this week in security — january 5 2025 edition
Welcome back to ~this week in security~ and a happy new year! Phhrrhbbttt! 🥳

...alright, let's get on with it. Commence the news!
~ ~
THIS WEEK, TL;DR
Chinese hackers compromised Treasury's sanctions office
Washington Post ($): Happy New Year to all — except, maybe, the U.S. Treasury's sanctions office, the Office of Foreign Assets Control (or OFAC), which was recently hacked by China government-backed hackers, per U.S. officials. The hackers used a breached private key owned by BeyondTrust, which provides remote access and identity services to big companies and government departments (like the Treasury), to gain remote access to Treasury employee workstations and unclassified documents. The hack was disclosed on Dec. 30 in a letter to lawmakers, attributing the hack to China, in the same week that OFAC sanctioned a major Chinese tech company, Integrity Tech, for its apparent role in running the botnet behind Flax Typhoon's hacks targeting U.S. systems and critical infrastructure. So maybe that's a clue why China hacked OFAC to begin with..! This is the latest cyberattack by China targeting the U.S. in recent months, so don't think this is settling down any time soon. The WSJ ($) has a great long-read on how China got this far; and Bloomberg ($) looks at why Guam has become a major U.S. focus of Chinese hacking efforts.
More: BeyondTrust | Wired ($) | Treasury | TechCrunch | The Guardian | NBC News
U.S. Army soldier arrested in alleged AT&T, Verizon extortions
Krebs on Security: U.S. prosecutors have arrested a serving U.S. Army soldier for his alleged part in the mass thefts of call records — thought to be from AT&T (via the cloud computing company Snowflake) and Verizon last year. The bare-bones indictment charges Cameron John Wagenius with two criminal counts, but says nothing about the actual case itself. Krebs, who first reported the indictment, spoke with Wagenius' mother who confirmed some details about her son's links to the also-indicted Snowflake hackers. The indictment comes soon after Krebs pieced together a digital trail of evidence pointing to Wagenius as another person who was likely behind the telco hacks. No confirmation from the authorities yet beyond Wagenius' arrest, but all the reporting so far suggests that's probably just a matter of time.
More: Indictment [PDF] | @briankrebs | @screaminggoat
Check if you ran any of these 33 malicious Chrome extensions
Ars Technica: Jussstt before Christmas, dozens of Chrome extensions were discovered to have been hacked to push out malicious updates that were capable of stealing cookies, session tokens and passwords from users' browsers. (That's a major problem since extensions generally auto-update in user browsers, with few checks to make sure they're not malicious.) One affected company included Cyberhaven's (which I mentioned in last week's dispatch), a security company that provides its Chrome browser extension to 400,000 users — mostly employees of corporate customers. Turns out the hacking campaign was largely directed at the theft of Facebook user account credentials for ads, per Secure Annex, which did the analysis. It looks like the campaign dated back at least 18 months, and may have stolen data on some 2.6 million devices. There's also a list of affected extensions here... Browser extensions can be a major risk. The fewer you have, the better.
More: Secure Annex | Bleeping Computer | @tuckner
~ ~
THE STUFF YOU MIGHT'VE MISSED
Tangem fixes bug that exposed seed phrases
Cointelegraph: Cryptocurrency wallet provider Tangem has fixed a bug that saw the company mistakenly log some users' private wallet keys. The fix came after Redditors called foul and Tangem, for its part, could have handled its communications better. Tangem provided a response and said about 0.1% of users were affected. Logging is great, but just make sure you're not logging sensitive data that you really don't want to see.
A look back at Mac malware in 2024
Objective-See: Top Mac researcher @patrickwardle published an annual round-up of the state of Mac malware last year. It's an interesting look at what's working in Mac malware (including info-stealers capable of pinching your passwords). Keep an eye out for fake apps or any untrusted app; it seems like this is a major delivery mechanism for backdooring access.
Vehicles amass huge troves of sensitive data
Washington Post ($): An exploding Tesla Cybertruck in Las Vegas this week led to discussion about the amount of data that vehicles collect and store, which can be used by police or investigators (counterpoint: or also shared with third-parties, or lost and stolen in data breaches). Most modern vehicles collect huge amounts of data, including precise location records, speed, and often any data from a phone connected to the car. It might sound obvious, but just like your phone, your car is a constant tracker of where you go (which can infer what you do or who you see).
2024 in CVEs show XSS bugs were the most reported
Jerry Gamblin: And back again this year is @jgamblin's review of recorded CVE vulnerabilities. During 2024, some 40,009 CVEs were published, up 38% from the year prior, with granular analysis on which days and months were most popular for filing CVEs, and more. An interesting note is that the most common type of vulnerability, aka CWE (or common weakness enumeration) shows CWE-79 — the fancy designation for web-based cross-site scripting (XSS) vulnerabilities — was by far the lead over others. Fix your web code, people!
~ ~

~ ~
OTHER NEWSY NUGGETS
U.S. teachers, firefighters paying for spyware firm: A deal to get Israeli spyware maker Paragon into the hands of U.S. private equity giant AE Industrial partners for some $500 million was funded, in part, from several retirement funds for American teachers, police and firefighters, per Israeli news outlet Globes. Can't help but imagine plenty of folks not being particularly thrilled about their pensions being used to fund spyware companies. (via @vaspanagiotopoulos, @evacide)
Pony up your ID for porn: As of today, some 17 out of the 50 U.S. states (mostly across the U.S. south) have age verification laws that require adult websites to verify the ages of visitors before entering. The result has been some of the bigger sites — like Pornhub — blocking access entirely to users in those states, arguing that giving your ID every time you access a restricted site "will put children and your privacy at risk." Clearly it's not a great idea to have a huge database of people's identity information tied to access to adult websites. Something, something... huge target for extortionists? (via 404 Media ($))
Hackers start leaking data on Rhode Island residents: The state government of Rhode Island said the hackers behind a recent ransomware attack on its state systems for residents' social services programs and benefits have leaked some of the data online. The state is urging residents to take action to protect themselves after residents' ID documents and personal information was stolen; around 650,000 people use the state systems that were attacked. Special shoutout to Deloitte, the govtech contractor who set up and managed the system that got hacked, which by the way made an eye-watering $67 billion in revenue during 2024 but couldn't secure a website. (via Rhode Island, The Record)
Tenable CEO Amit Yoran dies: Amit Yoran, the chief executive of security firm Tenable, passed on this week weeks after taking a leave of absence in December as he battled cancer. Yoran was 54, and widely acclaimed across the cybersecurity industry. (via Tenable, CNN)
~ ~
THE HAPPY CORNER
New year, same old happy corner. Welcome once again! (Sorry about all the glitter everywhere.)
To the lucky folks with data protection laws: Get spammed? Don't get mad, get even. This is one way to find out how they got your data to begin with.
This year brings a whole new edition of What Can 'Doom' Run On? and we're in for a treat. @rauchg built a Doom-CAPTCHA that's capable of verifying you're human by playing the age-old classic to take out at least three enemies (before they get you). I absolutely love this.
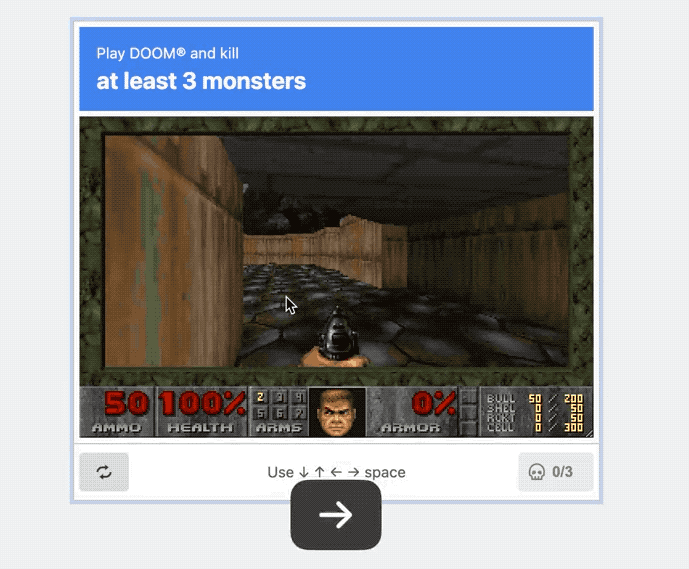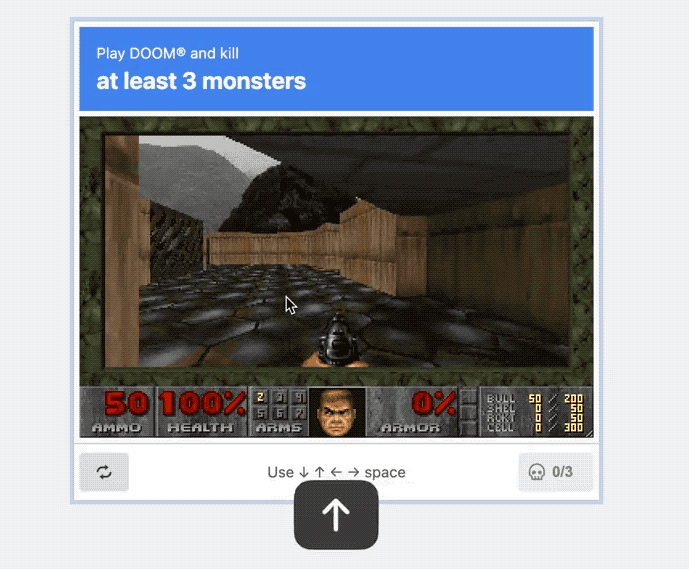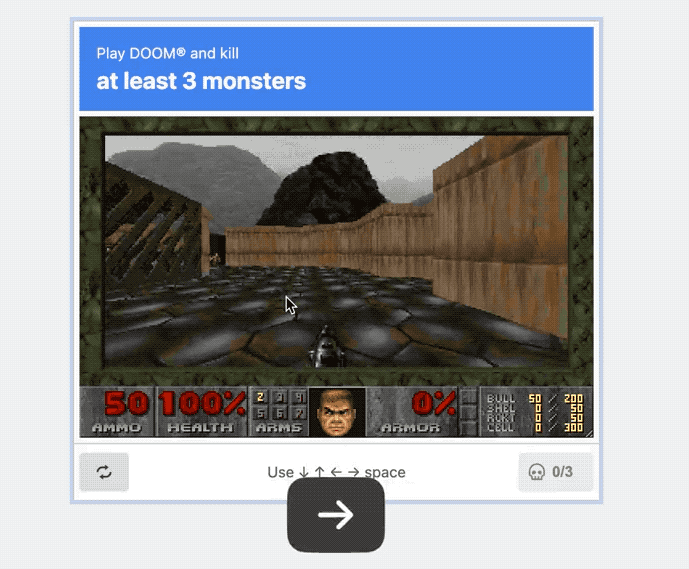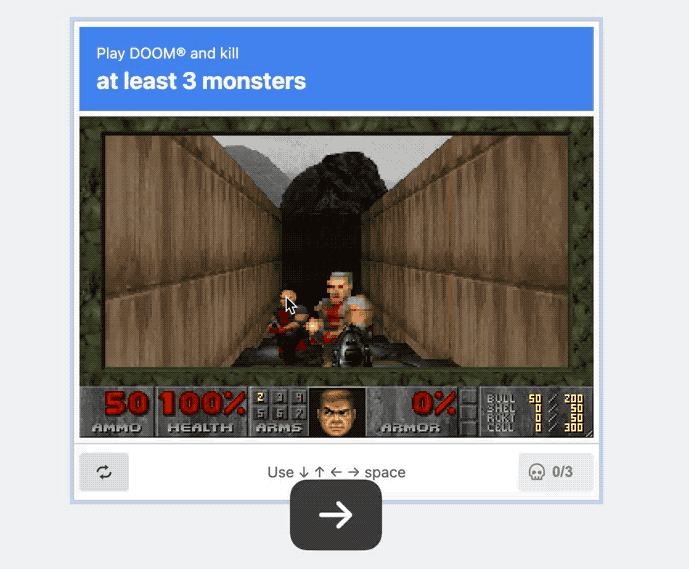
And lastly, this week. For so many folks catching up on their emails over the holiday, this is absolutely a mood.

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's (and this year's first!) cyber-cat-pup is Terrence, aka the Terminator, whose human tells me that this is his daily "Stop staring at screens" pose, which becomes a headbutt if not actioned within two minutes. Time to play! Thanks so much to his human Andrew L. for sending in!

New year, new plea: send in your cyber cats! (or a non-feline friend). You can email them in at any time with their name and a photo, and they'll be featured in an upcoming newsletter. Sent in before? Would love an update!
~ ~
SUGGESTION BOX
And that's it for this week, thanks for tuning in. Hope you had a good new year! I'll be back next week with the usual drop from the week.
If you want to drop me any feedback, please do — it's really lovely hearing from you.
From a chilly U.S. east coast, I'm out for now.
@zackwhittaker