this week in security — july 27 2025 edition
THIS WEEK, TL;DR
Microsoft faces fresh security scrutiny after 400+ SharePoint servers hacked
Wall Street Journal ($): The SharePoint zero-day disclosed last weekend is now fixed after Microsoft rushed out patches to affected customers running the self-hosted SharePoint software. Now all eyes are on Microsoft to see if it can handle its latest scandal. The SharePoint bug saw at least 400 SharePoint servers confirmed hacked so far, including federal government agencies like the Homeland Security, the Dept. of Energy, and others. The number may be higher, as China-backed hackers seek to exploit the bug to gain access to the files and documents inside affected systems. Per Bloomberg ($), Microsoft is reportedly probing if its program for alerting vendors to security bugs may have exposed the unpatched flaw. But since this isn't Microsoft's first major cybersecurity incident (remember the mass-hacks targeting Exchange servers back in 2021?), the technology giant is likely to face even greater scrutiny of its security practices. Given that CitrixBleed 2 (albeit unrelated) was only a couple of weeks ago, buggy enterprise software sure seems to be the root of a lot of security problems these days.
More: KrebsOnSecurity | Bloomberg ($) | Cyberscoop | TechCrunch | @curiousrobot
Clorox sues Cognizant for allegedly giving hackers employee passwords
Reuters ($): Consumer products giant Clorox is suing its helpdesk provider Cognizant for allegedly allowing hackers to walk in its digital front door by simply asking the helpdesk for a password to the network. Clorox had a major cyberattack in 2023 that cost the company at least $49M in expenses after hackers linked to Scattered Spider broke in. The company shut down its network and expelled the hackers, but the recovery took a while. According to the newly filed suit, the Cognizant-run helpdesk granted the hacker access to Clorox's network without any verification checks. Cognizant fired back on all cylinders, accusing Clorox of having an "inept internal cybersecurity system." In any case... this lawsuit is worth reading, not least from a defensive planning point of view.
More: Lawsuit (DocumentCloud) | The Register | @raphae.li
U.S. woman gets 8 years in prison for running laptop farm for North Korea
BBC News: This week saw the sentencing of Christina Chapman to eight years in prison for running a laptop farm for North Korean IT workers. I've mentioned this scheme a fair bit in this newsletter because it's increasingly a big deal — sanctioned North Korean workers get jobs at unwitting U.S. companies and earn a wage for North Korea's nuclear program. They do this using U.S. intermediaries, like Chapman, who run fleets of laptops for the remote workers on the other side of the world. The scheme has brought in billions of dollars for the regime's nuke program, and yet U.S. companies are ignoring the warnings, per the WSJ ($), and hiring the workers anyway. The Treasury's latest round of sanctions targeting the North Korean operation now makes this an even bigger problem that U.S. businesses have to get ahead of, or face stiff financial penalties if caught. Bloomberg ($)'s deep dive with Chapman is worth your time to read, including naming a few affected companies.
More: Justice Dept. | WSJ ($) | Cybersecurity Dive | NPR
Age verification checks have arrived... and kids are bypassing them
Wired ($): The big "age verification" switch got flipped in the U.K. on Friday, thanks to the Online Safety Act taking effect, forcing users across the country to hand over their driver's license or other government-issued document to prove they're old enough to access certain websites. Age checks are meant to protect children, but the way politicians have gone about it mean private companies are now taking on huge amounts of highly sensitive data of ordinary people so they can "prove" they are allowed access to potentially adult stuff on the internet, from Bluesky to Reddit, Discord, Grindr and more. There are huge implications for free speech and expression, including a potential chilling effect, since many folks will balk at the idea of giving over their ID to access a website. Let's just hope the kids haven't found a way t... aaaand of course they've already found a way to bypass the checks. The U.K. isn't the only one rallying behind this, plenty of U.S. states, wider Europe, and Australia are also rolling out age checks.
More: The Verge | Pink News | Alec Muffett
~ ~
THE STUFF YOU MIGHT'VE MISSED
Google took a month to shut down a spyware operation hosted on its servers
TechCrunch: Google finally took action against a phone spyware operation called Catwatchful, which was operating from Google's own Firebase service. After Catwatchful became the latest spyware operation in recent years (the 26th, by TechCrunch's count) to have a data breach, I contacted Google to alert them that Catwatchful was hosted on Firebase. The company only took action this week — but wouldn't say why it dragged its feet. (Disclosure alert: I wrote this story!)
Talent agency Toptal had its GitHub hacked to push destructive packages
Socket: Hackers have hijacked the GitHub account belonging to Toptal, which maintains the Picasso design system, to push malicious updates containing code capable of wiping a developer's system. According to security startup Socket, the code exfiltrates the developer's credentials then attempts to delete their machine. The malicious packages accumulated 5,000 downloads before they were detected. Bleeping Computer has more.
A new hack defeats car key fob security protections
Straight Arrow News: A new attack using a $1,000 Russian-developed custom firmware made for the Flipper Zero hacking tool can unlock cars in close proximity by intercepting and cloning a key fob's radio signal. The attack bypasses the key fob's authentication known as rolling codes, which generate one-time codes each time a key fob is pressed, by calculating valid key fob commands using a single intercepted signal. If you open your car trunk, a malicious actor can steal your entire key fob.
Sacramento power company tipped police to high energy usage
EFF: Tropical fish tank or weed farm? Despite a California law protecting the privacy of your smart electricity meter, Sacramento's power company has passed on thousands of tips about "high" household energy usage to the police, ostensibly looking for homes growing weed. The good folks at the EFF are suing to stop this dragnet surveillance practice. More from Ars Technica.
158-year-old company goes under after ransomware attack
BBC News: The BBC's Panorama program covered the gutting story of a U.K. transportation company that went out of business following a 2023 ransomware attack. The hackers broke into the company's network by guessing an employee's password. The framing of the BBC's story, however, which blamed the password (and to a degree, the employee) for the breach, seemed to miss a key point that years of the company's management underinvesting in cybersecurity and poor corporate security practices was ultimately what allowed the hackers to do so much damage the company's network, not the employee.
U.K. to back down on Apple backdoor after U.S. pressure
Financial Times ($): The London's FT (via Ars Technica) reports that the U.K. is seeking to wiggle out of a problem of its own making — undoing its call for a backdoor to access any customer's data in Apple's cloud. The demand (and the precedent it would set) royally annoyed the U.S., and Washington pretty much told the U.K. to back down. Daring Fireball had a good take: Love or hate the U.S. government right now, this was the right call to make — for security, privacy, and common sense.
Sam Altman warns of AI voice fraud crisis in banking
Associated Press: OpenAI boss Sam Altman warned this week that AI-generated or "deepfaked" audio can be abused to trick security checks that rely on authenticating using a person's voice, such as when you call your bank. The good news is that @spencerdailey has been warning about this very issue as far back as 2021, even if Altman is oblivious to the very problems he's ultimately helping to create. Switch off voice identification when you can.

~ ~
OTHER NEWSY NUGGETS
EU healthcare operator AMEOS breached: AMEOS, which operates a large health network across Europe, was hacked. The company told the DPA news agency that the company's German operations were affected, and said in a statement that "data belonging to patients, employees, and partners" was likely taken in the breach. (via AMEOS, DataBreaches.net)
U.K. mulls ransomware ban: The U.K. government said that following an earlier public consultation it will move to ban public sector bodies and critical infrastructure operators, like the NHS, local councils and schools, from making ransomware payments. Businesses not covered would still be required to notify the U.K. government if they plan to pay a hacker's ransom. The U.K. didn't give a timeline for the legislative proposal, but said the data will help the authorities "hunt down perpetrators and disrupt their activities." (via U.K. Government)
'Majority' of Allianz Life customers' data stolen: U.S. insurance giant Allianz Life confirmed Saturday that the "majority" of its 1.4 million customers had personal information stolen in a mid-July data breach. (Disclosure: I also wrote this!) The company said its CRM database was compromised. It's not known which CRM database Allianz Life is referring to, but recent social engineering hacks targeting Salesforce organizations are notably on the rise. (via TechCrunch)
Spyware founder wants FTC ban reversed: The FTC banned Scott Zuckerman from the surveillance industry in 2021 after his spyware company Support King (aka SpyFone) had a security lapse that exposed the private phone data of thousands of people it was snooping on. Now, Zuckerman wants the FTC to reverse that ban, but he pinky promises he'll stay out of the surveillance industry if the order is vacated or modified. If you want to say your piece about the proposal, the FTC's comments are open until mid-August. (via TechCrunch — double disclosure!)
XSS.is admin arrested: The alleged administrator of the notorious XSS.is cybercrime forum was arrested in Ukraine and its website seized. Per Europol, the site had more than 50,000 users and that data will now help the authorities in their ongoing investigations. French prosecutors said (en français) they wiretapped a Jabber server to identify the admin. (via Europol)

Travel plans left online: Simple security bugs in the website of U.K.-based luggage service Airportr, a premium travel service used by 10 different airlines, exposed the personal information of virtually every customer, including flight itineraries, and could have allowed malicious hackers to redirect or steal luggage in transit. (via Wired ($))
Spill the Tea... no, not like that! A new app called Tea, a dating safety app with 1.6 million users that rocketed to the top of the iOS App Store chart in recent days, spilled the private government-issued IDs of its users through shoddy coding and an exposed backend Firebase database. Some 72,000 images (and thousands of selfies) spilled online. The company confirmed the breach soon after. The claim that Tea was required to store raw ID documents doesn't really pass the sniff test. (via 404 Media, @malwaretech)
CISA nomination stumbles on election fact check: Trump's pick to lead the U.S. cybersecurity agency CISA, Sean Plankey, faced a grilling by lawmakers this week, but wouldn't be drawn on whether the 2020 election was rigged or stolen, which... is kind of a big deal for CISA, given that the agency is still tasked with election cybersecurity. Plankey isn't likely to be CISA director any time soon, as Sen. Ron Wyden still has a hold on Plankey's nomination over CISA's response to the Salt Typhoon hack targeting telcos and more. (via Cyberscoop, Cybersecurity Dive)
~ ~
~ ~
THE HAPPY CORNER
And breeeeeeathe. That's the news done with. It's time for the happy corner.
Thanks to this absolute mood of late. (If you're reading this and don't know what a phone connecting to the internet sounds like, I gotchu.)
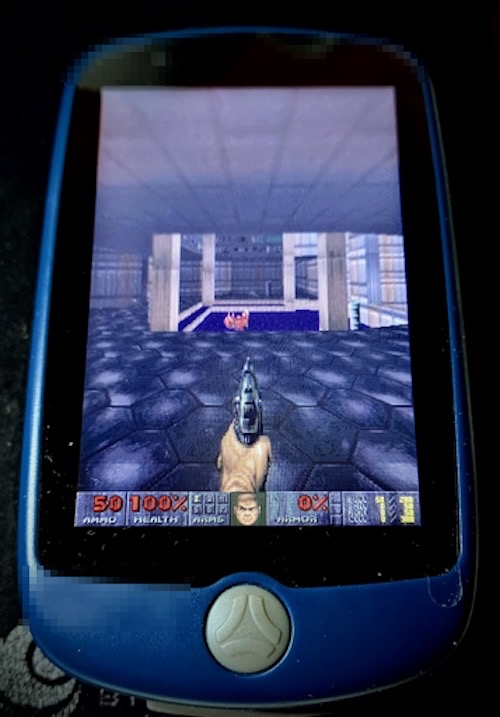
And, we're blessed to have another episode of, What Can Doom Run On? This time, its a decade-old bicycle navigator. Thanks to Raymii.org, this little bike-sized device might not have the bells and whistles of today's sat-navs, but is still very capable of running the first-person shooter.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat mini-void floof is PJ, who can be seen here all tuckered out after a very busy day of lock picking practice. Gotta get 'em started hacking young! (Side note: I have melted, PJ is so damn fluffy and cute.) Thanks so much to Rusty S. for sending in; the absolute highlight of my week.

Keep the cyber cats coming in! Got a cyber-cat or a non-feline friend? Send in an email with their photo and name and they will be featured in a future newsletter!
~ ~
SUGGESTION BOX
Aaaannndd I'm outta here! I've kept you for long enough with this extremely busy edition, thanks for reading! Enjoy the rest of your weekend! If you have anything you want to share for next week, get in touch.
Peace,
@zackwhittaker