this week in security — july 23 edition
THIS WEEK, TL;DR
Biden admin. announces cybersecurity labeling program for smart devices
White House: For years, the "s" in IoT has stood for security. Now, the Biden-Harris administration is rolling out a new cyber nutrition-style label for smart devices with the aim of helping Americans know which devices are better protected against cyberattacks. The idea is that by 2024 when the labeling program kicks off, consumers should be able to see a smart label and be reassured that the device or appliance meets NIST's security standards, such as the use of strong passwords, data protection, and software update capabilities. Nice idea in theory; the program will eventually include Wi-Fi routers at launch, too, since home routers can also be a target for botnets. I'd show you what the label would look like, but... nothing from the White House just yet.
More: CNN | The Verge | Stacey on IoT | @CISAJen
U.S. Commerce Dept. adds Cytrox and Intellexa to export control list
Reuters ($): Spyware makers Cytrox and Intellex are going to have a really hard time doing business with U.S. companies now that they're on the Commerce Dept.'s entity list, the economic sanctions list that bans U.S. businesses from transacting with them, from software licenses to Post-it notes. Adding the surveillance firms to the list is part of the government's efforts to crack down on the misuse of commercial spyware to snoop on journalists, activists and others by their nation-state customers. Cytrox makes the Predator spyware, which is sold by Intellexa. The Irish Times did a great job of parsing Intellexa's financials, since the company is registered in Ireland.
More: Cyberscoop | Wall Street Journal ($) | @criticalvas
Microsoft to make some security tools free after suspected China hack
Wall Street Journal ($): Microsoft will make security logs and tools available to customers for free. These logs can help incident responders find and investigate suspected breaches. These are the same logs that could've helped federal agencies respond faster to a recent espionage-driven campaign that allowed China-backed hackers to forge keys used to break into corporate email accounts, such as those belonging to several federal government departments and the occasional U.S. ambassador. Logs will be made available starting September. Better late than never, but also too little too late for the organizations (and government departments!) already hacked. The two things can be true.
More: Microsoft | CNN | @ericgeller
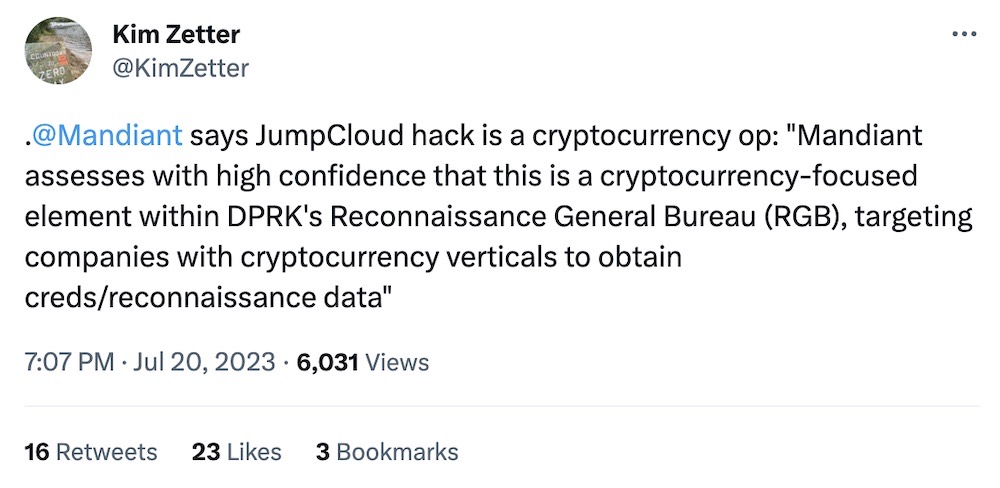
JumpCloud discloses breach by North Korea APT group
Ars Technica: JumpCloud, a company that offers IT services for hundreds of thousands of corporations and organizations, told customers last week that it reset their customer API keys citing an ongoing security incident. Now, it seems JumpCloud was breached by a North Korea-backed hacking group in order to target a handful of cryptocurrency customers — less than five customers, the company said, and fewer than 10 devices. Security researchers at SentinelOne and CrowdStrike earlier pinned the blame on North Korea's Lazarus Group, which is known for crypto raids in order to fund the regime's nuclear weapons program. News of North Korea's involvement broke in RiskyBiz's newsletter, and later by Reuters ($).
More: JumpCloud | SentinelOne | Bleeping Computer | @kimzetter
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Amazon to drivers: Don't worry about now-public in-van surveillance
Motherboard: Numerous posts on Reddit show Amazon delivery drivers' actions on the road, which isn't unheard of, but the frequency of these videos leaking online is on the uptick. The videos show the in-vehicle surveillance systems working (and sometimes failing) and monitoring drivers at all times, even while they drive. Very creepy stuff. Workplace surveillance is getting out of control. More from The Verge, too.
Bulk of Dutch patients' data stored on commercial firm's server
NRC: Dutch media reports (translated) that most medical records in the care of Dutch family doctors are copied and stored on a weekly basis to a server run by a commercial software company, but without the knowledge of the patients. The Canadian-run software firm Calculus in Leiden allows doctors to share information about patients. But doctors are worried (remember, GDPR exists here) that Calculus stores too much data in one place, and feel like they have no choice but to use the system. Fascinating reporting.
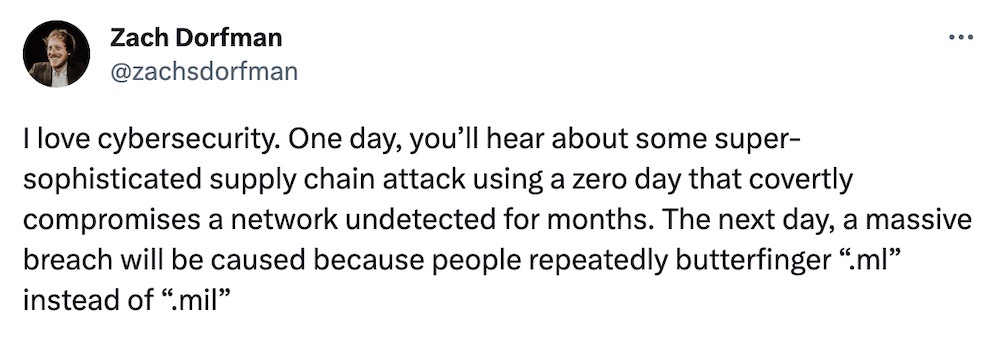
Typo leaks millions of U.S. military emails to Mali web operator
Financial Times ($): Speaking of other government-related security mishaps, this is a good one: Millions of U.S. unclassified military emails ended up redirected to Mali because of typos in the U.S. military's .mil email address, which is remarkably similar to Mali's top level domain .ml. Johannes Zuurbier, a Dutch internet entrepreneur who has a contract to manage Mali’s country domain, has been warning about this for years and trying to get the U.S. to take this matter seriously. But officials haven't, clearly. Zuurbier said he ended up receiving "X-rays and medical data, identity document information, crew lists for ships, staff lists at bases, maps of installations, photos of bases, naval inspection reports, contracts, criminal complaints against personnel" and more. More from the BBC News here. Incredible to think that this, in the year of 2023, is a security issue, but here we are. To wit, @zachsdorfman:
Google apologizes for recent accidental VirusTotal data exposure
VirusTotal: Google-owned VirusTotal, an online malware scanner and repository used for malware analysis, has apologized after an employee uploaded a CSV file containing information of its Premium account customers, some 5,600 names, including employees at U.S. Cyber Command, the U.S. military, the Justice Dept., the FBI, and international agencies, including one clandestine German agency. Google said it was a human error and not due to bad actors. You can read the original report via @hatr.
Fake passports, real bank accounts: How TheTruthSpy stalkerware made its millions
TechCrunch: A Vietnam-based startup called 1Byte, which develops and sells TheTruthSpy stalkerware, created a network of fake American sellers using forged U.S. passports, driver's licenses, and SSNs to evade detection for years, while funneling payments from Stripe and PayPal accounts into real bank accounts. I spent about a year on this story, tracking down this American network of sellers. Admittedly, the penny dropped after realizing the people behind the selling... didn't exist. This is how the spyware maker made at least $2 million selling TheTruthSpy. (Disclosure alert: I wrote this story.)

~ ~
OTHER NEWSY NUGGETS
Draft law blocking data broker sales progresses: A smidgen of good news as draft House legislation that would prevent data brokers from selling consumer data to law enforcement and federal agencies has moved forward. Sen. Ron Wyden (D-OR), who wrote the original Senate bill called the Fourth Amendment is Not For Sale Act, praised the passage of the House bill. Much of the bill came to fruition following reporting that showed how sensitive location data collected from consumers' devices was being used to spy on Muslims and also sold to the military. (via Cyberscoop)
MOVEit hack hits 370 organizations: The MOVEit mass-hack may be one of, if not the most widespread file transfer hack recorded. The Clop ransomware group continues to take responsibility for the breaches, which involves now-fixed zero-days that allowed hackers to break into these systems storing sensitive data. Now we're at 370 organizations confirmed affected, with the number of individuals' data surpassing 20 million. But, given only a fraction of total affected organizations have come forward, the victim count is expected to be magnitudes bigger. My TC colleague Carly Page has an update on the ongoing mess, including new corporate victims. @brett has some of the latest numbers. (via SC Magazine)
Thousands of Turkish TikTok accounts hacked before election: Turkish president Recep Tayyip Erdoğan eked out a narrow win in his presidential reelection in May, but Forbes reports that as many as 700,000 Turkish TikTok accounts were hacked in the run-up to the big day, allowing access to private information and control of their accounts. TikTok was made aware of the incident a year earlier, which stemmed from its use of "greyrouting," where SMS codes for accounts were routed to locations that allowed TikTok to save money, but at the price of exposing the messages to interception. Forbes said incidents like this have the capacity to move markets and swing elections. (via Forbes ($))
~ ~
THE HAPPY CORNER
Finally, the happy corner. Breathe in, breathe out. This is you-time.
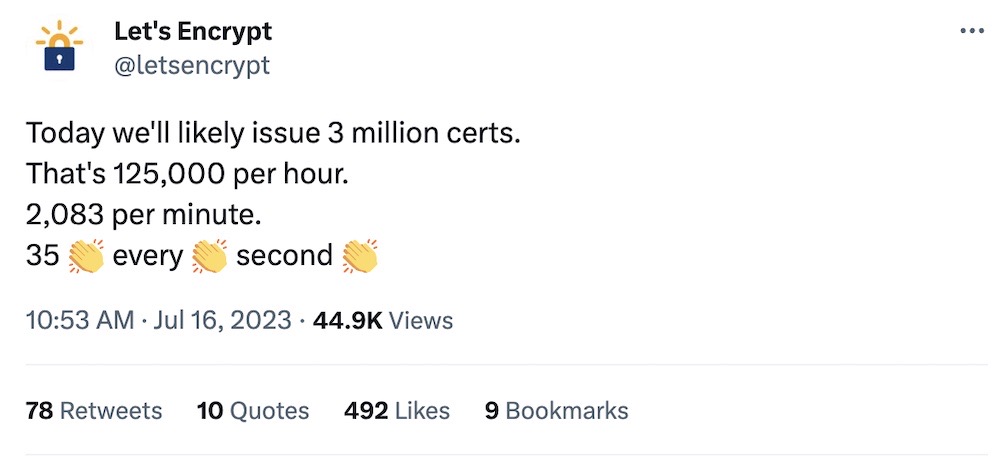
Congratulations to @letsencrypt, everyone's favorite free TLS/SSL certificate issuer, which this week issued three million certificates last Sunday alone. It's thanks in large part to free certificate providers like Let's Encrypt that the vast majority of the web is encrypted in transit.
Follow along this wonderful puzzle of what happens when a broken ThinkPad starts beeping in musical tones. I won't spoil the ending, but this is one incredibly smart way of figuring out what the very simple answer is.
(Don't) spare a thought for this hapless bad actor, who accidentally compromised their own computer with information-stealing malware, exposing their real-world identity, according to findings this week. You have to laugh; well, maybe not if you're the threat actor in question whose online handle just got published.
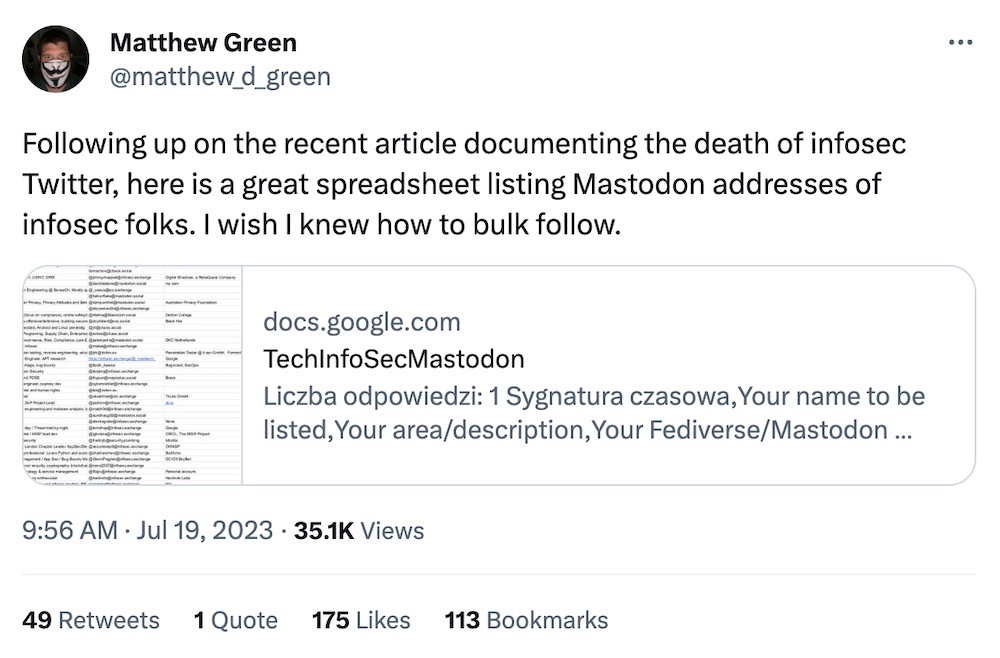
And finally. As the great Twitter exodus continues, @lukOlejnik has an updating list of Mastodon handles that you can follow to get your regular doses of infosec goodness. It's a long, long Google Doc, but it's packed with all the regular people you know and love.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet Dr. Ada Lovelace, this week's cyber cat, who as you can see is developing her intrusion detection skills. Many thanks to Eric for sending in!

Send in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's all I have this week. I'll be back next week with the usual round-up from the past seven days of cybersecurity mayhem. In the meantime, you can reach me by email with any feedback you have.
Chat again next weekend.
—@zackwhittaker