this week in security — july 24 edition
THIS WEEK, TL;DR
DOJ seizes $500K from North Korean hackers who hit U.S. medical organizations
CNN: It was fed week in New York as one of the top law enforcement conferences returned to Fordham University, where top DOJ cyber lawyer Lisa Monaco declared an "aggressive U.S. strategy to claw back money for victims of ransomware." Praising a relatively paltry $500k from a recent North Korea-run ransomware operation targeting healthcare organizations (compared to the $730 million raked in by ransomware last year) it's largely thanks to the researchers in the private sector who are helping the feds score wins against the state-sponsored hackers. The FBI admitted it's "never going to indict our way out" out of ransomware hacking threats, but FBI director Chris Wray said exposing operations is an "important component to stopping them," alongside a combination of arrests and disruptions. Wray added: "A lot of people don't understand the speed or agility with which these things are happening." Yeah, at a glacial pace. Of the few cyber wins that the feds touted, the FBI said it was "going after" people who threaten U.S. election workers, plus, a senior FBI official revealed that the GRU botnet it took down a few months ago was dubbed Operation Johnnie Cache. Heavy sigh.
More: Wired ($) | Cyberscoop | The Record | @kevincollier | @snlyngaas
Russia released a Ukrainian app for hacking Russia that was actually malware
Motherboard: Google researchers discovered a Russian malware campaign disguised as a Ukrainian app that claimed it would launch distributed denial-of-service (DDoS) attacks against Russian targets, such as members of the Ukrainian IT Army. Except it wasn't. The app, which wasn't in Google Play and had to be sideloaded, was actually intended to learn about those who were using the app — presumably would-be hackers wanting to join Ukrainian resistance — but the effort largely failed as the number of installs was "miniscule." Still, it was a smart effort, even if it was largely a flop. Speaking of the IT Army, @lorenzoFB dove into the Ukrainian state-backed IT Army, a "decentralized" collective of hackers, which got off to a bumpy start around the initial invasion but has been a critical cyber force in targeting Russian businesses and government systems as part of the country's wider resistance against the Russian forces. It's a brilliant read. Slava Ukraini.
More: Google TAG | Cyberscoop | Cisco Talos | @argvee | @billyleonard
Homeland Security records show 'shocking' use of phone data, ACLU says
Politico: Twice in two weeks, @alfredwkng is delivering back-to-back bombshells. A cache of documents obtained by the ACLU show Homeland Security bought vast amounts of commercial location data, sourced from apps installed on millions of phones, gaining the ability to track granular phone data as often as 26 times a minute without a warrant. The amount of data collected is staggeringly huge, and included major cities like Los Angeles, New York, Chicago, Denver — and non-U.S. cities like Toronto and Mexico City. The data was sold by location data brokers Venntel and Babel Street. So who's pulling the parachute cord? Sen. Ron Wyden has the Fourth Amendment is Not For Sale Act, or S. 1265, which would ban government agencies from warrantlessly buying location data if passed. But time is running out in this legislative session and Senate leadership are dragging their feet.
More: Motherboard | @jakelaperruque
FBI forced suspect to unlock Wickr with their face
Forbes ($): You know how some end-to-end encrypted apps like Signal, WhatsApp and Wickr have "screen locks" that require your face or fingerprint to access your conversations, even when your phone is unlocked? Turns out the feds are exploiting a weakness in the Fifth Amendment, which protects against self-incrimination, because police are allowed to force suspects (with a warrant) to unlock their messaging apps with their biometrics. It's because of a quirk in the law that allows police to use what a person has, like a biometric, but not what they know, such as a passcode or a PIN. What's eye-opening here is that while it's common for police to force suspects to unlock their phones, but not their apps. Remember, always use a strong phone PIN — and nothing else.
More: @iblametom | @caseyebabb
Data breach corner: JusTalk, Neopets, Twitter
Bleeping Computer, TechCrunch: This week I reported on a huge cache of unencrypted JusTalk user messages and conversations found online that show the messaging app, which claims to be end-to-end encrypted, actually isn't. JusTalk has 20 million global users. (Disclosure: I wrote this). Plus, virtual pet site Neopets saw the theft of 69 million accounts this week. And, threat actors were able to build up a database of phone numbers and email addresses of some 5.4 million Twitter accounts because of a vulnerability, which seems very similar to a vulnerability disclosed back in 2019 that was used to match contact information against 17 million user accounts.
More: The Verge | Bleeping Computer | HackerOne
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Hackers are scoring free gas
NBC News: Gas prices are going up but that's not stopping some enterprising hackers from manipulating gas station pumps to reduce their costs, though at least 22 people have been caught doing exactly that in recent months. The hacks aren't technologically savvy, according to @kevincollier, but instead rely on standardization from a handful of manufacturers that rely on remote controls that can be found online and default codes in systems that are seldom changed.
FBI found Huawei equipment could disrupt U.S. nuclear arsenal comms
CNN: Alarming but incredibly detailed reporting from CNN this week on the risk posed by China-made Huawei equipment on the communication systems used by U.S. nuclear missiles. The feds have been investigating land purchases near critical infrastructure. "Among the most alarming things the FBI uncovered pertains to Chinese-made Huawei equipment atop cell towers near U.S. military bases in the rural Midwest. According to multiple sources familiar with the matter, the FBI determined the equipment was capable of capturing and disrupting highly restricted Defense Department communications, including those used by US Strategic Command, which oversees the country's nuclear weapons." No wonder the government — even as far back as the Obama administration — has been so keen to block Huawei equipment in recent years.
Is the Secret Service's claim about erased text messages plausible
Zero Day: A lot to unpack with this fluid and ongoing story, but in short, the U.S. Secret Service — tasked with protecting the president and other senior government officials — is in hot water after it erased phones storing text messages relating to the U.S. Capitol attack on January 6, despite the agency being told by its internal watchdog several times to preserve the data to help the January 6 House Select Committee investigating the riot. The saga is a complete mess, legally and technically, but thankfully @kimzetter has you covered in this thorough explainer. Also check out CBS News, which has more on the case — including how personnel were instructed to back up their text messages by "uploading screenshots" to a dedicated website.
TeamViewer installs suspicious font useful for web fingerprinting
Ctrl.blog: Interesting find by @DaAleksandersen: remote access tool TeamViewer installs a mystery font that Aleksandersen says is "only useful" for fingerprinting browsers — a way of tracking users around the web based on information gleaned from the browser, such as screen resolution, user agents, language, plugins installed, and that sort of thing. According to a Hacker News comment, the font is used by its website, which "checks for the presence of font (and thereby whether you've got the software installed) when you follow a special screen-sharing session invitation link." But TeamViewer said it'll remove the font in a later release.
Intrusion Truth claims APT41 targets Hong Kong and Taiwan universities
Intrusion Truth: The unknown, mystery individual (or individuals) behind Intrusion Truth, a blog that seems hellbent on doxxing Chinese threat actors and state-backed hacking groups, is back with another round of Who Is China Hacking This Time™? Intrusion Truth claims APT41, a well-known China-backed group that was named-and-shamed by U.S. prosecutors in 2020, is targeting mostly universities in Taiwan and Hong Kong, two regions that China says is theirs but are internationally disputed. The goal is to feed the stolen data into China's vast surveillance machine. But according to the unknown doxxers, APT41 isn't the best OPSEC operator. "Due to their lack of skill at evading detection, we also have the names of five individuals linked to Chinese intrusion set APT41," writes Intrusion Truth.
~ ~
OTHER NEWSY NUGGETS
7 out of 12 appeals courts say OK to recording police: The majority of U.S. appeals courts have affirmed that it's legal and a First Amendment protected practice to record police while they work. The 10th Circuit ruling case came in response to a blogger who claimed a Denver officer blocked their recording of a traffic stop. With the majority of appeals courts in agreement, it's likely not a case that'll end up before the Supreme Court any time soon, that is assuming the remaining five appeals courts don't buck the trend.
Digital security giant hit by cyberattack: Entrust, a digital security company that provides identity management and authentication for a ton of organizations — including the U.S. government — has been hit by a cyberattack. Little is known about the breach, but sources tell Bleeping Computer that hackers stole corporate data a month ago, but the incident wasn't widely known until Entrust disclosed details weeks later.
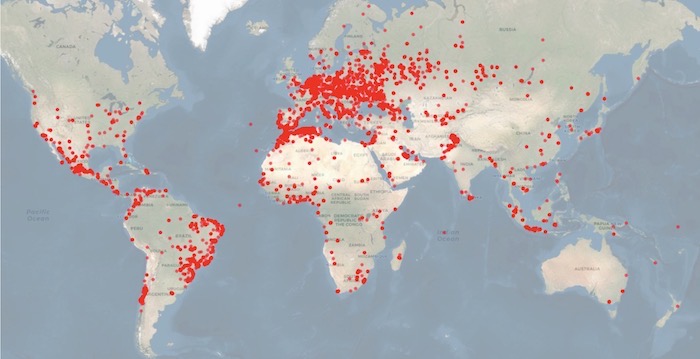
Chinese-made GPS tracker 'highly vulnerable': If you have a Micodus MV720 GPS tracker in your vehicle, you might want to rip it out as soon as possible. The Associated Press reports on new findings from BitSight, including a range of critical and high-severity vulnerabilities — such as hardcoded passwords — that can be easily exploited to remotely track entire fleets of vehicles and kill the engine while a vehicle is in transit. But Micodus is refusing to patch the vulnerabilities, exposing some 1.5 million trackers. CISA said it wasn't aware of any exploitation, but issued its own ICS advisory warning users to take action. Each red dot on the map is a vulnerable GPS tracker, according to BitSight.
Atlassian's fixes embarrassing password flaw: Speaking of hardcoded passwords (and companies that should know better), Atlassian has rolled out a patch that removes a hardcoded password in Questions for Confluence, an app that allows users to get support for Atlassian products. The password was "trivial" to obtain and soon leaked online. There are some 8,055 installations at the time of disclosure, and the hardcoded password protects an account that "allows for viewing and editing of all non-restricted pages within Confluence."
Feelyou exposed user emails: Popular Japan-based mental health app Feelyou, which lets users journal and track their moods either publicly or anonymously, left its GraphQL application exposed to the web, resulting in the spill of close to 80,000 user email addresses. Worse, "users' post history and profile information were also accessible," reports the Daily Dot. Feelyou fixed the issue.
Candiru used Chrome zero-day to target journalists: Avast published research this week linking spyware maker Candiru (also known as Saito Tech) to targeted attacks on journalists in Lebanon. Candiru planted a Chrome zero-day exploit on a website used by employees of a news agency to fingerprint users' browsers in order to find specific targets. Once it does, the browser exploit is used to get a foothold on a specific target's computer for delivering Candiru's spyware, known as DevilsTongue. The zero-day was fixed on July 4, days after Avast informed the company of the flaw. Meanwhile, Russ Graves has an excellent blog post out taking a deep dive in Apple's Lockdown Mode, which aims to protect iOS and macOS devices from these kinds of attacks.
~ ~
THE HAPPY CORNER
Scraping the barrel a little this week, but couldn't resist adding in this blog post by @lennyzeltser on What to Include in a Malware Analysis Report . I don't write malware reports, but I do read a lot of them, and this seems like a solid baseline of what to include. Shoutout to @de3ev for flagging it in a tweet.
Plus, seen on Imgur this week; after all, you can't get phished if you don't open your email.

And finally:
To send in good news for the happy corner, please reach out to: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's two-for-one cyber cats are Batman (left) and Arya (right), just goofing around and snoozing after a long day hacking. Many thanks to @emilyayale for the submission!

Don't forget to send in your cyber cats! Email here with their name and photo, and they'll be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
That's it for this scorcher of a week — both for weather and for news. Thanks for reading! The suggestion box is open if you have or drop me an email. And, if you liked this week's newsletter, please share with a friend or on your feeds. Smash those share buttons below.
See you again next week, have a great one.
—@zackwhittaker