this week in security — july 21 2024 edition
THIS WEEK, TL;DR
CrowdStrike outage causes travel and business chaos worldwide
BBC News: Well, that was a Friday... i..is everyone OK? By now, the biggest non-cyber cyber story of the year was CrowdStrike rolling out a buggy update that crashed much of the world's Windows enterprise computers. More than 8 million Windows PCs were bricked (until they can be manually unbricked, per CrowdStrike's remediation advice), but the full picture of damage caused by the outage won't be known for some time. Flights grounded. Cash registers failed. Businesses couldn't business. Some government departments had to close for the day. (What also didn't help was Microsoft's cloud going down at around the same time, though unrelated, we're told). To call this the biggest IT outage (not caused by DNS) to date is probably about right. Or, at least, so far. (Keepin' it light!) CISA said the outage wasn't caused by a cyberattack but warned all to keep an eye on bad actors trying to take advantage of the situation. At least we got a fresh xkcd cartoon out of the mess...
More: CrowdStrike | Microsoft | Wired ($) | Associated Press | TechCrunch

Kaspersky Lab closing U.S. division; laying off dozens of staff
Zero Day: Just as the U.S. government's new sales ban on Kaspersky software was coming into effect this week, Kaspersky announced it was closing its U.S. division and laying off around 50 staff — including the company's spokesperson who confirmed the news. Kaspersky cited the ban as the reason for the shutdown and layoffs, as the antivirus maker won't be allowed by law to sell its software any longer or roll out updates (which will result in the software's degradation over time). Kasperksy said it was initially going to fight the ban; it's not clear what changed. Kaspersky is headquartered in Russia and that, U.S. officials say, makes the company vulnerable to provide compelled help to the Russian government.
More: Bleeping Computer | TechCrunch | @hacks4pancakes
AT&T paid a cybercriminal $370,000 to delete stolen phone records
Wired ($): Double-dose Zetter, after breaking another major scoop this week: AT&T paid a cybercriminal who stole phone records on "nearly all" of its customers a sum of $370,000 (down from $1 million) to delete the cache of files taken from the phone giant's Snowflake instance. AT&T believes the only copy of the data was deleted, but — of course — risks remain and there are no clear guarantees that the crim kept their word. AT&T was one of the biggest companies embroiled in the Snowflake customer data breaches — in large part because neither Snowflake nor AT&T protected the data with multi-factor security. The data includes phone records and texting metadata on around 110 million AT&T customers — and many more whose non-customer data was included.
More: Bloomberg ($) | Nextgov | @kimzetter
USPS shared customer postal addresses with Meta, LinkedIn and Snap
TechCrunch: Not so great news if you're one of the 60+ million USPS customers who use Informed Delivery, the feature that lets you see photos of your mail before it arrives (for that extra anxiety you need in life, obviously), as USPS was sharing customer postal addresses with advertisers like Meta, LinkedIn and Snap. The postal service was using hidden pixels that scrape information from the page for analytics, but that resulted in the sharing of addresses on the USPS customer's dashboard with those tech companies. USPS pulled the trackers, but wouldn't say if it would ask the tech companies to delete the data. (Disclosure: I wrote this story!) USPS has long sold customer address information to data brokers, per Forbes ($), which resell this information to anyone who wants to buy it, but this is a lose-lose situation for customers and USPS.
More: SC Media | @zackwhittaker
~ ~
THE STUFF YOU MIGHT'VE MISSED
Unauthenticated API bug spilled Deutsche Telekom customer data
Borncity: German security expert Lilith Wittmann discovered [auf Deutsch] an unprotected API from Deutsche Telekom that allows anyone to retrieve details about landline connections via their internet access. That data includes the customer's permanent ID, which can be used to track subscribers on the internet. Wittmann set up a website that allowed anyone to test for themselves. Look back, unauthenticated APIs have caused a ton of problems recently. Think Peloton, Twilio, Optus, Ivanti...
New Firefox feature switched on by default aids advertisers
Mozilla: Firefox browser maker Mozilla has introduced a new feature (if you want to call it that) by "working with Meta" (and others) to provide an allegedly privacy-first way of tracking ad conversions. (C'mon, Mozilla, there's a reason why so many people use Firefox and not Chrome...) This feature caused a ruckus as it was enabled by default without giving Firefox users the chance to opt out first. You can, however, switch it off for good, per @jschauma's guidance. Also, use an ad-blocker like uBlock Origin or Wipr if you're not already!
FBI used Cellebrite device to crack attempted assassin's phone
Bloomberg ($): The FBI used Cellebrite phone cracking equipment to break into the phone of the shooter at Trump's rally last week. Cellebrite's equipment didn't initially work on the shooter's newer Samsung model — newer devices often don't, per documents leaked to 404 Media ($). In the end it took about 40 minutes (including a new Cellebrite software update) to crack the phone's passcode. Yes, despite claims that the FBI can't break into a ton of phones, it's actually never been easier for the federal agency to bust into our seized phones and acquire our data. Let's not forget the time the FBI almost destroyed privacy as we know it by demanding Apple build a backdoor for the iPhone — yeah, and not so long ago!
Microsoft links 'Scattered Spider' crims to ransomware attacks
Bleeping Computer: In a series of tweets, Microsoft said it's seen evidence that the cybercriminal crew known as Scattered Spider (read: bored but highly skilled teenagers on Telegram with terrible OPSEC), which allegedly broke into MGM Resorts last year, are linked to ransomware gangs based in Russia. Remember, Scattered Spider is a major player in "initial access" — they break into networks and, in some cases, hand off or deploy malware from other threat groups (like ransomware). What's clear is that these kids, although young, are incredibly motivated and highly capable, and probably one of the biggest actual threats to U.S. businesses and national security of late. Underestimating this threat is what got us here, frankly.
Simple bug in traffic lights controller could cause traffic jams
Red Threat: Security researcher Andrew Lemon dug into an old traffic lights controller (a device that controls traffic lights, who knew?) thinking he would spend a fair amount of time examining the devi... ohhh there's a huge bug already and that didn't take long at all. Turns out a popular Intelight X-1 device has an authentication bypass bug that grants access to its web interface. When Lemon went to report the bug to the company, he got back a legal threat — which he published (and good for him for doing so). In speaking with my TC colleague @lorenzofb, Lemon said the bug could've been exploited to cause traffic jams and other roadway chaos.

~ ~
OTHER NEWSY NUGGETS
Rite Aid? Ransomware aid, more like: U.S. drug store giant Rite Aid has experienced yet another data breach — this time caused by ransomware. Per a data breach notice filed with Maine's attorney general, some 2.2 million people had personal information stolen in the incident. RansomHub, the recently formed cybercrime group, took credit for the breach. RansomHub also took credit for the massive data breach of health and medical data from Change Healthcare earlier this year. (via Ars Technica)
Data brokers still exposing spies (Germany edition): Reporters with BD and Netzpolitik obtained a location data set from a data broker that contained location histories on employees at the BND, Germany's foreign intelligence service, and in one case track the precise movements of someone highly suspected of being an NSA employee in Germany. Again, this data is just available for sale. In the United States, that's a big legal argument under way — if it's purchasable, why need a warrant? (No, but really.) (via Bayerischer Rundfunk, Netzpolitik [auf Deutsch])

India's WazirX crypto reserves hacked: Crims stole some $230 million in crypto — around half of the crypto exchange's reserves — in a cyberattack. The Mumbai-based firm said one of its multisig wallets was compromised. (A multisig wallet requires two or more private keys for authentication.) In this case there were five signatories. The firm halted withdrawals while it investigates. Eyes are already focused on North Korea, which has long shown to be keen to steal and use crypto to fund its nuclear weapons program. (via TechCrunch)
U.K. plans cyber law shakeup: Zzz...zz. zzz... ..!! …w..What is happening? That's the U.K. waking up to its ransomware problem, finally, thanks to the new government in office. After NHS trusts across London were hit by a major ransomware attack at pathology lab Synnovis, the U.K. Labour government said in the King's Speech this week (which is actually written by the new government) that it will roll out a new cyber bill. The bill aims to "shore up defenses for supply chains" and "mandate more comprehensive government reporting if companies are hit with ransomware attacks," per Bloomberg ($), and more per another analysis. It only took a decade of largely ignoring the problem and a change in government to get here. (via BankInfoSecurity)
a16z fixes bug, reneges on bug bounty: Security researcher xyzeva found an inadvertently public environment variables file (which contained a list of private keys, passwords, and suchlike) on venture capital giant's a16z's website that exposed some data about its portfolio companies. When inquiring about a bug bounty, a16z seemed game, until it wasn't. a16z didn't seem to want details of the issue going public — even though that's what disclosure is. It's not like a16z, with $35 billion in assets under management, can't afford it. (via xyzeva)
~ ~
~ ~
THE HAPPY CORNER
Yeah, that was a week, and it pretty much felt like this:

But breathe. Take a moment in the happy corner.
First up... His Majesty requests we begin our emails with a duel. Well, not quite. But wouldn't this be nice?

Here's a nugget of common sense, but all too often overlooked (because your work email isn't forever and your IT admins can read them!) Thanks to area fediverse sysadmin, @CrabbyIT, for this solid advice.
And finally, this week. Speaking of work laptops (but maybe don't — or maybe? I'm not your dad) here's one to try out after this fustercluck of a week. This GitHub project, Open and Shut, turns your laptop screen lid into a Morse Code keyer. Vent some anger in encoded text!
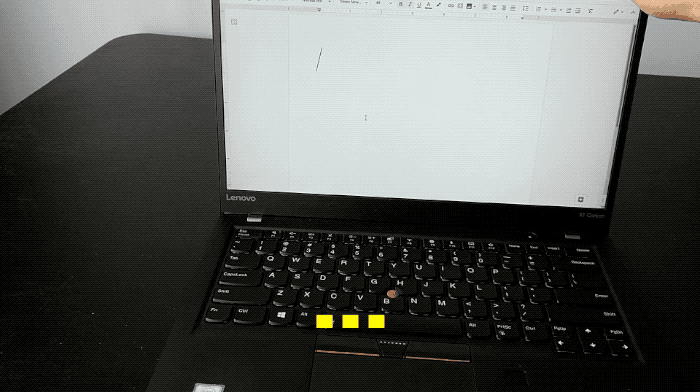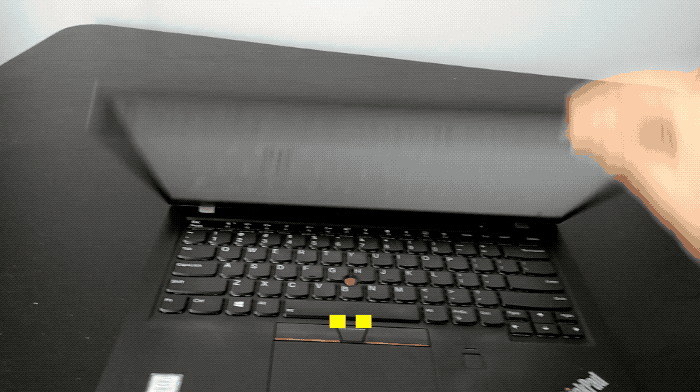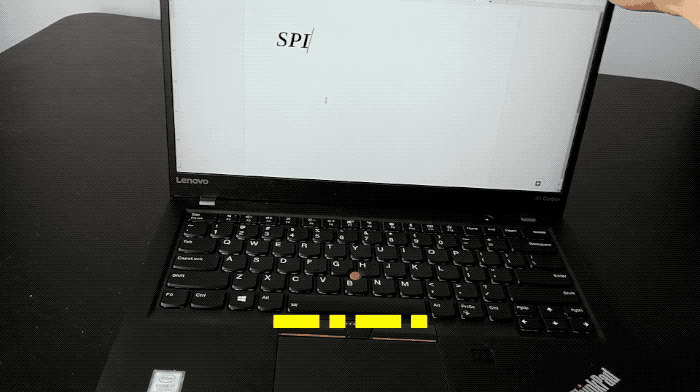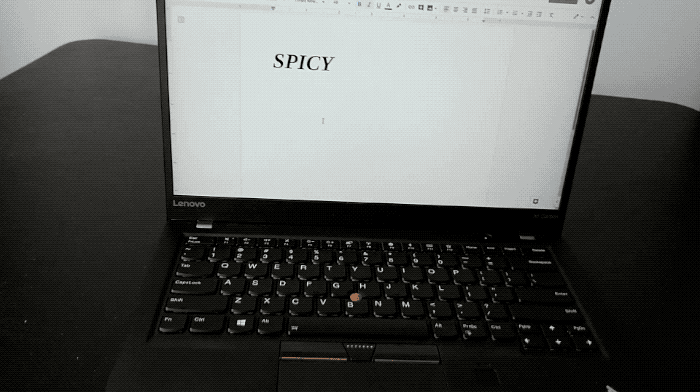
... .--. .. -.-. -.-- !
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's duo of cyber cats is Arya (left) and Batman (right) performing important cyber van cat duties. Looks like everything's in ship shape! Many thanks to Emily for sending in!

Send in your cyber cats! Feel free to drop me an email with a photo of your cyber cat (or your non-feline friend!) with their name and they'll be featured in an upcoming newsletter. Updates are always welcome — send 'em in!
~ ~
SUGGESTION BOX
And that was Hell Week. #hugops to all those involved in remediation and recovery this weekend. Rest, eat, hydrate, and take care of yourselves.
As always, my sincere thanks for reading. If you have any feedback (or anything else you want to submit) for the newsletter, you can reach out any time. And do please send in your cyber cats!
Peace,
@zackwhittaker