this week in security — january 23 edition
THIS WEEK, TL;DR
Crypto.com says 'incident' was actually $30 million hack
Motherboard: Ever have one of those days where you lose upwards of $30 million in cryptocurrency and you shrug it off as an "incident"? That's what happened with Crypto.com, which saw hackers making hundreds of transactions while bypassing its two-factor authentication system. Crypto.com was quiet about the "incident" — its wording, not mine — all week until it admitted it was hacked. The company didn't say how its 2FA system was compromised, but that it was more than $30 million taken in the end. For all that supposed Web3 magic, these companies sure are still suffering Web 2.0 problems.
More: Crypto.com | ZDNet | Bloomberg ($)
Red Cross hit by data breach, warns of risks to humanitarian work
Agence France-Presse: The International Committee of the Red Cross was hit by a cyberattack this week, resulting in the theft of more than 515,000 people's names, contact information and locations, and the temporary shut down of humanitarian programs tasked with tracking people separated from their families due to conflict or disaster. The Red Cross pleaded with the hackers to not use the data as it affects "highly vulnerable people," though the incident is believed not to be ransomware related.
More: International Committee of the Red Cross | CNN | Cyberscoop
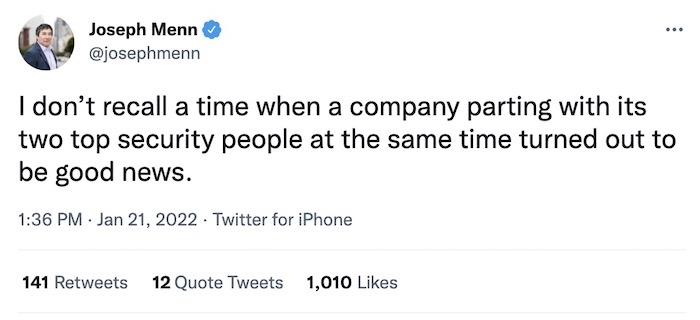
Twitter shakes up its security team
The New York Times ($): Unexpected news as two of the top security leaders at Twitter are departing. Twitter head of security Peiter Zatko (known as Mudge) was terminated for unspecified reasons, and CISO Rinki Sethi is also departing, she confirmed in a tweet, less than two years after joining the company after a major breach. Lea Kissner will head up the security team as its interim CISO. The departures have left pretty much everyone — except Twitter's new chief executive Parag Agrawal, apparently — surprised. But the stock market didn't like the news, dropping Twitter by 5% on the news, and left a lot of people asking the same question: Why?
More: @mikeisaac | @kateconger
Hackers were in Ukraine systems months before deploying wiper
Zero Day: There's a lot going on on the ground in Ukraine, with a hundred thousand Russian troops massing on its border with the country ahead of a widely anticipated ground invasion. As per the Russian playbook, cyberattacks are featured prominently. @kimzetter looks at the recent attacks on Ukrainian systems over the past couple of weeks and what they mean. The latest twist is that a disk wiper that infected systems may have been more opportunistic than extensively planned, since the wiper was compiled only days before it was deployed, according to Cisco research. MIT Technology Review has a good look at what Russia's cyber activities could play out in the run-up to what's looking more like an inevitable ground incursion.
More: Cisco Talos | @kimzetter tweets
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Hackers disrupt payroll for thousands of employers — including hospitals
NPR: The months-old ransomware attack on payroll company Kronos continues to plague thousands of employees, including frontline healthcare and public transit workers, who still aren't getting paid on a regular basis because of extended outages and downtime. Some paychecks are reported to be short by hundreds or thousands of dollars as a result of the attack, with further delays expected ahead of tax season. This NPR story really spells out the human toll the ransomware attack had on ordinary workers — even as Ultimate Kronos Group remains mum on its recovery effort.
Interpol busts a huge Nigerian email fraud operation
Forbes: A massive business email compromise operation has been busted wide open by Interpol. The numbers alone are staggering. Interpol said in a press release that the scammers used more than 800,000 usernames and passwords to hack into 50,000 company and personal email accounts in an effort to trick victims into sending money to the fraudsters. BEC scams remain the most costly kind of fraud to Americans, with an estimated total $1.8 billion in losses in 2020 alone. The group that Interpol took down is called SilverTerrier, and Palo Alto Networks has an explainer on its activities.
Apple says it never intended iOS 14 security updates to last forever
Ars Technica: When iOS 15 landed in September, Apple gave existing iOS 14 users the option to continue running the older version of its operating system and still receive critical security updates without having to upgrade to iOS 15. (iOS 15 was slated to include a controversial child sexual abuse materials (CSAM) detection feature — but the features were eventually paused.) But users recently noticed those updates weren't coming anymore after iOS 14.8.1.
~ ~
OTHER NEWSY NUGGETS
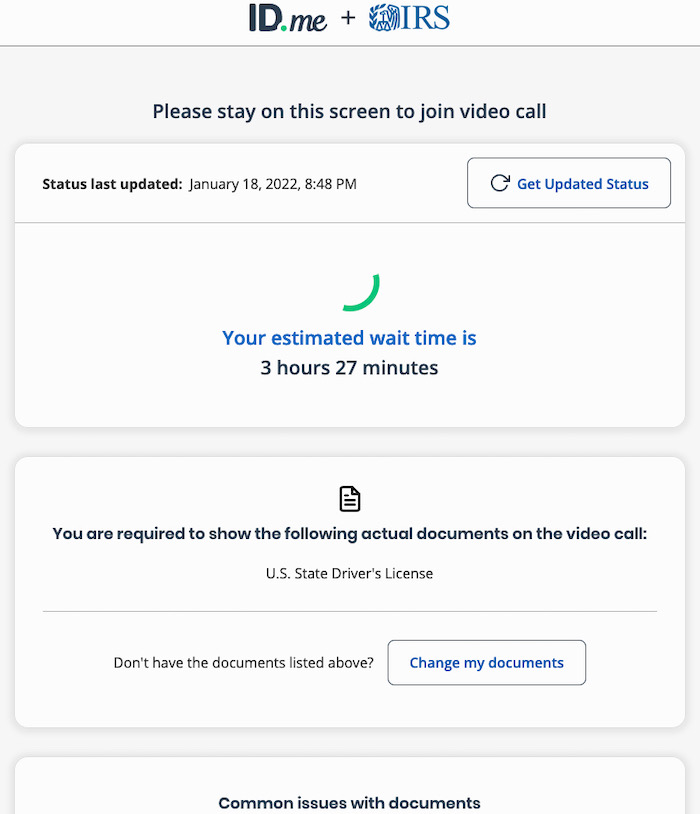
IRS will soon require selfies for online access
Krebs on Security: It's the sort of dystopian nightmare you almost, dare I say it, sort of expect? The IRS is changing identity providers and will by mid-2022 use ID.me, a third-party identity verification service, which requires applicants submit copies of bills and identity documents — including a live video feed of faces via a mobile device. The aim is to cut down on fraud, sure, but some have pointed out, ID.me has faced some difficulties — not just historically — as @libbycwatson notes in a lengthy tweet thread, but also as recently as this week, when the DOJ announced a New Jersey man bypassed ID.me's verification systems with false documents. So things are looking great so far.
Merck wins cyber-insurance lawsuit related to NotPetya attack
The Record: Here's an interesting legal case. Remember a few years ago when shipping giant Merck was hit by the NotPetya ransomware? Merck's insurance company Ace American refused to cover the $1.7 billion costs incurred by Merck, believing it was exempt as it was an "act of war." Except, the New Jersey Superior Court sided with Merck, finding the exemption didn't apply because the "acts of war" clause did not specifically exclude cyberattacks. It's a complicated case, but it's a major win for ransomware victims who find that their insurance companies aren't so willing to cough up after a major incident.
International effort takes down VPN service, VPNLab, used for criminal activity
Cyberscoop: Now it's Europol's turn to share in the international criminal takedown news. VPNLab, a VPN provider used almost exclusively for criminal purposes, was seized by authorities — 15 servers that host the site's infrastructure. "“Law enforcement has now gained access to the vpnlab.net servers and seized the customer data stored within. The investigation regarding customer data of this network will continue." Remember, your VPN provider is probably logging you, even if it says it isn't.
~ ~
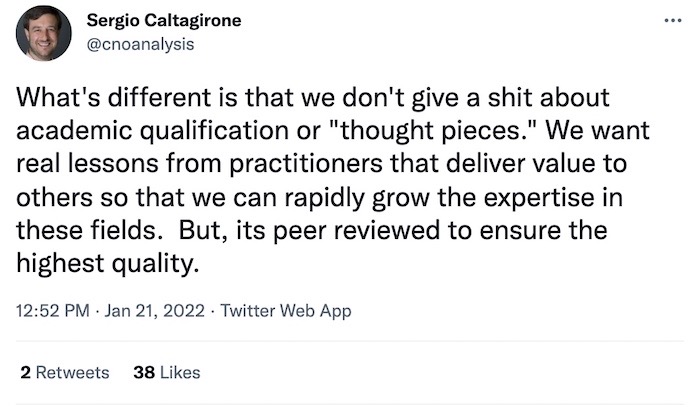
THE HAPPY CORNER
A quick good news item this week. A new peer-reviewed academic journal has launched focusing on threat intel and incident response. This promises to be a great read when it publishes for the first time later this year. More on the Journal of Threat Intelligence and Incident Response here, and more from @cnoanalysis on its aims. Very exciting.
If you want to submit good news from the week, reach out! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Miranda. Sure, she loves to sit on her human's laptop when he's making a cup of tea, but at least she's always making sure its operating system is up to date. A big thanks to Wiktor W. for the submission!

Don't forget to send in your cyber cats (or their friends)! Drop me an email here with their name and photo, and I'll make sure they're featured in a later newsletter.
~ ~
SUGGESTION BOX
And that's all we have this week, thanks for tuning in! The suggestion box is open as always, or drop any feedback at this@weekinsecurity.com. See you next week — be well.