this week in security — january 29 edition
THIS WEEK, TL;DR
DOJ disrupts Hive ransomware gang after months-long hack
NPR: There was a little good news this week. U.S. and European authorities have dismantled the Hive ransomware group's infrastructure. It comes as the FBI had more than six months of secret access to Hive's backend database, in which federal agents siphoned more than 330 decryption keys from victims to get their files unlocked — hacking the hackers — but all unbeknownst to the ransomware gang. That helped save victims some $130 million in ransom payments. In the end, the feds found Hive's infrastructure sitting on a server in Los Angeles, allowing its seizure. Hive has stolen at least $100 million since June 2021, per CISA. But, the feds made no arrests in the Hive seizure. Could they return? (Probably.) That's in part why the U.S. government put out a $10 million bounty for information on Hive members. But the fact that Russia is now blocking access to the State Department's bounty website says everything, really.
More: Justice Dept. | BBC News | Bloomberg ($) | @PogoWasRight | @uuallan | @brett
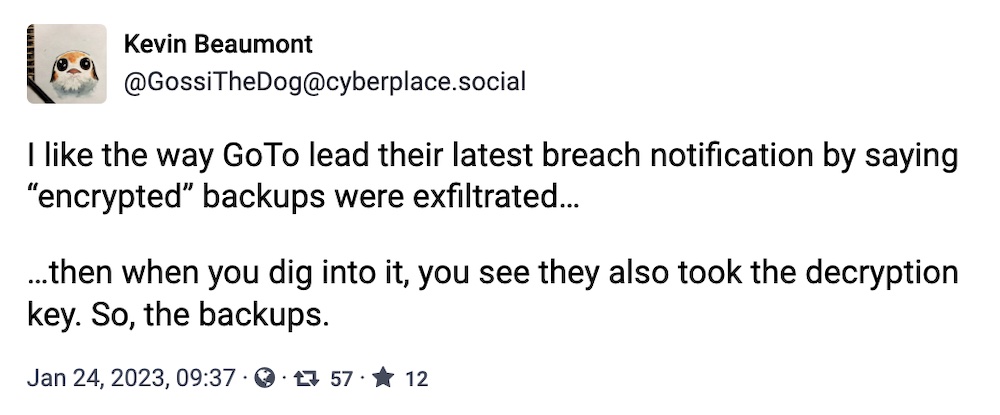
GoTo says hackers stole encrypted backups... and the encryption keys
GoTo: Totally normal stuff going on at GoTo, the company formerly known as LogMeIn, which might as well just be "log me out" at this point, given the company's catastrophic handling of its data breach. In a meager six-paragraph notice, CEO Paddy Srinivasan said that the intruders who broke into its shared cloud storage with LastPass, which it owns, and resulted in the theft of customers' encrypted password vaults, also took customer backups for its products Central, Pro, join.me, Hamachi, and RemotelyAnywhere — and the associated encryption keys. GoTo said it was notifying customers — and presumably telling them more than what was said in the notice, since the intruders got almost the lot.
More: TechCrunch | The Verge | SecurityWeek | @Barnacules
Britain sounds alarm on Russia-based hacking group Cold River
Reuters ($): The U.K. government is calling out a Russia-based hacking group dubbed Cold River, an information gathering campaign targeting journalists, government, politics, academia, and defense industries, and activists. Cold River impersonates targets using fake email addresses and social media. So far the hackers have targeted U.S. laboratories and the private emails of a former U.K. spymaster. It's similar in style to Iran's Charming Kitten, which uses similar techniques, and also noted by the U.K.'s National Cyber Security Centre. The NCSC said that U.K. victims are still in their "tens," but warned that the hackers are "ruthless" in pursuing their targets.
More: NCSC | BBC News | @pearswick
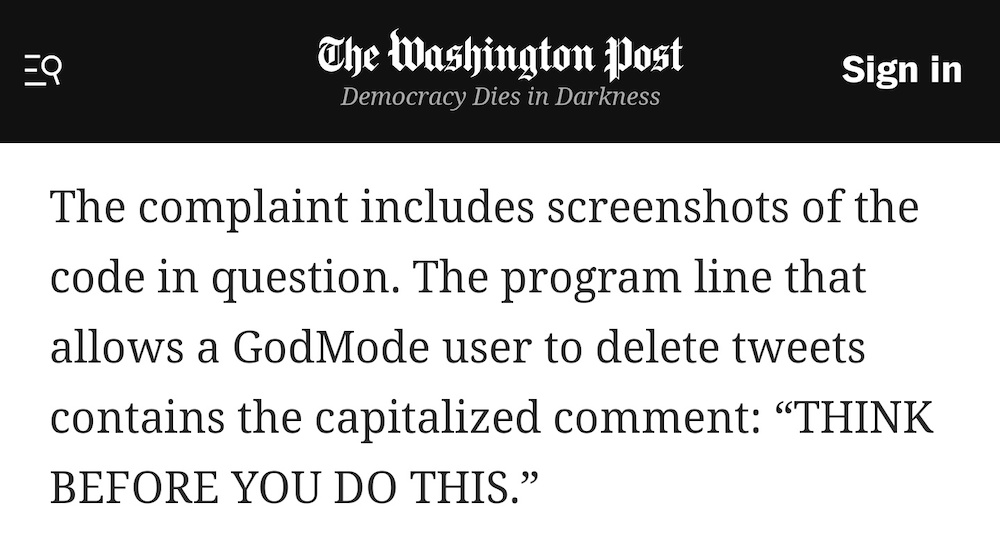
Ex-Twitter engineer tells FTC security violations persist after Musk
Washington Post ($): A new whistleblower has told the Federal Trade Commission that "any Twitter engineer" can activate an internal program previously called "GodMode," three months into Elon Musk's ownership. According to the Post, it's as simple as changing a line of code commented as "THINK BEFORE YOU DO THIS" and running it from a production system. Worse, there's no logging, the complaint said. Yes, that means in theory you could post cat pictures from the Pope's Twitter account, or worse, claim some awful event that dips the stock market or causes mass panic. Remember the fake tweets from 2018? Twitter might not be what it was, but its code still wields considerable power.
Background: Recode | More: Platformer | @deviantollam
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
An app flaw exposed the data of millions of Indian students
Wired ($): An app called Diksha, which was used by millions of students in India — especially during the height of the COVID-19 pandemic when schools across the country closed — was spilling the full names, email addresses and phone numbers of more than 1 million teachers, and other data on close to 600,000 students. That's because of a cloud server that wasn't protected with a password. EkStep, the foundation which develops Diksha, quickly took the unsecured data offline when reached by Wired.
Zendesk hacked after SMS phishing campaign
SecurityWeek: Zendesk, the company that provides customer service to small and big companies, was hacked. According to an email sent to Coinigy — an affected customer — Zendesk said several employees were targeted by an SMS phishing campaign (sounds like social engineering) between September 25 and October 26, 2022, and accessed unstructured data from a logging platform. Coinigy said in a blog post that some data may have been exposed by the breach. Given how quiet Zendesk has been on the incident, this might be one to keep an eye on.
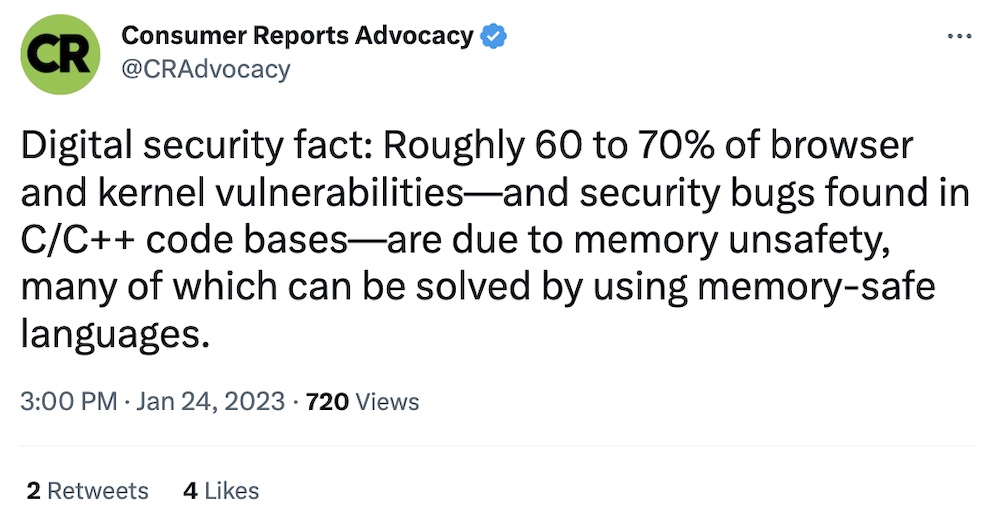
Why developers should move to memory-safe code
Consumer Reports: You might not think much about memory (see what I did there?) but actually memory-related vulnerabilities make up about one in six-to-seven browser and kernel vulnerabilities, such as buffer overflows (when memory spills over into other parts of the device's memory, causing leaks and security problems). That's because much of the world's most common code is built using memory-unsafe languages, like C and C++. This excellent report by Consumer Reports, authored by the esteemed @yaelwrites, looks at how developers can avoid these common security flaws by using memory-safe languages, like Rust (which Wired ($) did a great deep-dive on recently), as well as wider advocacy for using safer code. I'd really recommend reading this short, but important report.
FBI says North Korean hackers behind Horizon cryptocurrency theft
FBI: The FBI really wants you to know that its investigation found that APT38 and Lazarus Group — two North Korean state-backed hacking units — were behind the theft of $100 million in cryptocurrency stolen from U.S.-based web3 company Harmony's Horizon bridge (which lets users transfer cryptocurrency from one blockchain to another). Just one thing: pretty much everyone else in the private sector pointed the blame at North Korea months ago. Still, better that we got there in the end, even if it was at the speed of Internet Explorer.
Inside TikTok’s proposal to address U.S. national security concerns
Cyberscoop: TikTok continues to remain a hot button issue in Washington (and further afield) as lawmakers and states look to block TikTok on government networks fearing it could become some viral vehicle for spreading Chinese propaganda. Frankly, it's a bit of a hot mess and you'd be forgiven if you hadn't kept up to date with whether TikTok poses a national security threat. (It has cat videos and recipes; it seems fine for now.) But if you are interested in the ins and outs of what's going on with the viral video giant, Cyberscoop has a... tick-tock of events to date, and how TikTok plans to stay in the U.S. and not be banned.
A new global inventory of global government spyware
Carnegie Endowment for International Peace: Government spyware seems like it's everywhere these days. Now there's a spreadsheet tracking the use of spyware by governments across the globe. It shows which government bought which spyware, when, and from whom. It's a pretty handy guide; add it to your bookmarks.
~ ~
OTHER NEWSY NUGGETS
GAO to everyone, please stop ignoring us: The Government Accountability Office, aka GAO, said in a report this week just 40% of the cybersecurity recommendations it's issued over the past decade-plus have been implemented by federal agencies. The GAO called out a lack of a government cybersecurity strategy, which, granted, is on the way — plus shortfalls in hiring. The GAO's job is, among other things, to identify flaws in cybersecurity policies and find solutions, and over the years has shown to do a pretty good job of holding the government accountable. (via Cyberscoop)
Riot Games hacked, ransom demanded: The game maker behind League of Legends and Teamfight Tactics was hacked, and source code — including for a legacy cheat system — was stolen by someone who demanded $10 million to not release the stolen cache of data online. That leaked source code could be a major problem for the company, which said in a tweet thread that it wouldn't pay, given that it could help game cheaters evade its anti-cheat software. (via Motherboard, TechCrunch)
NSO "committed" to spyware, as governments probe: Yaron Shohat, the new head of the embattled spyware maker NSO Group, went to Washington this week — presumably to try to get his company off the U.S. government's denylist. In an interview with the Wall Street Journal, Shohat said little new — but did say that NSO had terminated 10 government customers for misusing its zero-click phone spyware, Pegasus. Still, the company said it's "committed" to selling Pegasus, even as global governments continue to breathe down the company's neck. @jsrailton has tweets. (via Wall Street Journal ($))
Dutch hacker has Austria's data: So, not to freak anyone out in Austria, but it looks like a Dutch hacker has your data — though basic, but everyone's. Dutch police arrested the 25-year-old hacker in his apartment in Amsterdam in November after offering "the full name, gender, complete address and date of birth of presumably every citizen" in Austria. The hacker also put "similar data sets" from Italy, the Netherlands, and Colombia for sale. "The police did not elaborate on the consequences for Austrians' data security," Reuters reports. At least nobody needs new fingerprints... (via Reuters ($))
~ ~
THE HAPPY CORNER
Now that we've gotten through the news, enjoy the happy corner. This week we've got a couple of things:
Last week I flagged Apple's new end-to-end encrypted cloud feature, dubbed Advanced Data Protection. It encrypts all your cloud-stored data, including photos, notes and your iCloud Backup (finally) — and it's now available worldwide with iOS 16.3. It is, overwhelmingly, a good thing. Just one problem — it's not the easiest thing to figure out or troubleshoot. Luckily, @tarah has an excellent blog post explaining the quirks in ADP's setup — and how to navigate them. (via @runasand)
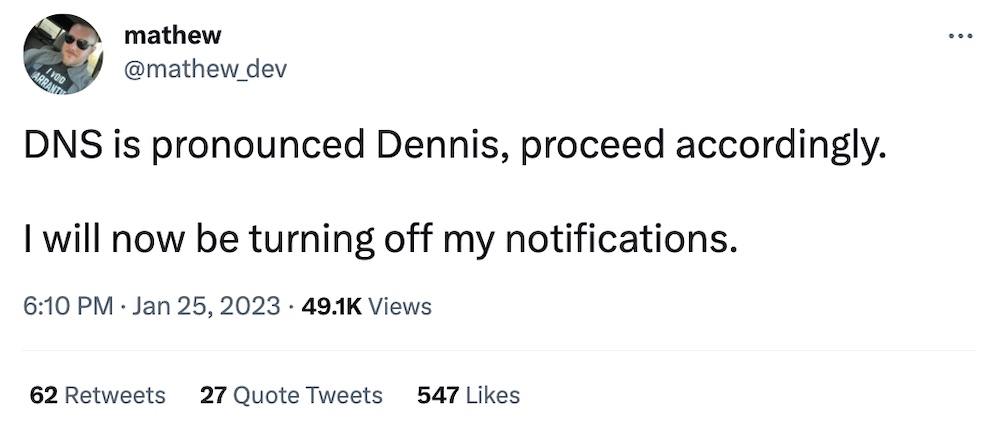
And finally. I had to see this, so now you do, too. Sorry, it's only fair.
If you have good news you want to share, get in touch at: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Stone Barrington, a 9-year-old rescue with, might I say, the most piercing eyes.... oh, he's asking for my passwords? Sure... and my credit card? Here it is... many thanks to Joe M. for sending in! And I'll get my Social Security number to him later...

Send in your cyber cats! (You can send in your non-feline friends too.) Email me a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
Thanks for reading! If you have any feedback, stories or other interesting things from the week, you can always drop them by email or in the suggestion box. It's always lovely to hear from readers (and their cyber cats, of course).
Have wonderful weeks, and see you next Sunday.
—@zackwhittaker