this week in security — july 10 edition
THIS WEEK, TL;DR
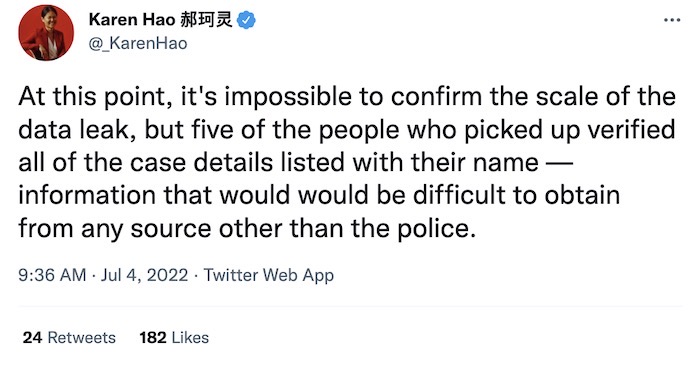
A vast cache of Chinese police files for sale after alleged hack
The Wall Street Journal ($): A wild story — if proven true — of the sale of a Shanghai police database swiped from an Alibaba cloud server after an alleged hack, or according to CNN, a possible data exposure that lasted for more than a year. The database has about 1 billion records, and is advertised as 23TB for 10 bitcoins, or $200,000. The seller provided a sample of 750,000 records, and both the WSJ and CNN verified that at least some of the data they checked with supposed victims was authentic. The alleged police database looks real, even if the seller's motives aren't known. The records contain personal information and detailed police reports from the serious to the mundane — like using VPNs to post critical comments on Twitter about the government, which is banned in China. China has already started to censor news of the leak on social media channels. This would make it one of the largest data breaches in history.
More: CNN | The Register | @zeyiyang | @mayhemdayone
Hotel giant Marriott hacked...again
Databreaches.net: Marriott has been breached — again. Turns out the ironically-named "Group with No Name" exfiltrated 20GB by tricking an employee into giving them control of a hotel computer. Marriott said it was notifying around 300-400 people of the incident, which allowed the unnamed group (or named, it's like Schrodinger's hackers here) to make off with credit card numbers and other internal files. Marriott was hit by a massive data breach back in 2018 that led to the theft of about 383 million guests, and in 2020 the hotel giant notified 5.2 million guests after employee credentials were compromised.
More: Cyberscoop | TechCrunch | @campuscodi
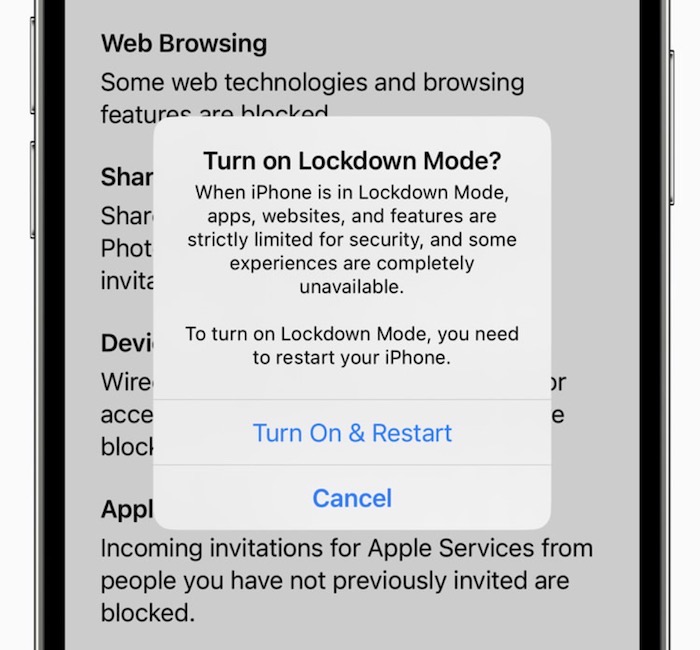
Apple announces 'extreme' mode for targets of government spyware
Motherboard: The next iOS 16 and macOS software will land with a new feature called "Lockdown Mode," which Apple bills as an "extreme optional protection" that allows high-risk users to switch off or vastly reduce the functionality of certain core features of an iPhone, iPad or Mac. The aim is to drastically reduce the attack surface area in which powerful government spyware (like NSO's Pegasus) or other malware can target your device. Lockdown Mode can be switched on and off as needed, but the trade off is that some features won't work as expected, like link previews or attachments. (@lorenzoFB has some tweets looking at how it works.) Security researchers have already praised the move, and Apple will lob $2 million from its bug bounty at anyone who finds a workable exploit in the new mode, expected out later this year.
More: Apple | BBC News | @danguido tweets
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
U.K. lawmakers call for Chinese CCTV firms
BBC News: U.K. members of parliament are calling for a ban on Hikvision and Dahua equipment, which has been connected to human rights abuses in China. The U.S. has effectively banned the equipment after the tech was linked to Beijing's mass incarceration, torture and surveillance of mostly Muslim minorities in Xinjiang. But in the U.K., Hikvision and Dahua cameras are everywhere — 75% of U.K. councils, the majority of secondary (high) schools and six out of 10 NHS trusts. Police forces and U.K. universities also heavily rely on the equipment.
OPM class action: $63 million set aside for victims
U.S. Office of Personnel Management: If you were one of the 21.5 million individuals whose information was compromised in the 2014/2015 breach of the U.S. Office of Personnel Management, or OPM, you may be entitled up to $10,000 as part of a recently settled class action. The press release has more, and the official class action site is here. The OPM was hit by a massive breach of personnel records containing highly sensitive information on those who obtained U.S. government security clearance. China has long been suspected as being behind the breach.
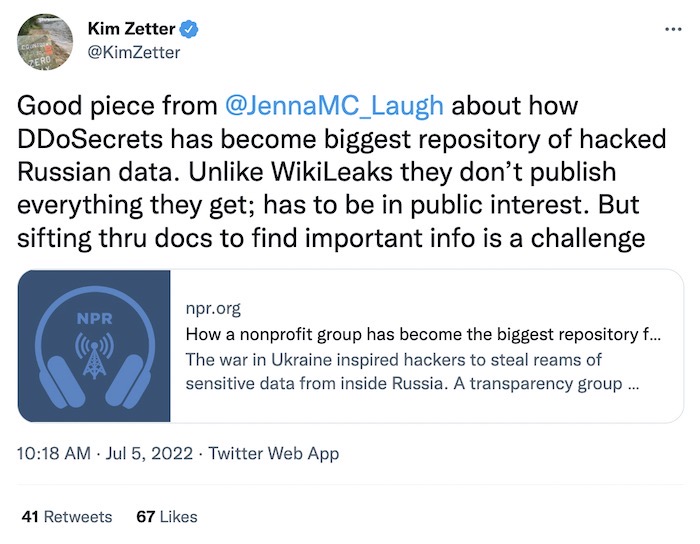
Profile of DDoSecrets, a huge repository of hacked Russian data
NPR: Distributed Denial of Secrets, or DDoSecrets, gets the NPR treatment this week, detailing the journalism organization's work in publishing data leaked or hacked from Russian organizations and government departments. Though DDoSecrets doesn't do the hacking or leaking, it carefully publishes files (and distributes them via peer-to-peer services, making it harder to delete) to reveal wrongdoing, corruption and other nefarious activities that could be used to identify Russian war crimes and other conduct illegal under international law. But first, that will require "serious digging" from journalists and researchers to trawl through the vast trove of data.
The code the FBI used to wiretap Anom
Motherboard: For those who have been following the Anom saga — the short version is, the FBI backdoored an encrypted phone and messaging company called Anom that was used almost exclusively by criminals around the world, and siphoned off every single message sent by the criminals, leading to more than 1,000 arrests. It was an incredible feat, if not highly controversial. But @josephfcox got his hands on the motherlode: the Anom Android app containing the backdoor code that shows exactly how the backdoor worked — and let the feds snoop for years.
U.S. chooses four quantum-resistant encryption algorithms
ZDNet: NIST, the U.S. standards setting agency, announced four algorithms (after a long six-year wait) that will become part of its post-quantum cryptographic standard, expected to be finished around 2024. Quantum computers are still a way away, but will have the theoretical ability to break today's encryption standards.
I sent my yoga studio a web form, and all I got was this lousy malware attack
Ars Technica: @dangoodin001 investigated a cyberattack targeting him (and others who go to the same yoga studio). With help from email security firm Proofpoint, he found that crime group TA578 hacked into the studio's email account, and used "thread hijacking" that involves replying to existing email threads to make the attackers' communications look more legitimate. That's when the attackers send attachments with malware. Goodin wasn't duped. But it's a solid reminder to always be on guard, even from supposedly known senders. Remember: trust but verify!
~ ~
OTHER NEWSY NUGGETS
FBI, MI5 warn of China threat: U.K. and U.S. intelligence chiefs joined forces this week to warn of the "immense" threat from China, reports the BBC. China is the "biggest long-term threat to our economic and national security" and has interfered in politics, including recent elections, and has "a hacking program larger than that of every other major country combined," said the heads of the FBI and MI5. It comes in the same week that alarm bells started to ring over the sale of the U.K.'s largest microchip plant to a China-based company, prompting concern on both sides of the Atlantic. The U.S. government's counterintelligence agency tweeted out a "hinty hint, winky wink" about the situation. The purchase, however, could still be unwound if found to violate national security rules.
Hackers dump Iranian secrets: Cyberscoop reports that the same hackers who targeted an Iran steel factory last week are back with a massive tranche of top secret documents allegedly stolen, which among other things, "reveal the facilities' affiliation with Iran's powerful Islamic Revolutionary Guard Corps." It's not known who the hackers are or affiliated with, but all eyes are on Israel, where not even the defense minister is denying it.
Web3 projects lost $2B thanks to hacks: If anyone wants to know how everything in Web3 is going, well, not great by all accounts. New research from Certik this week shows Web3 projects lost about $2 billion in assets this year alone because of hacks and exploits. It's also due to new threats, like "flash loan" attacks that can be used to manipulate tokens or, in some cases, abused to take over and withdraw a project's funds, like what happened with Beanstalk earlier this year. More here from The Verge.
IT giant SHI offline after malware attack: New Jersey IT and electronics retailer SHI, which sells to organizations, enterprises and government customers (and likened to the "Amazon for companies to order hardware and software"), was hit by a "coordinated and professional malware attack" and knocked the company offline over the July 4 holiday weekend. Its site was still down as of June 8, but is now up at the time of writing this. SHI has a blog post with details. SHI said there is "no evidence to suggest that customer data was exfiltrated." I guess time will tell.
Microsoft U-turns on sunsetting macros: And just when we thought macros were finally dead, Microsoft briefly reversed its position this week on stamping out the long-abused code running feature, reports The Register. Microsoft announced earlier this year that it was going to block macros sourced from the internet, since this is one of the most common ways for cybercriminals to target their victims by tricking them into opening a malicious Office document. Microsoft dropped a code change to block macros, but then rolled back the change without saying why, only that it was "following user feedback." Microsoft said it was a "temporary change."
~ ~
THE HAPPY CORNER
Alright, let's see what we have this week.
@runasand tweeted about a robot game (in the Activities tab) that you can play in Google Meet while you wait for other attendees. According to Reddit, it was added around a month ago. TIL!
For anyone attending hacker summer camp this year, Black Hat announced its keynote speaker is former CISA director @C_C_Krebs.
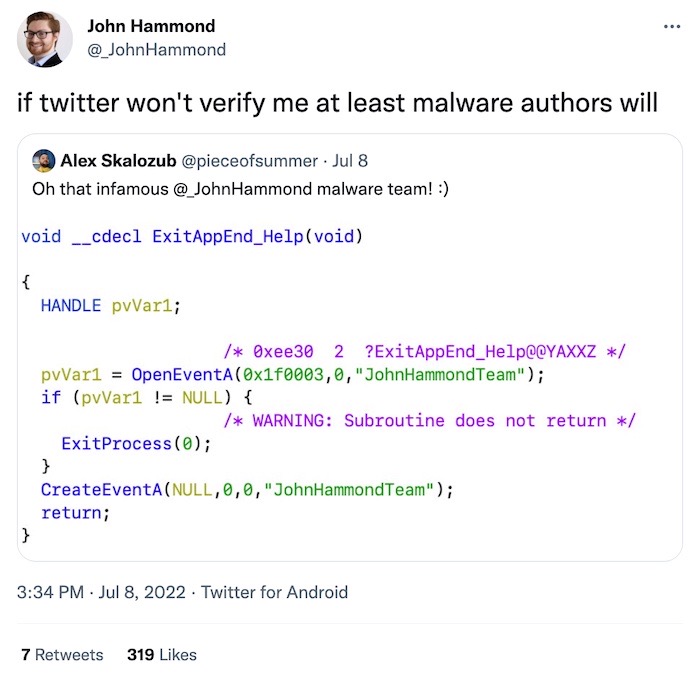
Meanwhile over on Twitter, @_JohnHammond is getting closer to that coveted Twitter blue check by the day if the malware authors have anything to do with it.
And, thanks to @jwgoerlich for tweeting out this brilliant comic this week.

To send in good news for the happy corner, please reach out to: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
Meet Marble, this week's cyber cat. She is an 18-year-old rescue and blind, but she can still sniff out a threat actor in your network faster than you ever will. A big thanks to Dustin V. for sending her in!

Please keep sending in your cyber cats (or their friends!). Email me here with their name and photo, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's it for this week, thanks again for reading. If you have any comments, questions, or feedback, the suggestion box is open or feel free drop me an email. Back next Sunday, hope you have a great week.
Cheers,
—@zackwhittaker