this week in security — july 9 edition
THIS WEEK, TL;DR
Lawmakers push amendment limiting U.S. agencies from buying location data
Wired ($): A very quiet week this week thanks to July 4, but here's a belter: A bipartisan pair of U.S. lawmakers are reintroducing an amendment to the U.S. national defense spending bill (known as NDAA), which has to pass every year, to limit what commercial data U.S. agencies can buy on Americans. The amendment already has chops, gathering support from both sides of the House. U.S. agencies are buying search and location data and other personal information that can be obtained from apps and services, and made available to data brokers, according to the ODNI. The amendment was introduced last year, but was stripped from last year's NDAA in the end. Will this year's effort make it?
More: @RepSaraJacobs | @demandprogress
Security researchers latest to blast U.K.'s Online Safety Bill as encryption risk
TechCrunch: Meanwhile, on the other side of the pond, things are looking dicey with the Online Safety Bill, which is currently under review in the upper chamber of the Lords. Some 68 researchers and academics have signed onto an open letter [PDF] putting the U.K. government on notice about the "child safety" bill (it's actually about undermining end-to-end encryption, and the experts say so), because like everyone else has been saying over the past few decades, there is no such thing as a secure backdoor just for police or the feds. Alas, British lawmakers aren't listening (or care — well, that's definitely clear). Still, with organizations like Signal and WhatsApp threatening to leave, and Apple putting on its rare boxing gloves, I can't imagine this ending well for the U.K. government.
More: Open Letter [PDF] | TechCrunch | Reuters ($) | SecurityWeek
New 'critical' MOVEit transfer tool flaw discovered
CRN: Progress, the company behind the beleaguered MOVEit Transfer tool that allows organizations to share huge data sets across the internet, has released fixes for three more flaws in its software, including a critical bug. The updates come weeks after the Clop ransomware gang found a zero-day vulnerability, which it used to mass-hack and raid hundreds of MOVEit servers — and everything stored inside — causing havoc across the industry. At least 17 million individuals are known to be affected, but that figure is likely significantly higher, as only a handful of organizations have confirmed data thefts. Better to get these patches out sooner than later. Progress says these bugs haven't been exploited — but, given it was a zero-day caused this whole mess, that's still not enough for admins to sleep well at night.
More: Progress Software | @snlyngaas | @sloppy_bear | @brett

Hundreds of thousands of servers vulnerable to critical Fortinet flaw
Ars Technica: Some 335,000 internet-connected Fortinet devices are vulnerable to exploitation because of a vulnerability with a 9.8 out of 10 rating, according to latest data from Shodan. Despite making patches available, some 70% of servers remain unpatched. A heap corruption bug (which Fortinet details here) can — and has — allowed hackers to remotely access affected systems. CISA has also added the new vulnerability — tracked as CVE-2023-27997 — to its catalog of known vulnerabilities. Fortinet confirmed there has been some exploitation to date, though it's not clear how many victims are known to be affected.
More: The Record | Bleeping Computer | The Register
~ ~
THE STUFF YOU MIGHT'VE MISSED
How Threads' privacy policy compares to Twitter's (and its rivals')
Wired ($): Yet another social app dropped this week. Threads, built by Facebook-owned Meta, is as much of a data trap as you'd imagine, collecting a metric ton of data about you, compared to the minimalism of Mastodon, which is none. Plus, Threads isn't opening to Europe any time soon, because Facebook — which makes all its money from tracking and profiling its users — can't guarantee it won't fall foul of GDPR's stronger privacy protections, compared to the U.S. law... oh, which doesn't exist.
Mastodon patches critical 'TootRoot' bug
Bleeping Computer: Speaking of Mastodon, this week security patches rolled out, including a fix for a bug that could have allowed attackers to create and overwrite any Mastodon server file, and obtain remote code execution, because of duff media processing code. According to @GossiTheDog, exploitation is relatively simple (and tootable), hence why the bug is called TootRoot. As you'd imagine, a pretty serious bug to discover, but the patch disclosure went pretty well — better than how some companies handle it, at least. The big Mastodon instances were immediately patched. The bug was found by Cure53 during an audit done at Mozilla's request.
Russia seeds a surveillance supply chain
The New York Times ($): Russia has amassed a huge arsenal of tech to track its own citizens, including buying tech from startups and contractors in the country. Now, Russia is using some of that tech, which largely plugs into Russia's existing telecoms infrastructure for a range of surveillance, to crack down on dissent. Some of its technologies can map relationships with people (such as knowing when people use apps like Signal, WhatsApp and Telegram — even it can't access their content), collecting passwords from unencrypted websites, and triangulating what phones have been in certain places. Interesting thread by @jsrailton on this story.
Ransomware criminals are dumping kids’ private files online after school hacks
Associated Press: A really good, but heartbreaking story about how kids are finding out that their data — some of it highly sensitive, personal, and mental health-related — is out on the open web after a string of ransomware attacks and data breaches, often by companies with crap security. AP informed several families whose data was compromised, who acknowledged that they weren't notified, with some of the exposed data including reports on sexual assault complaints by children. The AP said the children feel "doubly victimized" by the breaches. As adults, we're not just failing at security — we're failing the kids by failing at security. More by @fbajak in the tweets.
Deputy marshal pleads guilty to fake location data requests
Justice Department OIG: Deputy U.S. Marshal Adrian Pena pleaded guilty on June 30 to misusing a law enforcement tool run by a third-party company called Securus, which he used to upload fake subpoenas — sometimes blank pages — to obtain location data on individuals whom Pena had personal relationships with. Motherboard reported on this last year when the news first broke. Securus drew ire when it was discovered a few years ago that cell networks were selling its customers' location data to brokers, who sold the data on to companies like Securus.
~ ~
~ ~
OTHER NEWSY NUGGETS
Japan's busiest shipping port offline: CNN reports that Japan's Port of Nagoya was hit by LockBit ransomware, linked to Russian hackers, which prevented the port from receiving shipping containers for two days. The port handles cars, engines and other goods critical to the Japanese economy. (via CNN)
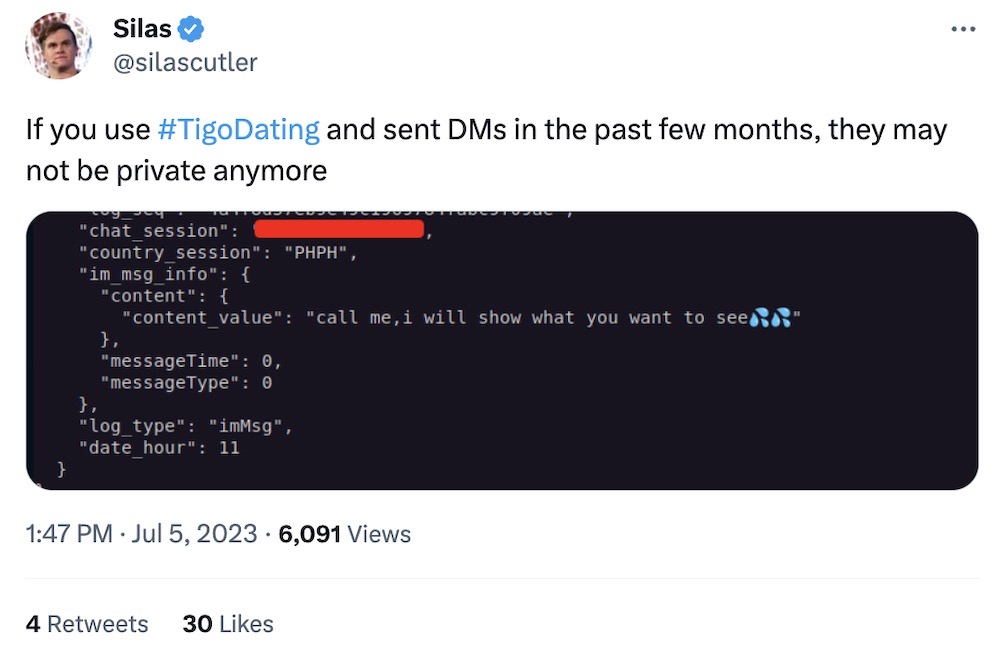
Tigo user? Maybe don't: It's not yet clear how or why, but some are reporting that a dating app called Tigo is exposing millions of private messages, potentially as many as 100 million. The app in Google Play claims that no data is collected. I see Google's safety labels are working well pretty useless. (via @silascutler, DataBreaches.net)
No response to massive Bangladesh data leak: A huge amount of Bangladesh's citizens' data has spilled online, according to a security researcher who found it. @lorenzofb verified the data was authentic and contacted the government for comment, but no dice and no response. The data includes full names, phone numbers, email addresses and national ID numbers. (via TechCrunch)
JumpCloud nukes API keys: Something is going on at JumpCloud, which says it's responding to an "ongoing incident," which hasn't yet been disclosed, but JumpCloud said it's invalidated all API keys in the meantime. (via @leereichardt)
Écoute clandestine: French lawmakers have agreed to a new justice reform bill that will allow authorities the "power to get suspects' geolocation through phones and other devices," as well as the ability to remotely activate cameras and microphones. A backdoor or some kind of government-mandated access won't fly, but it sounds like the French are justifying the use of spyware or other phone malware. Civil liberties concerns were raised, but largely ignored. (via Le Monde)
~ ~
THE HAPPY CORNER
Happy Sunday, and welcome to the happy corner. It's a short week, given July 4 here in the U.S. (Hope you had a good one!) Still a couple of things to share.
The next time a computer asks me not to challenge my login for a time, I'm going to think about this toot.

And finally, I want to thank you for reading, subscribing, donating, and submitting your cybercats and more. This newsletter hit the five-year milestone this week (can you believe it?). I love writing this newsletter, and couldn't be more thankful that I get to share it with you every week. Thanks again, so much, for all your support.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is HRH Lord Meow, who as you can see is perfectly adhering to treat-factor authentication before allowing anyone through that door. Excellent security as always, your royal highness. Many thanks to his human, Tapas, for sending in!

Thanks for sending in your cyber cats — keep them coming! Send in your cyber cats (or non-feline friend) with a photo and their name, and they'll be featured in a newsletter.
~ ~
SUGGESTION BOX
That's it for this week. Same time, next? As always, please do email me with any feedback, suggestions, or other thoughts about this week's (or next week's) newsletter; it's always really lovely hearing from folks.
Toot toot,
—@zackwhittaker