this week in security — july 20 2025 edition
THIS WEEK, TL;DR
U.K. reveals 2022 data breach exposed thousands of Afghans fleeing Taliban
The Guardian: We start this week in the U.K., where the government is mopping up probably one of the most serious data breaches in recent history. The 2022 breach, caused by a U.K. military official mistakenly emailing a spreadsheet of nearly 19,000 people — mostly Afghans trying to flee the Taliban but also some British spies and special forces personnel — which made it into the public domain more than a year later. Thousands of people on the list were relocated, costing more than £2 billion ($2.6bn). The government at the time gagged the press (and government ministers!) using a superinjunction, which barred anyone from disclosing the breach or even the gag order itself, fearing the disclosure would put those whose names are on the list at risk of persecution. By the U.K.'s own admission, it's not known how many people may have been killed as a result of the leak. This is a huge mess with real world consequences. I genuinely gasped while reading about the scale of this breach.
More: Gov.UK | BBC News | DataBreaches.net | Reuters ($) | Bloomberg ($)
Trump to spend $1 billion on offensive cyber operations while gutting cyber defense
TechCrunch: Moving onto the United States... Last week's newsletter noted that Trump's One Big Beautiful Bill Act, which passed into law earlier in July, cut more than $1.2 billion from the U.S. defensive cyber budget. Buried in the budget, however, was also a provision to add $1 billion for offensive cyber operations in the Asia-Pacific region, effectively allowing the U.S. to target China. It's not clear exactly what offensive operations would entail. Sen. Ron Wyden said in response that cutting a billion from CISA and defensive cyber programs while spending a billion on hacking operations would "invite retaliation." And worse, we might not even have the defensive capability to withstand such retaliation.
More: Forbes ($) | Fast Company | @lorenzofb
Microsoft to stop using Chinese engineers to work on U.S. military projects
ProPublica: ProPublica published a deep dive this week exposing a weakness in the way that Microsoft uses Chinese engineers to work on sensitive U.S. military cloud projects. These projects allow the Chinese engineers to work and code under the supervision of "digital escorts," who have security clearances but often lack the technical skills to know what the engineers are actually doing. One of the escorts told ProPublica that they rely on the goodwill of the engineers that what they code isn't malicious. The system, which has been in place for more than a decade, is only coming to light now — but already got the kibosh from the Pentagon. Secretary of Defense Pete Hegseth said in a video on Friday that China will "no longer have any involvement whatsoever in our cloud services."
More: Reuters ($) | ProPublica | @DAlperovitch
~ ~
THE STUFF YOU MIGHT'VE MISSED
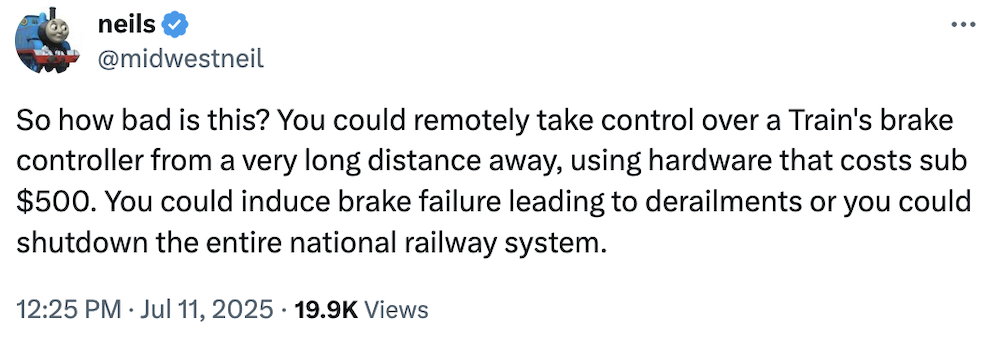
Hackers can remotely trigger brakes on American trains
404 Media ($): American trains are fitted with radio-controlled brakes that can be triggered from the driver's cabin (helpful, since trains can be very long!), but these radio signals can also be triggered by anyone using a software-defined radio within proximity of an affected train, "new" research has found. Who knew and how new? Well... actually, the industry has known about the vulnerability for years, but by CISA acknowledging the bug this week, this might actually light a fire under the train operators who rely on these buggy breaks. Really great thread from @midwestneil, who reported the bug.
Hackers are planting custom backdoors on end-of-life SonicWall devices
Google Cloud: Google has sounded the alarm after discovering a new hacking group compromising SonicWall Secure Mobile Access appliances, which big companies use to allow employees access to the network using their mobile devices. Little's known about the hackers or their motives, but clearly enough activity for Google's researchers to go public. The affected servers are end-of-life, so won't get patches, but are still widely used in enterprises. More from Ars Technica.
U.K. age verification checks to come into force July 25
BBC News: Age verification checks will be enforced starting July 25. The BBC has a pretty bleak picture into how these online age checks will work, who will get the data, and what some of the privacy issues are. The obvious concern is that this will end up with people's data getting leaked or stolen (let's hope it's the politicians who are compromised first!). Collecting data isn't the answer here. One expert (rightfully) told the Beeb: "The only non-hackable database is no database at all." Preach.
Hackers exploiting blind spots by hiding malware inside DNS records
Ars Technica: TXT records are public DNS/internet records typically used to prove domain ownership when setting up an online service, but TXT records can realistically include anything from ASCII art to malware. New research from DomainTools found hackers were able to host a malicious binary within DNS records by breaking up the payload into chunks, encoding the files into hexadecimal, then hosting the broken up file as TXT records on an attacker-controlled domain. This could be a way to sneak malware onto a company's systems via network traffic that can be difficult to monitor. Interestingly, the use of TXT records have also been seen containing prompt injections used to mess with drive-by AI agents.
Misbehaving AI Corner, featuring Gemini, Grok-4, Claude, Meta flubs
SecurityWeek, TechCrunch: Speaking of misbehaving AI agents... Here is... *drumroll please* Misbehaving AI Corner™. (I can't think of a better name.) In case you thought AI was in any way ready for use (it's not), this week we saw: Google's Gemini being tricked into showing a phishing message hidden inside an email; X's Grok-4 jailbroken to produce a recipe for molotov cocktails; Anthropic's Claude hacking itself; and, Meta confirming it fixed a security bug that allowed anyone to access anyone else's chat prompts and AI-generated content (disclosure: I wrote this story!). And that's not all: MIT Technology Review ($) reports a major open-source training set contains "millions of images of passports, credit cards, birth certificates," and more — so, yeah, all in all, not a great look (or week) for AI. Maybe it's time we stop feeding AI our most personal data? (I wrote this one, too!)
How China's "honkers" became the nation's top cyberspies
Wired ($): @kimzetter dives into some hacker history with a new story on Honkers, a.k.a teens and young Chinese hackers from the late 90's that launched "patriotic cyberattacks" against Western targets deemed disrespectful to China. These are the hackers who have, over time, essentially become some of China's most prolific cyberspies. Here's the original research [PDF].
Microsoft can't protect French data from U.S. government access
Ben Werdmuller: Sounds so simple and perhaps obvious, but this is very important to note. If you interact with a company from another country, those laws can (and usually do!) still apply. The same works when U.S. companies, like Microsoft, provide services to Europe. If the U.S. demands access to that European customer's data, it can pressure the U.S. company into granting that data, as dug into by @ben (via PPC Land). Trust alone isn't a data protection strategy. (Damn, I wrote about this very issue back in 2011 — woooof, I got old!)
~ ~
OTHER NEWSY NUGGETS
SharePoint Server zero-day under attack: Well this is rare, uhh, weekend breaking news but, Google says a zero-day in self-hosted/on-premise Microsoft SharePoint is under active attack. News of the critical bug came out Saturday. Microsoft said it's "aware that an exploit" for the bug exists. If you haven't already, check out Microsoft's post, patch, and then run some logs to see if you've been exploited. (via @cR0w, MSRC)
Rough week for Russia: Russia was hit with a trifecta of cyberattacks this week. A major drone supplier was hacked and data destroyed (Ukraine took credit for this). A top Russian gas supplier was also hacked, as was a major vodka producer. You know it's serious when the Russian vodka supply gets hit. (via Kyiv Independent, The Record)
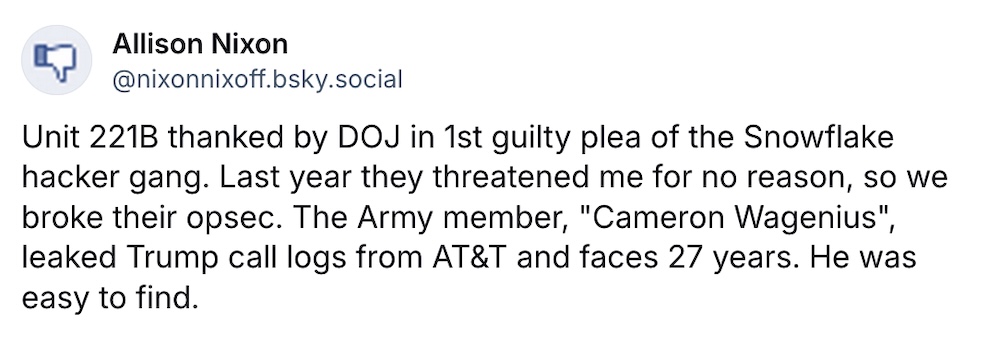
U.S. Army soldier pleads guilty... again: Former U.S. Army soldier Cameron Wagenius has pleaded guilty for a second time; now, he'll face jail for charges stemming from hacking and extortion related to hacking phone companies. Wagenius pleaded guilty earlier this year to hacking and stealing customer data from telcos AT&T and Verizon. (via Justice Department, TechCrunch)
Co-op confirms millions hit by breach: The U.K. retail giant Co-op has revealed "all" of its 6.5 million members had personal information stolen in its recent cyberattack. The stolen data includes names, addresses and contact information. Still no word yet on the number of people affected by other breaches in the same Scattered Spider hacking campaign, notably Marks & Spencer's. (via BBC News)
China targeting Singapore's infrastructure: Singapore is responding to cyberattacks targeting its critical infrastructure and other essential services, per the national security minister, who blamed the hacks on UNC3886, which Google's Mandiant says is a China-nexus spying group. Reuters ($) separately reported that China-aligned hackers are targeting Taiwan's chip industry and investment analysts, at a time when China is ramping up hacks on its regional neighbors. (via Reuters ($))
New SS7 exploit under attack: Security researchers at Enea have caught a surveillance company in the Middle East exploiting a new attack capable of tricking phone operators into disclosing a cell subscriber's location. I wrote about the findings in for TechCrunch (disclosure alert!). The bug involves exploiting a bypass attack in SS7, the protocols used by global phone networks to route calls and texts around the world. SS7 has long had security problems, and surveillance companies know this. (via TechCrunch)
Five Four-and-a-Half Eyes: Mark Warner, the top Democrat on the Senate Intelligence Committee (read: knows a lot of highly classified stuff) escalated his criticism of the U.S. top spy Tulsi Gabbard, saying Gabbard politicizing the role makes her unfit for the job. As such, Warner said he believes that the Five Eyes intelligence partners — Australia, Canada, New Zealand and the U.K. — are dialing back how much intelligence they are sharing with the United States. (via Politico)
~ ~
~ ~
THE HAPPY CORNER
Welcome back to the glorious, wonderful, and peaceful happy corner.
A spin-off from a classic xkcd, I loved this @bolson.org post this week. This is incredibly spot-on.
Ever wonder what happens when you reach the error message... for the error message? Well, someone on Hacker News found Gmail's.
And, since it's a short one this week, here's a double-bonus cybercat.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Double... double cybercats this week: here are Pien (left) and Muis (right), a very cute brother-sister pair of cybercats, who can be seen here once again interfering with their human's security work by demanding urgent pets and snuggles! Thanks so much to Rick R. for sending in!

Ding-dong: it's the cybercat gong! Got a cyber-cat or a non-feline friend? Send in an email with their photo and name and they will be featured in a future newsletter!
~ ~
SUGGESTION BOX
Well that's all there is for this week's news! Join me again next weekend for your usual roundup of everything you need to know in cyber. As always, if you want to get in touch about the newsletter, please do!
For now, have a great and enjoyable rest of your weekend. I really appreciate you for reading!
Ta ta,
@zackwhittaker