this week in security — july 25 edition
THIS WEEK, TL;DR
Revealed: Leak uncovers global abuse of Pegasus spyware
The Guardian, Washington Post ($): What a week, and mostly dominated by the Pegasus Papers, a list of 50,000 phone numbers (more on that in a minute) said to be targeted by nation-state customers of NSO Group, the maker of the Pegasus spyware. Numbers on the list include journalists, activists, human rights defenders — and even heads of state, some of whom are spied on by their own governments. Pegasus customers include known human rights abusers, like the UAE, Mexico, Saudi Arabia and more. Amnesty identified Pegasus had targeted or infected dozens of phones on the list. NSO denied the claims and stopped talking to the media, though it's not like it was ever particularly transparent to begin with. Twitter threads by Citizen Lab's @jsrailton and @billmarczak have good digests of the many stories that were published throughout the week. This was a breathtakingly good project — and so much to cover. Also you must read the Washington Post's reporting — but don't trip over the "military grade" in the first line. There's actually so much reporting from around the world that @runasand compiled a running list of stories from the Pegasus Project, and a list of confirmed targets on the list.
More: Amnesty | The Guardian | Washington Post ($)
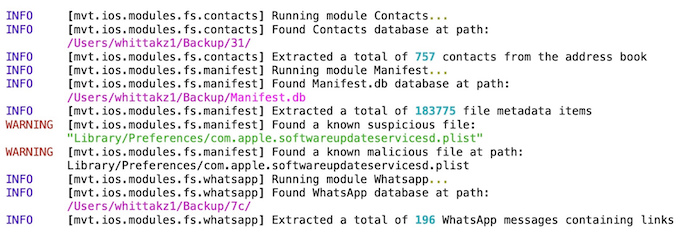
MVT, a toolkit for checking Pegasus infections
Amnesty International, GitHub: As part of the project, Amnesty researchers analyzed dozens of phones for Pegasus. They took the indicators of compromise — such as domains in text messages known to be used to install Pegasus, and other evidence of silent exploitation through zero-click attacks — from the phones of identified victims. The researchers built a tool that anyone can use to look for signs of Pegasus. The tool is called MVT, or Mobile Verification Toolkit. Its code is on GitHub. The toolkit works for both iPhones and Androids, but differently. Big thanks to @tenacioustek for helping me when I played with it on Sunday. If you want to know how to get started, I tried it last Sunday and wrote up some thoughts this week. (Disclosure: I wrote this!)
More: Amnesty International | TechCrunch
The NSO "surveillance list": What it is and what it isn't
Zero Day: So, about that list. Where did it come from? Nobody seems to know. But solid analysis from @kimzetter sheds some light on what this list of 50,000 phone numbers actually is without undermining the veracity of the published stories. Because despite the many Pegasus Project stories, nobody's really explained quite what this list is or how it was made. NSO denied any connection or claim to the list. Many questions remain, but this is a good start.
More: @zachdorfman | @runasand
A princess raced to escape Dubai’s powerful ruler. Then her phone appeared on the list
Washington Post ($): Probably one of the best reads of the Pegasus Project is from @drewharwell. UAE's Princess Latifa has tried to escape her father — the kingdom's ruler — Sheikh Mohammed bin Rashid al-Maktoum, for years amid allegations she's being held against her will. When her friends helped secure her a yacht to escape the UAE, special forces tracked her down miles from the Sri Lankan coast and returned her to the kingdom's ruler. This story follows how Latifa's phone number — and the numbers of her friends — were on the list of 50,000 other numbers said to be targeted by Pegasus, and how the spyware was used to track her movements and keep her captive. This is prize-winning reporting, no doubt, that reads like a Hollywood script. But the fact that this is real is what makes it so chilling.
More: @drewharwell
Chinese government recruiting criminal hackers to attack Western targets, U.S. and allies say
Politico: In other news, China was officially blamed by the Americans this week for the mass-hacking of Microsoft Exchange servers earlier this year. The DOJ said Beijing partnered with cybercriminals who carried out extortion and ransomware attacks on the side for personal profit. Four Chinese hackers were charged as a result for trying to steal Ebola research and other high-tech intellectual property from dozens of U.S. companies and others around the world. Some data was stolen through steganography, the indictment said, by stuffing the data inside digital images.
More: Justice Department | BBC News

In brief: Cloudstar hacked, Cloudflare bug squashed
The Register: A brief update on some other news. Cloudstar, a cloud IT provider that serves hundreds of companies, was hit by ransomware. Plus, Cloudflare fixed a bug in cdnjs, which hosts JavaScript and CSS libraries, that could've been used to compromise websites.
More: The Title Report | Ryotak
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
U.S. House terminates iConstituent contract after security issues raised
ZDNet: The U.S. House of Representatives has cut its contract with iConstituent, a platform used by dozens of House offices to access constituents' information, after a series of security issues — including a ransomware attack — which left some House offices unable to access data. The House's chief administrative officer said that iConstituent "does not appear to have meaningfully improved their security practices." And that was that. A good, short thread here by @MZanona.
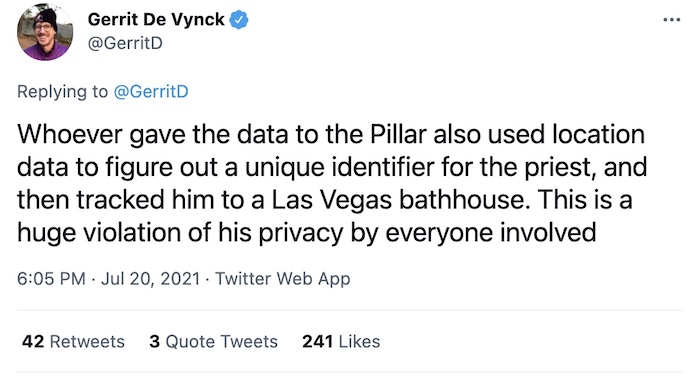
A top U.S. Catholic Church official resigns after cellphone data tracked him on Grindr
Washington Post ($): This story is so messed up on so many levels, but it's really important to note. A top U.S. Catholic bishop resigned after a Catholic publication on Substack obtained cellphone data that showed the bishop was an active user on Grindr and visited gay bars. Grindr called the publication's story homophobic (it is) but denied that the data used to identify the bishop came from the app. To call this entire story creepy is an understatement. This is the weaponization of app data, and it was inevitable this would happen eventually, especially given Grindr's less than stellar reputation on app security and privacy and the wider privacy-busting adtech ecosystem that allowed this tracking to happen. You don't need Pegasus when the creepy world of adtech can already do the job for you. You should also read @swodinsky's latest.
TSA issues second directive for pipeline operators amid China concerns
Dark Reading: TSA issued its second pipeline security directive in as many months. The first was in response to the ransomware attack on Colonial Pipeline. The newest directive, however, takes aim at efforts by China to break into two-dozen U.S. pipelines over the past decade, as recently discovered by CISA. Thirteen of those pipelines were compromised, three had near-misses, while eight were hit but at what level remains unknown.
Kaseya obtains REvil decryptor, starts customer data recovery operations
The Record: Good news and bad news. Kaseya has obtained REvil's universal decryptor, allowing it to start the recovery effort for its customers who were hit by the cascade of ransomware earlier this year. Kaseya wouldn't say how it got the decryptor (though there are many options available), but any customer wanting to decrypt their data will have to sign a non-disclosure agreement, which raises the question — why is Kaseya suddenly the gatekeeper here?
Gun owners' fears after firearms dealer data breach
BBC News: Thousands of names and addresses of U.K. gun owners were posted to the dark web after a security breach at a leading firearm's website. That's a major problem since the U.K. has strict gun laws and doesn't make it easy to get one, so knowing where someone with a gun lives puts them at risk from criminals. ("Oh, but can they just defend themselves with the gun?" Yeah, it doesn't work like that.) One person said the stolen data "seriously compromises my security arrangements for my firearm and puts me in a situation where me and my family could be targeted and in danger." Precisely.
~ ~
OTHER NEWSY NUGGETS
Clearview AI raises $30 million from investors despite legal troubles
Clearview AI, the controversial facial recognition startup that helped prompt a series of bans across the U.S. at the local, city and municipality level, has raised $30 million, proving that once again there's still someone willing to invest in this technology. Curiously, the Times ($) noted that the investors (cowards) don't want to be named.
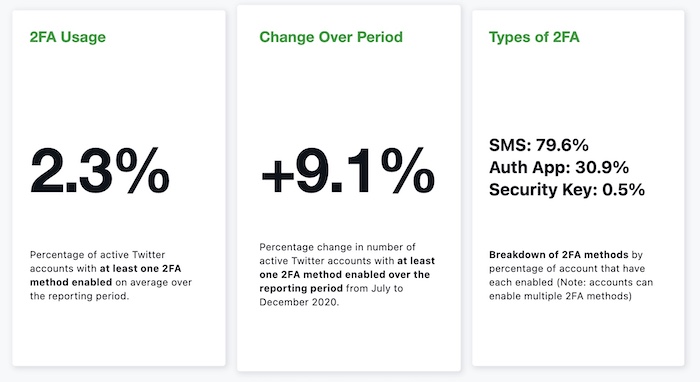
Twitter reveals surprisingly low 2FA adoption rate
Just 2.3% of all Twitter users have enabled two-factor authentication on their accounts. Given Twitter has about 206 million users, that's roughly 4.7 million users. Of those, close to 80% use SMS-based two-factor authentication and 30% use an authenticator app. Just 0.5% of all users use a security key, or 1.03 million users. The full transparency report is here.
Hikvision quits SIA, blames IPVM "bullies"
Why is Hikvision, a multi-billion dollar corporation, suddenly leaving the Security Industry Association (SIA), a trade association that represents the CCTV and surveillance camera industry? Because Hikvision had issues with IPVM, a video surveillance news site with a couple of dozen employees. Hikvision called IPVM "bullies" and as a result no longer wants to be a member of the SIA if IPVM is also a member. It might have something to do with how IPVM has aggressively reported on the SIA's members — including companies like Hikvision and Dahua — who are accused of human rights violations for selling their surveillance equipment to Beijing, which used the technology to oppress the Uighur minority. IPVM explained its side of the story, which noted Hikvision was under investigation for violating SIA's ethics code. It comes just weeks after Dahua was expelled from the SIA for violating the group's ethics policy.
Google pushed a one-character typo to production, bricking Chrome OS devices
Whoops! A single character bug in Chrome OS broke a conditional statement that was necessary for verifying passwords, rendering users unable to access their own devices. Google fixed the bug soon after, but warned it could still take a few days to roll out properly.
~ ~
THE HAPPY CORNER
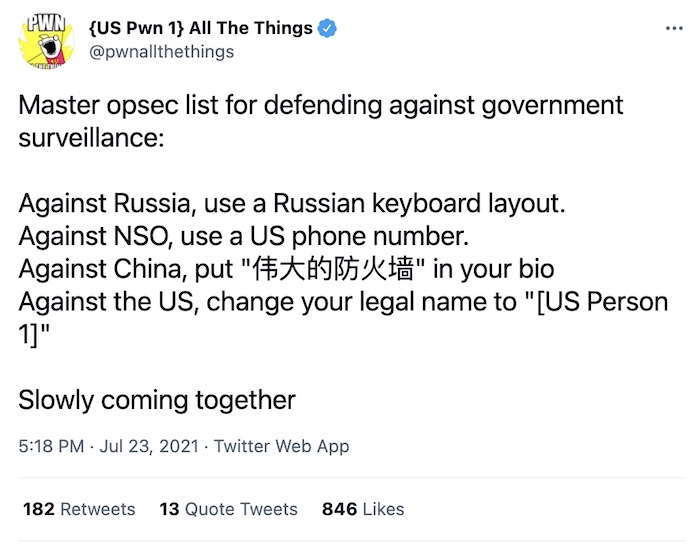
This week, @pwnallthethings came up with some solid OPSEC defenses. (Some more serious than others.) The full thread can be redeemed for one solid chuckle.
Meanwhile, if only all knocks at the door from the FBI were as friendly as this encounter.
If you want to nominate some good news from the week, feel free to reach out.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Leo Ram, who's clearly trying his best not to bellyflop or roll all over that very tempting-looking keyboard. (Who could blame you?) Many thanks to Lorenzo F.B. for the submission!

Keep sending in your cyber cats (or their friends). Drop a photo with their name here. And of course you can submit more than one — or again!
~ ~
SUGGESTION BOX
And I'm out. What a busy week. Hope you enjoyed this week's edition. As always, if you have any feedback, throw it in the suggestion box, or drop me a line at this@weekinsecurity.com. Take care and see you next Sunday.