this week in security — july 4 edition
THIS WEEK, TL;DR
Ransomware attack on software manager hits hundreds of companies
Double Pulsar: If you're working this weekend, there's a greater than zero chance that it's because of the breach at Kaseya, a company that provides IT management software, Kaseya VSA, to managed service providers, which in turn remotely run the IT systems for their customers. The attack, first revealed on Friday, saw hackers push a malicious update to the software run by at least 200 companies, according to Huntress Labs, though likely a lot more, and deploy ransomware associated with the Russian-speaking REvil group. The attackers are said to have used a zero-day vulnerability to launch the attack, though technical details are still largely unknown. Think of this as 'SolarWinds but with ransomware,' and you're not far off. (The numbers are still in considerable flux, but Kaseya says it has 40,000 customers.) CISA is calling this a supply chain attack. Whether you agree, suffice to say that this "trickle-down" ransomware attack is still in motion and will likely change throughout the week.
More: Wired ($) | Kaseya | NBC News | @gossithedog
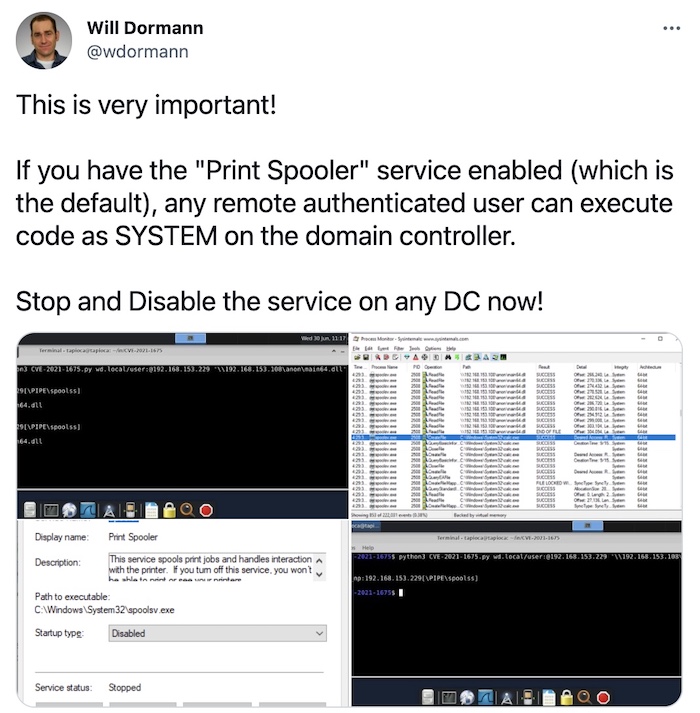
Microsoft tries, fails to patch critical Windows flaw. Chaos ensues
Motherboard: Microsoft patched a Windows flaw in early June, but that patch didn't fix a closely-related bug that's actually way worse, and can be used to remotely compromise any supported(!) Windows computer or server. Researchers have published proof-of-concept code that can exploit the vulnerability, dubbed PrintNightmare (which is not the same flaw as the bug fixed in June). Confused? So is everyone else. For now, disable the Print Spooler and hope you don't need to print anything anytime soon. Here's @_johnhammond with a video of the PoC.
More: Double Pulsar | Help Net Security | The Register | @gentilkiwi
Coordinated law enforcement action takes DoubleVPN offline, logs seized
Europol: Authorities in the U.S., Canada, and Europe have seized and taken down the infrastructure of DoubleVPN, a Russian and English-advertised VPN that claims to mask the location and activity of its users by double, triple or even quadruple encrypting the data that's sent through its service. But the service was, predictably, used by threat actors to launch cyberattacks. Now with access to the servers, infrastructure and logs, we'll have to see what law enforcement turns up — but no doubt we'll learn just how "secure" the network really was. No arrests are known to have been made... yet.
More: Bleeping Computer | Cyberscoop
Privacy watchdog member says XKeyscore still raises privacy concerns
Washington Post: It's been almost a decade (incredibly) since XKeyscore was disclosed, the program run by the NSA that's essentially a search engine for the agency's vast databases of data it collects from around the world. XKeyscore was subject to a five-year investigation by the government's privacy watchdog, PCLOB. But Travis LeBlanc, a Democratic board member appointed by President Trump, released a statement (partly redacted after declassification) that claims the board "failed to adequately investigate or evaluate" the NSA's collection activities. NSA disagreed, but it's rare to see this kind of pushback — including from Democrats, who did little to rein in the government's Bush-era surveillance powers after the Snowden disclosures. It's somewhat comforting to know that oversight isn't completely dead.
More: @ashgorski tweets
Russian hackers are trying to brute force hundreds of networks
Wired ($): The Russian-led operation that became known as the SolarWinds espionage campaign earlier this year made headlines, but all the while another unit of Russian government hackers were quietly trying to brute-force their way into hundreds of networks. Mass-password guessing is a crude attack but it's effective when it works. That's what the NSA said this week when it released an advisory warning that this effort was underway, and that this effort is likely to "collect and exfiltrate data, access credentials and more." NSA said Fancy Bear, or APT 28, was to blame for the password-guessing spree, the same attackers who ran hack-and-leak operations during the 2016 U.S. presidential election.
More: ZDNet | BBC News | The Register
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
How a Docker footgun led to a vandal deleting NewsBlur's MongoDB database
Newsblur: The tl;dr is that someone deleted NewsBlur's MongoDB during a migration, though no data was lost or stolen. But the write-up of what happened is an incredible first-hand view of how to discover and remediate a semi-successful cyberattack. An absolute must-read, and major props for this level of transparency.
Hackers exploited 0-day, not 2018 bug, to mass-wipe My Book Live devices
Ars Technica: Last week's mass-wiping of Western Digital devices was as a result of a vulnerability that the company itself introduced in 2011. Hackers found the bug and used it to remotely wipe storage drives without requiring a password. Much of the digging here was done by @dangoodin himself, one of the finest technical cybersecurity reporters in the industry. Western Digital confirmed the findings, and will provide data recovery services starting next month.
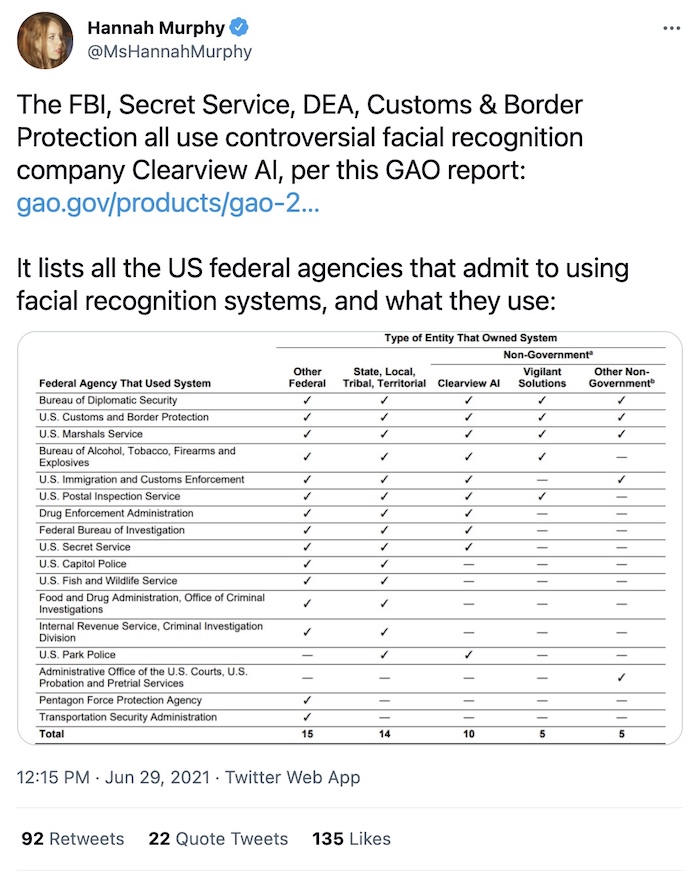
GAO may have missed Clearview AI use by five federal agencies in a new report
BuzzFeed News: Who's watching the watchdogs? BuzzFeed, evidently. @caro1inehaskins had a short but good thread on a new report by the Government Accountability Office about federal agencies' use of facial recognition. But the report curiously omits data from agencies that used Clearview AI, the controversial facial recognition startup made up of 3+ billion scraped public profile photos (allegedly). Several agencies said they didn't use Clearview, but were listed as having used the technology as noted by an earlier BuzzFeed investigation. GAO could not explain the discrepancy but noted that the agencies self-reported their use of facial recognition. Hmm!
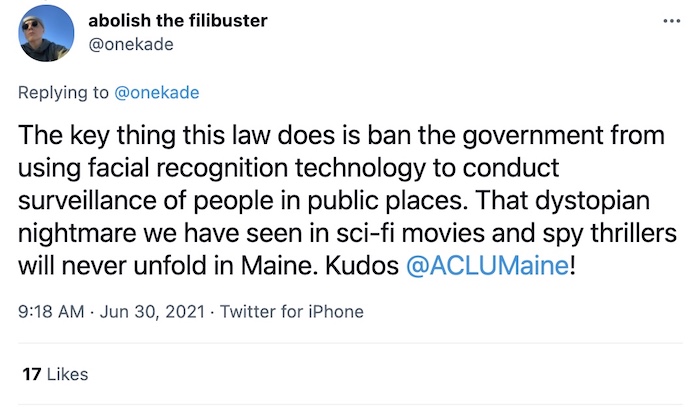
Maine bans facial recognition in Maine, with limited exceptions
Kade Crockford: Excellent news: @onekade reports that Maine's legislature has banned facial recognition across the state with limited exceptions. Crockford said this ban will prevent most government agencies (including schools) from using or possessing facial recognition tech. Exceptions, though, will allow police to request the use of it in serious criminal investigations.
~ ~
OTHER NEWSY NUGGETS
New charges filed against Capital One hacker, trial postponed to 2022
Paige Thompson now faces up to 20 years in prison after the Justice Department filed a superseding indictment with fresh hacking charges, on top of the chief accusation that she took records on more than 100 million Americans from Capital One's AWS-hosted servers. Thompson is now accused of hacking into an unnamed U.S. state agency, a U.S. public research university, and a technology company that provides threat protection services(!). She is accused of using her knowledge as an engineer at Amazon to download the data from systems where web application firewalls that she allegedly knew to be misconfigured. Her trial date was pushed back to 2022.
Windows 11's security push puts Microsoft on a collision course
Windows 11 has raised the security bar, and in the process left plenty of older computers stranded and unable to upgrade. That's because the minimum hardware requirements have gone up with the next Windows release. Much of the requirements hinge on having a TPM 2.0 chip, which Microsoft has required in all new Windows devices since 2016, but many don't have it enabled.
Apps with 5.8 million Google Play downloads stole users’ Facebook passwords
Google has booted nine apps from its Google Play app store after researchers found they were secretly stealing Facebook credentials. The apps were downloaded more than 5.8 million times, per Dr. Web. Google pulled the apps — which is good — but doesn't look good for Google Play's allegedly high-walled garden.
~ ~
THE HAPPY CORNER
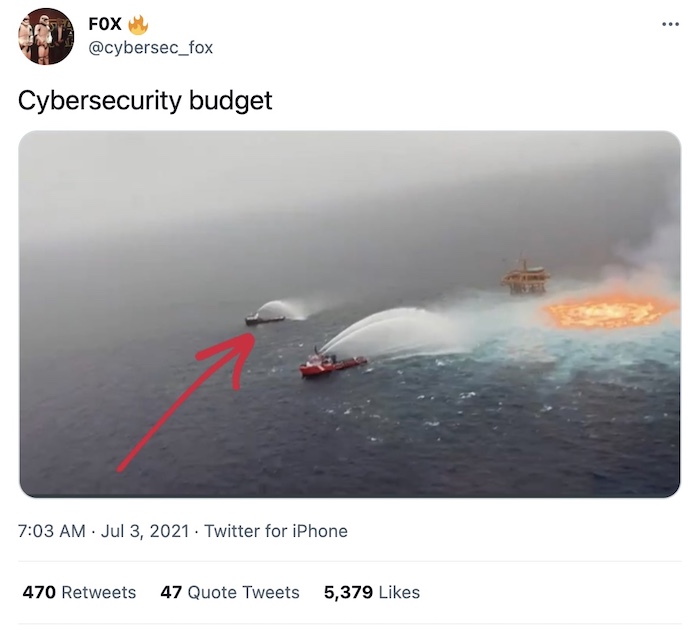
I wish there was more good news in the world this week, but alas it's been a tough one. That said, my heart goes out, especially, to everyone working in the U.S. on this July 4th holiday — especially given that this tweet by @cybersec_fox is all too real.
And finally, a quick one from me. This edition of ~this week in security~ marks the third year of this newsletter first going out. This newsletter goes out to 8,500+ subscribers each week, which is the only data point I have on this newsletter since I don't track clicks or opens. I'm enormously proud of this thing. A lot of work goes into it and it's a real labor of love, but it's really the highlight of my week. I'm grateful I get to read some of the best security news and research from the sharpest journalists and hackers in the industry, and share it with you every Sunday. I'm also deeply thankful for everyone who reads and subscribes, and to those who chip in on the costs that go into making this newsletter each week (and get stickers and a mug in return!)
If you like the newsletter, please recommend to a friend: this.weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Kiska. He's in your house to steal your heart — and your Wi-Fi. You're adorable, Kiska. Big thanks to his human Sergey T. for the submission!

We're low on cyber cats (and their friends) — keep sending them in! Drop me a photo with their name, and email it here. And of course you can submit more than one!
~ ~
SUGGESTION BOX
That's all for this week. Hope you have a good July 4th for all the folks who mark the day. The suggestion box is open for any feedback you might have. Take care, and see you next week.