this week in security — july 14 2024 edition
Nice to come back to the news after a relaxing week on vacat... ohh no.

~ ~
THIS WEEK, TL;DR
Cybercriminals steal phone records of 'nearly all' AT&T customers
AT&T: So... to begin with the big news of the week. AT&T confirmed on Friday that the company had a huge amount of customer phone numbers and phone records stolen during a recent breach at its cloud data provider Snowflake. AT&T said in an 8-K filing that crims stole phone records — think calling and texting metadata, but not the contents of those calls or texts — on "nearly all" of its customers between May 1, 2022 and October 31, 2022 — and in some data from customers dated January 2, 2023 and later. An AT&T spokesperson told me the data theft was to the tune of 110 million customers — but that doesn't include the many, many non-AT&T customers whose phone numbers and associated calling records were also leaked as a result. The DOJ delayed AT&T's notification to customers on national security grounds (twice!) and to allegedly arrest an individual involved in the financially motivated hacking crew, but no words from the feds on that just yet. The data isn't public — and let's hope so — because that could cause a lot, and I mean a lot of trouble for at-risk individuals. AT&T has a support page with more.
More: 404 Media ($) | TechCrunch | WSJ ($) | @josephfcox | @racheltobac tweets
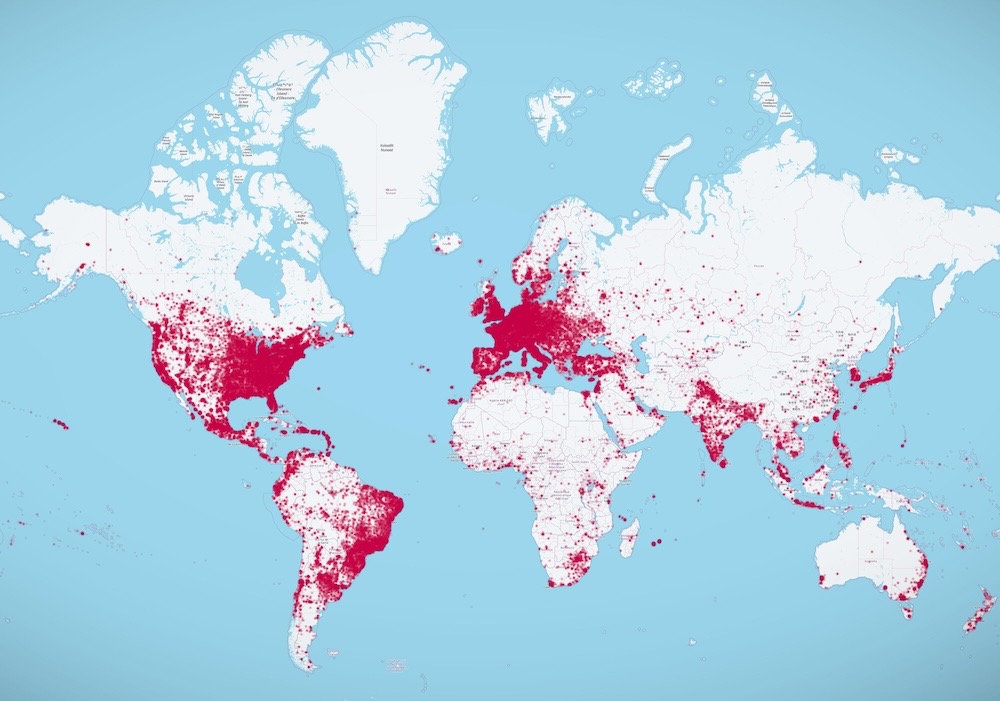
Data breach exposes millions of mSpy spyware customers
TechCrunch: A customer service Zendesk instance run by the makers of the widely used mSpy spyware (or "stalkerware") app was stolen and leaked online last month. A review of the data shows it contains about 2.4 million unique email addresses of customers, but also those seeking to contact mSpy for other reasons — such as police departments and government agencies issuing subpoenas, requests for trial software, and making inquiries about whether it can be used in government. I analyzed the data and found customers in almost every country, with large clusters in the United States, Europe, and South America. (Disclosure: I wrote this story!) Troy Hunt loaded the email addresses into Have I Been Pwned. mSpy is the latest stalkerware app to have been hacked in recent years (at least 20 others have been pwned so far) — so plenty of reasons why you shouldn't ever use surveillance apps like mSpy. The good news, though, if there is any, is that the data also exposed the Ukrainian company behind the secretive mSpy operation.
More: Reason | Wired ($) | maia arson crimew | @troyhunt tweets
Ticketmaster's hack is becoming a logistical nightmare for fans and brokers
404 Media ($): Several online brokers have figured out a way to reverse engineer Ticketmaster-issued tickets and generate ticket barcodes following the earlier breach at Ticketmaster (also linked to Snowflake). In doing so, it removes the anti-scalping restrictions put on tickets by Ticketmaster and others. The hackers behind the breach at Ticketmaster released new data that allows anyone to create PDF tickets for upcoming events, meaning someone could use the hacked data to create a ticket that could refuse entry to someone else. More from 404 Media ($)'s follow-up.
More: Bleeping Computer | BBC News | @jason_koebler
~ ~
THE STUFF YOU MIGHT'VE MISSED
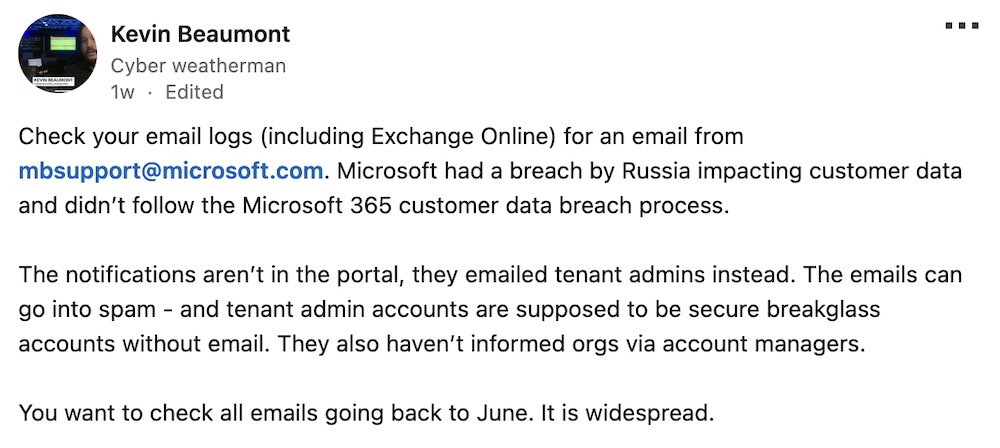
Microsoft flubs customer notification of Russian government hacks
TechCrunch: Hundreds of customers are being notified that the Russian government-backed hackers known as APT29 (or Midnight Blizzard) stole their emails directly from Microsoft's servers by way of an ongoing cyberattack that began late last year. The problem is that Microsoft made the email notification look incredibly suspicious, akin to a malicious phishing email, so much so that the company might as well have just written the email in Russian. Plenty of folks were left confused by the weird-looking email, but — yes, it's actually legitimate. Check your tenant admin logs! More from cyber weatherman Kevin Beaumont, who by the looks of it has done a better job of helping customers than Microsoft itself.
Australia and partners issue APT40 advisory about Chinese hacking
Australian Signals Directorate: From ATP29 to... APT40, a China state-sponsored actor that Australia and its Five Eyes partners along with Germany, Korea and Japan revealed more about this week in a new alert, warning of the increased risk posed by the China-backed hacking group. APT40 relies on breaking into small office and home office (aka SOHO) routers that are old and no longer receive security patches. That allows the Chinese hackers to break in and conduct espionage and more. CISA and Australian authorities have more.
CISA hacked a federal agency and reported the results
CISA: The cyber defensive sleuths at CISA hacked into a U.S. federal agency (without warning or notice — that's the way to do it) using the tools and techniques to mimic a real attack, and weren't spotted for months. CISA reported the results in detail — and it's worth the read. The short version is that the "targeted" federal agency should've fixed the initial access bug (a known vulnerability) that CISA itself had warned about some years ago. At one point, CISA's red team hackers deployed an implant during the engagement that accidentally churned up 8 GB in its "malicious" traffic but that the agency's tools failed to notice. Whoops!
Remote execution bug in Ghostscript library under attack
Bleeping Computer: A bug in the Ghostscript document conversion library — widely used on Linux — allows remote code execution, and is under attack in the wild. The bug is tracked as CVE-2024-29510, and exploited by way of malicious PostScript files disguised as JPEG images to get shell access. Developer @llimllib warned that, "if you have GhostScript anywhere in your production services, you are probably vulnerable to a shockingly trivial remote shell execution, and you should upgrade it or remove it from your production systems."
Google adds passkey support for most at-risk users
Wired ($): Google is bringing passkeys — the new phishing-proof password replacement — to its Advanced Protection Program, which allows high-risk users to beef up their account security without having to use a physical security key (which some might find cumbersome). Replacing your Google account password with a passkey makes it significantly stronger against online account hijack attempts.
Top Google privacy officials depart, worrying lawmakers
Politico: Speaking of Google, though... Politico reports that at least six of Google's top privacy and regulatory officials have yeeted from the company in recent months — and a major oversight team for its AI programs disbanded — leading to lawmakers like Sen. Ron Wyden to call on the FTC to investigate whether the company is adhering to its legally mandated privacy requirements.
Cult of the Dead Cow marks 40 years
cDc: And I can't not note that this week marks the 40th anniversary of the founding of Cult of the Dead Cow, per @dethveggie. For the young'uns who weren't around at the time (including me, alas), it just so happens @JosephMenn literally wrote the book on Cult of the Dead Cow and its history so go buy yourself a copy. (It's a brilliant read, I read it on vacation a couple of years ago.)
~ ~
OTHER NEWSY NUGGETS
Debt collector breach hits millions: Some four million people had personal and health information exposed following a breach at the medical and auto finance-focused debt collection agency Financial Business and Consumer Solutions, per a filing with Maine's attorney general. The data includes medical claims, clinical information, diagnosis data, and more. (via The Record)
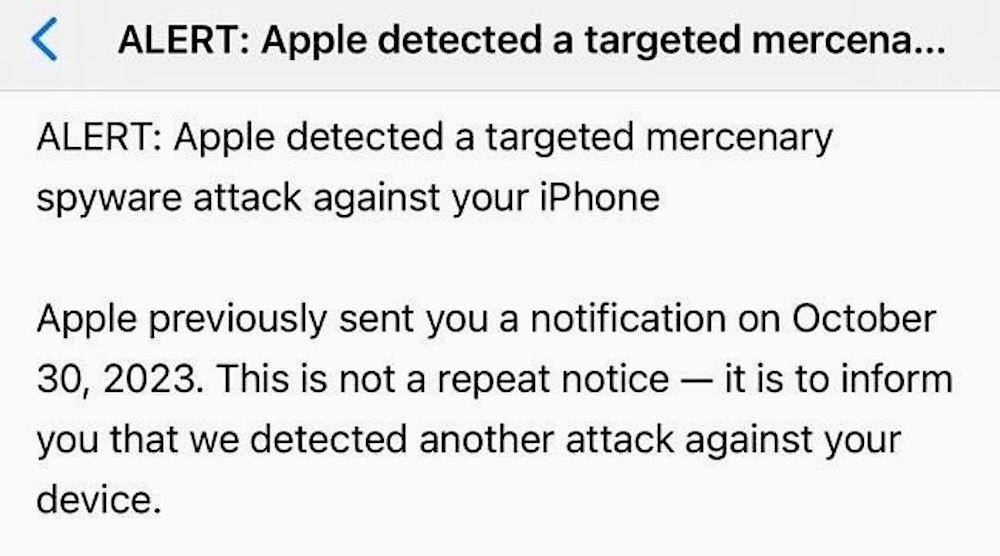
Apple notifies of spyware attacks: The iPhone maker sent out another batch of threat notifications to customers who Apple has evidence that they were targeted by mercenary spyware attacks (such as Pegasus and Predator). Apple notified customers in 98 countries, though the total number of notifications is not known — and likely a closely guarded Apple secret. One Indian opposition politician said he got a notification from Apple telling him he was targeted again and that it was "not a repeat notice." India's Modi government is accused of using spyware on its political opponents. (via TechCrunch)
Patch it like it's Tuesday: It's Patch Tuesday week, and Microsoft has fixed 139 security holes across Windows and its other products. Two of the flaws are under active attack as zero-days targeting Windows users. Patch today! (via KrebsonSecurity, @msftsecresponse)
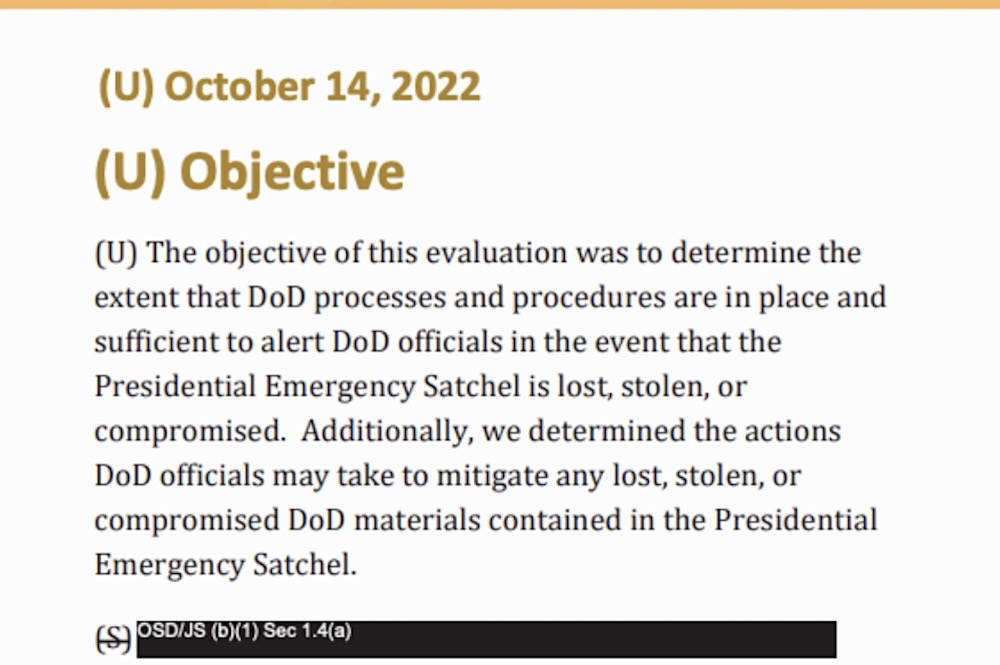
Don't kick (or nick) the nuclear football: The so-called "nuclear football," a suitcase that travels with the U.S. president at all times that allows the commander-in-chief to launch nuclear weapons from anywhere, was dangerously close to rioters during the January 6 attack in 2021. @JasonLeopold obtained a watchdog report looking at the security of the nuclear football — you know, in case the bad thing happens. Turns out there are procedures so that only the president can authorize the use of nuclear weapons. (Apparently that's good news?) If you haven't signed up for Leopold's FOIA Files newsletter already, you absolutely should. (via Bloomberg ($))
Tank gets jail time: The cybercrime boss, a Ukrainian national called Vyacheslav Igorevich Penchukov — aka Tank — who helped lead the prolific Zeus malware gang, was on the FBI’s most wanted list for years. Now he's behind bars and ordered to repay millions of dollars. (via Wired ($))
Car dealer hack ends with payoff: The ransomware attack on car dealership management software maker CDK a few weeks ago, which froze thousands of dealerships and auto shops across North America for at least two weeks, appears to have paid the criminal hackers a ransom of $25 million. CDK said last week that most of its 15,000 or so car dealerships were back online. (via CNN)
~ ~
~ ~
THE HAPPY CORNER
Fire extinguishers down, that's the hellfire week of news done with. Happy corner, commence!
Excellent news that Semiphemeral, the service that once allowed Twitter/X users to automate the deletion of their tweets, likes and DMs, until hissy-fitter-of-the-year Elon Musk shut it off, will soon be back and then some. @micahflee explains more in a blog post. (I'm personally very excited for this.)
Congratulations are in order to @gluley and partner for gaining persistent access to each other's lives, aka marriage.
FYI: A rare Wireshark found in the wild.
And, a new blast from the past. Back in the early days of the web, the search engine before Google became big (then got, well, bad) was a website called Ask Jeeves. It was a simple site where you'd ask a virtual butler a question and it would spit back search-like results. Now, imagine Jeeves in this day and age spitting back pizza recipes with glue and instructions for making napalm. Probably best that Jeeves a memory of yesteryear for now...
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Tennessee, who's back with a helpful reminder that doing the basics — using a password manager and ad-blocker, and multi-factoring all the things — can do a lot to help protect your security and privacy online. Thanks Tennessee, you rock. And many thanks to Jeri D. for sending in!

Send in your cyber cats! You can drop me an email with a photo of your cyber cat (or your non-feline friend!) with their name and they will be featured in an upcoming newsletter. Have an update? Feel free to send in — updates are always welcome!
~ ~
SUGGESTION BOX
OK, that's it — I promise. Thank you so much for reading and taking the time with this bumper newsletter. As always, please do get in touch any time if you have anything you want to share for the next edition.
All the best,
@zackwhittaker