this week in security — june 2 2024 edition
THIS WEEK, TL;DR
Live Nation says Ticketmaster was hacked, says data stored by Snowflake
Live Nation: Well that was a week. Let's start with the late Friday breaking news that Live Nation confirmed its Ticketmaster subsidiary was hacked — more than a week after a hacker, known as ShinyHunters, claimed the theft of 560 million customer records. Ticketmaster has said very little, only that personal information (presumably customers) was taken, and, crucially, that the stolen data "was hosted on Snowflake," a cloud storage and analytics company. Snowflake hasn't said much about how Ticketmaster's data left its systems, but confirmed it's notified a "limited number of customers" affected by the security incident, which Snowflake is blaming on its customers. Very murky picture here, but given that Snowflake is used by many companies to store data in the cloud, we could be looking at a much bigger breach than just Ticketmaster. Santander Bank also said it had an unspecified amount of data stolen in a recent breach (though ShinyHunters says it has 30 million records), which some have also linked to Snowflake. It's going to be a watch and wait game.
More: Snowflake | BBC News | ABC News | Wired ($) | 404 Media ($) | DataBreaches.net | @vxunderground
'Largest ever botnet' tied to COVID fraud, CSAM and other crimes
Justice Department: U.S. prosecutors dismantled a botnet called 911 S5 and nabbed its administrator, Yunhe Wang, as part of a global law enforcement effort. The botnet was huge, infecting some 19 million residential IP addresses, to mask the activity of cyber-crims who paid for access to the botnet. Wired breaks down the indictment more; the botnet was linked to a ton of criminal activity, including bomb threats, the distribution child abuse imagery (known as CSAM), and used to create over half a million fraudulent claims that resulted in the attackers netting some $6 billion in COVID-19 relief funds. Wang, along with other co-conspirators, have also been sanctioned, making it far more difficult for them to profit from criminal activity in the future. The FBI has a guide on how to remove the botnet malware (disguised as VPN apps — another reason to avoid 'em).
More: IC3 | BBC News | Krebs on Security | Wired ($)

'Operation Endgame' takes down malware-dropping botnets
Europol: From one cop op to another. Operation Endgame, as it's called, was the FBI and Europol's takedown operation aimed at taking down botnets of hijacked computers that are designed to drop malware (like ransomware), including Pikabot, IcedID and Trickbot (whose previous takedown didn't last long). The operation saw more than 2,000 domains seized and four arrests, one in Armenia and three in Ukraine. The main suspect allegedly made some €69 million in cybercrime proceeds. Since the feds have been playing mind games with the cybercrime crowd for some time, cue its jaunty Operation Endgame micro-site and mini-series.
More: Operation Endgame | Troy Hunt | Associated Press | Ars Technica
Nearly three million affected by Sav-Rx data breach
The Record: Close to three million people had names, addresses, some eligibility data and Social Security numbers stolen in a data breach at Sav-Rx, a company that manages prescription benefits for health plan customers. The company didn't describe the nature of the incident, but claimed that "any data acquired from our IT System was destroyed and not further disseminated" — which sounds a lot like paying off the hackers. Was it ransomware or an extortion event? Sav-Rx won't say (or comment at all by the sounds of it). Yet another healthcare company hacked and still little to no recourse for the millions affected.
More: Bleeping Computer | HealthITSecurity | @brett
~ ~
THE STUFF YOU MIGHT'VE MISSED
Mystery malware knocks out 600,000 Windstream routers
Lumen: A new report by Lumen sheds light on an event, dubbed Pumpkin Eclipse, which saw more than 600,000 routers connected to a single ISP "taken out by an unknown threat actor," or bricked. It's not clear who's behind the attack, but the ISP had to replace customer routers en masse. This kind of router wiping has happened before, but limited to circumstances — like war (think AcidRain, which took out Viasat across much of Europe ahead of Russia's invasion of Ukraine). Lumen's findings match reports from October that linked the incident to an ISP called Windstream. Ars Technica also has a good write-up.
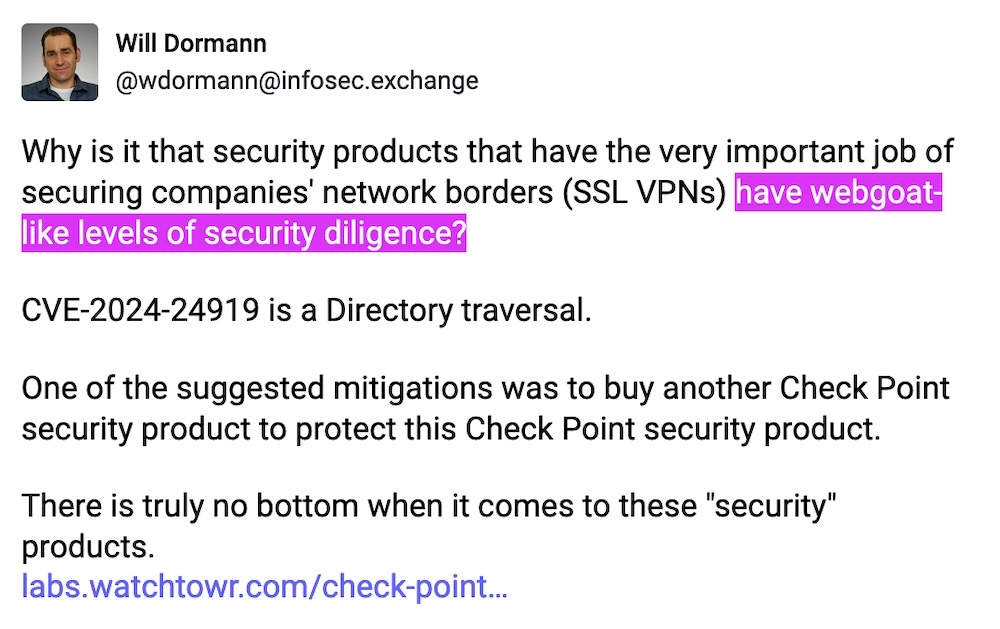
Thousands of Check Point VPN devices vulnerable to zero-day
The Record: Here we go again, another zero-day bug found in a security company's hardware. This time it's Check Point's enterprise VPN product. The bug in Check Point's Quantum devices is "extremely easy" to exploit, per watchTowr Labs. Thousands of affected devices on the internet are vulnerable, but there are patches out. In recent months we've seen major bugs in Ivanti, Palo Alto Networks, Cisco and ConnectWise. As usual, @wdormann says what most are thinking:
The obscure U.S. intelligence bureau that got Vietnam, Iraq, and Ukraine right
Vox: Really interesting story about INR, or the Bureau of Intelligence and Research, a little-known bureau within the State Department, which often dissents from the rest of the intelligence community, and it's almost always right — even when other agencies are wrong. Vox's long-read on the INR is really good.
Inside Microsoft's Recall disaster
DoublePulsar ($): Kevin Beaumont, aka @GossiTheDog, has the blog post to read on Microsoft Recall, the spyware feature (sorry!) that records everything you do on your Windows PC so you (or malware) can search (steal) all of your content. This is a very slow moving disaster waiting to happen. (I Can’t Believe It's Not Security!™) To wit: Microsoft "tried to do a bunch of things but none of it actually works properly in the real world due to gaps you can drive a plane through." Beaumont has an excellent point; Microsoft should recall Recall until Microsoft can make it safe. Right now, it's not.
~ ~
OTHER NEWSY NUGGETS
Bug in password manager cracked a $3M crypto wallet: @KimZetter is back with a belter on how a famed hardware hacker cracked a crypto wallet with $3 million inside... thanks to a bug in a very old version of the RoboForm password manager, no less. Good news for the wallet owner, who got their crypto back. But not-so-great news for any user who used RoboForm to generate passwords prior to the fix in 2015, whose passwords might still be vulnerable. (via Wired ($))
NIST gets vulnerability reporting reinforcements: U.S. standards agency NIST said it's awarded a contract to an "outside vendor" — confirmed to be Analygence — to help NIST organize, review and process incoming security bug reports added to the National Vulnerability Database. The NVD has fallen behind in recent months due to a huge backlog, which NIST has struggled to handle. Hopefully we'll start to see a flood of CVEs disclosed in the next few weeks. (via The Record, Axios)
PACER leaking SSNs: The federal court records system known as PACER has exposed tens of thousands of unredacted Social Security numbers in court filings, according to a new study and as reported by CourtWatch. Most of the exposed SSNs come from district court filings and some 70% of failed redactions "appear to be noncompliant" with privacy rules. (via CourtWatch)
Canada wants to tap the telcos: A new Canadian federal cybersecurity bill, Bill C-26, contains "secretive, encryption-breaking powers" that can be used to secretly order telecoms inside Canada to install backdoors. Canada, a long-standing member of the Five Eyes intelligence alliance, seems to be following in the U.K.'s slippery surveillance footsteps. Citizen Lab, the global security unit at the University of Toronto, warns that the bill seeks to "create more [security] holes, rather than patching them." (via Globe and Mail)
~ ~
THE HAPPY CORNER
And with that done, let's move onto the happy corner. Or, for the reverse-readers, welcome to the newsletter.
The New Yorker ($) has the (satirical) data breach notice that, frankly, we all deserve. "Please know that we take your privacy very seriously. In fact, that seriousness is why you have no idea who we are or why we have your data." Chef's kiss detail, right there.
As we rapidly approach Black Hat and Def Con season, consider donating to WISP's hacker summer camp scholarship fund. WISP's scholarships help provide opportunities to women and underrepresented folks to attend Vegas' top security conferences this year. It's a really great cause and a perfect way to pass down opportunities to an entire new generation of hackers and security pros.
Yours Truly, Johnny Dollar is back with a new comic book investigation, per @uuallan. Dollar, a freelance cyber insurance investigator, is set to track down a ransomware kingpin in the finale of the Johnny Dollar series. If you haven't backed already, check out its Kickstarter.
Speaking of incredible work, if you haven't snagged yourself a copy of @josephcox's book DARK WIRE, this weekend would be a really good time to buy ahead of preorders shipping on June 3. It's one of the best books I've read in years, uncovering the real, inside story of how the FBI ran its own encrypted phone company as the largest criminal wiretap in history. Breathtakingly good reporting and storytelling.
And, lastly this week:

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Poe, who as you can see is surrounded by cable protectors. Consider those cables protected! Many thanks to Zach E for sending in!

Please send in your cyber cats! Drop me a photo of your cyber cat (or non-feline friend!) with their name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
We made it! What a week, and a lot to get through. Thanks for joining me in this busy edition, no doubt there will be a lot more next week to dive into. As always, feel free to get in touch. I love to hear from you — and see your cybercats!
For now, I'm off to have a late breakfast and enjoy some of the nice weather we've been getting on the U.S. east coast. Same time next week?
Take it easy,
@zackwhittaker