this week in security — june 12 edition
THIS WEEK, TL;DR
U.S. ordered travel companies to spy on Russian hacker for years
Forbes ($): Solid reporting from @iblametom by way of a Forbes legal challenge that unsealed documents revealing how U.S. authorities obtained an court order to compel travel data companies — Sabre and Travelport — to continually turn over the travel records of notorious Russian hacker Aleksei Burkov to catch him while he traveled overseas outside of Russia. The feds used an obscure provision in U.S. law called the All Writs Act, which might ring a bell for those who lived through Crypto Wars 2.0 when the FBI tried to force Apple to backdoor its own iPhone software to break into a terrorist's device. Great work here revealing the scope of this kind of underreported surveillance.
More: Input | @iblametom | @fbajak
U.S. warns Chinese hackers are targeting ISPs and telecoms
The Record: Strong warnings from the U.S. government about how Chinese state-sponsored hackers have been targeting internet providers and major telecoms firms around the globe for the past two years by using known vulnerabilities — and what action network defenders can take to protect their organizations. It comes as new research dropped from Sentinel Labs about a new espionage group dubbed Aoqin Dragon, which uses poisoned Word documents to plant a backdoor and get access to the wider network.
More: Bleeping Computer | @martinmatishak
RSA 2022: Cloud providers still using secret middleware
The Register: I didn't need to go to RSA to still get COVID — but for those who braved the in-person event, The Register has your news rundown covered. Among the highlights includes Wiz research that found vulnerabilities in cloud middleware, and a renewed plea from the private sector for government help. Plus, word is getting around about the emerging threat of hacking-for-hire outfits targeting election officials. It's a tactic seen most recently in Poland and Catalonia. And finally — bonus Enigma in the wild.
More: @tonyajoriley tweets | @lilyhnewman
Inside ID.me's torrid pandemic growth spurt: ill-equipped staff and data-security lapses
Insider ($): @caro1inehaskins back with a fresh inside look at ID.me, the digital identity verification company that caused a ruckus when it secured a deal with the IRS. The reporting shows a growth spurt during the pandemic that left the company unprepared to handle the massive influx of new business, which inevitably led to data security lapses. One former employee said: "It was disturbing to me that my background check wasn't completed and that I was allowed to take home a computer with people's information on it." Yikes. And to think this company secured government contracts. ID.me also laid off employees this week after hiring nearly 1,500 new people during the pandemic.
More: Insider ($) | @caro1inehaskins
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
iOS 16 lands with rapid security updates
MacRumors: The next version of iPhone software, iOS 16, comes with several new security features, including rapid security updates that can deliver fixes without having to download a full update. Also included is the new Passkeys feature that big tech giants announced a couple of weeks ago aimed at killing the password for good. Plus, a new safety check feature that can aid those in abusive relationships, which when activated can immediately reset an account and app access for all people at once.
How a saxophonist tricked the KGB by encrypting secrets in music
Wired ($): A brilliant story about how U.S. saxophonist Merryl Goldberg devised an encryption scheme that used musical notation to allow her to smuggle information into and out of the former USSR, defying the watchful eyes of the then-KGB. Another great story that came out of RSA. @kennwhite with the stan tweets.
How to open a locked Sentry Safe in seconds
GitHub / H4ckd4ddy: A security researcher found a vulnerability that allows the opening of electronic safes from the Sentry Safe and Master Lock company without needing a PIN code. Great walkthrough, including a bonus sneaky method of delivery: a highlighter pen.

Android stalkerware exposing images of children
Motherboard: TheTruthSpy, a notorious Android stalkerware app that encourages users to spy on their spouses, is exposing data collected from victims' phones that includes photos of children and babies, and granular location data. Anyone who knows the link to the exposed data can find it, per @josephfcox. TheTruthSpy is one of several near-identical stalkerware apps with the same security flaw.
New Tesla hack gives thieves their own personal key
Ars Technica: An apparent flaw in Tesla's NFC card — used as a way of unlocking an owner's Tesla — has a bug that allows a would-be attacker 130 seconds to enroll a new key and effectively take over the car. "If a vehicle owner normally uses the phone app to unlock the car—by far the most common unlocking method for Teslas — the attacker can force the use of the NFC card by using a signal jammer to block the BLE frequency used by Tesla's phone-as-a-key app."
~ ~
OTHER NEWSY NUGGETS
How electronic warfare is shaping Russia-Ukraine war: Good read from the Associated Press on the use of electronic warfare in the ongoing Ukraine-Russia war, a critical part of Russia's offensive but also used by Ukraine to score some successes — including capturing important intelligence. The U.S. and Britain also supply jamming gear to the Ukrainians, but Russia is warning, per Reuters ($) that the West risks a "direct military clash" after reports of Russian government websites getting hacked over the weekend, in what looks like another threat aimed at tempering Western involvement in its ongoing skirmish against Ukraine.
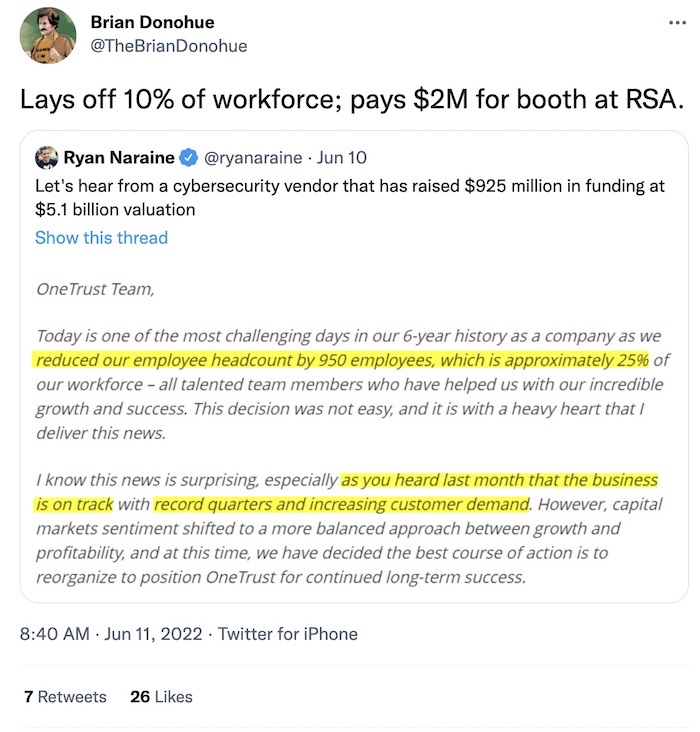
OneTrust has 'record' quarters, still lays off 25% staff: Privacy unicorn OneTrust has been growing from strength to strength — if its statements are to be believed — with "record quarters and increasing customer demand," reports Insider ($). But the Softbank-backed giant is cutting a quarter of its staff, some 950 employees, all the while splashing the cash at RSA. Cybereason also acknowledged layoffs despite a $3 billion valuation.
Feds shutter marketplace selling SSNs: SSNDOB, a series of websites that listed about 24 million Social Security numbers and other personal information, has been seized by U.S. and Cyprus authorities. The crime market netted some $19 million in sales over the past ten years — or more than $22 million in Bitcoin, per Chainalysis. SSNDOB has been active since at least 2013.
Microsoft mum on Follina exploit: Tech giant Microsoft is reportedly in "no hurry" to patch the Follina vulnerability under active attack, which exploits a bug in Office documents that crucially doesn't require macros to work. Simply previewing a document will render a device compromised. The bug is already being exploited to infect devices with the Qbot malware and ransomware. But Microsoft has said very little since it declared the bug a vulnerability — at a 7.8 out of 10 rating — and hasn't said anything about it since.
~ ~
THE HAPPY CORNER
@gregotto delighted us with cybersecurity-themed responses from DALL-E, the artificial intelligence that creates images based on text prompts. And the responses are trippy.
And, new from @BlueSpaceCanary, EmpOS, a theoretical new operating system that makes your devices impervious to malware. Finally, something that's entirely hack-proof.
![Blue Space Canary tweet: "cant get malware if you blast every electronic device near you with a massive [electro-magnetic pulse]"](https://this.weekinsecurity.com/content/images/scraped_images/c2ddbf14-b42a-88f3-64d5-14daf21e4e81.jpg)
To send in good news for the happy corner, please reach out to: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's featured cyber cat is Roby, who is enjoying the sun after a tough day hacking the dry food dispenser. Great work, Roby. Thanks to Bianca R. for sending him in!

Please keep sending in your cyber-cats! You can drop me an email here with their name and photo, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's it for this week. Hope you enjoyed! As always, if you have any feedback, drop it in the suggestion box or send me an email. And do send in your cyber cats — we're low!
See you next week.
—@zackwhittaker