this week in security — july 16 edition
THIS WEEK, TL;DR
China hackers breached U.S. government inboxes via Microsoft cloud flaw
CNN: The U.S. government was hacked... again. This time it's Microsoft's turn in the spotlight after China-backed hackers somehow* acquired a signing key that allowed them to forge tokens to break into email accounts. (*somehow, because Microsoft still doesn't know — or won't tell us). What's worse is that the key — used for consumer accounts — allowed the hackers access to enterprise accounts. The hacking group is known as Storm-0558, and it looks like an espionage actor given its stealthy techniques. The State Dept. was the first to notice something awry, in part because it had a higher paid account that allowed access to audit logs. Other departments weren't able to, according to the WSJ ($). State reported the breach — around mid-May — to Microsoft, and we're just now hearing about it now. This is going to be an ongoing affair, so stay tuned.
More: CISA | Ars Technica | Wall Street Journal ($) | Washington Post ($) | Cyberscoop
HCA Healthcare discloses breach affecting 11 million after data put up for sale
DataBreaches.net: One of largest U.S. healthcare providers HCA Healthcare said in a statement this week that personal data on some 11 million patients was likely compromised after a hacker claimed days earlier to be selling the data. The data — related to email messages for scheduling and reminders — was made public in a listing on a known cybercrime forum on July 5. It's not clear how the data was taken, but HCA said it doesn't contain clinical information. DataBreaches.net, which first reported on this, explores more.
More: HCA Healthcare | CBS News | TechCrunch | Houston Chronicle
Former Amazon security engineer arrested with crypto thefts
U.S. Attorney's Office, SDNY: A former security engineer was arrested this week over what the SDNY claims is the first-ever criminal case "involving an attack on a smart contract" operated by a crypto firm. Prosecutors claim Shakeeb Ahmed, who used to work at Amazon (a spokesperson confirmed), stole $9 million in cryptocurrency by exploiting a bug in what's believed to be the Crema exchange (the timing lines up) to fraudulently insert fake pricing data to generate millions of dollars worth of fees that he could allegedly withdraw. SDNY said Ahmed's resume "reflected skills in, among other things, reverse engineering smart contracts and blockchain audits, which are some of the specialized skills Ahmed used to execute the attack." Inner City Press has more from the courtroom.
More: Hacking But Legal | Coindesk | @SDNYnews | @lorenzofb tweets | @molly0xFFF
Top big law firms targeted in global cyberattack
Above the Law: Several big law firms, Kirkland & Ellis, K&L Gates, and Proskauer Rose, are all named victims of the Clop ransomware group's latest data raids involving exploitation of a flaw in their MOVEit file transfer tools. Banks, hotels, hospitals are among other victims of the MOVEit mass-hack, now said to be affecting tens of millions of individuals. Law firms hold valuable client data that can be of high value to hackers, even years down the line. Case in point: In an unfortunate twist, global law firm Orrick reported a data breach involving 40,000 people (unrelated to MOVEit) whose data was breached three years earlier in another data breach that the law firm was called in to manage. But because Orrick was hacked, the people's data was breached for... a second time. It's the circle of life cybercrime.
More: TechCrunch | Bloomberg Law ($)
~ ~
THE STUFF YOU MIGHT'VE MISSED
Massachusetts considers ban on sale of phone location data
Wall Street Journal ($): Lawmakers in Mass. are weighing a near total ban on the buying and sale of location data from phones in what's seen as a first-in-the-nation effort to curb the data broker market. The Location Shield Act would also institute a warrant requirement for police, and ban data brokers from providing location information about state residents without court authorization in most circumstances. Most of the location data is derived from phone apps, which sell the data to brokers.
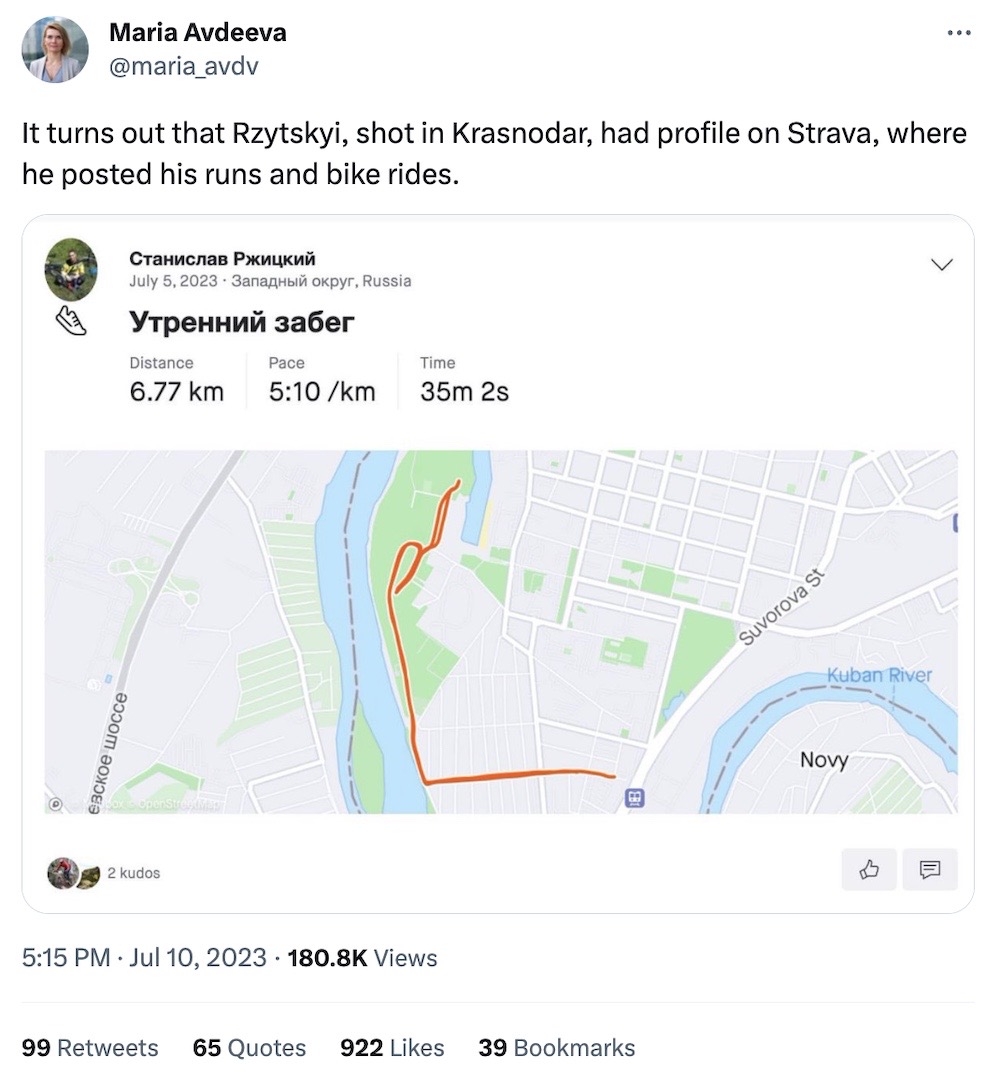
Russian sub commander killed after posting runs on Strava
Kyiv Post: Ukraine's Defense Intelligence confirmed the death — and provided "very specific details" about the killing — of Stanislav Rzhytsky, a Russian sub commander, who apparently posted his running and cycling routes on the fitness app Strava. It's not clear who's behind the killing, but it does sound like someone was watching his Strava posts. Strava has been criticized in the past for exposing military bases and other sensitive locations, but this Russian military man's opsec mistake might just have been his last. BBC News has more on the case.
U.S. used 'potent' surveillance power to tap global travel database
Forbes ($): The Justice Department decided this month to unseal a secretive government order, filed under the All Writs Act (remember Apple-FBI?), which allowed the government to demand travel data from companies known as global distribution suppliers, such as Sabre, which processes some one-third of all air travel reservations. The order was used to track a Russian national suspected of facilitating $20 million in stolen credit cards from a cybercrime site. More by @iblametom.
Three tax prep firms shared ‘extraordinarily sensitive’ data about taxpayers with Meta
Associated Press: A group of Democratic lawmakers have accused H&R Block, TaxAct and TaxSlayer of sharing "extraordinarily sensitive" information on tens of millions of taxpayers to Facebook's parent company Meta over at least two years. They did this through pixel tracking; the same tracking that's resulting in a crackdown on health startups doing similar data sharing. The Dems are calling on the IRS, its OIG, the DOJ and the FTC (lots of acronyms, I know) to investigate. Props to The Markup for revealing this last year.
~ ~
~ ~
OTHER NEWSY NUGGETS
Zero-day, patch! Wait, roll-back! Apple's Rapid Security patches will plug your Apple devices with fixes for zero-days as they're discovered, but its latest patch for a WebKit flaw under active attack had to be rolled back after the bug interfered with certain websites. Good news, though, it's back as a new update. Patch today, again! (via Ars Technica)
Huge cyber bill incoming: The U.S. NDAA, the national defense bill that has to be passed by Congress every year, is back with a ton of new cyber amendments tacked on in the hope that they'll pass as well. That could include bans on the U.S. government purchasing commercial data on citizens and investigating the SolarWinds hack — that is, if the bill passes the Senate. The Post has a good round-up of what's going on in the bill, but it's still relatively early days. (via Washington Post ($))
Silk Road's second-in-command jailed: Roger Thomas Clark, aka Variety Jones, will spend the next 20 years in prison after he was convicted for running a key role in building and running Silk Road, the notorious dark web marketplace for drugs that saw its admin, Ross Ulbricht, also jailed for much of the rest of his life. At one point, Clark, a 62-year-old Canadian, allegedly encouraged Ulbricht to have a staffer killed for apparently stealing bitcoins from the market. (via Wired ($))
Calls to hire new national cyber director: As industry groups call on the White House to nominate a new National Cyber Director following the departure of Chris Inglis, news broke this week that it will likely not be Kemba Walden, one of the most experienced cyber officials in government who has served as acting-NCD since Inglis left. According to reports, Walden was told she would not receive the White House's nomination. The Post followed, saying it was due to personal debts that she and her husband — both public servants — have to "put their kids to private school" — despite pretty much everyone calling for the White House to nominate Walden to the role. "If the requirement to take a job like this is that you have to be independently wealthy, then it will be a poorer place because you’ll be cutting out a lot of great talent," one friend told the Post. As @kevincollier tooted, it's "truly jaw-dropping." (via The Record, Washington Post ($))
~ ~
THE HAPPY CORNER
And that's enough of the news. Here's the happy corner. Keeping it light since 2018.
First up: @lmorchard was hacked by a cat. Sorry, but I don't make the rules.
Meanwhile, Mission Impossible hacked the blockchain. (via @matthew_d_green)
And finally this week. The valuable lesson here is that it's OK to ask for help — and probably better than you do, especially when you accidentally lock everyone out of the intranet by mass-resetting everyone's password.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat(?) is Ruby, who is extremely happy because she uses a password manager and MFA on every account. Setting a great example, Ruby. Many thanks to Dani D. for sending in!

Keep sending in your cyber cats! Send in your cyber cats (or non-feline friend) with a photo and their name, and they'll be featured in a newsletter.
~ ~
SUGGESTION BOX
That's all from this week's edition, what a busy one! I can't imagine this week will be much quieter... In the meantime, and as always, please drop me an email with any feedback you have. Otherwise, same time next week?
Take it easy, and have a good one.
—@zackwhittaker