this week in security — june 15 2025 edition
THIS WEEK, TL;DR
Cyberattack at U.S. grocery distributor UNFI affecting store shelves
TechCrunch: It's been a rough week if you're into, well, food. A cyberattack saw one of the top food distributors in North America, United Natural Foods (UNFI), shut much of the company's operations down last week (which wasn't disclosed until a Monday filing) hampering shipments to local grocery stores and large supermarkets. Whole Foods was one of the bigger retailers hit, in part due to its size and that UNFI is its "primary distributor," telling staff the shelf shortages were due to an "outage" at its distributor. (How quaint!) By Saturday, things were starting to return online, but widespread disruption continues across the U.S. and Canada, per affected customers chatting with me over the past few days. (Disclosure alert: I wrote these stories!) I think we sometimes forget how fragile the supply and logistics industry is. No word yet on UNFI's full recovery, or whether data was stolen in the incident. Expect more updates this week, as (hopefully) store shelves will start to recover as the company begins slowly shipping goods out again, but still may take time.
More: UNFI statement | KARE11 | WTIP | Grocery Dive | NBC News
Paragon spyware confirmed used against journalists
Citizen Lab: An ongoing spyware scandal in Italy continues to unravel... the latest twist is that researchers at Citizen Lab have confirmed two journalists — Fanpage reporter Ciro Pellegrino, and the other is unnamed — were hacked with spyware made by Israeli surveillance vendor Paragon. Citizen Lab said the two were probably hacked by the same customer. But whom? All eyes are on Italy, since a parliamentary report confirmed that some of the people involved in this spyware scandal were spied on, in some cases for 'lawful reasons' (heavy quotes for obvious reasons), but that there was no mention of spying on journalists, like Pellegrino. So, is this a cover up? It's starting to look a little more than suspicious, and now Paragon has pulled its contract with Italy over the scandal. As the excellent @jsrailton told my TechCrunch colleague @lorenzofb that last week Italy was "putting this scandal to bed [but] now they'll have to reckon with new forensic evidence." The ball is in Italy's court. Meanwhile: Apple quietly disclosed this week that it fixed the zero-day bug back in February that was being used to hack the journalists.
More: TechCrunch | Associated Press | TechCrunch | The Guardian | Haaretz ($)
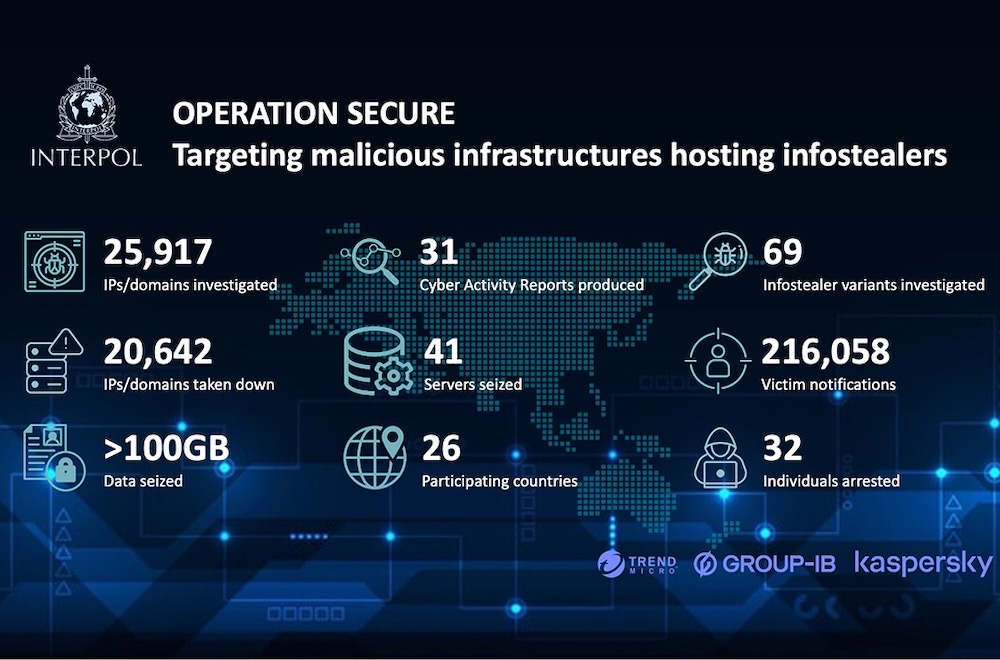
Interpol and police across Asia take down infostealer operations
Interpol: A little amuse-bouche of good news ahead of the happy corner: Interpol released details about a sizable law enforcement operation across Asia that saw more than 20,000 malicious domains used in info-stealing operations taken down over a four-month effort. Password stealers are still a major worldwide security problem; by stealing passwords, attackers can break into systems that aren't protected with MFA. (In some cases infostealers can bypass multi-factor authentication by stealing your logged-in session tokens.) No specific malware groups named (yet) but more than 216,000 victims and potential victims notified with actionable recommendations on what to do next (such as changing passwords, freezing accounts; all the usual jazz). Authorities in Sri Lanka, Nauru, and Hong Kong among others assisted. This is a pretty good result, but still a drop in the ocean to the wider info-stealing economy.
More: The Register | SecurityWeek | CSO
~ ~
THE STUFF YOU MIGHT'VE MISSED
Apple will allow users to transfer passkeys
Ars Technica: At last! (Well, almost.) Apple will soon allow users to import, export and transfer their passkeys across platforms, reducing a significant headache and barrier to using the passwordless tech. The news was revealed at Apple's annual developer conference, WWDC. Also announced: Apps developed for Apple platforms will be able to adopt new security features like pointer authentication, which makes it harder to exploit memory corruption bugs to leak data from your apps. (via @never_released)
Android 16 features Advanced Protection for better security
Android Authority: Google fans aren't left out of this week's mobile security fun-fest. Android 16 devices will land with Advanced Protection (a feature similar to Apple's Lockdown Mode) allowing Android users to lock down their devices further to protect against advanced external threats, like spyware. Interestingly, the feature includes Intrusion Logging, which includes logs for forensic analyses to determine if a device was compromised. That's going to be huge for researchers investigating spyware. (Relatedly, there's a section in Citizen Lab's report on Paragon — mentioned earlier — about the challenges of Android logging.)
Privacy research: Detecting hidden GPS trackers
ResearchGate: Two interesting research papers worth looking at. One study looked at the risks and dangers of hidden cellular-enabled cellular GPS tracking devices on vehicles, and provides an "affordable and practical solution for would-be victims" to detect trackers using relatively cheap hardware. Also: the University of Cambridge dug into the risks associated with commercial menstrual apps, which track periods and fertility cycles and more, given that this data in the wrong hands can be catastrophic for individuals. It's always important to think about where your data is and how it can be accessed (and by whom).
Bug could reveal any phone number linked to a Google account
brutecat: Security researcher brutecat found a way to determine the private recovery phone number of pretty much any Google account, the sort of attack that would be a boon for SIM swappers. The bug involved in part bypassing an anti-bot protection, allowing the brute-forcing of phone numbers. In some cases a number can be determined in a matter of minutes, or faster. Google has fixed the bug. 404 Media ($) has a good write-up. (I also wrote some words!)
Telegram servers controlled by man with links to Russian intelligence
OCCRP: The Organized Crime and Corruption Reporting Project has a deep-dive story about a Russian network engineer called Vladimir Vedeneev, who runs a company that controls thousands of Telegram IP addresses and maintains many of the company's servers, all the while keeping extremely close ties with Russia's intelligence services. This reporting is a good explainer on why you pretty much use Telegram at your own risk, since messages aren't end-to-end encrypted by default. (For more, read up on @pwnallthethings from 2022 on how Russia monitors Telegram using metadata.)
How Waymo handles footage from events like protests
Wired ($): Driverless cars like Waymos (and also those creepy autonomous food delivery robots) are packed with cameras, sensors and other data collectors as they drive around cities transporting folks (or food) from one place to another. All of that collected data, of course, can be accessed by police. Waymo doesn't say much about when it gives over data to cops (even though it does!). All to say, any time you see a Waymo, know that it's also seen you, too.
~ ~
~ ~
OTHER NEWSY NUGGETS
Com kids' crimes carry consequences: At Sleuthcon, the incredible @nixonnixoff spoke about the Com, one of the most pressing cyber and real-world threats of today. These are "not the stereotypical old-school hacker"-types, per Nixon, but are typically teenagers and young adults (aka "advanced persistent teenagers") who use threats and violence to get what they need, including access to networks. It's also probably a consequence of having underfunded education systems that can't (or don't) intervene with kids at a time to harness their skills for good, though some are deemed too far gone. (via Cyberscoop)
Airlines sold your data to DHS: As if you could hate flying any more, but fresh new twist: Some U.S. (and European!) airlines sold your data to U.S. Homeland Security through a data broker, which obfuscated how your personal information, full flight itineraries, and financial details were originally obtained. Lever News and Papers, Please! also looked at this last month. Now, Ron Wyden wants answers from the airlines, so hoo boy, buckle up (pun intended). (via 404 Media ($), Wired ($))
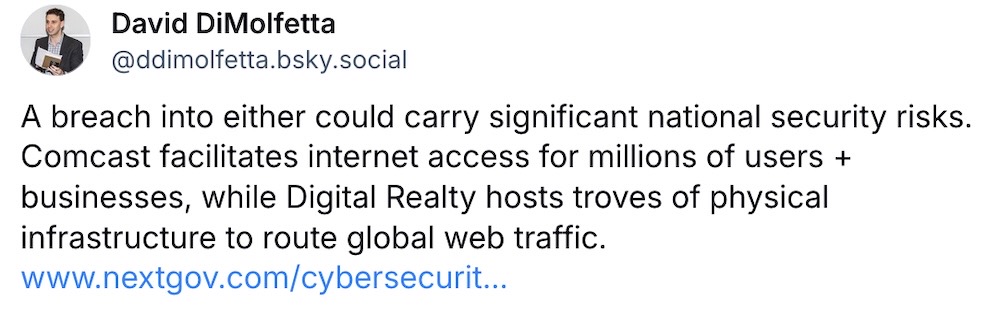
Chinese telco hackers likely hit data centers: Last year, U.S. officials sounded the alarm on a group of Chinese hackers, aka Salt Typhoon, which were embedded in several telecoms across the United States. Now it seems that officials believe the intrusions were potentially broader than first thought and may've had access to data centers, like Digital Realty, which runs 300 colocation data centers used by cloud giants. Comcast was also named as a likely victim. (via Nextgov, @ddimolfetta)
Predator has a new African customer: New data on Predator, developed by the now-sanctioned spyware maker Intellexa, suggests Mozambique has signed on as a government customer. The research also links high-tier Predator infrastructure to a Czech entity. (via Recorded Future)
PowerSchool hack leaves questions unanswered: Veteran security blogger Dissent Doe has a really interesting analysis looking back at the PowerSchool hacks, one of the largest-ever education hacks that unfolded largely this year, affecting at least 60 million students, plus teachers. A 19-year-old student from Massachusetts pleaded guilty to the hack, and will now skip directly to sentencing. But Dissent Doe still has outstanding questions — and reads between the lines with solid analysis of what we still don't know about the hacks and subsequent extortion events. (via DataBreaches.net)
~ ~
THE HAPPY CORNER
There's just a little time left in this busy newsletter this week to dip our feet into the cool shallow waters of the happy corner.
If you ever wondered why loading screens always takes forever, here's why.
Caption contest this electrifying photo. (My favorite reply: "Just not for very long.")
And finally, this week. Icelandic grocery store Netto is reportedly looking for a thief who was caught on camera stealing from their store. I don't know about you, but all I see is a first-time pen-tester really trying their best. I will say, though, the full video (on Facebook) is *chef's kiss* hilarious. (h/t @hildur)

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet Yoshi, this week's cyber cat, once again proving the theory that "if they fit, they sit." What an absolutely glorious photo. Thanks so much to Matt S. for sending in!

Keep sending in your cyber-cats! Drop me an email with a photo and name of your cyber-cat (or non-feline friend!) and they'll be featured in a future newsletter.
~ ~
SUGGESTION BOX
Aaaaannnddd I'm outta here! Thanks so much for reading and making it through this busy week of security news. Let's do this all over again next Sunday. I'll keep a close eye on the UNFI cyberattack aftermath, and we're likely to hear more on "Italian Watergate" (we need a better name, let's be honest; suggestions welcome!).
It's always lovely to hear from you, so if you have anything you want to share for the newsletter — including a cybercat (or a friend) — please get in touch.
And if you really like what you see, tell a friend or coworker about this newsletter or feel free to forward this email on!
Have a wonderful week,
@zackwhittaker