this week in security — july 13 2025 edition
THIS WEEK, TL;DR
Everyone but Citrix agrees that 'Citrix Bleed 2' is under attack
The Register: For the past week, security researchers have been sounding the alarm over cyberattacks linked to "Citrix Bleed 2," (aka CVE-2025-5777) a bug that can be used to extract sensitive credentials from an affected Citrix NetScaler device and used to break into a company's wider network. The bug takes its name from CitrixBleed due to its similarity to the 2023 flaw in the same product. With exploits now public and evidence of hacks dating back to mid-June, CISA has added its name to the chorus of folks warning about its exploitability. Citrix, meanwhile... *crickets*... seems to be the only one left not to acknowledge the active hacking campaigns abusing the bug, instead just telling customers to patch as soon as possible. That's a pretty lousy response all in all. Maybe it has something to do with the fact its CEO was moonlighting at DOGE for the past few months? Nah, it's Citrix, we've been here many times before already! If you haven't patched already, patch — and hunt for activity — today.
More: CISA | Citrix | DoublePulsar ($) | ReliaQuest | TechCrunch | CSO Online
U.S. feds announce arrest of 'Hafnium' Exchange email hacker
Justice Department: The still-somewhat-functioning U.S. DOJ announced the arrest(!) of a Chinese national who prosecutors say is a key figure within "Hafnium," a hacking group that works on behalf of the Chinese government. The hacker, Xu Zewei, who was arrested in Italy, is accused of working for a company Shanghai Powerock Network that conducted cyberattacks and breaches for China's interests, including stealing COVID research from U.S. universities during the height of the pandemic. The "Hafnium" hacking campaign saw the alleged hacker and another named Chinese national mass-hack thousands of self-hosted Exchange email servers across the world, stealing mailboxes and contacts. It's believed "Hafnium" effectively morphed into Silk Typhoon, another campaign aimed at breaching large companies and government departments (remember the Treasury hack?) to steal information. Suffice to say, when the arrested Chinese hacker arrives in a U.S. court, we may get more information about how the long-running hacks went down.
More: Microsoft | Bleeping Computer
Four arrested over recent U.K. retail hacking spree
BBC News: The feds (or in the U.K., plods) had a busy week rounding up four alleged members of the Scattered Spider hacking collective — a woman aged 20, two men aged 19, and a minor aged 17, per the U.K. National Crime Agency. The suspects can't yet be named due to the quirks of British law... nevertheless, some of the identified hackers are accused of, well, hacking (obviously), but also blackmail, money laundering and participating in the activities of an organized crime group. The plods directly attributed the arrests to the breaches at Marks & Spencer and the Co-op, and the cyberattack targeting Harrods. With any luck, we'll also figure out more about the hackers, their techniques, and operations. As an amorphous and loose-knit threat, Scattered Spider remains a major, major problem for network defenders.
More: National Crime Agency | DataBreachToday | Wired ($) | KrebsOnSecurity
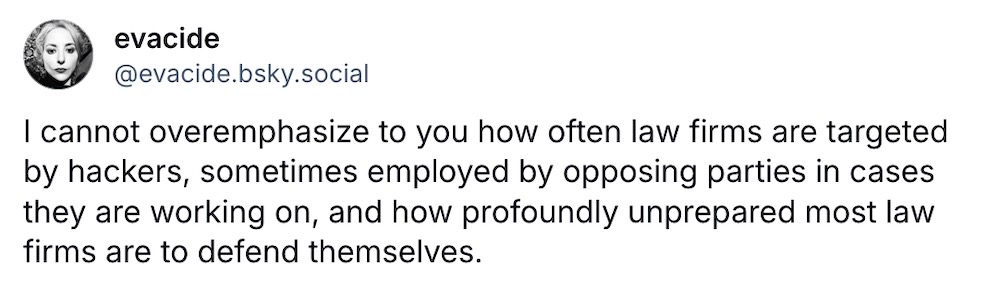
Chinese hackers suspected in breach of powerful D.C. law firm
CNN: Suspected Chinese hackers broke into the email accounts of Wiley Rein, one of the biggest law firms in Washington, D.C. The firm told its clients that the stolen information relates to "trade, Taiwan and U.S. government agencies involved in setting tariffs and reviewing foreign investment," so... pretty sensitive stuff as of late. It's the latest major law firm to have been hacked in recent years; it actually happens a fair bit, like Orrick, Fragomen, and others. Not only are law firms a target, some firms are said to have actively hired hackers to dig up damaging information on litigants to win their cases. Just this week, a pair of lawsuits were resolved (with no admission of liability) following claims by an airline executive that his emails were targeted, hacked, and leaked.
More: @snlyngaas | @AnnieGrayerCNN | Archive: Readme (2023)
Jack Dorsey's 'secure' Bitchat app wasn't security tested before launch
TechCrunch: Twitter co-founder Jack Dorsey vibe coded his way through last weekend to develop the terribly named decentralized messaging app Bitchat. Dorsey said the messaging app relies on nearby Bluetooth signals rather than the internet, making it helpful where the internet is monitored or offline. He also billed the app as "secure." Just one major problem — it isn't secure, not least because of a serious bug that undermined the app's encryption (which Dorsey closed without learning more), but that Dorsey didn't even bother getting the app security tested before launching, by his own admission. To be clear, words matter. Claiming something is secure when it's not is the sort of dumbassery (or Jack-assery, amiright?) that could get someone in a high-risk situation put in harm's way, or worse. Not a good look for one of the world's richest people. Riches can't buy you common sense, clearly.
More: TechCrunch | Supernetworks | GitHub | @jack
~ ~
THE STUFF YOU MIGHT'VE MISSED
Android is allowing Gemini to access third-party apps
Ars Technica: A whole new surveillance hellscape just opened up: Google, beginning this past Monday (with barely any heads up), began rolling out an update that allows its Gemini AI to access the data from other apps on a user's Android device. Yes, that also includes end-to-end encrypted apps like WhatsApp, and more. (What could go wrong, except a million things?) Actively removing the Gemini app is a pain but might be worth it, and Ars has the details. Meanwhile: Meredith Whittaker (by far the smartest Whittaker I can think of) warned against this exact kind of threat, by way of AI compromising the app-layer protections that messaging apps put in place to prevent other apps from reading their private messages.
Trump seeks unprecedented $1.2 billion cut to federal cyber budget
CSO Online: Trump's tax bill, which became law on July 4 will overall cut the federal cyber budget by more than a billion dollars, a 10% drop in cyber expenditures in 2026, when the tax bill takes effect. Experts say it's a hard sell to be spending less on cybersecurity these days. Cue this incredibly telling line, per the Cyber Threat Alliance CEO: "If I were a nation-state adversary, I would be joyous at what's going on inside the US government. Decreased funding is only going to fuel that." Welppp.
Litigious company demanding tweet removal learns of Streisand effect
Techdirt: The very excellent @joebeone is a fountain of knowledge and awesomeness, so when he posts or tweets, people read. But Hall found himself in receipt of a legal threat from a company called Cloud Innovation, simply for posting a tweet of a link — yes, just a link — to this story about Cloud Innovation's litigious conduct in Africa regarding the region's internet registry. Hall fired back a letter from his own lawyer (worth reading, it's scathing!) and got a fantastic write-up in Techdirt about the saga. It'd be a real shame if you read the story that Cloud Innovation clearly doesn't want you to know about!
'123456' password risked exposing McDonald's job applicants' data
Ian Carroll, Sam Curry: Carroll and Curry, a hacking duo behind some roaring findings in recent years, found that a McDonald's hiring site called McHire, which was using an AI chatbot that filters out prospective employees, was protected with a password of "123456," allowing access to the internal API. Thanks to a separate IDOR bug, the hackers could access the private data on potentially millions of applicants. The bugs were reported, fixed, and disclosed. As you'd expect, Wired ($) has a great write-up.
State Dept. investigating Marco Rubio impersonator
Reuters ($): The State Department is investigating a Marco Rubio impersonator, who allegedly used an AI voice to contact three foreign ministers and two U.S. officials over Signal and text messages pretending to be the U.S. top diplomat. This probably wouldn't be much of an issue if Rubio et al didn't occasionally use non-official channels (like that Signal group chat) to communicate with their counterparts. At least if he stuck to classified only channels, he probably wouldn't have someone running around on Signal pretending to be him. (In news you can use, here's some solid advice from @RachelTobac on how to detect AI voice clones.)
Spain awards Huawei contracts to manage spy agency wiretaps
The Record: This story is submitted (almost) without comment... Huawei, the Chinese tech giant that was banned from use in the U.S. over national security fears that it could (or will) provide sensitive network data and internet traffic back to the Chinese government, will now manage and store judicially authorized wiretaps for Spain's intelligence agencies. Yeah, not sure that's the smartest idea... This is pretty much what Spain's intelligence allies look like right now:

~ ~
OTHER NEWSY NUGGETS
DOGE accesses huge database on farmers: NPR has a new long read on DOGE's latest data dive, and this time they're coming for U.S. farmers. With access to a database that contains vast amounts of financial data on farmers and personal information on their workers — including immigration status — DOGE now has control over tens of billions of dollars in government payments and loans to America's food growers. If farmers can't guarantee receiving loans or payments, this could "disrupt entire growing seasons." Just absolutely stellar reporting here from one of NPR's best journalists. (via NPR, @jennamclaughlin)
Ingram hobbles back online: Following its ransomware attack, Ingram Micro is back online as of July 9 after restoring its operations globally. It's not clear yet if any customer data was stolen in the hack, or who it relates to. Given that Ingram Micro provides and ships tech to many of the world's biggest companies (and their remote employees!) it could be sizable, so one to keep an eye out for. (via SecurityWeek)
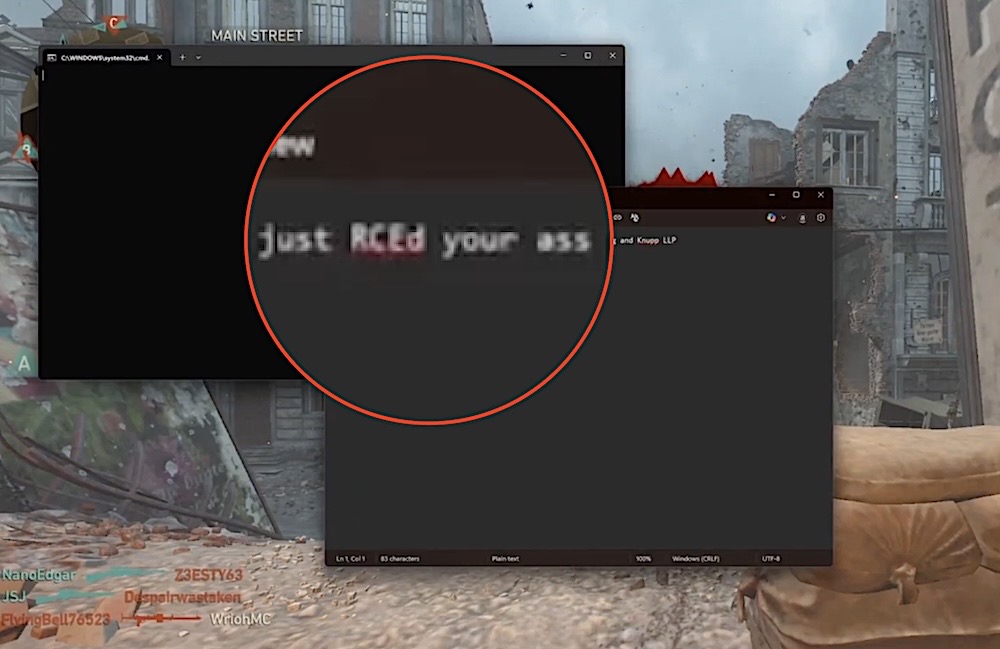
CoD offlined after players hacked: A source with knowledge of the situation said game publisher Activision took down its Call of Duty: WWII game from the Microsoft Store after players reported targeted hacks during their gameplay. Turns out Activision patched the bug once already, but forgot to port the fix over when it launched the game for PCs. In one video posted to X, one player's gameplay froze and a couple of command prompt windows appeared, with text saying that someone had just "RCE'd [their] ass." (via TechCrunch)
Stingrays caught snooping on ICE protests: Wild reporting here: @MikaelThalen found evidence that an IMSI-catching surveillance device (think "stingray") was being used during a July 4 protest at an ICE immigration detention facility. This shows law enforcement's appetite to use cell site simulators and other surveillance tech at protests. Stingrays are generally only allowed to be used in exigent or emergency cases, circumstances that are often subjective (and favorable) to the cops using the damn things. (via SAN)
10/10 bug warning in Wing FTP: A very easy-to-exploit bug found in Wing FTP Server, used by thousands of big companies around the world, allows anyone to break into an affected server. The bug is rated 10/10 in severity because of its simplicity. Huntress said it's seen one customer exploited so far; let's hope it stays that way. (via RCE Security, Huntress, The Register)
~ ~
~ ~
THE HAPPY CORNER
The sun is shining, the birds are chirping, and the water is warm. This is as happy as the happy corner gets.
Congratulations to the good people at the Electronic Frontier Foundation on their 35th anniversary! Thanks to everyone there for all you do to support the cyber community. Throw 'em a tax-deductable(!) donation if you can spare a few.
If you need a good laugh today, and let's be honest — we all do (/me gestures wildly in every direction), one Redditor recently found that it's still possible to jailbreak ChatGPT into spitting out things that it shouldn't. This time, the chatbot can be tricked into providing Windows 7 product activation keys, thanks to the "grandma exploit." This is a trick where you convince the chatbot into thinking outside of its guardrails and pretending to be a fictional grandma who recently passed away. This trick isn't new, but has been used to trick chatbots into spitting out instructions for things like napalm.
It's that time again... Let's buckle up for another round of Patch Tuesday and...

...Microsoft reported no actively-exploited zero-days! That's rare in itself. (Mind you, there are still patches to install!) Google also had a good week — confirming there are no Android security patches in the July 2025 security bulletin. @campuscodi notes that this is the first month without one in six years.
The Onion wins this week's best headline. (Even for parody, this is pretty spot on.)
And finally: From the National Park Service:

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet this week's cyber cat kitten, Gidget, who can be seen here glaring at her human to demand more cuddles. That's social engineering at its finest! Thanks so much to Tristan for sending in.

Keep sending in your cyber-cats! Got a cyber-cat or a non-feline friend? Send me an email with their photo and name and they will be featured in a future newsletter.
~ ~
SUGGESTION BOX
That's it for this week's busy edition of this newsletter, thanks so much for reading! I hope you have a great week ahead of you. I'll be back on Sunday with your roundup.
Want to get in touch with something for next week's edition, like good news or a cyber cat? I'd love to hear from you — I'm just an email away!
Offlining for now,
@zackwhittaker