this week in security — july 31 edition
THIS WEEK, TL;DR
UEFI-based rootkits found in motherboards dating back to 2016
Ars Technica: Kaspersky published research this week into a UEFI-based rootkit it's calling CosmicStrand. The rootkit was found buried deep inside the basic firmware of some Gigabyte and Asus motherboards used to help the operating system boot up. Because it's in that computer's basic firmware, the malware can survive and persist even after an OS reboot or reinstall. Kaspersky said the rootkit was likely developed by an unknown Chinese-speaking hacking group with ties to cryptominer malware. That's led the researchers to believe that the rootkit malware, which is generally at the top end of complexity and capabilities, may not be as rare as they might think, since the implant may have been used as far back as 2016. It's likely that the rootkit exploits unknown vulnerabilities in Gigabyte and Asus motherboards. How the malware got there to begin with, though, is a bit of a mystery. There's more to come on this, I suspect.
More: SecureList | TechSpot | @JusticeRage | @k8em0
Microsoft: Austrian firm behind spyware targeting law firms, and banks
Reuters ($): An Austrian "red teaming" company called DSIRF was behind a string of intrusions at banks and law firms in at least three countries, according to Microsoft. DSIRF is the developer of the "Subzero" spyware which uses Windows and Adobe zero-days to break into vulnerable PCs. DSIRF is a known as a private-sector offensive actor (or PSOA), which tend to sell their exploits but play no part in the actual hacking. But Microsoft said that they've seen DSIRF both sell and use its infrastructure to control the malware. It's not clear on who DSIRF sold its spyware to — or whether that was a government or a private-sector entity — only that the spyware was for "use in EU states only." Microsoft's technical report said DSIRF used macros as an initial point of entry and embedded its malware in a JPEG meme of Kim Jong-un holding up a guitar saying, "Can I eat this?" Relatedly, Proofpoint has some new data out this week on how threat actors are trying to skirt Microsoft's new macro blocks by burying exploits in archive files.
More: Microsoft | Reuters ($) | TechCrunch

Hacker claims access to 50 U.S. companies through breached MSP
The Record: Remember when Kaseya, a managed service provider that is effectively an outsourced IT for hundreds of companies, was hacked and used to spread ransomware to its customers? Security experts are warning that another MSP may have been compromised after a hacker claimed to have accessed the "MSP panel of 50+ companies," with a hint that the end goal is ransomware or extortion. @jgreigj does all the sleuthing you need to read, though still early days on whether a Kansas City-based MSP was the ultimate victim. Both CISA and the NSA have warned about possible MSP breaches in recent months (hmm, it's almost like they... know something we don't?), since MSPs can — and in some cases do — have large, if not unfettered access to their customers' networks.
More: @campuscodi | @gossithedog | @NSA_CSDirector
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Anti-vax dating site left user data exposed
The Daily Dot: An anti-vax dating site that allowed users to advertise their vaccine-free bodily fluids left all their users' data exposed to the internet for anyone to access. The site, called Unjected, (which doesn't even make sense?) left an internal administrator's dashboard exposed in debug mode. Just when you think you've heard everything...
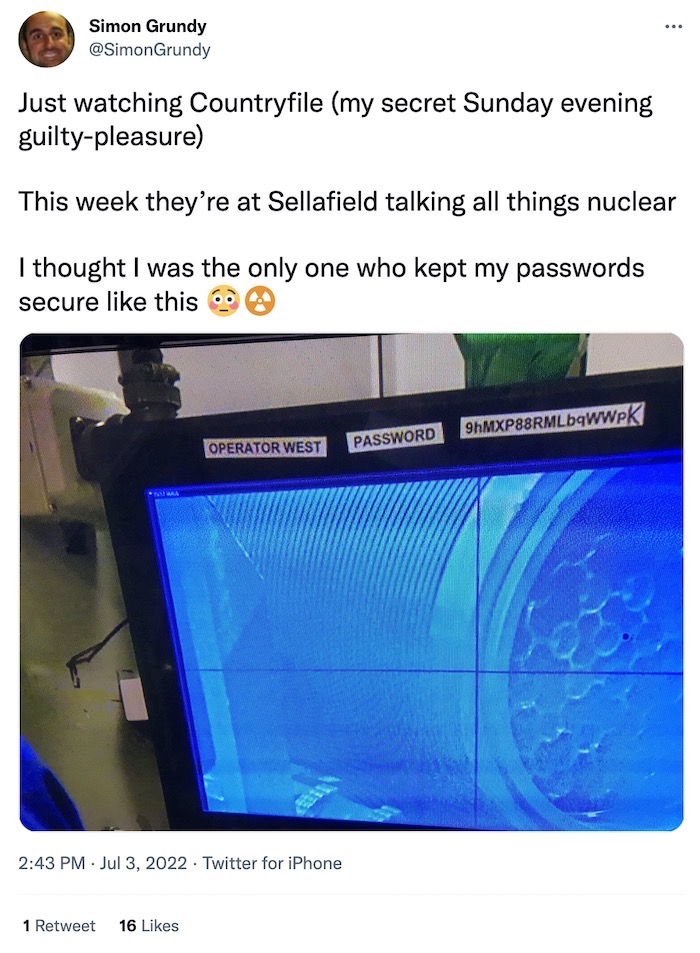
BBC broadcasts Sellafield nuclear plant password
Simon Grundy: Countryfile, a weekly BBC show dedicated to cool things going on in the British countryside (it's nice, I watched it growing up), this week went to one of the U.K.'s nuclear power plants, Sellafield. What alarmed viewers was when the camera panned over to a computer display in the control room that had a password taped to the screen. Sellafield is being slowly decommissioned, which will take years, and these days largely stores nuclear waste. Sleep easy, everyone!
EU found evidence employee phones were hacked with spyware
Reuters ($): EU officials found evidence that phones used by some of its staff were hacked with Pegasus, the notorious spyware developed by NSO Group. A letter obtained by Reuters, EU Justice Commissioner Didier Reynders confirmed his phone was "possibly" hacked after he was notified by Apple of a possible compromise. It comes in the same week that Greek politician and European MEP Nikos Androulakis was targeted by the so-called Predator spyware, developed by Cytrox. Androulakis "never clicked" on the link sent to him, which likely would have hacked his phone had he done so. @jsrailton has more.
911 proxy service implodes after disclosing breach
Krebs on Security: A "residential proxy" service that has since 2015 sold access to hundreds of thousands of Windows computers has shut down after a security incident that destroyed core parts of its operations, including critical servers and backups. "On July 28th, a large number of users reported that they could not log in the system," a statement from 911.re reads. The service was hacked weeks earlier, after evidence was found that someone manipulated the balances of a large number of user accounts. Residential proxies claim to offer similar capabilities to VPNs — by relaying internet traffic through other people's systems, often claimed for anonymity — but instead use home internet connections that are more difficult to identify and block.
~ ~
OTHER NEWSY NUGGETS
Google can warrantlessly share your data with cops: A new wrinkle in the exigent/emergency data disclosure saga. If you recall, police can ask tech companies to disclose customer data in emergency situations, like risk to life, without first getting a warrant — but that they have to get a valid legal process later. Video doorbell maker Ring fulfilled 11 emergency requests this year alone without demanding a warrant (and doesn't disclose this in its transparency report, and only disclosed it when lawmakers came knocking). Now, it turns out Google can do the same thing — though, Google says it hasn't yet turned over any data under these circumstances, according to The Verge. Meanwhile, Arlo and Wyze confirmed that they won't give authorities access to your smart home camera's footage unless they're shown a warrant or court order first — and, Apple and Anker, owner of Eufy, can't anyway since they offer end-to-end encryption. More from @rychrist in the tweets.
U.S. courts record system hacked... again: The Justice Department is investigating a data breach of the U.S. federal courts system dating back to early 2020, according to top DOJ national security official Matthew Olsen. Democrat lawmaker Jerrold Nadler said "three hostile foreign actors" were to blame for causing a "system security failure," whatever that means? What's interesting is that this is a distinctly separate attack from the courts record system breach as part of the SolarWinds espionage campaign, which saw Russian agents apparently able to access sealed court records in high profile cases. You know, like Russian indictments that were in the pipeline at the time.
Health mailing provider hit by breach: OneTouchPoint, a mailing and printing vendor used by dozens of healthcare companies across the U.S., has notified at least 30 healthcare providers and insurance carriers of a ransomware attack that compromised personally identifiable information from its network, reports SecurityWeek. The data includes names, addresses, birth dates, date of service, description of service, diagnosis codes, information provided as part of a health assessment, and member ID. It's not clear how many individuals are affected.
WhatsApp would prefer blocks than to weaken E2EE: BBC News interviewed WhatsApp chief Will Cathcart, who told reporter @shionamc that he would rather see WhatsApp blocked by governments than be told to weaken end-to-end encryption (E2EE). "If we had to lower security for the world, to accommodate the requirement in one country, that...would be very foolish for us to accept, making our product less desirable to 98% of our users because of the requirements from 2%," said Cathcart. It's not a new stance per se, we know WhatsApp and Facebook are pro-E2EE (even if it is for selfish reasons), but the first time seeing this ultimatum — if you want to call it that.
~ ~
THE HAPPY CORNER
Alright, onto the good stuff.
Let's head on Down Under to @geoffreyhuntley, who found a way to gain desktop access to a McDonalds ordering kiosk. Apparently the local user runs as "admin" rights. Always fun to pop calc in public, but Geoff's blog post explains why it's maybe a good idea not to use them. McDonalds: where the cybersecurity is as bad as the food.

Congrats to @CamilleEsq for being appointed to the White House's Office of the National Security Director as its deputy national cyber director for technology and ecosystem security, a role that is focused on workforce programs and supply chain security issues. (Double congrats for also having one of the longest job titles in government.) Stewart Gloster hails from Google and is widely known for her work in #ShareTheMicinCyber — and will start in her new role on August 1.
EU authorities have helped 1.5 million people decrypt their ransomwared computers, according to the No More Ransom project, which brings police and private industry partners together to help provide decryption tools for ransomware victims. As of now, the group offers 136 free decryption tools for 165 ransomware variants, including Gandcrab, REvil, and Maze, according to Europol. Motherboard explains more.
Here's a fun hacker project from last month that lets you set up a system that plays a loud audio clip of a dog moving towards a front door if a camera outside is triggered. The code is public, and a pretty nifty idea for when you need something convincing while you're away on vacation.
And finally, proof that you can run Doom on, well, anything and everything.

To send in good news for the happy corner, please reach out to: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is... a cyber dog, Senja. You might be this happy if you had just spent your entire day successfully hacking the cat who lives next door. A big thanks to Nikita R. for the submission!

Keep sending in your cyber cats or your other friends. Email here with their name and photo, and they'll be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
That's it for now — thanks so much for reading this week. The suggestion box is open if you have any feedback, or drop me an email any time. And, if you liked this week's newsletter, feel free to hit those share buttons below.
Same time next Sunday. Have a great week.
—@zackwhittaker