this week in security — july 2 edition
THIS WEEK, TL;DR
Apple joins opposition to encrypted message app scanning
BBC News: Apple has become the latest tech giant to unceremoniously piss on the U.K.'s parade by joining Signal and WhatsApp in opposing the Online Safety Bill, a draft law that has little to do with actual online safety and more about an effort by the U.K. Conservative-run government to millions of people's messages under the guise of trying to stop child abuse. Signal and WhatsApp said they'd walk away if the U.K. brought in the law, saying it's not going to weaken its encryption for a select few million. Apple hasn't said it won't comply, but called on the government to "amend the bill to protect strong end-to-end encryption for the benefit of all." Them's fighting words (you'd hope, at least). Let's not forget much of the U.K. government is run on WhatsApp, so it's not just idiocy we're dealing with, it's hypocrisy, too.
More: The Verge | Dark Reading | Ars Technica
SEC targets SolarWinds CISO for rare legal action over Russian hack
Zero Day: The Securities and Exchange Commission, the government regulator overseeing securities and publicly traded companies, sent Wells notices to several SolarWinds employees indicating the agency may take legal action over how the company handled its 2020 breach by Russian spies. Wells notices can be indications that federal securities laws were violated. First reported by CNN, now Zetter reports that one of the Wells notice recipients was SolarWinds' CISO, who was head of the company's security at the time of the breach. Russian hackers eventually got access to the networks of federal agencies by backdooring SolarWinds' popular network monitoring tool, Orion. Zetter explains more about what it all means for SolarWinds.
More: CNN | Washington Post ($) | Wired ($)
LetMeSpy, a phone tracking app spying on thousands, says it was hacked
TechCrunch: LetMeSpy, a spyware app developed in Poland by Rafal Lidwin and used by tens of thousands of "customer" operators, was hacked. Niebezpiecznik, a Polish blog, first reported the breach, which was later confirmed on LetMeSpy's website. After the bloggers emailed LetMeSpy for comment, the hacker responded, saying it had carried out an SQL injection attack. I obtained the data soon after from DDoSecrets, and analyzed the data set. The spyware ensnared at least 13,000 compromised devices, with many location data points showing clusters of victims in the United States. That's another spyware maker we can add to the breached pile. (Disclosure: I wrote this story.)
More: Daily Dot | DDoSecrets | @zackwhittaker
~ ~
THE STUFF YOU MIGHT'VE MISSED
The tech flaw that lets hackers control surveillance cameras
BBC News: A vulnerability in Hikvision cameras — you know Hikvision, the surveillance device maker that develops torture and interrogation devices used against the Uyghir population — can be easily exploited to snoop on video camera footage from over the internet. Though the bug is fixed, some 100,000 cameras online worldwide are still vulnerable to exploitation. The U.K. (and other countries!) are swarming with Hikvision surveillance cameras. The U.K. government recently began efforts to remove Hikvision (and Dahua) cameras from government sites, citing national security concerns that they could be used for spying by China. More on BBC's Panorama if you're a U.K. resident.
U.K. NCSC publishes analysis of 3CX malware
National Cyber Security Center [PDF]: The U.K. government has published its technical analysis of Smooth Operator, the malware used in the supply chain attack at 3CX, the enterprise phone software maker that was hacked to compromise downstream companies running the software. The hack was ultimately blamed on North Korea, probably trying to pilfer some crypto for its "nuke the West" efforts, but maybe we can learn a thing or two about how they got in to begin with. NCSC has a PDF for that. For more, you can check out @patrickwardle, who examined Smooth Operator in two-parts. (via @campuscodi)
Cyberattacks on hospitals 'should be considered a regional disaster,' researchers find
NPR: Incredible reporting here on how cyberattacks on healthcare providers and hospitals should be considered a disaster zone, in large part because of the knock-on effects caused by outages affecting entire regions. UC San Diego examined an incident at one nearby hospital, Scripps Hospital, which was hit by a significantly damaging ransomware attack, and its research found that hospitals within close proximity to a victim of a ransomware attack experience serious resource constraints, "affecting time-sensitive care for conditions such as an acute stroke." Really fascinating stuff here. A long-read for the weekend crowd.
White House issues warning to U.S. firms interested in acquiring NSO's spyware
The Guardian: Here's a sentence I never thought I'd write: a Hollywood financier "best known for producing several Adam Sandler films" (say no more) is apparently interested in buying NSO Group's surveillance tech assets, including its notorious phone spyware Pegasus, according to The Guardian. But the U.S. isn't happy about it, and warned any potential buyer of the troubled spyware maker would likely involve a lengthy counterintelligence review that "will not automatically remove the designated entity from the entity list." In other words, buy it, but you'll face an uphill battle to do anything with it.
~ ~
~ ~
OTHER NEWSY NUGGETS
Suncor gas stations hit by cyberattack-related outage: A chain of gas stations across Canada continues to face credit and debit card processing outages related to a cybersecurity incident, which looks like it could be ransomware. In the briefest of mandatory stock market statements, Suncor confirmed transactions "may be impacted." The Suncor-owned subsidiary has around 1,500 gas stations across Canada. Oh no, will someone please think of the shareholders? (via CBC, Bleeping Computer)
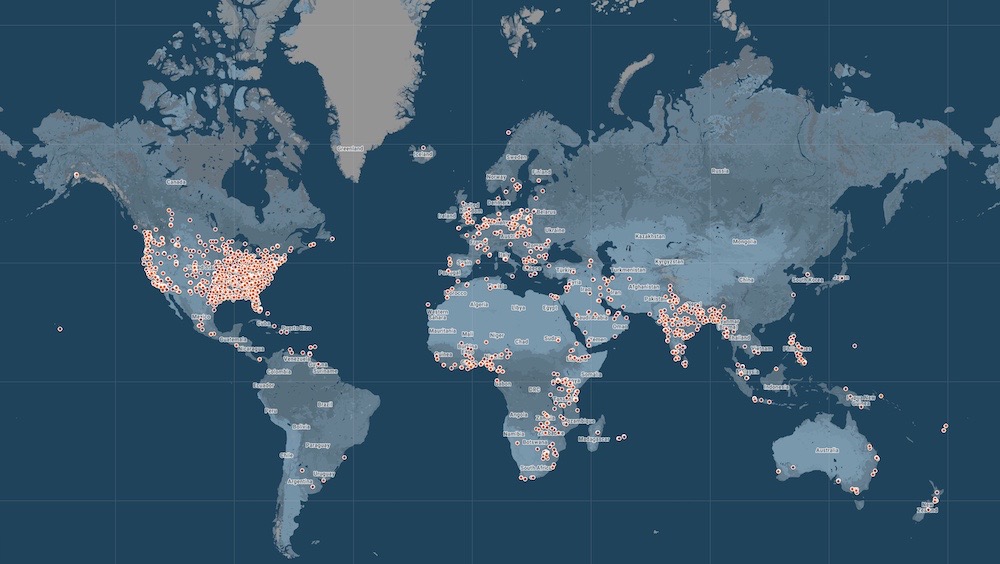
MOVEit? Yeah, right out of our hacked servers: The MOVEit mass-hack continues to ensnare more victims. Earlier this week, it was at 122 victims, now it's over 160 victims. Struggling to keep up? Ars Technica dug in, as did my TechCrunch colleague @carlypage, as by the end of the week more than 16 million victims were affected, per @BrettCallow. One of the worst breaches of the year — and it's only July. (via Ars Technica, TechCrunch)
Kazakhstan detains Russian cyber expert wanted by U.S., Russia: Kazakh authorities have detained Russian cyber expert Nikita Kislitsin, accused of breaking into LinkedIn and Dropbox in 2012. Interestingly, Moscow also wants Kislitsin, but for reasons that aren't yet clear. Kislitsin is currently head of network security at FAACT, a Singapore-based company spun off from Russian cybersecurity firm Group-IB, whose former-CEO remains detained in Moscow on treason charges. (via Reuters ($), Krebs on Security)
NJ cops need a wiretap to eavesdrop on your Facebook posts: Good news out of the garden state: New Jersey police do in fact need a court-ordered wiretap order before it can snoop on your Facebook messages (or near-real time content). Wiretaps are one of the most intrusive kinds of surveillance as they can tap real-time messages, calls and more, but to obtain one, cops need a very high bar of probable cause and evidence that other investigative measures would fail. Other tech giants Google and Microsoft joined the case in Facebook's defense, which definitely benefits them, but also benefits us in the process. (via New Jersey Monitor)
~ ~
THE HAPPY CORNER
Welcome back to the happy corner. Nothing but good things, as usual.
This week, check out this @joncallas snap. Beautiful as the photo itself is, it's also particularly lovely seeing two privacy-focused billboards next to each other competing for space. You have to appreciate — the companies and their problems notwithstanding — it's still good to see.

I both loved, and loathed, this Password Game. See how far you can get before you give up and read up on passkeys.
Meanwhile, practice safe browsing, use an ad-blocker.
And finally. @DavidLonghorn5 is right. We all knew it in our hearts. Plus, depending on how you see it, bonus cybercat.

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This is Zombi. She's always looking for cyber threats, no matter how small or where they might be. Doing great work, Zombi. Thanks to Ingrid P. for sending in!

Don't forget to send in your cyber cats, with a photo and their name, and they'll be featured in an upcoming newsletter. (Non-feline friends are also welcome!)
~ ~
SUGGESTION BOX
And that's all for this edition of ~this week in security~, thanks so much for reading!
As always, feel free to email me with any feedback, suggestions, or other thoughts you have about this week (or next week's) newsletter.
Until next week, have a good one (and happy July 4, if you celebrate 🇺🇸).
—@zackwhittaker