this week in security — june 11 edition
THIS WEEK, TL;DR
MOVEit hack: BBC, BA and Boots among victims
BBC News: More victims of the MOVEit mass-hack are coming forward. Zellis, a U.K. payroll provider, confirmed that its MOVEit file transfer tool was breached, allowing hackers to access a ton of data on other U.K. businesses — the BBC, airlines British Airways and Aer Lingus, and pharmacy giant Boots are all Zellis customers and are among the downstream companies affected. (These file transfer tools are for sharing huge data sets over the internet.) Adding an unfortunate twist, MOVEit's corporate parent Progress confirmed a second vulnerability (patch now!), just as Kroll said the first bug may have existed since 2021 (oof!). The fallout is expected to continue as the Clop ransomware gang — blamed (and taken credit) for the mass-hack — names more victims. If you're wondering, "doesn't this all sound rather familiar?" It does, because it is! This is believed to be the third time Clop has used a zero-day to mass-raid corporate file transfer tools. First it was Accellion's file transfer tool, then Fortra earlier this year.
More: Bloomberg ($) | The Record | Kroll | @razhael
Barracuda urges replacing — not patching — its email gateway hardware
Krebs on Security: From one fustercluck to another. You know it's bad when a tech company tells you to rip out your hardware and replace it, but that's what happened with Barracuda Networks, the maker of network security appliances. Barracuda said a vulnerability in its Email Security Gateway (ESG) devices should be "immediately replaced regardless of patch version level," per a blog post. (These devices filter email messages for malicious content.) Clearly however the hackers exploiting the zero-day achieved device access persistence that requires the owner to throw it out and replace it altogether, since patches aren't enough to boot the attackers out. It's rare, extraordinary guidance. For context, Barracuda has some 200,000 corporate customers around the world, including the Australian Capital Territory government, which confirmed it was likely hit.
More: Barracuda Networks | TechCrunch | The Register | SecurityWeek
North Korean hackers target NK Pro readers with malicious websites, emails, docs
NK Pro: Hackers associated with the North Korean regime, dubbed Kimsuky, targeted a popular news and research site about North Korea, NK Pro. SentinelLabs said it found the group trying to steal subscribers' credentials by sending initially legitimate, then later malicious documents that prompted for the user's Google password. Other documents were laced with the ReconShark malware, which exfiltrates information about a device for conducting subsequent "precision" cyberattacks. By going after NK Pro subscribers (going as far as spoofing its domain), the believed aim was to target "high-profile experts in North Korean affairs" to help understand how the country is perceived. The FBI, NSA and South Korean intelligence issued an advisory [PDF] just days earlier saying it was part of a wider intelligence gathering effort by the Kim regime to aid the breakaway country's decision making. Not that it seems to think about much other than nuclear weapons...
More: SentinelLabs | Bleeping Computer | CSO Online
~ ~
THE STUFF YOU MIGHT'VE MISSED
Analysis of common spy camera reveals non-fixed flaws
Arxiv: Spy cameras are bad. (In fact, spying on anyone without permission is bad). But what's even worse is that many of these tiny internet-connected spy cameras have major security flaws. According to a new paper, researchers examined a generic whitelabel and rebranded spy camera and its Android app, and confirmed that "serious vulnerabilities have been identified in every component." Some of the flaws are as easy as using a camera's serial number, which some customers share publicly in reviews, while other flaws allow the theft of the Wi-Fi network's password, and potentially allow hackers to pivot to other devices on the network. The manufacturer has "no intention" of fixing the problems, despite some 50 million of these IoT devices out there in the wild. Lovely, he says in an incredibly sarcastic voice.
Martinique dealing with cyberattack that knocked government services offline
The Record: The Caribbean island of Martinique says internet access and other infrastructure has been disrupted for weeks following a suspected cyberattack. Databreaches.net says the Rhysida ransomware gang took credit for the attack. The French government, which claims the island as an overseas territory, hasn't yet commented. The government in Martinique, for its part, published a statement [PDF] that basically provided a ton of cyber advice, as officials continue to work to restore services across the island nation.
Turkish citizens' personal data offered online after government site hacked
BalkanInsight: Speaking of country hacks... now Turkey? According to local news, a website is offering data on Turkish citizens allegedly stolen from a government website — including Turkish president Recep Erdogan. The publication said the data includes "ID numbers, phone numbers and information about people's family members."
Log4j was bad, but "everybody was rushing to patch, too"
Washington Post ($): A little glimmer of hope for the crowd. This week, Verizon published its annual Data Breach Investigations Report, which looks at the security landscape over the past year. Turns out that the Log4j bug, which was actively exploited and put hundreds of millions of devices at risk, wasn't as bad as feared. Just as the alarm bells started to go off, there was a rush to exploit — but there was as much of a push to patch, too. Log4j is a major, ongoing bug — but "the scale of this was potentially muted because of the coordinated response." See? Look what happens when we all work together.
State Dept. offers $5M for information on key Anom distributor
Motherboard: A few years ago, the FBI secretly infiltrated an encrypted phone company called Anom, allowing it to spy on hundreds of gangsters and organized criminals that used Anom's encrypted phones. Now the U.S. government wants help capturing Maximilian Rivkin, an alleged top figure and key Anom phone distributor, who apparently had no idea that the feds were running the company he was essentially working for. (Reminder that @josephfcox is literally writing the book on this.) The State Department is now offering $5 million in help capturing the alleged crim. Rivkin is believed to be located in Turkey. Here he is in happier times.

Honda's power equipment and gardening tech platform allowed access to "all data"
Eaton Works: Missing access controls allowed hacker Eaton Zveare access to all data stored in Honda's power equipment, marine, lawn and garden dealer e-commerce platform. (Same name, but this has nothing to do with Honda vehicles, just so you know.) Using a test Gmail account (literally test@gmail.com), Eaton could access reams of customer data. As usual, they have a fantastic write-up. Obscure? Yes. Good security find? Also yes. As weird as Eaton's hot tubs security story? Almost certainly.
~ ~
OTHER NEWSY NUGGETS
Rickrolling ISIS: Australia's Signals Directorate, aka spies down under, targeted Islamic State fighters with zero-click malware... and not just to rickroll them. The malware was designed to play the now-infamous video to knock fighters' devices offline but didn't always work very well. A second payload was worked around by Islamic State tech support (a real thing, apparently). A third and more successful payload made it more difficult for fighters to coordinate their defenses. The newly revealed secrets were aired as part of a documentary. (via The Register)
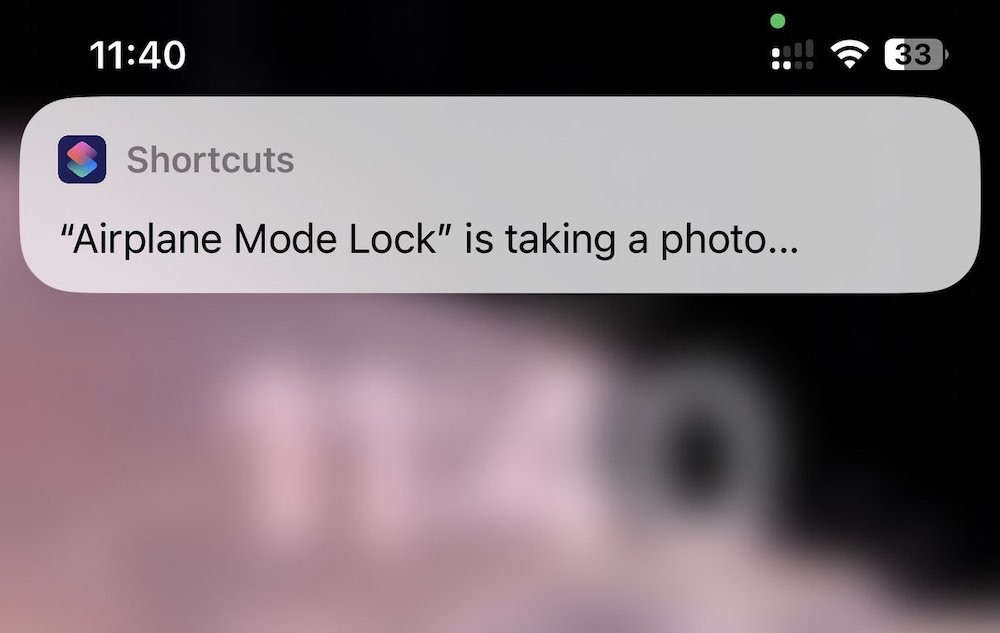
iOS shortcut blocks airplane mode: What's the first thing a crook does with a stolen phone? They switch it onto airplane mode. That blocks connectivity, including the ability to remotely wipe a stolen phone. @diegojimenez has a new iOS shortcut that effectively adds a passcode to the airplane mode option, preventing thieves from blocking access to your phone. As with any work in progress, your mileage may vary, but this is a pretty nifty approach. Plus, if the passcode is wrong, it'll blast out your phone's location — and a selfie of the thief. Brilliant! (via @geekgrrl)
Contractor accounts are a hacker's best friend: Cisco Talos has new research out this week that shows vendor and contractor accounts — often with expanded privileges and access due to customer service or other administrative functions — are increasingly targeted by malicious hackers working to gain access to organizations' networks. In two recent incident response investigations, Talos researchers found two vendor accounts with domain admin or similar privileges. Time for an account audit? (via Cisco Talos)
Lockdown Mode coming to Apple Watch: This week, Apple's annual tech reveal confirmed iOS 17 will land with a ton of new things, including security and privacy features, like passkey sharing (more later). Apple said Lockdown Mode, which aims to block nation-state cyberattacks like spyware, is also coming to Apple Watch. While exploits targeting Apple Watch are rare, they're not unheard of. (via Apple)
IOActive opens huge cyber security lab: Cheltenham, just around the corner from Britain's GCHQ, is the new home to IOActive's cybersecurity lab, according to the BBC. The 5,000 sq ft facility is said to be one of, if not the biggest private cybersecurity labs in the world. IOActive are research-driven pentesters and security consultants, who've hacked planes, vehicles and industrial control systems — and infamously tricked an ATM to spit out money. (via BBC)
The P in ChatGPT stands for 'pirate': People are pirating access to ChatGPT by using stolen OpenAI API tokens that have been scraped from other people's code. These keys can allow people to use ChatGPT for free — well, the actual account owner's bill is racking up. (via Motherboard)
~ ~
THE HAPPY CORNER
Happy Sunday, and welcome to the happy corner. This week I'm in London (a lucky escape, since New York was smoggy as hell last week due to the Canadian wildfires). It's been a while since I've been home, and it's good to be back! While I'm here, here's a random OSINT challenge. If you can figure out where I was, reply to my toot!
From this week:
Phishing-resistant passkeys are taking off, with Apple, Google, Microsoft and other big tech giants supporting the new authentication method. Apple said this week it'll allow passkey sharing (and generally better passkey management) with friends and family, all end-to-end encrypted. @rmondello explains more in a toot.
This is just brilliant: @uuallan and a team of artists are working on a comic book form of Yours Truly, Johnny Dollar, a radio series mostly during the 1950s about a private detective. Now, Dollar is back, this time as a cyber insurance investigator with a modern twist, by trying to piece together clues from ransomware attacks. You can support the project on Kickstarter. (I'm super excited for this.)

And, speaking of British things... (since we have postcodes, not ZIP codes).
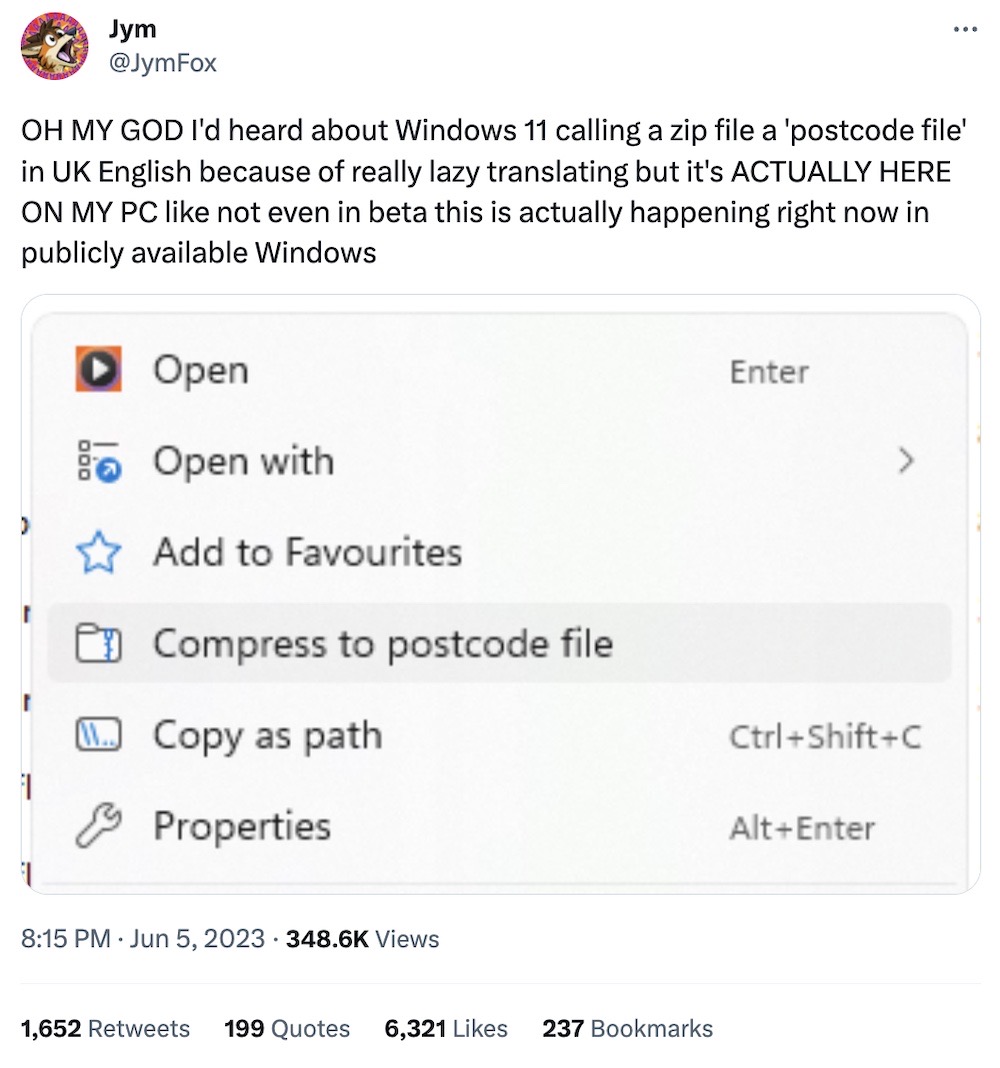
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Pixel, who as you can see is trying to stay hidden from adversaries. Many thanks to his human Manuel for sending in!

Please keep sending in your cyber cats! Send in a photo and their name, and they'll be featured in an upcoming newsletter. (Cyber cats and their non-feline friends are welcome!)
~ ~
~ ~
SUGGESTION BOX
That's it for this week — and next! I will be back in a couple of weeks. Thanks so much for reading and subscribing. If you have any feedback, I'm just an email away.
Take care, and catch you soon,
—@zackwhittaker