this week in security — january 7 edition
THIS WEEK, TL;DR
Ransomware attacks up in 2023, experts call for ransom payments ban
Emsisoft: Happy new year to everyone except ransomware gangs, which during 2023 battered schools, governments and hospitals across the United States. Statistics show that some 321 (known) ransomware attacks happened last year and the situation is getting worse, with little intervention from lawmakers or meaningful action by the federal government. But there is one option left: "The only viable mechanism by which governments can quickly reduce ransomware volumes is to ban ransom payments," writes Emsisoft's @brett, who alongside @uuallan and @gossithedog say it's time to ban ransomware payments. "Ransomware is a profit-driven enterprise. If it is made unprofitable, most attacks will quickly stop." The argument is that a ban is the "safer" option, when the alternative is continued and ongoing widespread disruption to public services that can have devastating impact on human life. While not a perfect solution, expect a huge kickback from the billion-dollar cyber insurance industry, which stands to lose a lot. But also don't expect the government to stop sitting on its hands any time soon. (Cue The Simpsons episode: "We've tried nothing and we're all out of ideas!")
More: The Register | ITPro | @uuallan | @brett
Orange Spain hit by three-hour outage after account takeover
The Record: Hackers downed about half of Orange Spain's traffic for several hours after taking over the cell giant's RIPE NCC account. RIPE is like the phone book of the internet. Using a password stolen by an info-stealing malware, the hackers broke into Orange Spain's RIPE panel and scrambled the company's traffic routing, causing downstream outages. Orange Spain quickly reverted the changes after wrestling back access. Turns out RIPE admin panels are accessible from the internet and don't always have MFA enabled. RIPE confirmed an intrusion to one of its accounts and said that it was working to expedite the use of MFA. Until RIPE gets a hold of its security, we might expect more of these incidents to happen. Great post-mortem on the incident by DoublePulsar, as always.
More: SecurityWeek | RIPE | @gossithedog thread
Britain wants new surveillance laws, including blocking security updates
Politico EU: Britain, the former European nation state, has some of the most far-reaching surveillance laws in the democratic* (*terms and conditions apply) world, but is looking to expand those powers to make it easier for its spy agencies to snoop on people's internet browsing and messages. New legislation specifically looks to prevent "technical updates that might impede information-sharing with U.K. intelligence agencies." Yes, the U.K. government could decide to block product features like end-to-end encryption and other privacy technologies if lawmakers think those features would make it more difficult to snoop on people. This, said from the government that relies on WhatsApp (and hypocrisy), one can't help but see this as an incredible short-sighted self-own.
More: Just Security | BiometricUpdate
~ ~

~ ~
THE STUFF YOU MIGHT'VE MISSED
School leader apologizes after kid monitoring software 'inundated' staff with alerts
Lawrence Journal-World ($): Gaggle, a child surveillance software system that uses AI to monitor keywords, is under fire in Kansas after the software "inundated" staff with notifications, alerts and other false positives. One notification triggered a brief lockdown, even though a threat had not been made. According to the school district's superintendent, one of the problems with the alert system is that "the sheer number of Gaggle alerts has infringed on the personal time of staff," adding that "notifications that didn’t require urgent action were often being sent to district personnel during their time off work." Worse, it turns out that the school board approved the use of the software but didn't fully scrutinize it. Very messy.
Mandiant says X account, protected by 2FA, was hijacked
Mandiant: Incident response giant Mandiant found itself responding to its own incident this week after its X account (formerly Twitter) was hijacked and used to spread a crypto scam. Mandiant said it got the account back in the end but didn't say how or why it was taken to begin with — only that an unspecified type of 2FA was used on the account. Cue friendly hacker @RachelTobac with some analysis. Could it have been a stolen session token or social engineering, or a malicious insider at Twitter X? Who knows. Compounding the theories is that Mandiant wasn't the only company whose X account was hacked this week; CertiK also said its X account was briefly taken over to spread a similar crypto scam, though it's not clear how.
2023 in CVEs: A year in review
Jerry Gamblin: @JGamblin is back with a 2023 year in review of CVEs vulnerabilities. Gamblin dives into the data and pores over trends. The way we're going, 2024 could be a record year for vulnerability disclosures. If you're curious, Gamblin also reads the tea leaves for 2024.
EFF urges Pennsylvania top court to nuke keyword search warrants
EFF: Geofence warrants are basically dead, but keyword search warrants are still very much in play. Instead of police dumpster-diving Google's databases for the location data of anyone who was nearby to a crime at the time it was committed, police can also use this same "reverse" warrant technique by demanding Google turn over records on who searched specific keywords. That could be a particular address or name before a crime was committed, but the EFF notes that these dragnet warrants violate the privacy of entirely innocent people who have no involvement whatsoever. Colorado's top court has already upheld one case involving keyword search warrants (boo!), so it's eyes on Pennsylvania — and potentially ultimately up to the U.S. Supreme Court.
~ ~
OTHER NEWSY NUGGETS
https://keybase.io: No, it wasn't just you: Keybase was down briefly earlier this week after a certificate authority expired, resulting in the app grinding to a halt and preventing existing users from doing anything. Keybase told users to update their apps to get it working again. "Short version, the only way this can be fixed would be to build and release new client executables," said @kg4zow. (via GitHub, Keybase)
Software cyberattack knocks museums offline: The Museum of Fine Arts Boston, the Rubin Museum of Art in New York, and the Crystal Bridges Museum of American Art in Arkansas were among the institutions confirming that their systems were hit by outages caused by a cyberattack on gallery service provider Gallery Systems. The New York Times ($) has a report that suggests the incident may have been ransomware ("computers running its software became encrypted and could no longer operate"). Gallery Systems hasn't commented, but told its customers that it notified law enforcement and brought in incident response. Some museums are unaffected as they host their own databases. (via Artnet, @zacharyhsmall)
Facebook's gross new way to track what you click: The data hungry Facebook records everything that its mobile users click on through its app by way of Link History, a "feature" (heavy quotes here) that saves a copy of the link you've tapped on Facebook's servers. Facebook has always known what you tap and click on through its apps and sites, so this isn't new per se, but it is supremely gross and you should opt-out before deleting the app altogether and hurling your phone into the nearest body of water. Only half-kidding. (via Gizmodo)
Wickr switches off the lights: The Amazon-owned end-to-end encrypted messaging app Wickr is no more. Amazon pulled the plug on the app this week. 404 Media looks back at the app, and how it was ultimately relied on by government agencies (and criminals). Cryptographer and early Signal developer @fj looked back. (via 404 Media)
23andMe tells victims it's their fault their data was breached: Genetic testing giant 23andMe recently had a huge data breach that allowed hackers to break into about 14,000 accounts using re-used passwords and subsequently scrape genetic and personal data on close to seven million 23andMe users. But 23andMe told customers suing the company that this was the users' fault, not 23andMe's. Lawyers representing 23andMe said "users negligently recycled and failed to update their passwords following these past security incidents, which are unrelated to 23andMe." But the lawyer for the customers said 23andMe is "shamelessly" blaming victims, and doesn't account for the millions whose accounts weren't actually compromised. The full letter is quite vile. 23andMe, everyone! (via TechCrunch, DocumentCloud)
Last-minute deal dodges landmark ransomware 'warlike' court case: Merck struck an eleventh-hour settlement with three insurance giants saying the court case is off — on the eve before oral arguments were set to begin. Merck claimed it was entitled to about $700M in claims after the NotPetya cyberattack (later attributed to Russia) crippled Merck's systems back in 2017. The insurers waived responsibility because of a clause waiving responsibility for "acts of war." Unsurprisingly, big businesses and cyber insurers wanted the court to uphold the case because, well, money — that's why. What exactly is defined as an act of war as it pertains to the cyber realm remains an untested question for now. (via Bloomberg Law ($))
~ ~
THE HAPPY CORNER
New year, same happy corner.
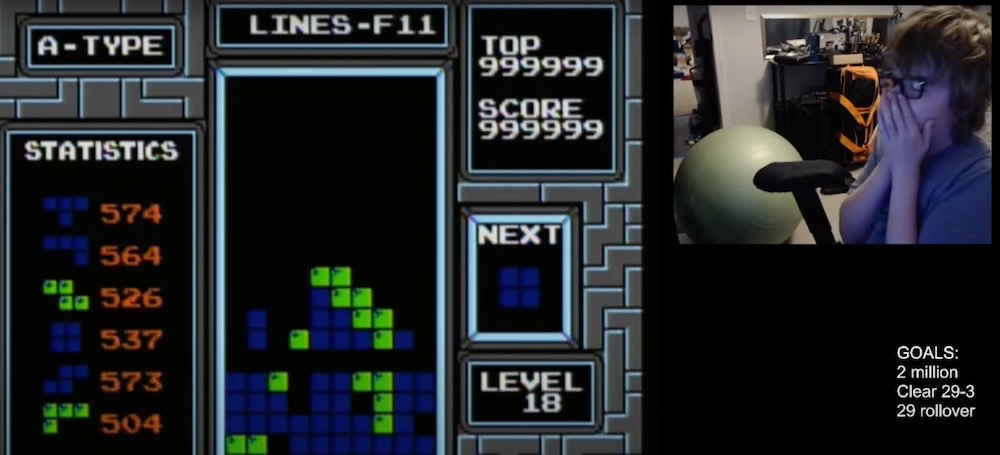
An Oklahoma teenager is the first person known to have beaten the classic video game Tetris, some three decades after it was first released. 13-year-old Willis Gibson posted a video to his YouTube of the moment he reached the maximum score that caused the game to crash — the so-called "kill screen." Major congrats to this kid, I bet there are adults who are in absolute awe of this accomplishment. You have to watch the video (about 38-mins in): the kid's reaction is absolutely priceless; even this grumpy reporter welled up a bit.
Regular reminder about Lockdown Mode on Apple devices, the security feature aimed at blocking spyware and other cyberattacks. While the security mode limits certain Apple apps, in the words of @lhn, Lockdown Mode is "surprisingly usable." Wired ($) dives in more.
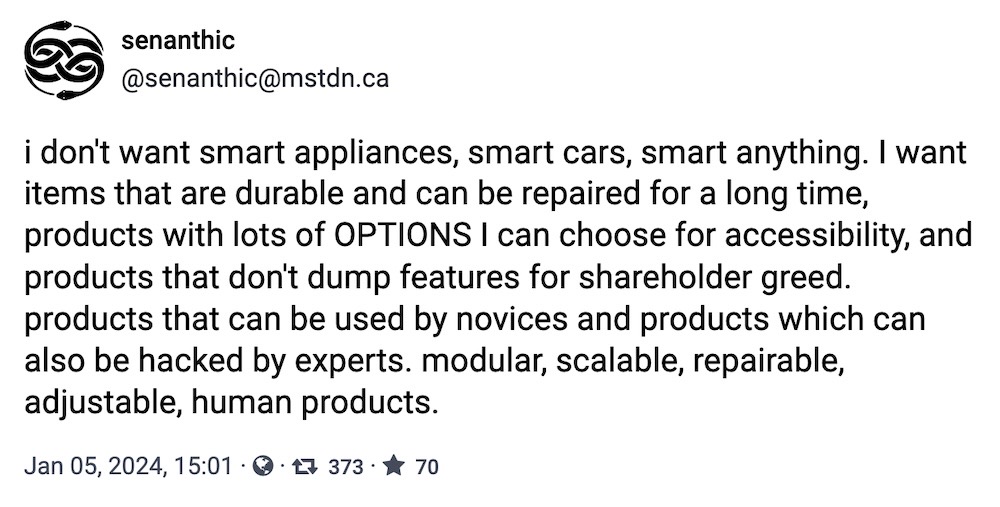
And finally, utopia in a toot. I'd pay good money for a new fridge, dishwasher... car... without a Wi-Fi connection.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet this week's (and 2024's first) cyber cat, Mister, whose human tells me that he has his CCP certification, a Certified Chonk Pussycat. Look at that belly fuzz, very handsome. Many thanks to Kara C. and David S. for sending in!

Send in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with their name and photo and they'll feature in an upcoming newsletter.
~ ~
SUGGESTION BOX
Many thanks for reading the first edition of the year! It's good to be back in the new year. Get in touch with me by email as always if you have any comments, feedback (or cyber cats you want to share!).
Back next week,
@zackwhittaker