this week in security — january 30 edition
THIS WEEK, TL;DR
Hactivists say they hacked Belarus rail system to stop Russian military buildup
Ars Technica: Hacktivists in Belarus said this week that they had infected the country's state-run railroad system with ransomware, and will only give up the decryption key if Belarus president Alexander Lukashenko stops aiding Russian troops ahead of a possible invasion of Ukraine. The Belarus Cyber Partisans tweeted that they had locked systems to disrupt the railroad to prevent, in part, Russian troops from using the railways from being used to mass forces on its border with neighboring Ukraine. Screenshots showed privileged access from inside of the private networks of the Belarus Railway. On the front-end, the railroad warned of delays and unavailable tickets — and more disruption. @brettcallow said ransomware has the potential to be almost as effective for "cause-based extortion" as it is for financial extortion. Resistance-as-a-service?
More: Wired ($) | Cyberscoop | SentinelOne | @HowelloNeill tweets

These apps sold data on people's location to a controversial data broker
The Markup: Incredible reporting from The Markup this week after it identified over 100 apps that sold granular location data to a controversial data broker called X-Mode in 2018-2019. The apps included LGBTQ+ dating apps, as well as Muslim prayer apps — which was initially reported by Motherboard. That granular location data was sold to the U.S. military contractors, putting those app users at risk of surveillance. This is the first time that the full range of apps using X-Mode has been disclosed. @alfredwkng has a good tweet thread. In related news this week, family location sharing app Life360 — one of the largest sources of raw location data — agreed to stop selling the precise location data it collects, following The Markup's reporting.
More: The Markup | The Conversation | @mguariglia
White House attempts to strengthen federal cybersecurity after major hacks
CNN: It took more than a year after the discovery of mass intrusions across the federal government by Russian spies (SolarWinds, anyone?) — but we did it, Joe! — we got a new cybersecurity strategy to better protect federal agencies from outside threats. The new strategy seeks to apply zero trust principles across the federal government. Zero trust, if you recall, is where no user or computer is inherently trusted and continuous checks — like multi-factor authentication — are needed. The policy also does away with a long-time pain point — special characters and regularly rotated passwords. (Finally!) Some who've been on the zero-trust inside track for, well, ever, could barely contain their excitement.
More: White House | ZDNet
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Dark Souls PC servers down amid hacking fears
BBC News: Popular video game Dark Souls 3 was taken offline after reports of an exploit that could take control of a gamer's PC. The alert came after a user was hacked and their stream interrupted by a pop-up Powershell command that opened a text-to-speech tool on the player's PC to tell them, predictably, not very nice things. The game took its online player-to-player service offline while it investigates, but Xbox and PlayStation users are unaffected.
The battle for the world's most powerful cyberweapon
The New York Times ($): New details have emerged about efforts by the FBI to buy and deploy the controversial hacking tool, Pegasus. The feds secured a $5 million contract to deploy Pegasus from a building in New Jersey but the feds wanted to spy on U.S. phone numbers, which Pegasus couldn't do. NSO's U.S. subsidiary presented Phantom, a version of Pegasus that works in the U.S., which was previously known long before the Times' report. But the deal went flat in the end, in large part because a slew of reports as part of the Pegasus Papers derailed the effort. As of now, the Pegasus system in New Jersey remains dormant. (Minus ten points for the unnecessary and inaccurate use of "cyberweapon" in the headline.) The Times' report comes in the same week that Finland confirmed that diplomats with its Foreign Affairs ministry were hacked with Pegasus.
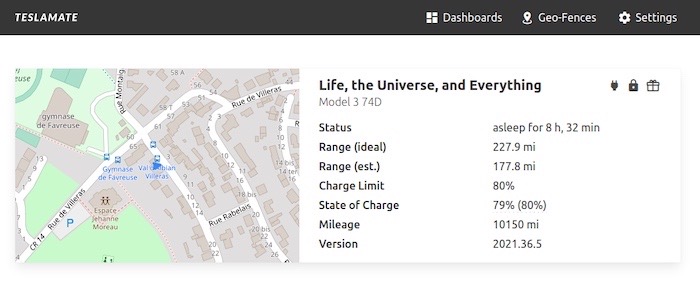
How I got access to 25+ Tesla’s around the world — by accident
David Colombo: A couple of weeks ago I flagged an early story about how a security researcher got remote access to dozens of Teslas. Turns out it was because of a flaw in third-party software, Teslamate, which many Tesla owners were running on their own internet-exposed systems. Those exposed systems also leaked a vehicle's API keys — and with those keys, you can remotely open the doors and windows, honk the horn, start the car — and access a ton of Tesla's data within, including driving histories and location data. The researcher @david_colombo_ followed the disclosure playbook down to a tee, notified Tesla, got thousands of API keys revoked, and published details on his blog once the issue was resolved.
Exploit broker looks for zero-days in Outlook and Thunderbird email clients
The Record: Zerodium announced plans this week to pay $200,000 and $400,000 for zero-day exploits in Mozilla Thunderbird and Microsoft Outlook, respectively, two of the most popular email clients today. Some have noted that the controversial zero-day broker isn't just looking for RCEs to access the target's computer, but also the emails in the client itself. Incidentally, SpiderLabs this week revealed a security bypass flaw in Outlook, fixed last year, that allowed some emails to slip through Outlook's security defenses by using a specially crafted URL.
~ ~
OTHER NEWSY NUGGETS
ID.me backtracks on claims it doesn't use powerful facial recognition tech
Cyberscoop: Last week there was focus on ID.me, a company that will soon be the identity provider to the IRS, meaning millions will need to enroll with ID.me before they can access their online tax services. The CEO this week backtracked on earlier claims, now saying that the company uses 1:many facial recognition, which is where you compare a face to a large database of known faces, which can be a huge security risk. Internal Slack messages obtained by Cyberscoop also show that the service uses AWS Rekognition, which critics have previously slammed for having gender and racial bias.
Hackers target Canada's foreign ministry in cyber attack
CNN: CNN reports wide disruption to internet services at Canada's foreign ministry, confirmed by Ottawa, though "critical services for Canadians" were not affected. It's not clear what the attack is, exactly. This week the LockBit hack-and-publish ransomware gang claimed it stole data from France's Ministry of Justice, according to ZDNet. The ministry reportedly confirmed the attack, and LockBit has about 8,000 stolen files advertised.
This NFT on OpenSea will steal your IP address
Motherboard: NFTs don't do much — they're mostly just digital art. But art doesn't generally steal your IP address when you view it — and neither do NFTs. But some new NFTs are being used to collect IP addresses because OpenSea, an NFT marketplace, allows vendors, or potentially attackers, to load custom code when someone views an NFT listing. OpenSea, like most websites, will log your IP address, but not generally users of the sites themselves. That can lead to individuals being able to collect a viewer's coarse location — or their IP address used to dig up other data from other sites and breaches. @josephfcox explains how the IP address-stealing NFT works. (It reminds me of the time growing up on the internet with custom HTML on MySpace and eBay. Fun times!)
Safari flaws exposed webcams, online accounts, and more
Wired ($): A set of macOS vulnerabilities — fixed by Apple last year — exposed Safari tabs and other browsing settings to attack, potentially allowing malicious hackers access to your online accounts, microphone, or webcam. The bugs were found in ShareBear, a behind-the-scenes app that Apple uses for sharing iCloud documents. Because the relationships between Safari, macOS and iCloud are trusted, a researcher found an attacker could revisit a previously shared file and swap it with a malicious one — without iCloud knowing the difference. That can grant a hacker access to the user's Mac — and their files stored locally. The bug was severe enough for Apple to dole out a massive $100,500 bug bounty prize.
~ ~
THE HAPPY CORNER
This week everyone seems to have Wordle fever. Well, almost.
And, check out this super l33t hacking tutorial video. (I almost lost it at "Shoutout to NSA".)
If you want to submit good news from the week, reach out! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week is a two-for-one cybercat special. Meet Marci and Melly, who are taking a break from a day of threat (and mice) hunting. A big thanks to Martin P. for the submission!

Keep sending in your cyber cats (or their friends). Drop me an email here with their name and photo, and I'll make sure they're featured in a later newsletter.
~ ~
SUGGESTION BOX
That's all for this week. Same time next? As always the suggestion box is open as always, or feel free to drop any feedback at this@weekinsecurity.com. Have a great week.