this week in security — june 22 2025 edition
THIS WEEK, TL;DR
Iran in internet darkness as conflict escalates, amid fears of cyber spill-over
NBC News: We start this week in Iran, where on Saturday the U.S. bombed three of its top nuclear sites. The politics of the military action notwithstanding, the U.S. is now embroiled in another conflict in the Middle East that has security folks and network defenders around the world on high alert. In the preceding days, Israel attacked Iran with airstrikes and via cyber, with Predatory Sparrow, a pro-Israel hacking group, taking out a major Iranian bank and the country's largest crypto exchange one after the other, wiping out millions from the Iranian economy. The internet there largely collapsed, now confirmed as blocked by the Iranian government. Israel, meanwhile, warned that Iran is hijacking web-connected cameras of Israelis to gather intelligence, per Bloomberg ($), similar to tactics used by Russia following its invasion of Ukraine. To be clear, this is a messy ongoing situation. Iran is a major cyber power and emerging nuclear threat. The effect this conflict will have around the world isn't clear, and critical networks in the U.S. are preparing in the event of Iranian retaliation.
More: Reuters ($) | Wired ($) | TechCrunch | Politico | Associated Press
Scattered Spider attacks now targeting insurance industry
CNN: In other major threat news, one of Google's top security folks is warning the insurance industry to be on guard against Scattered Spider-style attacks, whose tactics involve social engineering and imitating help desks and more (as well as using threats and sometimes violence) to get access to networks. The alert came from @johnhultquist, who says he's losing sleep over the threat from Scattered Spider attacks; these are largely young'uns and adults who are incredibly financially motivated and, frankly, quite dangerous. The insurance industry has most of our collective data, so it's a prime target for these hackers, which can in some cases execute their attacks in a matter of hours, not days. On the back of hitting the retail sector, now several insurance companies of late have been hacked, including Aflac, but it's not clear just yet how linked they are to this latest round of cyberattacks; we may learn more in the coming weeks when data breach disclosures come out. Don't underestimate this threat.
More: Cyberscoop | Bleeping Computer | The Record
Middleman telco could access two-factor codes for the world's tech giants
Lighthouse Reports: Fantastic story here by Lighthouse — also Bloomberg ($) — looking at how a little-known Swiss telco called Fink, which has links to intelligence agencies and the spy industry, was carrying SMS-based two-factor codes for some of the world's biggest companies, including Amazon, Google, and Meta. Of course, the lesson here is SMS 2FA isn't secure as telcos can inherently access these messages. (There have been similar exposures of SMS 2FA codes back in 2018 and 2024.) The main takeaway is to still multi-factor all the things, but if at all possible, use an app-based method or a passkey (or hardware key) if at all possible. As an aside: Some of you may've seen that "16 billion password breach" story this week, which Bleeping Computer debunked and rebalanced things by doing a great job explaining why this matters to you and what you can actually do about it. In cybersecurity, you need news you can use, not just be needlessly alarmed by! @jerry has a good short take on this.
More: Ryan Gallagher (LinkedIn) | @lighthousereports
~ ~
THE STUFF YOU MIGHT'VE MISSED
Alleged shooter found Minnesota lawmakers’ addresses online, per court docs
Politico Pro ($): The alleged shooter behind the killings of two Minnesota Democrats at their homes used "people search" websites to find the names and addresses of his intended targets, per @alng. These sites are fed by data brokers and are entirely legal, because the U.S. doesn't have any privacy rules stopping this (yes, still). Remember: not all data removal offerings are equal (or effective), but good folks like @yaelwrites has a list of sites you can opt-out from.
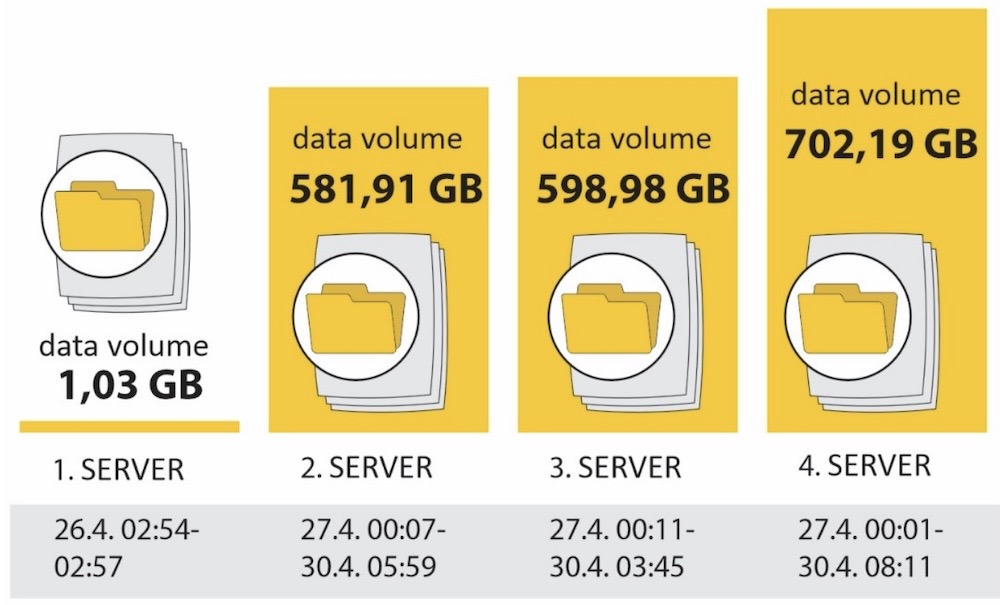
Helsinki's data breach post-mortem identifies security failings
Finland's Safety Investigation Authority: Last year, the city of Helsinki had a data breach affecting thousands of kids, their parents and guardians, and city workers. Now, the country's investigators have published a detailed post-mortem of the cyberattack. The full report is in English (and translated into others!), so CISOs put on a pot of coffee and go read this and take notes. (via @campuscodi)
Websites are tracking you via your browser's fingerprint
Texas A&M University: Interesting research out of Texas examining the privacy risks of browser fingerprinting, a way to use the unique characteristics of your browser, such as screen size, user agent, browser plugins and more, to track you around the web. This kind of tracking has been known for some time, and the EFF has been sounding the alarm on this for years. Using an ad-blocker can help in some cases to block some of the trackers that use browser fingerprinting. Using an ad-blocker is like your crash helmet for the internet. You don't have to think about it, and it'll help to keep you safer online.
When is a good time to fix that vulnerability?
Patrick Mathieu: I enjoyed reading this blog, looking at vulnerability management. Patching your devices and systems just isn't that easy in practice and goes quite far beyond just "patch everything and often." This blog looks at triaging what are the most pressing bugs to fix, and why. Funnily enough, much of this applies in journalism, too: Many vulnerability news stories are designed to scare folks into reading but don't offer much beyond "patch your stuff," and seldom take into account exploitability — which, ideally, should be one of the main things to consider.
Microsoft cut off ICC chief's email, sparking concerns for Europeans
The New York Times ($): Earlier this year, Trump issued sanctions against the International Criminal Court's top prosector, a move that effectively cut off the ICC's chief from the United States — including his Microsoft-hosted work email account. That prompted a huge alarm, allowing the U.S. to unilaterally penalize individuals across the world using sanctions. This is yet another reminder that we are often at the mercy of cloud or tech providers that can cut us off at any moment.
Exposure of forensic phone dumps found online
Martin Seeger: Security researcher @JayeLTee found an exposure of what appears to be forensic phone dumps, which include highly confidential information taken from the phones of suspects. The leak was traced to what is likely the Montana Department of Justice. The general reluctance, it seems, to get the damn thing fixed was arguably just as bad. If you don't have any public means for a security researcher to contact you, you're not doing it right. DataBreaches.net also has more.
~ ~
~ ~
OTHER NEWSY NUGGETS
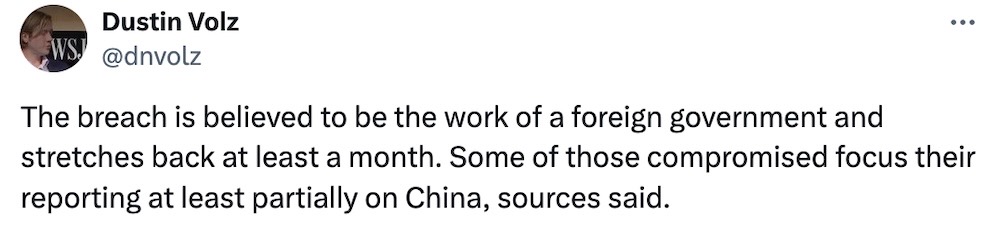
Hackers strike reporters' email accounts: Hackers targeted the email accounts of Washington Post reporters, apparently as part of an effort to gather intelligence to "benefit China's interests." This obviously isn't great, but probably worth a wider question as to how the hackers got in. Since the Washington Post is a Microsoft email shop, and given the Chinese, the Russians (and the Russians again) have broken into Microsoft-hosted email accounts in the past few years, maybe that's where the scrutiny should be. (via Wall Street Journal ($), @dnvolz)
UNFI's week of silence: The cyberattack at UNFI, the main food distributor to Whole Foods and other small grocery stores and large supermarkets alike, is about to enter its third week, and we haven't heard anything new from the company since its brief most recent update on June 15, saying the company was making "significant progress" in its recovery. No filings with the SEC since, either, all the while folks are still reporting food shortages at stores across the United States. (Disclosure alert: I wrote this story!) (via TechCrunch)
New named victim of Salt Typhoon hacks: Remember last year when Chinese spies were running around the networks of U.S. phone and internet giants? Bloomberg now reports that Viasat, the satellite provider (which was also hacked during Russia's invasion of Ukraine) was the latest victim of those Chinese espionage hacks. AT&T, Lumen, and Verizon were named victims of the Chinese espionage campaign, as well as Comcast and datacenter giant Digital Realty named recently. The long-running breach affected more than 100 million records belonging to 1.3 million users — mostly in the Washington DC area. (via Bloomberg ($))
Third time flip-flop on TikTok: I know it's been a while but... remember when TikTok was banned on national security grounds and nothing much ever really came of it? Yes, it's still going, with the Trump administration extending the full-blown ban for a third time for reasons that are frankly unclear. TikTok is a big deal to a lot of folks (and fair, to be honest). But the longer that the U.S. delays this ban, the less officials get to argue about the pressing risk of content manipulation by China. The U.S. can't have it both ways! (via Associated Press)
WhatsApp-a-Mole on Paragon exploits: A nondescript bug in the FreeType open source library discovered in March by the security folks at WhatsApp was being exploited by Paragon-made spyware, the company confirmed this week. If you recall, Paragon's Graphite spyware was also being widely used to spy on journalists and others mostly who have some link to Italy (and beyond). It's the latest in an ongoing Whac-a-Mole situation where WhatsApp keeps outing Paragon's exploits, and Paragon must be getting reeeeeally annoyed. Good! (via SecurityWeek)
San Diego exposed license plate data exposure: The San Diego Police Department uses the surveillance giant Flock for its automated license plate readers. Flock is a network of searchable databases that other U.S. police departments and law enforcement agencies can access. But San Diego's settings were misconfigured and allowed any other agency to query its databases – nearly 13,000 times in just two weeks between 2023 and 2024. Notwithstanding the fact that this was unlawful under California law, it is also a terrible security practice. (via Times of San Diego)
Kicking 23andMe while it's down, U.K. edition: UK's data protection agency the ICO has lobbed a fine of £2.3 million (around $3m) at failed genetics testing firm 23andMe for its massive data breach back in 2023. But even by the ICO's own acknowledgement, it's not clear if the data watchdog will end up collecting since the company filed for bankruptcy earlier this year (though, the company might still be rescued). The ICO's more detailed report [PDF] is worth reading because it's a rundown of the many, many security failings that could have otherwise been an opportunity by 23andMe to identify the breach. (via ICO, BBC News)
~ ~
THE HAPPY CORNER
All aboard the happy bus! Next stop, the happy corner. Ding ding!
Pssst. Hey, kids. Wanna see a bunch of mansion-living cybercriminals get raided by the cops? Yeah you do. According to Thai cops, the crims were running an investment fraud ring that targeted Australians, duping unsuspecting victims out of a couple of million Aussie bucks.

Thanks to @lisaforte, I've had that song stuck in my head for the past few days...
Obviously the next... uh, while... is going to be a busy and likely stressful time in cyber. But these words from @cR0w really stuck with me this morning as I was writing this newsletter. It's not easy staying focused when the world feels like it's on fire. It probably feels very "First Time?" meme for a lot of folks. But remember, we are collectively(!) a great team, and can accomplish great things if we work together. Share something that can help someone else. Share something that can make someone smile. We — each other — are all we have!
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
You know sometimes when the excitement just hits? Well, meet this week's cyber cat pup, Whisky, who clearly cannot contain herself. According to her human, Whisky is incredibly cute and soft, and whose pupper superpower is melting away anyone's ill-will. Get Whisky to the cyber front-lines, stat! Thanks to Kathrin M for sending in!

Keep sending in your cyber-cats! Drop me an email with a photo and name of your cyber-cat (or non-feline friend!) and they'll be featured in a future newsletter.
~ ~
SUGGESTION BOX
On that week, I bid you good day for now and wish you all the best for this week. We're all in this challenging time together, but we can do this — for ourselves and each other. Love is the antidote to hate! I'll continue to keep a close eye on all things cyber and report back next Sunday in my usual dispatch.
As always, feel free to drop me a note if there's anything you want to share for the newsletter. If you have a cyber cat to share, I doubly want to hear from you!
All my best,
@zackwhittaker