
Ars Technica: A new malicious Android app can remotely tamper with the wireless router that the infected phone is connected to, changing its DNS settings, and allowing the hackers to silently route victims to malicious sites. Kaspersky's findings shows the malware uses common or default credentials to break into local routers to carry out so-called DNS hijacking attacks. That means it's possible to route victims to legitimate looking domains, but are in fact pointing to malicious spoofs.
The many ingenious ways people in prison use (forbidden) cell phones
The Marshall Project: This is an eye-opening story about how convicted criminals in U.S. prisoners are using contraband cell phones to better their lives. "That’s the only way we can do things to better ourselves because they damn sure don’t offer that stuff here," said one prisoner. Cell phones in prison are illegal (and if caught can lead to solitary confinement and even extra criminal charges). But many prisoners use these contraband phones to take public Harvard classes, learn medical care and first aid, and use YouTube and TikTok to develop new skills, even fixing the very phones they managed to smuggle in. "I was able to FaceTime my mom before she passed away,” a federal prisoner who used to have a contraband phone told @keribla. Think what you will about prisoners. Many deserve to be in prison, and some will never leave. But you can't help feel compassion for folks who, just like you and I, want to do better in this world, or just say goodbye to their loved ones before they pass.
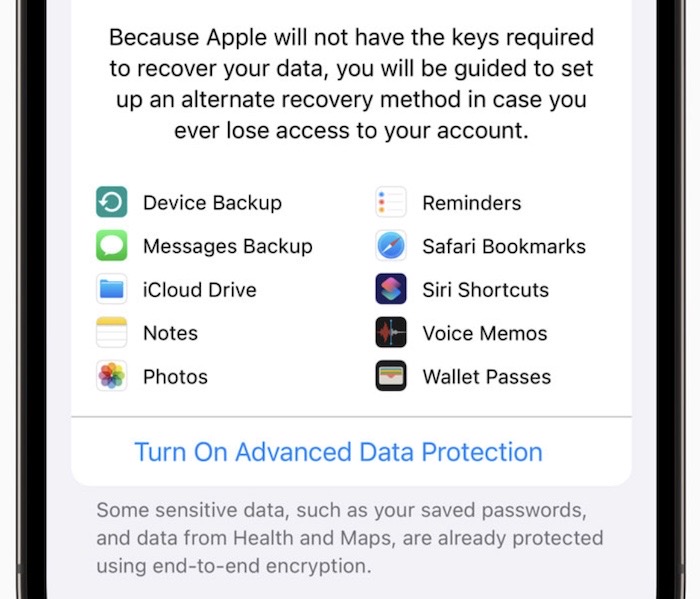
iOS 16.3 brings end-to-end encryption to iCloud worldwide
9to5Mac: iOS 16.3 will allow users around the world to switch on iCloud's Advanced Data Protection, a new feature that end-to-end encrypts users' data stored in its iCloud service. The idea is to make data uploaded to Apple unreadable to anyone, other than the user, even Apple. The feature was rolled out in iOS 16.2 (those who want to encrypt local backups can continue doing so), and was confirmed this week that it'll roll out globally. But watch out for updating HomePods, which apparently get snagged (but not irreversibly) by the encryption feature.
~ ~
OTHER NEWSY NUGGETS
Mailchimp hacked for second time in six months: Mailchimp, the company that gets hacked only slightly less (it seems) than T-Mobile, confirmed another compromise this week, one that mirrors a near-identical breach from August. Mailchimp said this week (as it did back then) that a social engineering attack nabbed employee passwords, allowing access to internal tools that exposed personal information from 130 Mailchimp accounts — including one belonging to WooCommerce, which has millions of customers, and web3 company Yuga Labs. When reached for comment, a spokesperson for Intuit, Mailchimp's parent company, wouldn't say who, if anyone, was presently responsible for security at Mailchimp following the departure of CISO Siobhan Smyth following August's breach. (Disclosure: I wrote this story! Also, this newsletter is sent via Mailchimp but was unaffected by the breach.) (via TechCrunch)
You want a side of ransomware with your KFC? U.S. fast food conglomerate Yum Brands, which owns KFC, Pizza Hut and Taco Bell, said it was hit by ransomware, in a remarkably transparent statement. Well, -ish. The company said the ransomware attack resulted in data being exfiltrated — though not customer data — so perhaps its corporate IT network was directly affected. Yum said that less than 300 restaurants in the U.K. were closed for one day as a result of the incident. But questions remain, and regulators will likely want answers. (via The Record)
How Guacamaya hackers are exposing Latin American corruption: A deeply reported look at the hacktivist group Guacamaya, the Mayan name for a macaw, which is holding powerful governments (and companies) in Latin America — like Mexico and Chile — accountable by way of publishing leaked data. It's not clear who the hacktivists are, but they are fighting back against corruption and wrongdoing in the best way they know how — "through hacking," they said. (via Cyberscoop)
PayPal users got stuffed: PayPal sent out notifications to some 35,000 PayPal users following a credential stuffing attack that allowed cyber-crims to mass-login using leaked or breached sets of usernames and passwords from other sites. PayPal said its systems weren't compromised, but wasn't exactly the most reactive to the incident either. PayPal said the credential stuffing attack exposed users' names, addresses, Social Security numbers, other tax ID numbers, and dates of birth — much of which is available from the users' logged-in account view. (via Bleeping Computer, Maine.gov)
~ ~
THE HAPPY CORNER
Alright, that's the news. This is the happy corner. And breathe.
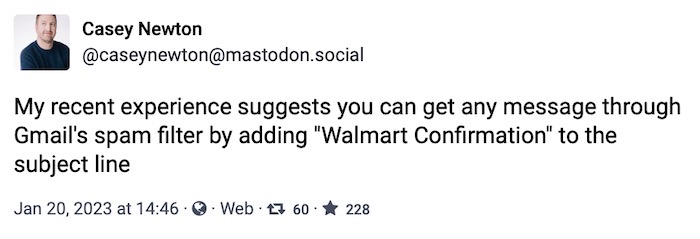
Platformer's @caseynewton may have figured out how to achieve a near-100% email delivery success rate.
The EFF is hiring for a U.S.-based (remote-friendly) full-time position as Security and Privacy Activist (full listing here and more information here). Looks like a solid position for an experienced pro who wants to lead the EFF's flagship security resource, Surveillance Self-Defense, blog, and more.
And finally. The incredible @lorrietweet showed off her new password dress for the first day of class. It's absolutely brilliant — go check it out.
If you have good news you want to share, get in touch at: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
Meet Lily, this week's cyber cat. Here she is helping her human by practicing stealthy monitoring. And she's doing an excellent job. Many thanks to Jim C. for sending in!

Keep sending in your cyber cats (or their non-feline friends!). You can email me a photo with their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
Thank you for reading! The suggestion box is always open, or drop any feedback by email. I'll be back next week with the usual round-up from the week. For those at ShmooCon, hope you have a great time. I have major FOMO for not being there this year.
See you next Sunday, and have a great week.
—@zackwhittaker