this week in security — july 30 edition
THIS WEEK, TL;DR
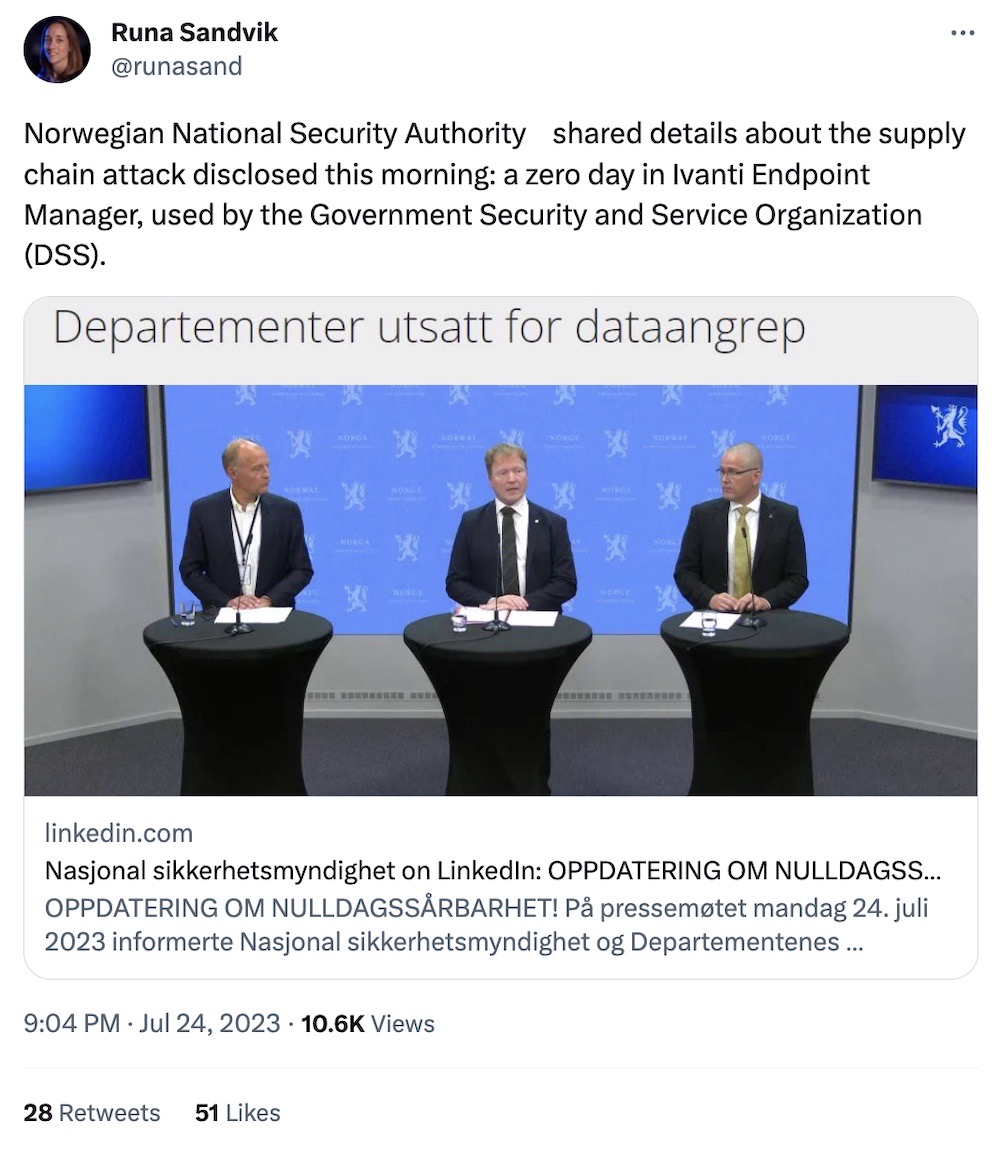
Ivanti zero-day bug used to hack Norwegian government
WSJ Pro ($): Hand up if you weren't hacked this week? Norway, put your hand down. On Monday, the Norwegian government sounded the alarm on a new zero-day in Ivanti EMM (previously MobileIron Core) software that it found under active exploitation. The bug allowed unknown hackers to compromise 12 Norwegian government ministries. CISA said federal agencies on this side of the pond should patch ASAP, given that the bug is a remote unauthenticated API access flaw that could allow an attacker to remotely spin out new admin accounts. Yeah, that's breathtakingly bad! What's worse is that Ivanti held the security advisory for the 10/10 CVSS-scored bug behind a paywall for the first few days (now public). Add Ivanti to your naughty vendor list.
More: CISA | Ivanti | SC Magazine | Reuters ($) | Bleeping Computer
SEC rule requires public companies disclose breaches in four days
Associated Press: The SEC has a new rule that requires U.S. public companies to disclose all cybersecurity breaches within four days that could have a material affect on their bottom lines. Seems simple enough, no? Start the clock! ...Well, kind-of. The key wording here is "material." The second that a company thinks a cyberattack may impact their profits, the clock starts when the lawyers tell you, which probably isn't what the SEC wanted here. Still, there was more criticism, since public companies will have to disclose through a public 8-K filing that they were breached, which could in theory give malicious hackers insight into how much financial damage their cyberattacks cause, and what they could demand for ransom. I'm sure folks can appreciate the SEC's efforts here, but can't help but think that there should be greater focus on the individuals affected by security incidents, rather than very wealthy investors who lose what ultimately amounts to pocket money to them.
More: SecurityWeek | Bloomberg ($)
Microsoft faces mounting scrutiny over China-linked email hack
Wall Street Journal ($): Forget the Wyden siren. This week it's spicy Wyden. In a letter to U.S. cybersecurity top brass, including CISA and the FTC, the Oregon senator accused Microsoft of "negligent cybersecurity practices" that allowed China-backed hackers to break into Microsoft-run email inboxes, including those belonging to senior U.S. government officials. "Even with the limited details that have been made public so far, Microsoft bears significant responsibility for this new incident," Wyden writes. Sure, Microsoft is finally giving its customers security logs for free (in September, not immediately), but many questions remain — and Wyden has them all, including how hackers stole "a single encryption key that could be used to forge access to consumer, commercial and government customers’ private communications." Meanwhile, Newsweek reports that more than a dozen bipartisan senators sent a letter to State's CIO asking for more details about the breach of State Department emails.
More: Newsweek | Axios | @kimzetter
Researchers say TETRA radio code kept secret for years has backdoor
Wired ($): Police, critical infrastructure workers, and others use TETRA radios every day to communicate reliably and securely. Except on that last point... researchers say they've reverse engineered the notoriously locked-down and proprietary radio systems and found a significant vulnerability in TEA1, one of the radio's algorithms (and another bug that affects all of the radio's algorithms) that could be used to decrypt their communications with relative ease. The researchers call it a deliberate "backdoor." Stick around for @kimzetter's fascinating (and masterful) interview with ETSI, the organization that created the TETRA standard.
More: Zero Day | Motherboard | @josephfcox | @kimzetter
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
North Korea hackers hacked JumpCloud to target crypto clients
Mandiant: Mandiant, which led incident response for a JumpCloud customer, linked the JumpCloud hackers back to North Korea's Reconnaissance General Bureau, a specialist hacking unit designed to target crypto to fund the regime's nuclear weapons program. Mandiant attributed their evidence in part thanks to an opsec mistake that the hackers made.
Only a handful of Fortune 100 firms list security executives
Krebs on Security: It's been a few years since cybersecurity journo Brian Krebs looked at the executive suites of Fortune 100 companies to find it was barely represented by security professionals, like CISOs. Now, Krebs has found things haven't changed much. Only five — yes, five — of the Fortune 100 last year listed a CSO or a CISO in their highest corporate ranks. Next time a company claims to take security "seriously," you can remind them to elevate the person responsible for cybersecurity to the company's leadership pages. Call it a lesson in transparency (or accountability).
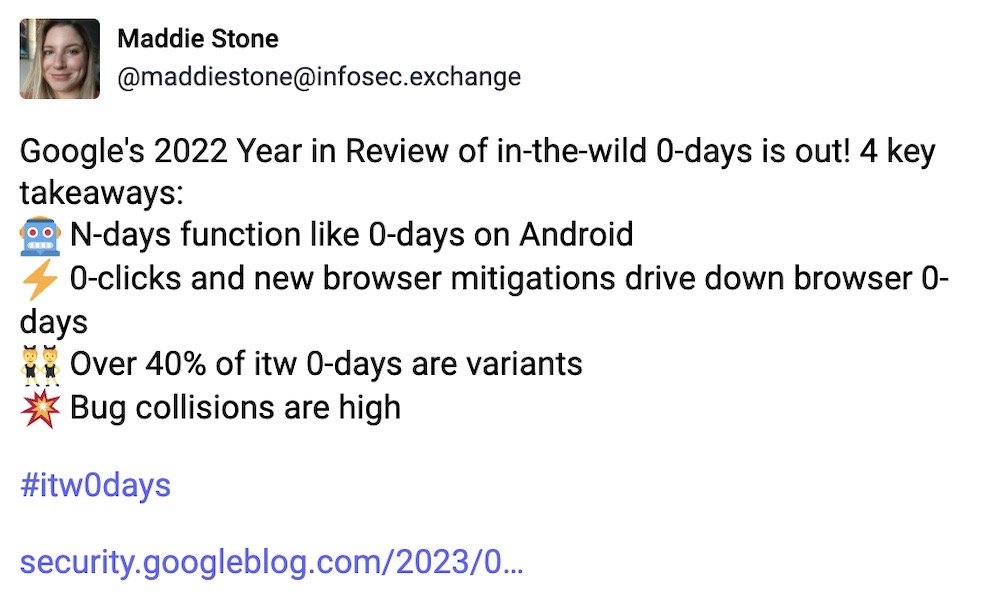
Google's key takeaways from 2022 in zero-days
Google TAG: Another year-in-review of zero-days exploited in the wild dropped this week. @maddiestone said in a blog post that there were 41 in-the-wild zero-days (ie. newly found bugs with no patches at time of exploitation) were disclosed in 2022, the second most that Google has ever recorded. Interestingly, bug collisions are high, which means, "when an in-the-wild 0-day targeting a popular consumer platform is found and fixed, it's increasingly likely to be breaking another attacker's exploit as well." In other words, patch quickly — and patch thoroughly.
Twitter scammers stole $1,000 from my friend, so I hunted them down
Wired ($): Hell hath no fury like a pissed-off security researcher: @selenalarson found out a friend, who uses a screen reader, lost $1,000 from a Twitter scammer. With the help of a social engineer, Larson tracked down the people behind the scam ring with incredible accuracy and precision and handed their information to police. Brilliant work, and a reminder that criminals aren't as anonymous as they might think.
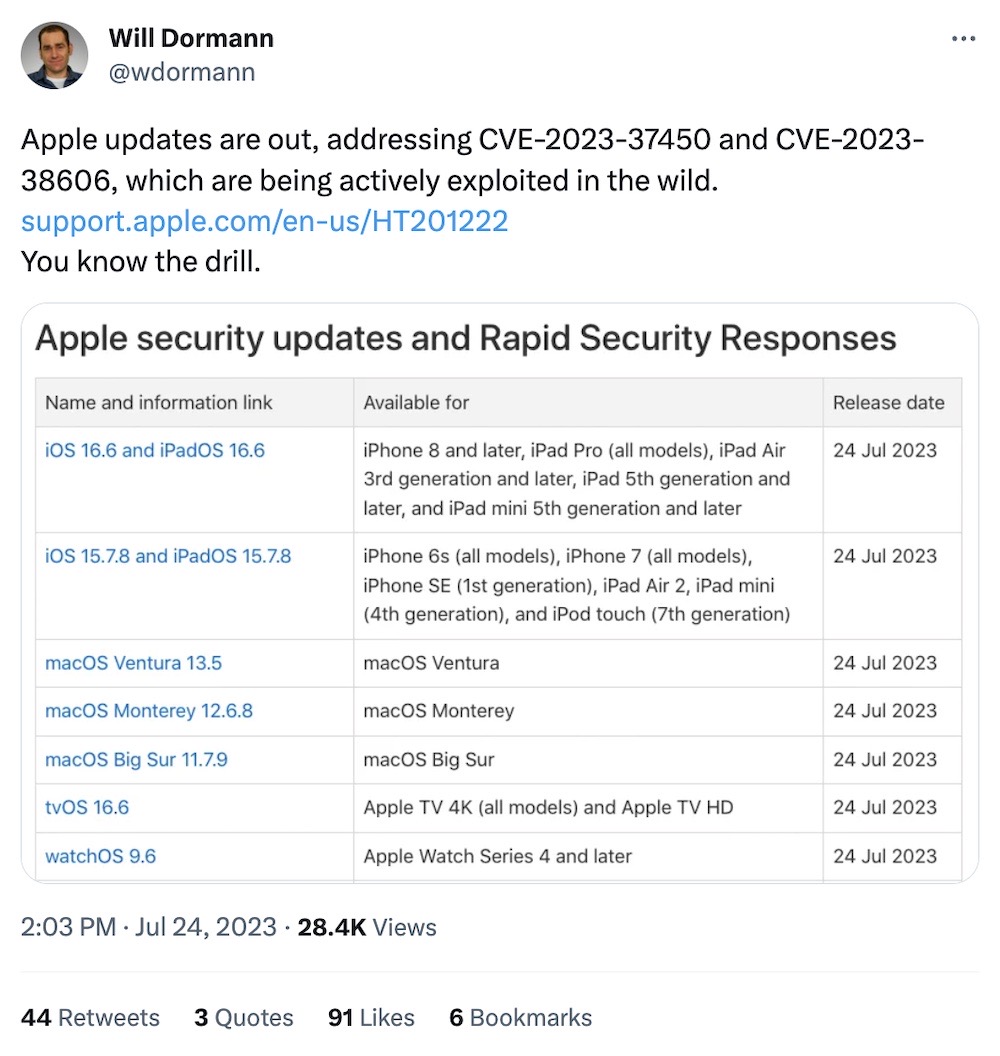
Update your iPhones, iPads, Macs, new zero-day patches have arrived
Apple: The fruit-themed tech giant has released updates for iPhones, iPads, Macs, Apple TV and Watches that fix two zero-days in WebKit and the kernel. Details are scarce. As usual, you should update as soon as possible to be safe.
~ ~
OTHER NEWSY NUGGETS
California bill to ban geofence warrants stalls: An anti-geofence warrant bill in California has stalled, making its passing unlikely due to pushback from law enforcement. The bill, AB 793, got a ton of support for aiming to shield those seeking abortions from having their data collected by geofence warrants (aka "reverse location" warrants, since police can see who was in a particular geographic radius at nearly any point in recent history by obtaining that data from Google and other location-hungry tech companies). But police threw major opposition at the bill, saying a ban on all geofence warrants would be a "real overreach." Which is complete BS, by the way, since geofence warrants are probably unconstitutional and have already been found to violate the Fourth Amendment. This is a real shame, and a hugely missed opportunity. (via Los Angeles Times ($))
Russian court jails cyber CEO for 14 years: Ilya Sachkov, founder and CEO of Group-IB, one of Russia's most prominent cybersecurity firms, was jailed for 14 years on allegations that he passed classified information to foreign spies. Sachkov denied the charges and critics said he, somewhat predictably, wasn't given a fair trial. Sachkov had previously criticized the Putin regime for turning a blind eye to ransomware attacks stemming from Russia. More from this Bloomberg ($) profile from 2021. (via Reuters ($))
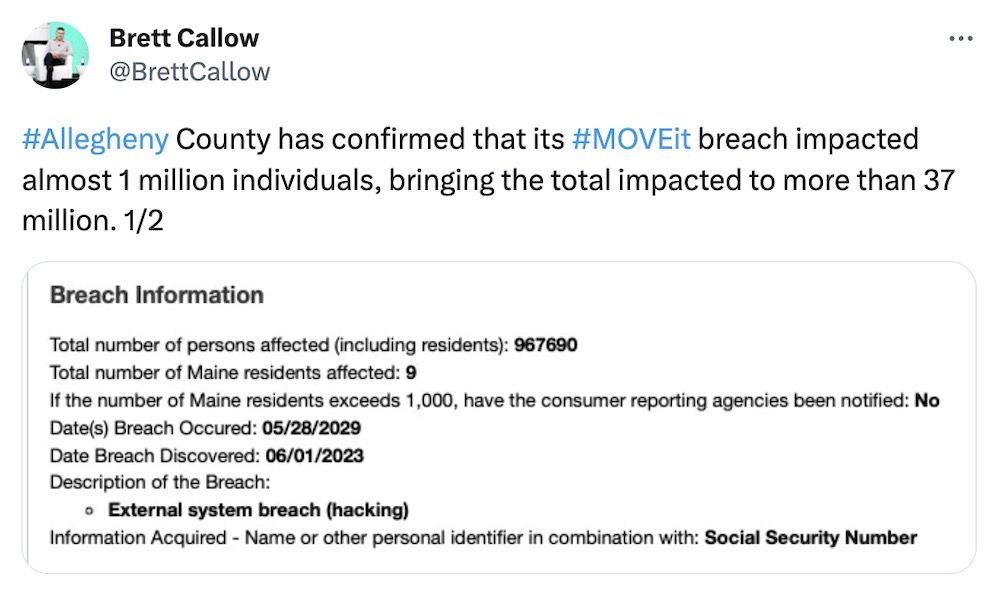
MOVEit hacks hit 37 million victims: The worst mass-hack of the year has claimed new corporate victims, totaling more than 530 organizations and affecting about 37 million people, per new data by Emsisoft. That's in part due to several huge breaches caused by the Clop ransomware gang hacking MOVEin file transfer tools with a zero-day. Allegheny County (including Pittsburg) in Pennsylvania was hacked, with a million residents affected, and a U.S. government contractor Maximus saw between 8-11 million people's health data taken. (via TechCrunch)
U.K. ambulance service hit by patient data outage: Swedish-headquartered software vendor Ortivus said its patient record system was hit by a cyberattack that knocked it offline, forcing U.K. ambulances — which use the system — to rely on pen and paper. Ortivus' CEO couldn't say when the company's analysis of the attack will be complete. (via The Register)
Biden admin. nominates Harry Coker as cyber director: Harry Coker will be the next U.S. national cyber director, if the Biden administration gets its way. Coker, who comes from the CIA and the NSA, now has the challenge of implementing a cyber strategy that he had no part in writing and, according to the Washington Post ($), is "not recognized as someone who has deep cyber experience within government or industry." The highly cyber-experienced Kemba Walden, who is currently acting director and helped author the cyber strategy, was passed over for the promotion. (via Axios, Washington Post ($))
~ ~
THE HAPPY CORNER
And with that, it's the happy corner.
Everyone's favorite hacker toy, the Flipper Zero, now has its very own phone app, allowing users and hobbyists to search and browse for tools and plugins. The hacker multi-tool is packed with radios, ports, and capabilities. (I have one, and it's really a lot of fun.) The Verge has more about the app.
This fortune cookie has encountered an error:

And finally. For those heading to Las Vegas this week for Black Hat and Def Con, travel safely and have fun. For those who haven't been before (and even seasoned veterans), here's some good advice from your friendly neighborhood cyber reporter.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Molly, who's all grown up since the last time we saw her. Some things never change, though. Molly is still jealous of the attention the laptop gets from her human. Thanks so much to her human for sending in an update!

Send in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's all I have for this week, a busy one!
If you're heading to Las Vegas for the big security shows, have loads of fun. Stay hydrated! In the meantime, I'll be back next week with the usual rundown from the week. As always, catch me by email with any feedback.
Have a wonderful rest of your weekend.
—@zackwhittaker