this week in security — july 6 2025 edition
I'm starting with a little personal note from me. This newsletter edition marks the seventh(!) anniversary since launching ~this week in security~. I'm thankful, honored and grateful for your trust, readership, and support. Writing this weekly dispatch to thousands of people every Sunday is the highlight of my week, as much as I hope it's one of yours.
More from me in a few, but first, I guess we should do… the news!
~ ~
THIS WEEK, TL;DR
U.S. DOJ announces charges, actions against North Korean IT worker operation
Justice Department: Some great news to start the week! Phhhrrbbbt! 🥳 The U.S. announced it successfully outed and knocked back North Korea's remote IT workers' operations. This long-con scheme has been described as a "triple threat" because these North Koreans infiltrate tech companies to earn a wage, stealthily steal their intellectual property, and then use the data to extort the companies for money. North Korea uses its regular payday to fund its sanctioned nuke program to the tune of billions of dollars. (Yeah, they're not messing around!) The DOJ announced multiple charges to name-and-shame the operators (who are still in North Korea), as well as taking down over two-dozen "laptop farms" across 16 states that were used by the North Korean spies to remotely "log in" to the U.S. as if they were located here. These North Korean scammers are deeply embedded in the crypto world as well as the Fortune 500 — and yet this scheme allows them to make bank, per the WSJ ($), which profiled one affected firm. Microsoft has a good dossier on the threat, but remember that this recent catch of spies is still only a drop in the ocean.
More: Associated Press | Wired ($) | TechCrunch | The Record | ABC News

U.S. probing whether ransomware negotiator took slice of hacker payments
Bloomberg ($): Sticking with the feds for a hot second, in separate news, the DOJ is reportedly investigating a former ransomware negotiator who allegedly took a cut of the ransom payments paid to hackers. The former negotiator isn't named, but worked for DigitalMint, which the company confirmed in a statement. Negotiators "help" (air quotes) to settle ransomware attacks by facilitating ransom payments to hackers who lock a victim's systems with file-encrypting malware. This isn't illegal, but the FBI and others have long advised against paying ransoms because (for many reasons...) this doesn't guarantee the data's safe return or that the victim won't get re-victimized with another ransom demand. Watch this space: It seems like this entire cottage industry (which ProPublica profiled in 2019) is on shaky ground. The DOJ hasn't commented yet, nor released the allegations.
More: Bleeping Computer | CoinTelegraph
Ingram Micro outage caused by ransomware attack, company confirms
Bleeping Computer: Prepare for a rough week if you've got any dealings with Ingram Micro... Bleeping Computer reports the U.S. tech distributor and managed service provider (read: outsourced IT) was hit by a SafePay ransomware attack, citing sources and employees who saw ransom notes visible on internal computers. The company said in a statement on Saturday that it "identified ransomware" on internal systems. The outage began Thursday, just ahead of the July 4 holiday (which probably isn't a coincidence — incidents happen around holidays and downtime). By Friday, Ingram Micro hadn't disclosed anything untoward beyond a "technical difficulties" notice (heavy wink) on its website, until Saturday when it was forced to 'fess up after Bleeping's reporting. Clearly, everything is not fine and we'll likely hear more about the incident and its downstream effect this week.
More: Ingram Micro (statement) | Reuters ($) | The Register | Reddit /r/msp
~ ~
THE STUFF YOU MIGHT'VE MISSED
Xfinity Wi-Fi 'motion tracking' feature allows data sharing with cops
Xfinity: Comcast has a new "feature" in early preview called Wi-Fi Motion, which uses Wi-Fi signals to detect motion in a person's home if they're away. Sounds cool in theory, but Comcast makes it clear that it may "disclose information generated by your Wi-Fi Motion to third-parties without further notice," which can include telling law enforcement whether you're home or not.
AT&T rolls out new account lock security feature
The Verge: In news you can use: AT&T has a new security account lock feature that allows customers to prevent unauthorized modifications to their phone account, with the aim of preventing SIM swap attacks and phone number changes. It's a good (overdue) step that tacitly confirms phone companies are still battling SIM swappers and other social engineering attacks. Verizon, T-Mobile and others have a similar feature, too.
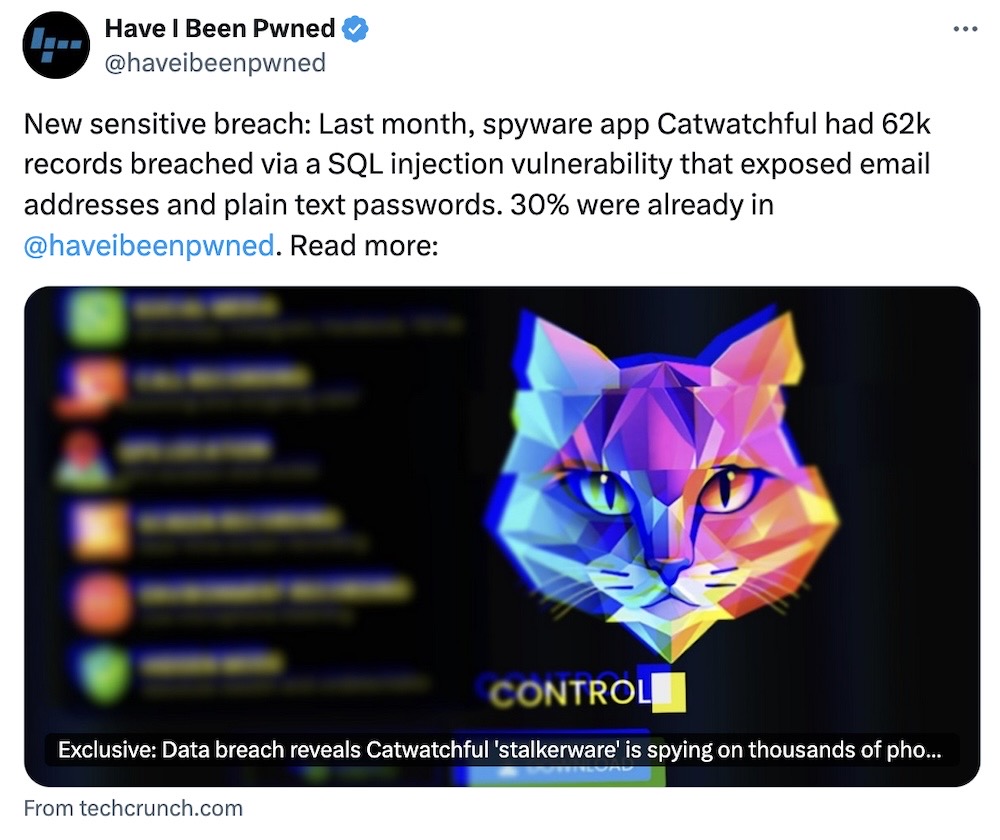
Catwatchful spyware bug exposes thousands of hacked phones — and its admin
TechCrunch: Security researcher Eric Daigle found an SQL injection bug in an unauthenticated API of a stealthy phone monitoring app called Catwatchful. The bug exposed thousands of users who signed up to spy on someone's phone (gross, illegal... and did I mention... gross?!). Daigle shared the extracted text-only database of customers and victims with me, which contained real-world and identifiable information on none other than Catwatchful's "anonymous" administrator, which I reported for TechCrunch. (Disclosure alert!) Sweet karma aside, the Catwatchful spyware also has a backdoor code, so the hidden app is easy to identify, which I explain in my piece. With no prospect of the administrator disclosing the breach, the data was shared with breach notification site Have I Been Pwned.
Criminals are smarter and faster: CISOs must rethink defense playbooks
CSO Online: Cynthia "Metacurity.com" Brumfield has solid analysis and advice out this week on how and why CISOs should rethink their defensive planning and strategies, especially in the face of today's financially motivated attacks, which are faster and more ruthless than ever and lead to ransomware and extortion attacks (think Scattered Spider!) Now, the real trick is getting the C-suite executives to actually care before it's too late.
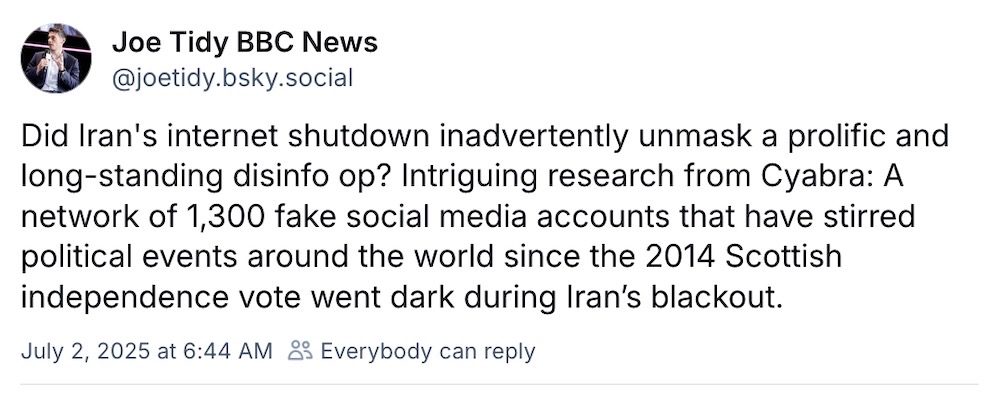
Iran's internet blackout exposed political disinformation operation
Joe Tidy: An Iranian government-ordered internet outage caused one of the country's major long-running disinformation operations to go silent, inadvertently exposing it, per the BBC's cyber reporter. The network of some 1,300 fake social media accounts used for meddling in politics disappeared for 16 days, a period that "directly aligned with Iran's nationwide blackout," which began after the brief military conflict between Iran, Israel and the U.S. a few weeks ago. Guess what happened when the power went back on? Bingo.
'El Chapo' cartel used phone data and CCTV cameras to find FBI informants
DOJ OIG: Absolutely wild disclosure from the DOJ's watchdog, which conducted an audit of the FBI's counter-surveillance and opsec practices for protecting sensitive investigations. Turns out that in 2018, a hacker hired by the Mexican drug cartel run by notorious kingpin "El Chapo" was somehow "able to use" (it wasn't specified how) an FBI attache's phone to grab calls and location data to identify and "kill potential sources [or] witnesses." Spyware would make sense, but practically speaking, given how many bugs are in the SS7 protocol that connects much of the world's telcos together akin to string and sticky tape, that'd be my top guess.
Android 16 can warn users connecting to fake cell towers
Android Authority: Speaking of dodgy cell shenanigans: Android 16 is getting a new feature that can alert users when their device connects to a potentially fake cell tower. These are sometimes called "stingrays," a secretive cell site simulator device that cops use to mimic cell towers, which can be used to identify the locations of nearby phones. These are often used in criminal investigations, but also sometimes deployed at big events, per Wired ($).
~ ~

~ ~
OTHER NEWSY NUGGETS
Qantas cyber "incident": Aussie airline giant Qantas said 6 million records of customer data may have been stolen from a third-party platform in one of its contact centers. Qantas admitted fault. The data includes email addresses, names, phone numbers, dates of birth and frequent flyer numbers. Side note: please don't "noindex" your breach pages. (via Qantas, News.com.au)
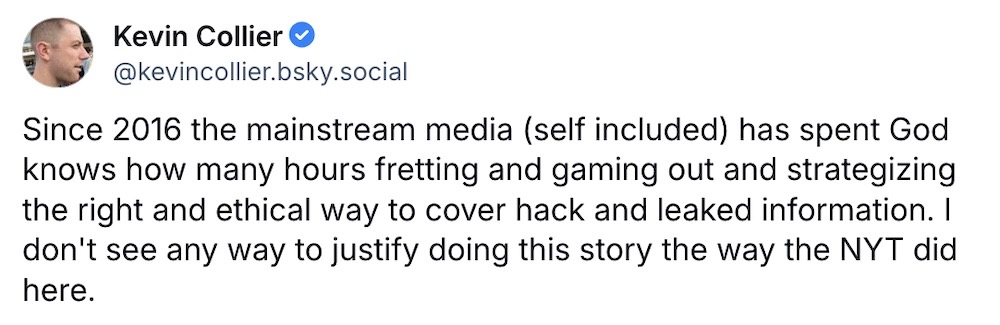
Applicants' data stolen in Columbia University hack: Bloomberg ($) confirmed and verified that a database allegedly stolen from Columbia University was in fact authentic by contacting individuals whose information was in the dataset. The information contains applicants' information — including citizenship data — going back years. That's hugely sensitive, especially given today's politics and, well, everything regarding the university right now. On the other hand, The New York Times published a piece using that hacked dataset, which was provided by a promoter of white supremacy, to smear a New York mayoral political candidate. Politics notwithstanding, actually: for a news outlet to use hacked data in this way was deeply unethical and not justified. (via Columbia Journalism Review)
IU cyberattack... cover-up? Indiana University has acknowledged that a weeks-long outage of its websites was a "security incident," but the university's top IT official seems to think he doesn't expect there to "ever be a public airing" about the breach. Well, that's deeply unethical as noted by @tarah. Cue the inevitable floodgates opening in 3... 2... 1... (via IPM, @the_real_sand)
International Criminal Cyberattack Court: The International Criminal Court confirmed it was hit by a fresh cyberattack that it described as "sophisticated" (yeah, yeah, they all say that). Little else was said about the incident, but notable since by the court's own admission that this is its second hack in three years. (via ICC)
Treasury just can't stop getting hacked: More great reporting from Bloomberg ($), looking at a trio of hacks that befell the Treasury in recent years, raising questions about the department's ability to protect itself from hacks, in spite of its... *checks notes* $1 billion cybersecurity budget...(!) This is a long-read, but worth it. (via Bloomberg ($))
Medicare.gov accounts used in fraud scheme: The U.S. Centers for Medicare & Medicaid Services (CMS) alerted over 100,000 beneficiaries of Medicare that their information was breached after scammers created online accounts using their previously-made public information as part of a fraud scheme to steal funds from the government. A similar-ish fraud scheme hit the U.K. taxation office some weeks back. (via DataBreaches.net)
Swiss government data hit by ransomware: Zurich-based non-profit health organization Radix said it was hacked and hit with ransomware, after a gang posted stolen data on its dark web leak site. The data can be restored, but apparently also affects several Swiss government agencies. (via Swiss government, The Record)
~ ~
THE HAPPY CORNER
Ding, dong, it's the good news gong. Welcome once again to the happy corner! There's a little something for everyone.
I have to admit that I laughed when I saw this historical reason for blocking access to Mastodon from a school's network.
It's always good to see a ransomware gang shut down.
I'm absolutely thrilled to return with another episode of What Can Doom Run On?, and this week it's... a set of earbuds?! Oh-kay then. You'll want to read this hilarious teardown of these headphones and the security flaws found along the way.

And finally... seven years flies by so fast... I can't tell you enough how much of a joy it is to write and curate this newsletter for you every week; some of you have been reading since the very first edition back in July 2018! Since its launch, ~this week in security~ has grown to thousands of weekly readers all over the world, with friends of the newsletter regularly contributing interesting news stories, groundbreaking research, cool things from around the web — and, of course, cyber cats (and friends!) that are featured each week. (If you haven't sent one in already, please do!)
Without your support, I doubt ~this week in security~ could've lasted this long, as the costs of running the newsletter continue to go up. As a working journalist, I cannot accept ads or sponsors, so this newsletter relies entirely on the generous support from you to keep it running. If you love this newsletter, please consider supporting with a few bucks or more to get cool swag from me to say thanks!
You may remember a few months ago, I ran a feedback survey to hear from you about what you like and what you'd want more of in this newsletter. Hundreds of you reached out with your insightful and kind feedback, and I'm excited to share more with you in the next few weeks. Don't worry; this free weekly newsletter isn't going away anytime soon — here's to another seven years!
~ ~
CYBER CATS & FRIENDS
Meet Rosie ... this week's cybercat... or this week's cyber eavesdropper. You never know when your communications are being monitored, especially by a cat-in-the-middle attack. Thanks so much to Michael T. for sending in!

Keep sending in your cyber-cats! Got a cyber-cat or a non-feline friend? Send me an email with their photo and name and they will be featured in a future newsletter.
~ ~
SUGGESTION BOX
This edition has already gone on for way too long... thanks for sticking around! I'll sign off for now and let you get back to your weekend. If you do want to get in touch, please do reach out!
See you next,
@zackwhittaker