this week in security — july 17 edition
THIS WEEK, TL;DR
L3Harris ends talks to buy NSO Group’s surveillance technology
The Guardian: Looks like U.S. defense firm L3Harris is dropping its bid to buy NSO Group's surveillance technology — the maker of the mobile spyware Pegasus. It comes not long after the White House warned any deal raised "serious counterintelligence" concerns because of the company's close ties with the Israeli government, months after NSO was put on a U.S. sanctions list, and was almost certainly the deal's death knell. The Guardian's @skirchy reports some government-insider bickering over the deal, but without the blessing from the U.S. government, L3Harris had no way but to back away from the table, leaving NSO's future in doubt.
More: Washington Post ($) | The New York Times ($) | @skirchy | @jsrailton
A key fob bug lets anyone remotely unlock and start Honda cars
The Drive: A bug in Honda key fobs, which researchers are calling Rolling Pwn, allows anyone to wirelessly steal authentication codes from a Honda car owner's key fob and be used to remotely unlock and start a Honda car. The Drive verified the bug and tried it out on a 2021 Honda Accord using a software-defined radio to capture and replay the stolen key fob codes. Honda initially flip-flopped on whether it was going to fix the bug, since rolling out updates to non-internet connected key fobs isn't easy at all — the car maker said it plans to have an "improved system" for future vehicles.
More: Rolling Pwn | Motherboard | TechCrunch

Amazon gave Ring videos to police without owners’ permission
Politico: Ring gave over 11 people's information without a warrant and without their consent so far this year, per a letter from a Ring executive to lawmakers this week. Ring video doorbells are always on and recording, and the Amazon-owned unit has cozy relationships with over 2,100 police departments across the United States. But police are also taking advantage of "exigent" circumstances that allow Ring to turn over video footage without legal process in emergency settings — but that's a broad category and Amazon doesn't spell explicitly what counts as an emergency. Worse, Ring doesn't disclose how many times it's given over data in allegedly emergency situations. According to Ring's latest transparency report, Ring processed 3,147 legal demands last year — up 65% on the year earlier — and turned over content data in about four out of 10 cases. But still no word on those emergency figures... it's almost like Ring doesn't want you to know.
More: The Intercept | Recode | TechCrunch
'Vault 7' leaker found guilty after massive leak of CIA secrets
Emptywheel: Former CIA engineer Joshua Schulte has been found guilty in all nine charges filed against him over what's been claimed is the biggest theft of classified information in CIA history. Schulte leaked a vast trove of hacking tools to WikiLeaks, which published the files as "Vault 7". The tools included zero-day exploits able to hack into iPhones, Android devices, and bug the microphones embedded in internet-connected televisions. The SDNY, which prosecuted the case, flat-out called Schulte's leak "espionage," which could lead to further fallout for WikiLeaks. The New Yorker had a great story a month ago on how the leak went down.
More: NPR | @emptywheel
European Central Bank head targeted in hacking attempt
Associated Press: Here's a pretty brazen social engineering attempt on one of the world's most powerful financiers: Christine Lagarde, head of the European Central Bank, was "recently" targeted by a hacking attempt but was "halted quickly." Turns out someone spoofed former German chancellor Angela Merkel's cell phone number and sent a text message to Lagarde asking her to send back an authentication code, which would have allowed the hackers to create a WhatsApp account in Lagarde's name, according to Reuters ($). It's not clear who was behind the attempt.
More: Reuters ($) | Bloomberg ($) | @hatr
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Here's how North Korean operatives are trying to infiltrate U.S. crypto firms
CNN: Here's a deeper dive by @snlyngaas on how North Korean hackers are posing as tech workers and getting hired at crypto-related companies to ultimately steal cryptocurrency funds and assets to fund Pyongyang's nuclear weapons program. "These guys know each other. Even if a particular IT worker isn't a hacker, he absolutely knows one," said one former FBI intelligence analyst. "Any vulnerability they might identify in a client's systems would be at grave risk."
CISA urges federal agencies to patch Windows bug actively exploited
The Record: CISA has ordered all federal civilian agencies to patch a Windows escalation of privilege bug because Microsoft says there is evidence that the bug is being actively exploited. The bug affects Windows 7 and Windows Server 2008 and later, and "allows an attacker to execute code as SYSTEM, provided they can execute other code on the target," per Trend Micro. Microsoft patched the bug, tracked as CVE-2022-22047, as part of its regular Patch Tuesday updates, but CISA warned agencies to act before August 2.
How a GOP-led Congress might change cybersecurity
Politico Pro ($): With the possibility of the Republicans taking Congress at the midterm elections later this year, Politico looks at how cybersecurity — although a rare area of bipartisan compromise — would fare under GOP leadership, and how cybersecurity funding and CISA's budget will likely be cut. @ericgeller's tweet thread is a helpful tl;dr.
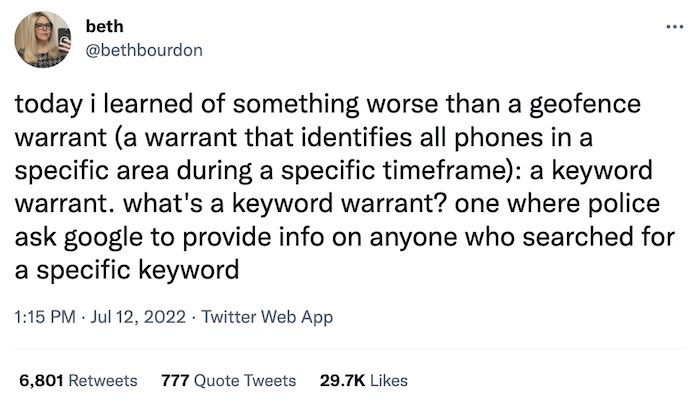
Reverse keyword warrants face first major legal challenge
Techdirt: FOIA lawyer @bethbourdon had a great tweet thread looking at reverse keyword warrants, a way in which law enforcement demands that Google provides information on anyone who searched a particular keyword at a given moment in time — such as before a crime was committed. These warrants are highly controversial because they can, just like geofence warrants, ensnare entirely innocent people. As such, these reverse keyword warrants are now subject to a legal challenge that could determine their constitutionality. NBC News has a good piece on where the court case is, and how these kinds of warrants could — and likely will — be used now that Roe v. Wade has been overturned.
A ransomware attack on a debt collection firm is one of 2022’s biggest health
TechCrunch: A little-known debt collection firm called PFC was hit by a ransomware attack that affected more than 650 healthcare organizations and facilities across the U.S. In a filing with HHS' Office of Civil Rights, which enforces the HIPAA privacy and security rules, PFC said 1.91 million patients are affected. That's just shy from the 2 million affected by a separate breach affecting a medical imaging company in March 2022. (Disclosure: I wrote this.)
macOS sandbox escape discovered and patched
Microsoft: Microsoft found and published a blog this week uncovering a sandbox escape in macOS, designed to keep app processes and data separate and isolated from one another. The bug could be used to "gain elevated privileges on the affected device or execute malicious commands like installing additional payloads."
~ ~
OTHER NEWSY NUGGETS
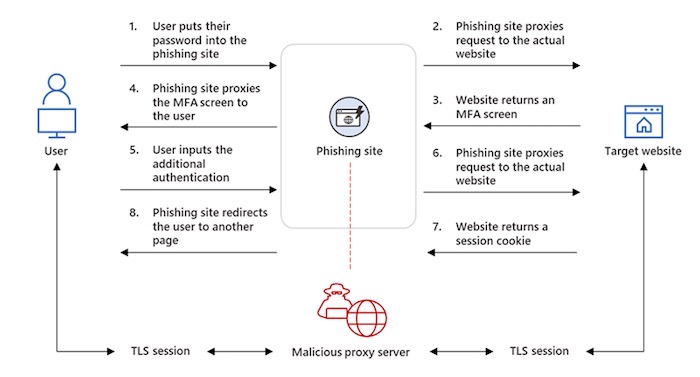
New phishing campaign skirts MFA: Ars Technica has a write-up on a new phishing campaign that's targeted at least 10,000 organizations since September and can hack users even with multi-factor authentication enabled. The attack works like a man-in-the-middle attack but using a proxy site run by the attackers. The user enters their credentials on a phishing page, the page passes the credentials to the real server that the user is trying to login to, which returns a session token letting the user log in. But the attackers copy the session token as it's sent back to the user via the proxy site. The user logs in, but the attacker now has the user's session token in hand, allowing the attacker to log in as that authenticated user. Microsoft's MSTIC explains more in a blog post.
FTC calls BS on anonymized data: The Federal Trade Commission warned this week that it is "committed" to fully enforcing the law against the illegal sharing of highly sensitive location and other health data, especially in light of the overturning of Roe v. Wade. The FTC said apps and services often make claims that data is "anonymous" or "has been anonymized," but that these claims are often deceptive or untrue. Even when data is said to be anonymized, it can often — very easily — be linked to real people with other supplemented data (which companies either have or can easily get, thanks to advertising IDs), explains @karlbode. "Companies that make false claims about anonymization can expect to hear from the FTC," the government agency said.
Log4j bug becomes 'endemic,' review board finds: CISA's Cyber Safety Review Board, the 15-member panel founded last year to help understand and improve the government's approach to cybersecurity, published its inaugural report into the Log4j vulnerability, which went wild ahead of last December's holiday season. The board's findings show that although the bug was discovered and reported by a cloud engineer at Alibaba, one of China's biggest cloud providers, the board found no evidence that China used its advanced knowledge of the bug to exploit networks. But the board warned that Log4Shell, as the bug became known as, has become an "endemic vulnerability," meaning unpatched versions of the omnipresent software could be with us for the next decade or so. Luta Security, run by @k8em0, has a blog post with guidance and recommendations for organizations. And check out @argvee, the board's deputy chair, who has a tweet thread on the findings.
Dozens of Lenovo laptop models affected by UEFI flaw: Dozens of Lenovo laptop models are vulnerable to a firmware flaw that allows attackers to install malware that's virtually impossible to detect or remove, per Ars Technica. The laptop maker released updates for the three flaws that can be exploited during the boot process, which can be used to gain persistence even if the operating system is wiped and reinstalled.
~ ~
THE HAPPY CORNER
Some really great news this week. Here we go:
First up, veteran cybersecurity reporter @kimzetter will keynote Black Hat this year, alongside former CISA director @C_C_Krebs. This makes Zetter the first journalist to keynote the annual hacker conference. Incredible news, and well deserved.
Meanwhile, speaking of journalists, I chatted with @runasand about her new startup, Granitt, which aims to secure journalists and other at-risk people — activists, politicians, lawyers, refugees and human rights defenders — around the world from threats, hackers, and powerful and well-resourced adversaries. I published our conversation this week.
Moving on. @CISAJen gets in on the "he's a 10" meme.

Meanwhile, wrong interview answers only:
And finally, @wendynather serves up some brutally honest out-of-office auto-responses for those heading into vacation season.
To send in good news for the happy corner, please reach out to: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
Meet Taro, this week's cyber cat. Sure, Taro looks cute, but will stealthily socially engineering you into belly rubs to steal your heart (and your passwords). Taro is definitely a red-teamer at heart. Many thanks to Kenly X. for the submission!

It's officially drought season in the cyber cats corner. Please send in your cyber cats! Email here with their name and photo, and they'll be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
That's all for this week. As always, the suggestion box is open or drop me an email. And if you liked this week's newsletter, please share with a friend or on your feeds. This coming week looks like it could be a busy one. I'll be back next week as usual with your roundup from the week. (And please send in your cyber cats!)
Take care, and be well,
—@zackwhittaker