this week in security — june 14 edition
THIS WEEK, TL;DR
Facebook helped the FBI hack a child predator
Motherboard: Bombshell reporting by @lorenzofb this week. California man Buster Hernandez harassed and terrorized girls on Facebook for years, but he was an expert at hiding his identity online. So Facebook paid a cybersecurity firm to build a zero-day exploit for Tails, the privacy-focused operating system, to deanonymize him. Facebook handed the exploit to the feds, which are legally allowed — with a judicial order — to use it. Once unmasked, Hernandez was indicted. But as reported, questions remain. Tails, as you'd imagine, was out of the loop. The bug was eventually patched, without Facebook's help. And it's not known if the FBI reused the hacking tool it purchased, said Democratic senator Ron Wyden.
Background: Motherboard | @kimzetter tweets
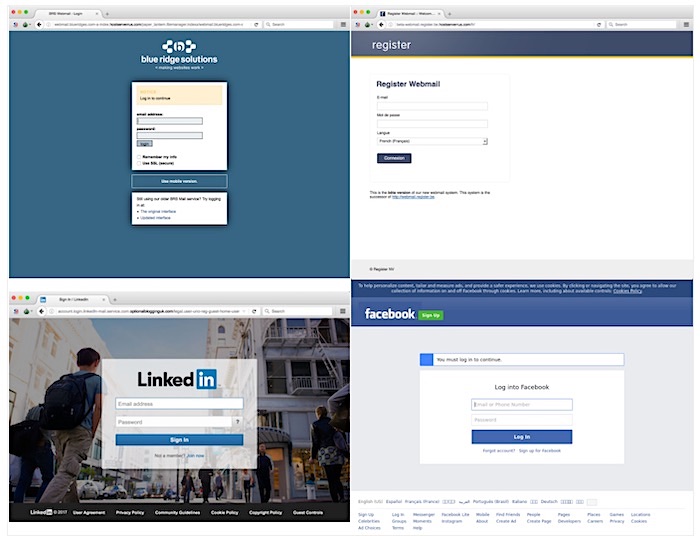
An obscure Indian cyber firm spied on politicians, investors worldwide
Reuters: A little known Indian cyber firm is behind a major hacking-for-hire effort that saw its clients spy on more than 10,000 email accounts over a decade. BellTroX targeted U.S. victims, which has apparently caught the attention of the Justice Dept. One such victim is short seller Muddy Waters, which said it was "disappointed but not surprised" that it was targeted by the hackers for hire. This was incredible reporting all round.@Bing_Chris has a good thread on this story. Citizen Lab was one of the firms that uncovered the hacking operation, dubbed Dark Basin. EFF reported in 2017 that Dark Basin targeted several well-known advocacy groups. Below, you can see some of the phishing sites BellTroX used to ensnare their victims.
More: Citizen Lab | Norton LifeLock | @Bing_Chris
Online voting system used in Florida, Ohio has severe security flaws, say researchers
OneZero ($): It's no surprise that given COVID-19, many are looking for alternative voting systems. Voting-by-mail seems to have the general consensus, even if politics is getting in the way. But that's not stopping the vote-by-internet crowd. Now, MIT researchers have found severe problems with Democracy Live's OmniBallot internet voting system that could result in altered ballots "without detection." As always, @kimzetter's work is well worth the read.
More: MIT | Ars Technica | Politico | New York Times ($)
We mapped where CBP drones are flying in the U.S. and beyond
Gizmodo: CBP drones have been flying over the U.S. for years as part of the agency's border monitoring efforts. But last week Motherboard found that CBP was flying over Minneapolis, where much of the protesters in the wake of George Floyd's death were centered. Lawmakers demanded that the aerial surveillance stop but CBP continues to spy from the sky. Although details about how CBP uses its drones, where, and why, Gizmodo looks at where those drones have been flying in the past year to reveal a bit more about its domestic surveillance.
Background: Motherboard
Senate bill wants DNI to investigate commercial spyware threats
Cyberscoop: Buried in a newly revealed bill, the Senate Intelligence Committee is calling on the U.S.' top spy to investigate commercial spyware threats, like from Hacking Team and NSO Group, which allegedly hacked into a phone of a friend close to murdered journalist Jamal Khashoggi before his death. The committee specifically wants to look at the threat posed to U.S. citizens and federal workers both at home and abroad.
More: TechCrunch | @jsrailton thread
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
ACLU sues Los Angeles over e-scooter tracking
ACLU: Electric scooter rental companies are required to provide real-time and historic GPS tracking data to Los Angeles city officials to make sure that those rental firms are operating legally. But the ACLU says that violates the Fourth Amendment and is suing the California city. The ACLU also says that this presents a data risk in the event that the data gets "in the wrong hands."
Plundering of crypto keys from SGX sends Intel scrambling again
Ars Technica: Another day, another bug found in Intel chips. Researchers found two new vulnerabilities in Intel's software guard extension, known as SGX, allowing them to pluck passwords and encryption keys from the chip's memory with access to the affected computer. Below you can see an image file that was pulled from a chip by exploiting the bug. Intel fixed the bugs, and operating system makers should be rolling out the patches in the coming weeks.

What that Capital One court decision means for corporate cybersecurity
Cyberscoop: After Capital One's massive data breach last year, a court has decided that the company must provide outsiders with an incident report detailing what led to the incident. In other words, it has to make its findings public. Typically these reports are kept hidden — much to the chagrin of researchers and experts, who'd want to know how the company was hacked so they can put in protections at their own organizations. Experts said this could be a game-changing decision.
Babylon Health says its GP app hit by data breach
BBC News: An app maker for doctors, Babylon Health, has admitted a data breach after a "small number" of users gained access to other users' sessions. Babylon allows doctors to remotely speak to patients and issue prescriptions to more than 2.3 million users across the U.K., but one user found footage of another person's appointment.
~ ~
OTHER NEWSY NUGGETS
Google got rich from your data. DuckDuckGo is fighting back
Wired U.K. has a great profile on DuckDuckGo, the privacy-minded search engine. It got a much-needed boost from a European antitrust decision in 2014 that forced Google to offer a broader array of search engines than just its own. In the next few weeks, Android devices will let users pick DuckDuckGo by default. This profile looks back at how DuckDuckGo grew to prominence, and where it looks like it'll go next.
U.K. security company exposed its own leaks database
U.K.-based Keepnet Labs inadvertently exposed a massive database of more than 5 billion previously-leaked records. Keepnet, which published its own statement, said it provides this for its threat intelligence. Making matters worse, Keepnet threatened blogger @gcluley with baseless legal action over an apparent error that it refused to reveal.
Slovak police seize wiretapping devices connected to government network
Authorities in Slovakia arrested four suspects as part of an investigation into how a series of suspicious-looking devices got onto the government's IT network. The devices are said to be used for wiretapping, according to local media. Two of the suspects work at the division overseeing the government's IT network, and a third works for the deputy prime minister's office. The arrests were announced in a Facebook post.
~ ~
THE HAPPY CORNER
A couple of things from the week that might put a smile on your face. Firstly, this thread (found via @josephfcox) is a brilliant example of using OSINT. You won't be disappointed.
And: you can take your son's car keys but you can't stop him driving away.

If you want to nominate some good news from the week, feel free to reach out.
~ ~
THIS WEEK'S CYBER CAT
This week's cyber cat is Balkan. Here he is sitting on the router, sniffing your Wi-Fi. Classic Balkan! A big thanks to his dad Josh Snow for the submission!

Send in your cyber cats! The more the merrier. They are always featured, first come first serve. And if you've sent in before, feel free to send in again! You can email them in here.
~ ~
SUGGESTION BOX
That's it for this week. The suggestion box is always open for feedback, comments, and questions. Hope to see you again next Sunday. Take care, and stay safe.