this week in security — july 28 2024 edition
THIS WEEK, TL;DR
Internal checks at CrowdStrike failed to flag bug that caused mass outage
CrowdStrike: By now, more than 97% of Crowdstrike's affected Windows sensors are back online after last week's global mega outage, which caused travel and business chaos for days (in some cases it's still lingering). Turns out CrowdStrike released its bad sensor update in part because internal checks that were supposed to prevent buggy updates from going through failed. CrowdStrike's snafu may have caused at least $5 billion in losses among the Fortune 500. Security researchers pulled apart the buggy update and found the update caused an "out-of-bounds memory read," despite rumors to the otherwise. (Forget bringing a gun to a knife fight; if you want to wipe the floor in infosec, bring @taviso to a vulnerability showdown.) At least CrowdStrike said sorry (briefly) by way of a $10 Uber Eats gift card. Although, CrowdStrike couldn't seem to get that right, either...
More: Bloomberg ($) | BBC News | Luta Security | @patrickwardle | @dwizzleMSFT
Russia-linked malware cut heat to Ukrainian buildings in deep winter
Wired ($): Russia-linked (*heavy wink*) malware was used in a first-of-its-kind cyberattack to knock the heat out of hundreds of Ukrainian buildings in sub-zero temperatures earlier this February. Security firm Dragos disclosed the ICS malware, dubbed FrostyGoop, which along with Ukrainian cyber authorities found the malware was used to target a heating facility that powered the buildings. The cyberattack wasn't atrributed — Dragos doesn't do that — but the strongest hints suggest Russia may have had a hand, given IP addresses used to deploy the attack were linked to the Moscow region. This is the third time Ukraine has experienced an outage of critical infrastructure linked to Russia in recent years, including two malware-linked power outages in 2015 and 2016, which were definitely Russia's fault.
More: Wired ($) | Cyberscoop | TechCrunch
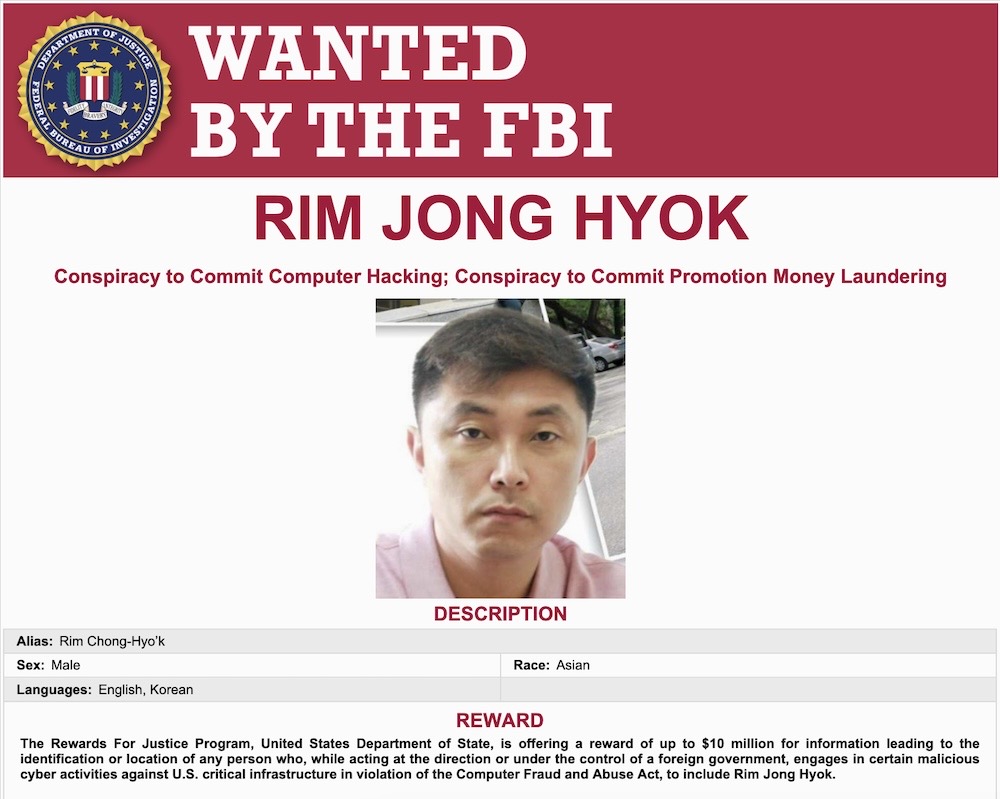
U.S. discloses North Korean hacks trying to steal nuclear secrets
Justice Department: The Kim Jong Un regime only wants one thing, and that's nuclear weapons (yuck). And when it can't have nuclear weapons, it wants crypto so it can make nuclear weapons (double yuck). That's where its state hackers come into play. The U.S. and its allies just warned that North Korean hackers are trying to steal nuclear secrets from governments and private businesses around the world all so that Pyongyang can have some nukes to play with of its own. Known as the groups Andariel and Onyx Sleet, the hackers use malware for conducting espionage. And, in some cases, ransomware — according to a Justice Department charge sheet, which indicted at least one North Korean government hacker for targeting hospitals with ransomware to fund the regime's illegal activities.
More: IC3.gov [PDF] | Microsoft | BBC News | Associated Press
Automakers sold driver data for pennies, senators say
The New York Times ($): It's a @kashhill story, so it's got to be good news, right? Right? Cue Hill: "If you drive a car made by General Motors and it has an internet connection, your car’s movements and exact location are being collected and shared anonymously with a data broker." Ahh... oh no. The practice was revealed in more detail by lawmakers this week after an investigation by the New York Times found carmakers collecting and sharing gobs of sensitive telemetry, including location data. Customers weren't asked for permission and the only way to opt-out was disabling the car's internet connection entirely. For the companies to claim this is data is "anonymous" is a real push, as location data is rarely scrambled in a way that's untraceable to the person (and research shows it's very possible to identify people). All in all, GM and other car makers made very little money from selling your data to brokers, in some cases pennies, and most gave data to police without a warrant.
More: Sen. Ron Wyden | @kashhill | @byrontau
~ ~
THE STUFF YOU MIGHT'VE MISSED
Banking group mulls access to social media data for anti-AML
The Rage: An association that represents some of the world's biggest banks said in a new statement that anti-money laundering techniques these days don't go far enough and are proposing access to "reputable external, publicly available sources" — such as IP addresses and verified social media accounts — to "comprehensive customer behaviour analysis which could expedite risk management decisions." In other words, banks want even more of our data to protect... well, their bottom lines, ultimately. More data is not the answer here, and I'm not sure if trusting a tech company with your verified identity is the smartest approach, either...
U.K. infiltrates booter site and arrests admin
National Crime Agency: U.K. cyber plods infiltrated the the notorious digitalstress.net booter-for-hire site and arrested its suspected administrator. The NCA said the site "has been controlled" by its officers, and "collected substantial data from those who have accessed this domain." Damn! And not for the first time, either. Booter-for-hire sites are illegal because they can be used for launching malicious DDoS attacks, which they frequently are. The lesson here? Don't use them — or face getting caught.

Wiz turns down $23B Google offer
BBC News: Cybersecurity startup Wiz turned down an ungodly amount of money this week from Google, which offers $23 billion to buy the Israeli cloud security company. Wiz's CEO Assaf Rappaport was "flattered" by the offer, but that the company wants to go it alone to reach $1B in annual recurring revenue. One of the biggest cyber deals in recent years... that wasn't. My TC colleague @mtemkin has Rappaport's memo to Wiz staff.
Breaking iChano AtHome's network encryption with Frida
Eric Daigle: Rolling your own crypto(graphy) at the best of times is a terrible idea, but no more so in 2024 when we've learned the lessons from yestyear. Alas, a vulnerability in iChano's AtHome internet-connected camera (with more than five million Android downloads to date) shows why using your own cryptography is a bad idea — because as demonstrated, a bug allows the unscrambling of traffic without needing the key. Why roll your own when there are plenty of extremely good, lasting and secure ciphers out there already?
~ ~
OTHER NEWSY NUGGETS
Un-KnowBe4-ingly hiring a North Korean hacker: Since there's no better time to disclose your security incident than during a worldwide IT meltdown, KnowBe4 dropped the news that it unknowingly hired a North Korean threat actor as a principal software engineer. After vetting and checking references, the company shipped a company laptop to the new hire's alleged address — and it immediately got loaded with malware, which was picked up by KnowBe4's security operations center. (Yes, these "laptop farms" exist!) KnowBe4 said this wasn't a data breach. Still, good to disclose it — KnowBe4 is unlikely to be the only firm targeted. (via KnowBe4, )
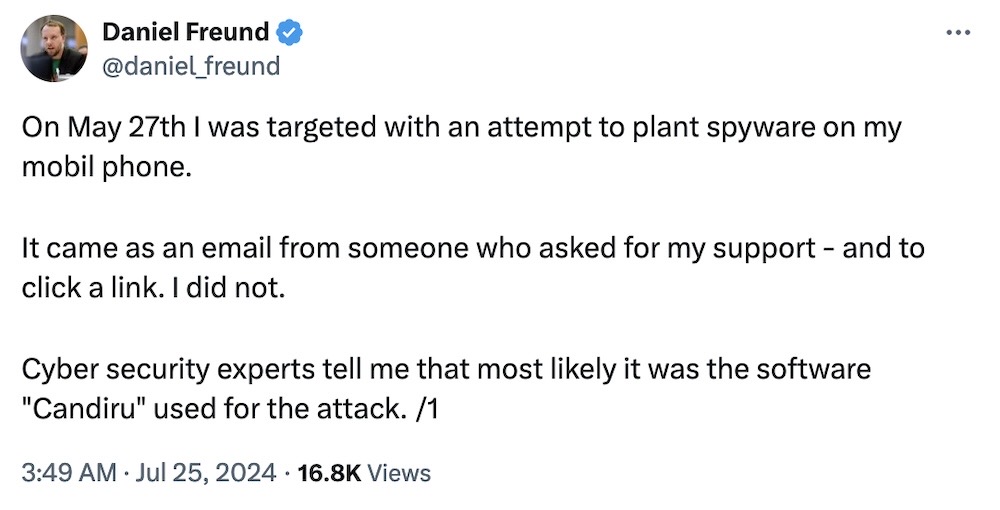
Euro MEP targeted with spyware: Another member of the European Parliament has been targeted with government-grade spyware. German MEP Daniel Freund says he was targeted with a malicious email that contained a link to the Candiru spyware. Freund said he suspects a few countries — including Hungary's Orban government, a known user of spyware — which Freund has been critical of. Other lawmakers across Europe have been targered by spyware, including Spain and Greece. In Greece's case, it led to an huge scandal dubbed "Greek Watergate." Inside Story [Ελληνικά] has a ton more reporting. (via Politico, @RonDeibert)
21st (at least) stalkerware company hacked: From spyware to... stalkerware, a different kind of phone spyware. Spytech is the latest stalkerware maker has been hacked — specifically the 21st stalkerware maker hacked since 2017 — spilling gobs of information about its victims. The upside is that the data also contained enough information to confirm the identify of its administrator and CEO who runs the Minnesota-based phone malmare maker. (Disclosure: I wrote this story!) Spytech makes stalkerware apps for Windows, Macs, Chromebooks and Android devices. (via TechCrunch, @zackwhittaker)
Secure Boot? Manufacturers: Hahaha — no: You know you really messed up when you mistakenly used publicly leaked private keys labeled "DO NOT TRUST" to cryptographically protect the boot process of more than 200 device models sold by Acer, Dell, Gigabyte, Intel, and Supermicro. But that's what happened, per Binarly. Now that the leaked key has come to light, security experts say the key effectively torpedoes the security assurances offered by Secure Boot and potentially introduce rootkit-level exploits. (via Ars Technica)
~ ~
~ ~
THE HAPPY CORNER
Are we clear? We're clear. News over; it's the happy corner.
First up, can't waste a good opportunity to vote for the Cyberscoop 50 top cybersecurity leaders across the industry. There are some fun and familiar (and some new!) faces here — check out the cream of the cybersecurity crop and vote, and share a little love of recognition for the folks who kick butt in cyber every day.
404 Media, the journalist-owned media site that has been consistently reporting important cybersecurity and privacy scoops and stories with impact, will be among those honored by the Electronic Frontier Foundation at this year's 2024 EFF Awards. If you haven't subscribed to 404 Media yet, now's your time.
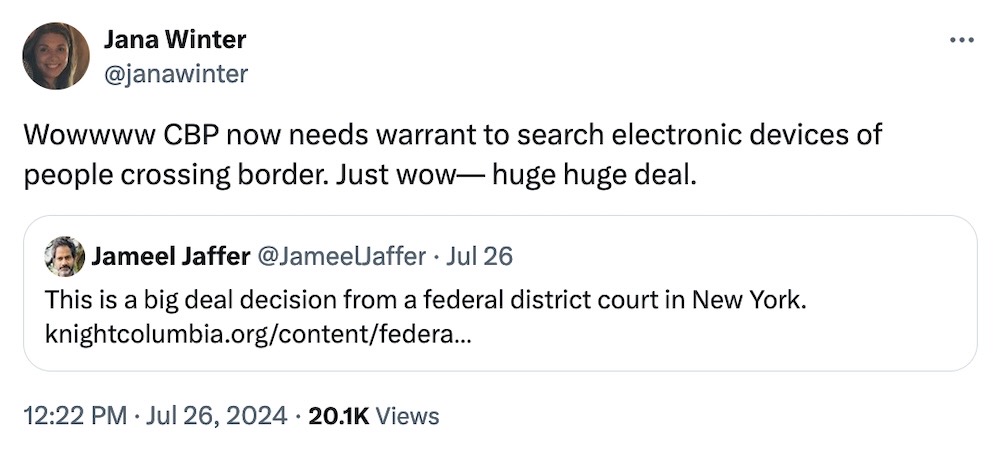
And, in fun legal news, the border feds now need a warrant to conduct device searches at the border. A long overdue ruling, but good nonetheless.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet Boomer, this week's cyber-tiger, whose human tells me Boomer is definitely a hacker cat and quite the social engineer, since he will beat anyone at a staring contest. Cuddly enough to trick you into turning over your passwords with just a hug? Many thanks to Gary R. for sending in!

Send in your cyber cats! Feel free to drop me an email with a photo of your cyber cat (or your non-feline friend!) with their name and they'll be featured in an upcoming newsletter. Updates are always welcome — send 'em in!
~ ~
SUGGESTION BOX
And that's it for this week! I hope you managed to get some rest and recoup after the hot mess of last week. Onwards and upwards, as they say. And thanks so much for reading! If you ever want to reach out, you can drop me a note any time. It's lovely to hear from you (and getting your cyber cats).
I'll be back next Sunday with more as always. In the meantime, enjoy your week!
All my best,
@zackwhittaker