this week in security — june 19 edition
THIS WEEK, TL;DR
L3Harris in talks to take over NSO Group's hacking technology
The Guardian: L3Harris, a major U.S. defense contractor, is apparently in discussions to buy NSO Group's surveillance technology, including the zero-click mobile spyware known as Pegasus, in a deal that's raised eyebrows — and alarm — from civil liberties groups to the White House. NSO's Pegasus has been embroiled in phone hacking of journalists and human rights defenders, which resulted in the U.S. government effectively sanctioning the company, and now the Biden administration thinks the deal raises "serious counterintelligence" concerns for the U.S. government, because of NSO's close relationship with Israel, which the Washington Post ($) explains more. The deal would need the approval of Israel, the U.S. and L3Harris' board. This story was jointly reported by The Guardian, the Washington Post and Haaretz.
More: Washington Post ($) | Haaretz ($) | @skirchy | @jsrailton tweets | @granick tweets
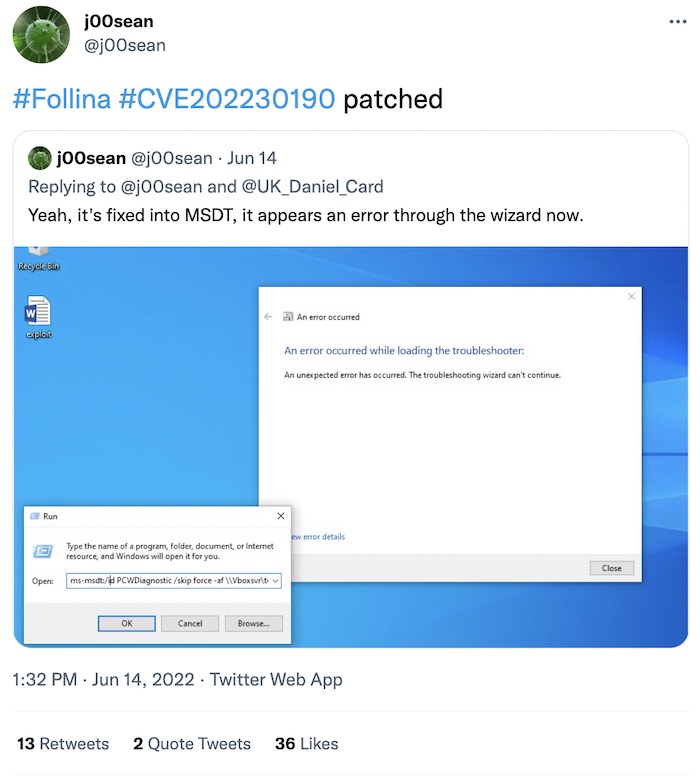
Botched and silent patches from Microsoft put customers at risk, critics say
Ars Technica: Microsoft is facing the heat for what some are saying is a lack of transparency and expeditiousness in responding to security flaws and releasing security patches. Case in point: Orca Security said Microsoft slowly patched — and repeatedly flubbed — a critical flaw that allowed any Azure account the ability to access the resources of other customers for months until it was fixed. On top of that we're seeing effectively silent fixes like Follina, which was finally patched this week. Patch Tuesday details here.
More: Cisco Talos | SecurityWeek | Bleeping Computer
Police linked to hacking campaign to frame Indian activists
Wired ($): Last year it emerged that evidence, which allegedly pointed to a group of Indian activists planning to overthrow the government, was actually planted on a laptop later seized by police. Now @a_greenberg has the story linking the planting of evidence to none other than the very same police agency in Pune that arrested them. Researchers at SentinelOne, plus a combination of sleuthing and using open-source intelligence, pulled in a lot of evidence here. This line will stay with me: "The conclusion that Pune police are tied to a hacking campaign that appears to have framed and jailed human rights activists presents a disturbing new example of the dangers of hacking tools in the hands of law enforcement—even in an ostensible democracy like India." The story is breathtakingly detailed and thorough, but frankly hard to stomach.
Background: Washington Post ($) | More: @a_greenberg tweets
How DOJ took the malware fight into your computer
Politico: Interesting interviews with the FBI's top cyber brass on the decisions made to take action — in some cases effectively legal hacking — against botnets and malware. There've been a few instances of the FBI taking down nefarious operations, like taking down a Russian GRU botnet and removing backdoors from hacked Exchange Servers. Both good outcomes, but the discussion about the government's role in malware removal is an interesting one for sure. A good read.
More: @tonyajoriley
U.S. Marshal charged for using police location tool to track people he knew
Motherboard: The Justice Department this week charged a deputy U.S. Marshal for allegedly abusing access to a location tracking tool provided by Securus, and often used by police and law enforcement. He is accused of improperly accessing the tool between 2016 and 2017 to track people he knew by uploading blank documents that he provided in place of warrants. The tool was discontinued by Securus some years ago.
More: Justice Department | Cyberscoop | @josephfcox tweets
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Attackers exploit Confluence bug to drop ransomware webshells
Decipher: Hardly the headline you want to see, but it's happening right now. Microsoft is seeing the recently disclosed Confluence flaw, tracked as CVE-2022-26134, exploited by a China-backed ransomware actor to drop webshells for further exploitation. Though there are patches out, @0xDUDE says they've seen German companies decline to patch or notify customers who are at risk.
Kaiser Permanente breach led to exposure of 70,000 patient records
TechCrunch: The largest nonprofit health plan provider in the United States, Kaiser Permanente, disclosed a data breach that exposed the sensitive health information of close to 70,000 patients in Washington state. According to the breach notice, someone gained access to a single employee's emails on April 5 that contained patient data, including lab test results.
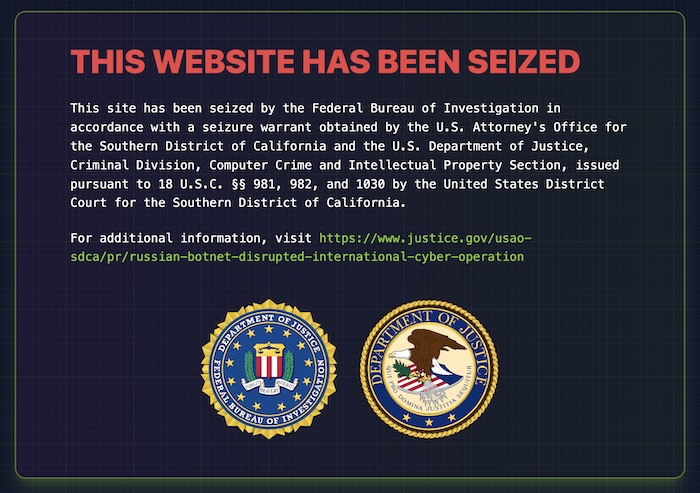
Rsocks web proxy service seized by DOJ for hacking millions of devices
Justice Department: Rsocks, for a time a popular web proxy service that allowed buyers to route their traffic through a range of different IP addresses, was actually a front by Russian cybercriminals, and the 8 million claimed IP addresses that the service used as proxy servers were... actually hacked devices that had been ensnared as part of a giant botnet to hide malicious traffic and activity. Bleeping Computer has a good explainer on the operation and the government's takedown efforts.
What it means that the U.S. is conducting offensive cyber ops against Russia
Zero Day: A fascinating set of interviews by @kimzetter that tries to understand exactly what U.S. Cyber Command chief Gen. Paul Nakasone meant when he told a reporter earlier this month that it had conducted "offensive" (and defensive) operations against Russia. Turns out it's a lot more complicated than it seems (or probably has to be, but that's the military for you). It's a solid read, which you'll undoubtedly learn something from, because it is a bit complicated. Luckily, Zetter (and corresponding Twitter thread) has you covered.
Heroku's April incident review of its supply chain attack
Heroku: The cloud giant this week released a review of its April 2022 incident involving GitHub and Salesforce — which forced the company to reset user passwords in response to a security breach — and, I can save you a read, but it didn't say much new — except, tellingly, that it has "been unable to definitively confirm the third-party integration that was the source of the attack." Well that's not reassuring.
Android spyware used by governments deployed in Kazakhstan
Lookout: Fascinating research out this week by Lookout, looking at a newly discovered mobile spyware — used by governments — to selectively target Android (and iOS) users. The spyware, dubbed Hermit, is modular and impersonates well-known brands, like Oppo and Samsung, and has been found deployed in Italy and Syria. Its most recent connection ties it to victims in Kazakhstan, and said to have been deployed by an agency of the national government, at a time where the nation state cracked down on protesters opposing government policies only a few months ago. More from SecurityWeek, and I wrote some words here too.
~ ~
OTHER NEWSY NUGGETS
A new chip flaw hits Intel, AMD chips: Enter the Hertzbleed flaw, a new side-channel vulnerability that targets power-conservation features on most Intel and AMD chips. Ars Technica has the run-down. In the worst case, the attacks can be used to "extract cryptographic keys from remote servers that were previously believed to be secure," which really isn't great! Neither chipmakers provided security updates. The website (yes, there's a website) has more. But questions remain about how (and why) Intel sat on its own Hertzbleed findings for months without fixing anything, as noted by @matthew_d_green.
Zombie zero-day in the wild: What's a security bug that refuses to die? A zombie bug. That's according to new findings by @maddiestone, whose latest Google Project Zero writeup of a Safari zero-day that was fixed in 2013(!) came back as an exploited-in-the-wild bug in 2022. Details and a proof-of-concept are here.
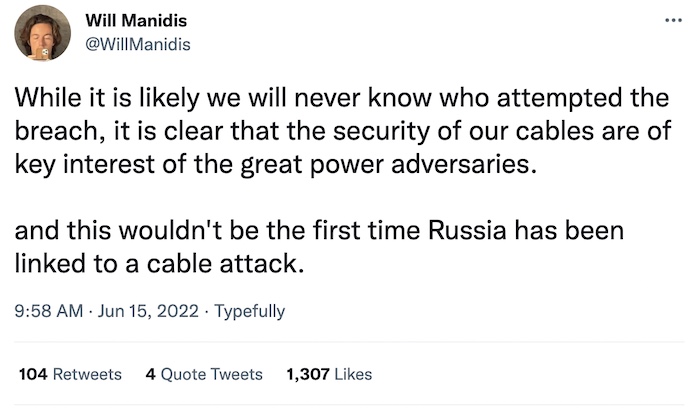
How hackers almost compromised a submarine fiber cable: Interesting tweet thread from @willmanidis about how a team of cyberattackers attempted to breach an undersea cable off the coast of Hawaii. The hackers were stopped and an arrest made (though no details released), but the tweet thread is worth the read. "By comprising these servers [at cable landing sites], they could control or sniff whatever was happening on the line." That's similar, though not identical to what the NSA did with Google and Yahoo datacenters under the MUSCULAR program.
~ ~
THE HAPPY CORNER
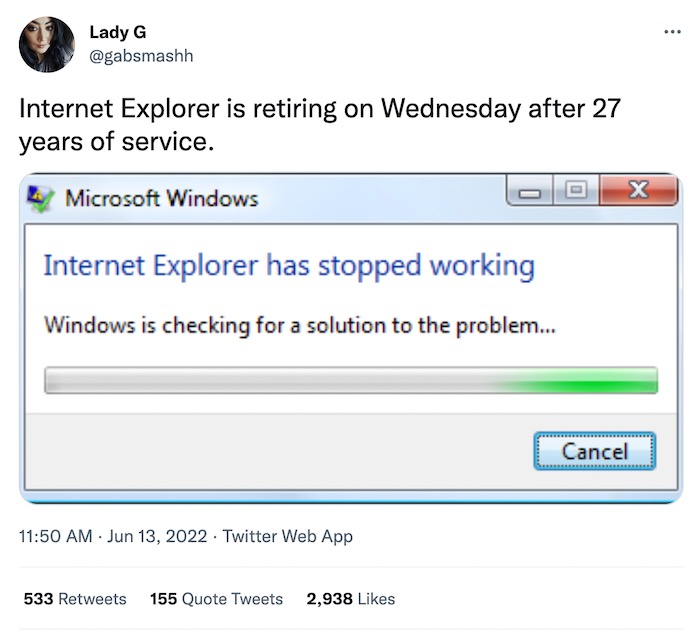
Ding dong, Internet Explorer is dead. And thank the stars for that. Enough of IE already! The long-running internet browser was sunset on June 15 in favor of Edge, which is based on Google Chrome. (Funny how the world turns out...) So long, decades of security bugs... or maybe not, since it's just the browser that's disappearing. Its underlying engine, MSHTML, will be around for some time... 😱
To send in good news for the happy corner, please reach out to: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Morpheus (of The Sandman fame). Who needs the NSA when your cat can wiretap just by sitting on the line? Many thanks to Paul B. for the submission!

Send in your cyber-cats — or their friends! (We're running very low!) You can drop me an email here with their name and photo, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's all for a busy week in security. Hope you'll join me next week, too. As usual, feel free to drop any feedback in the suggestion box or drop me an email.
Be well and be kind,
—@zackwhittaker