this week in security — january 28 edition
THIS WEEK, TL;DR
Microsoft reveals more on Russia's APT29 email hacking campaign
Microsoft: New details dropped this week on the Russian cyber espionage campaign targeting Microsoft executives and other organizations, including HPE, which hosts its email with Microsoft. In a blog post detailing more, Microsoft said the hackers, Russia's APT29 aka Cozy Bear (either way, the same Russian SVR spies behind the SolarWinds hacking campaign) "has been targeting other organizations" and Microsoft has notified them. This is probably the tip of the iceberg of what's going on (and likely more to come). Microsoft said the Russian spies gained access by way of a non-production test account without MFA, but took advantage of a "pretty big config error" that allowed the reading of any Microsoft mailbox (whoops) by way of malicious OAuth applications. So, it wasn't the most sophisticated attack in the world (since no vulnerabilities were exploited, Microsoft said), but it didn't need to be. That's not to underestimate APT29, but Microsoft really dropped the ball here.
More: Cyberscoop | Washington Post ($) | Ars Technica | @malwarejake
NSA buys Americans' internet records without a warrant
TechCrunch: Sound the Wyden siren, a new surveillance scandal just dropped. Sen. Ron Wyden revealed this week that the NSA is buying vast access to internet records, like netflow and DNS data, per a letter from the NSA's outgoing director. This non-content data can identify traffic flow and volume, and can be exploited for surveillance, which Wyden argued in his letter to the U.S. chief spy asking that the practice stops. Wyden was unable to disclose this for two years while his request was still classified, and so Wyden blocked the incoming NSA director's appointment until the information was cleared for release. The key thing here is that the NSA is purchasing the data — which, like other federal agencies, says it doesn't need a warrant since the data can be bought by anyone. (Wait, no?) But actually, yes! The point is really that nobody should be allowed to buy this data. The Biden administration is reportedly making progress in blocking some data broker sales, per Bloomberg ($). But with the FTC banning data brokers from selling this sensitive information and the NSA actively buying it, the U.S. government can't seem to police its own agencies from its own regulatory decisions. (Disclosure: I wrote this story.)
Background: 404 Media ($) | More: Ron Wyden | Reuters ($) | Wired ($)
Australia sanctions top REvil member accused of Medibank hack
ABC News (Australia): The Australian government announced its first ever(!) batch of cyber sanctions (congrats, folks) targeting Russian national Aleksandr Ermakov, who is accused of the massive Medibank hack that saw 9.7 million Australians have their private health information stolen. The Aussies accuse Ermakov of being behind the attack, meaning it's now illegal to pay Ermakov any assets, including cryptocurrency, such as ransom payments. Medibank was one of the biggest (if not most damaging) breaches in Australia's history. Security reporter Brian Krebs digs into Ermakov's life, and his apparent senior membership of the prolific REvil ransomware and extortion group. Medibank's hack was highly personal in nature — as is Australia's response — by pointing the blame directly at the man it blames for the cyberattack. Ermakov, who remains in Russia, probably won't feel too safe about having his name publicly attached to a lot of bitcoin.
More: U.S. Treasury | Krebs on Security | @briankrebs
~ ~
THE STUFF YOU MIGHT'VE MISSED
Inside Patternz, a global phone spy tool monitoring billions
404 Media ($): A new investigation by 404 Media looks into Patternz, a company that created a mass monitoring tool based on access to hundreds of thousands of apps — including 9Gag, Kik and caller ID apps. Using this access, the company can track the physical location, hobbies and family members of potentially millions. This investigation "provides one of the clearest examinations yet of how advertisements in ordinary mobile apps can ultimately lead to surveillance by spy firms and their government clients through the real time bidding data supply chain." Google and PubMatic, another ad firm, have cut off a company linked to the surveillance firm following the report.
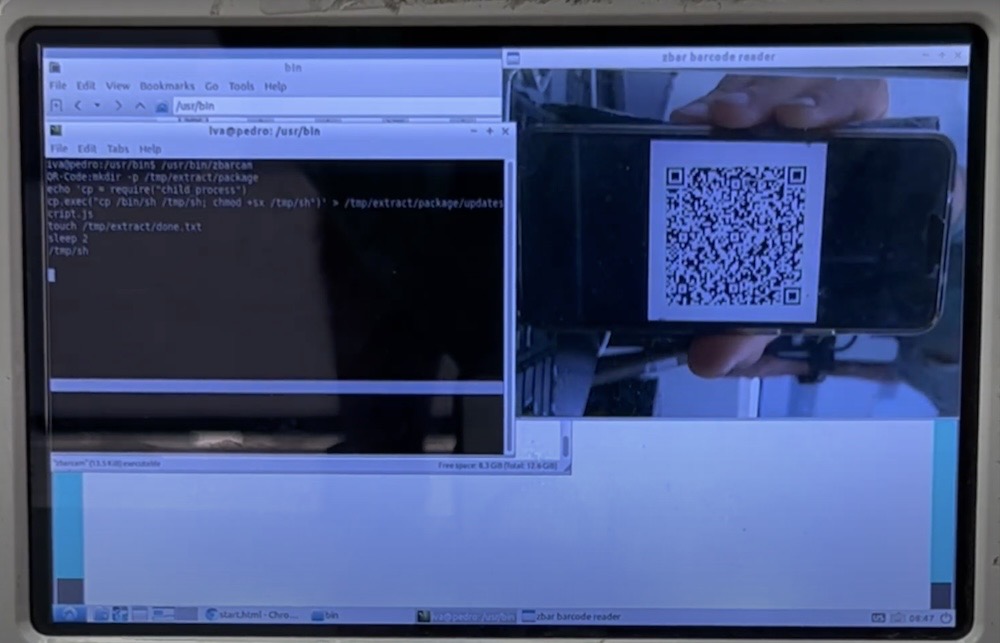
Hacking a Bitcoin ATM using a malicious QR code
IOActive: Researchers at IOActive found three flaws in a popular bitcoin ATM developed by Lamassu. On boot, the ATM's touch-screen display briefly allowed access to interact with the Linux window manager and a terminal window. To get full control, though, the friendly hackers used a malicious QR code (finally, a real-world example!) scanned in by the ATM to pop a root shell. Genuinely impressive stuff here. Lamassu fixed the bugs. But this isn't the first time IOActive busted into an ATM. The late Barnaby Jack famously hacked an ATM live on stage at Black Hat 2010 to spit out reams of cash.
Wall St. stock-lending tech downed by ransomware
Bloomberg ($): The hacking group LockBit claimed responsibility for a ransomware attack that targeted EquiLend, a financial tech firm that processes trillions of dollars of securities-lending transactions monthly. CNN reports that it could take "several days" before the company is back up and running, but the impact on the financial market has been "limited," per FS-ISAC, the financial cyber intelligence sharing group.
No evidence of HP CEO's claim that third-party ink risks hacks
Wired ($): If you missed HP CEO Enrique Lores' comments last week, the tech executive explained why the company is bricking printers that use third-party ink (read: printer ink is expensive and doesn't want you buying it anywhere else). Lores' claim was that "you can embed viruses in the cartridges." But HP later said there's no evidence of this kind of attack in the wild. Or maybe if there's such a concern, the argument is... that HP should just make more secure printers?
~ ~

~ ~
OTHER NEWSY NUGGETS
iOS 17.3 lands with anti-theft protection: If you haven't updated to the latest Apple software yet, go do that! iOS 17.3 lands with Stolen Device Protection, a feature that when enabled (so you have to switch it on) adds a biometric time-delay before it'll let you change certain device or account settings that normally might prevent the victim from getting their device or data back. The feature makes it significantly more challenging for a thief to use a stolen iPhone or iPad. The software update also lands with a fix for a WebKit zero-day under active exploitation, so there's your carrot and your stick. (via Apple, Wired ($))
Togolese journalists targeted with spyware: Speaking of exploitation of Apple devices, Reporters Without Borders disclosed this week that two Togolese journalists had their phones hacked by the Pegasus spyware, likely by the Togolese government (effectively a dictatorship), which is known to be a customer of NSO Group. The two journalists' phones were hacked until at least mid-2021, and they were also detained under spurious charges, amid fears that the Togolese government may be able to identify some of their sources. (via RSF, The Record)
Amazon fined for excessive workplace surveillance: French authorities have fined Amazon about €32 million ($34m) for the "excessively intrusive" surveillance of its workers. Per the BBC, the French data and privacy authority "found Amazon tracked activity so precisely that it led to workers having to potentially justify each break." Amazon broke GDPR as a result of this surveillance, the authority found. And that's how Amazon treats its own employees! One can only imagine what Amazon is capable of doing to its customers. (via BBC News)
U.K. councils report breach to regulator: The curious case of a cyberattack targeting three U.K. councils in Kent rumbles on. Canterbury, Dover, and Thanet councils continue to experience outages to their online services linked to an incident at EK Services, a partnership set up by the three councils some years back. Canterbury City Council said no customer data was accessed. But this week, my TechCrunch colleague @carlypage reported that the U.K. data protection regulator, the ICO, said it had in fact received a breach report from the three councils (as required within the 72-hour reporting window), suggesting there may have been a breach of resident data. We will see. (via TechCrunch)
No MFA on SEC's X? WTF? And now to a different regulator: the U.S. Securities and Exchange Commission said its X account was hacked (and used to share a fake tweet about bitcoin ETFs) because there was no multi-factor authentication on the account. The SEC explained in more detail that the MFA was suspended on the X account by X Support at the SEC's request following an account lock-out. A subsequent SIM swap associated with the phone number on the SEC's X account resulted in the account hijack. How the hackers got that number is a big question — but since Twitter (back when it was Twitter) had several leaks over the years that exposed millions of Twitter account usernames and associated phone numbers, the SEC's account phone number probably wasn't as difficult to get as some might think. (via SEC, BBC News)
~ ~
THE HAPPY CORNER
Ding, dong. It's happy corner o'clock.
If you haven't checked out the EFF's Field Guide to Police Surveillance, go take a look. Fantastic work here! The project, which debuted this month, explores a range of surveillance technologies and their impact — from license plate readers to CCTV, drones, facial recognition, and real-time location tracking. There's also a great interview on The Register about the project.
And, congratulations to @bartongellman who joins the Brennan Center as a senior advisor. Gellman is a Pulitzer Prize-winning reporter who worked on the Snowden stories back when (a decade flies by), wrote a book about it, and went on to write extensively about the ongoing threats to U.S. democracy. Per the Brennan Center, Gellman will "collaborate with Brennan Center experts on strategy for the pre- and post-election period, including public strategies to anticipate, prevent, and address autocratic initiatives in the next presidential administration."
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Puffin, who can be seen here closely monitoring for any backdoor attacks. You're doing great work, Puffin. Thanks to Khelsey S for sending in!

Send in your cyber cats! Email me a photo of your cyber cat (non-feline friends welcome!) with their name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
And that's it for this week! Thanks so much for reading. I'll be back next week with everything you need to know from the past seven days. Keep in touch by email if you have any comments, questions or feedback.
See you next?
@zackwhittaker