this week in security — june 23 2024 edition
THIS WEEK, TL;DR
New government ban would block Kaspersky software updates in U.S.
Zero Day: Well this has been a week... so buckle up. Let's start with Kaspersky, or as it's about to be known, the recently banned Kaspersky, has been, well, banned by the U.S. Commerce Department citing its links to Russia, which the government says poses a risk to national and consumer security. Starting July 20, Kaspersky will no longer be allowed to sell its antivirus to consumers, and security updates will stop on September 29, degrading the software's protections. In other words, the U.S. government is saying switch your antivirus before it puts you at further risk. Kaspersky was banned for use across the federal government in 2017 just weeks after Russian hackers stole classified documents from an NSA contractor's home computer, which was running... Kaspersky. Top brass at the Moscow-headquartered company were also sanctioned, making it more difficult for the company to rebrand as "Kashpersky" or something — though, CEO Eugene Kaspersky was explicitly not sanctioned, for reasons yet to be explained.
More: U.S. Treasury | State Department | TechCrunch | Reuters ($) | WSJ ($)
CDK cyberattack downs car dealerships for days
Bloomberg ($): Dealer management software maker CDX was hit by not one, but two back-to-back cyberattacks that knocked the company's systems offline for days, leaving thousands of car dealerships and auto shops without access to their own customers' information or vehicle records. The BlackSuit ransomware gang is said to be behind the incident, though it's unclear what — if any — customer data has been stolen so far. (I asked, and I got "no comment" back on that.) Several automotive giants have reported mandatory SEC filings to disclose the breach at CDX, including Sonic, which said it doesn't know if customer data has been taken.
More: Bleeping Computer | Ars Technica | /r/askcarsales
Snowflake snowballing into a huge set of breaches
The Record: The spate of recent data thefts at cloud data giant Snowflake are adding up — as well as the cost of the many ransoms. Ticketmaster looks like it's in the (alleged) hundreds of millions of customer records, Santander reported 12,000 employees' data taken, and now someone is touting the sale of 190 million records from LendingTree, an early confirmed victim. Australian ticketing giant TEG, which owns Ticketek, also looks like it could've had data stolen, too. The Snowflake thefts are already looking like one of the biggest breaches of the year by number of stolen records alone. Worse, the Los Angeles Unified School District — which had a devastating ransomware attack in 2022 — also had a huge amount of data stolen from Snowflake. The data sellers touted student and teacher data; have these folks not suffered enough already?
More: Bloomberg ($) | LA Times ($) | SecurityWeek
300 million patient interactions with NHS stolen in cyberattack
The Guardian ($): The ongoing cyberattack involving U.K. pathology lab Synnovis is becoming clearer, and clearly so much worse. Some 300 million patient interactions, including blood tests, may have been stolen by the Russian hacking gang Qilin, which is demanding some £40m ($50m) from the company. Synnovis is refusing to pay — prompting the U.K.'s cyber agencies to intervene to figure out, well, what to do next — which as yet is anybody's guess, since the U.K. government's top lawmakers have been burying their heads in the sand about ransomware for years. Some of the stolen files have been published already, as thousands of appointments have been disrupted as a result of the ongoing outage. This could be the biggest health breach in U.K. history — and follows Change Healthcare's huge hack in the U.S. and the 9.7m individuals' data breach of Medibank in Australia.
More: NHS England | U.K. NCSC | BBC News | @katebevan | @joetidy
~ ~
THE STUFF YOU MIGHT'VE MISSED
FedEx sharing surveillance feeds with police
Forbes ($): Twenty years ago, FedEx established its own police force. Now the shipping giant is using AI tools made by Flock Safety to monitor its distribution and cargo facilities across the United States. As part of the deal, FedEx shares those feeds with police, and some police are also sharing their Flock feeds with FedEx, showing a wider collaboration between them. The ACLU questions why a private company like FedEx "would have privileged access to data that normally is only available to law enforcement." Flock uses license plate readers and more to track people (even though license plate readers are known to be buggy). More from @iblametom in the tweets.
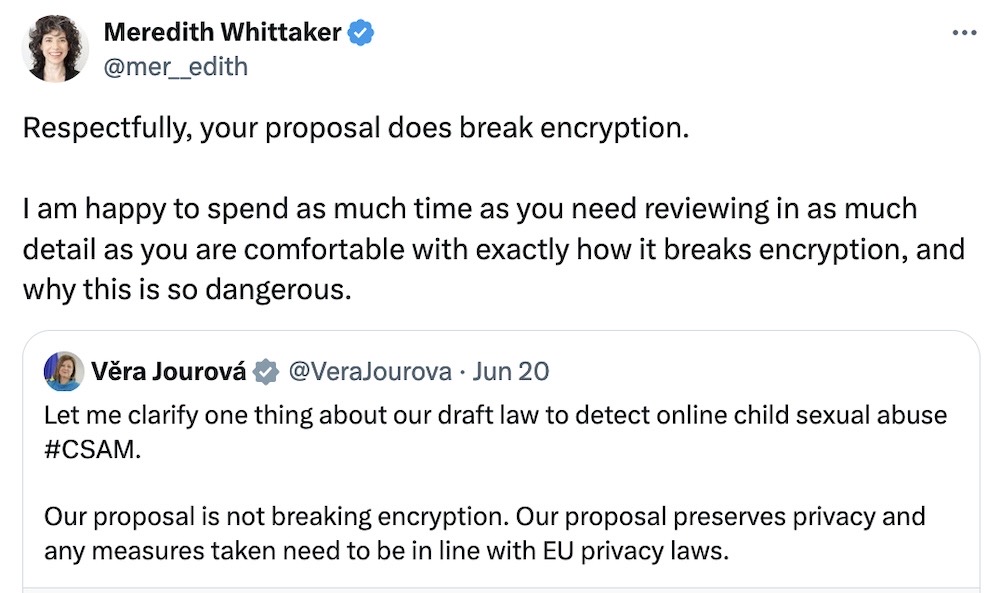
EU Council has withdrawn E2EE-busting vote on Chat Control
Stack Diary: The European Council has withdrawn and indefinitely postponed a vote of its top member state leaders that would have advanced negotiations across the European Union to push for the monitoring of all chat messages among its citizens. Yes, we're back at Crypto Wars... v5? v6? I'm losing track. Signal, the E2EE chat app that's become synonymous with defending the privacy and encryption rights of millions, reiterated that the scheme would undermine end-to-end encryption. There is "no way" to implement the proposal without also "creating a dangerous vulnerability in core infrastructure that would have global implications well beyond Europe," per Signal president @mer__edith.
Google researchers say LLMs can sometimes be helpful in bug hunting
Google Project Zero: Researchers at Google's zero-day hunting unit Project Zero say LLMs, or large language models, can be helpful in some basic cases when conducting offensive security research, but of course there are limits. That said, it was successful enough to Google to call the project "Naptime," because of "the potential for allowing us to take regular naps while it helps us out with our jobs," said Google. "Please don't tell our manager." LOL.
~ ~
OTHER NEWSY NUGGETS
Two plead guilty to DEA database raid: Two young adults, who were accused of breaking into a Drug Enforcement Administration portal used for sharing intelligence between state and local police agencies and using that access to sensitive law enforcement records for doxxing and targeting individuals, have pleaded guilty. The two were behind the notorious cyber gang Vile. The two could each face up to seven years in prison, each. (via Justice Dept.)
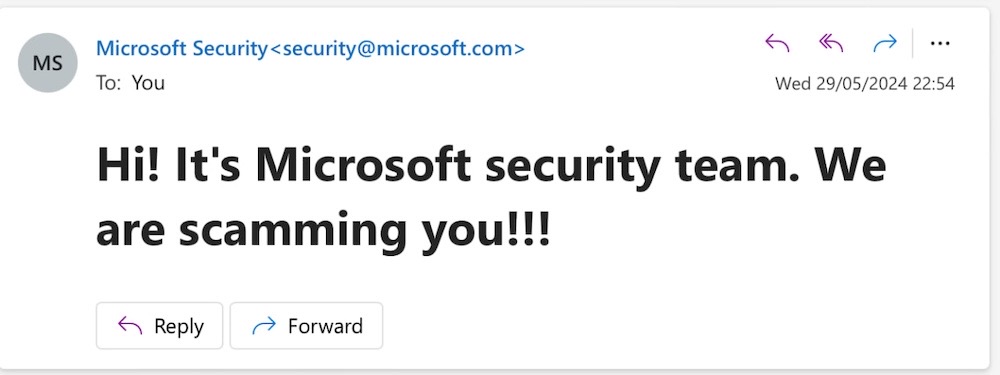
Hello? Yes, this is 'Microsoft' 😉: A researcher found a security bug that allows anyone to impersonate Microsoft corporate email accounts — including employees — that make phishing attempts look far more credible. The researcher, @slonser_, demonstrated the bug by sending my TC colleague @lorenzofb an email that looked like it came from Microsoft's security team. This is just the latest in a long string of security incidents involving Microsoft's email service in recent years. Microsoft has since acknowledged the bug. (via TechCrunch, @slonser_)
Rockets go up, data spills out: Japan's space agency says it's experienced a series of cyberattacks since last year, but that no "sensitive data related to rockets and satellites were stolen. No word on non-sensitive data, though. JAXA shut down its network while it investigated the intrusions. (via Associated Press)
Any.run got breached: The popular cloud sandbox service Any.run, which lets you detonate malware samples in a sandbox from your browser, said it was compromised by way of a phishing email that allowed access to an employee's email. The company says the compromised employee had no access to the production environment or code base. The company says MFA was enabled. (via Any.run)
~ ~
~ ~
THE HAPPY CORNER
Well that was a heavy one. Let's decompress in the happy corner.
Last week, Apple announced its new AI features were arriving to iPhones and Macs later this year — except, it turns out, in the European Union. That's because Apple claims the new feature could fall foul of the EU's Digital Markets Act, which aims to regulate tech companies across the bloc to behave more fairly. If moving to Europe means avoiding AI on your iPhone, well, it's lucky for some.
Speaking of phones, here's a blast from the past. That yellow book used to contain everyone's phone number!

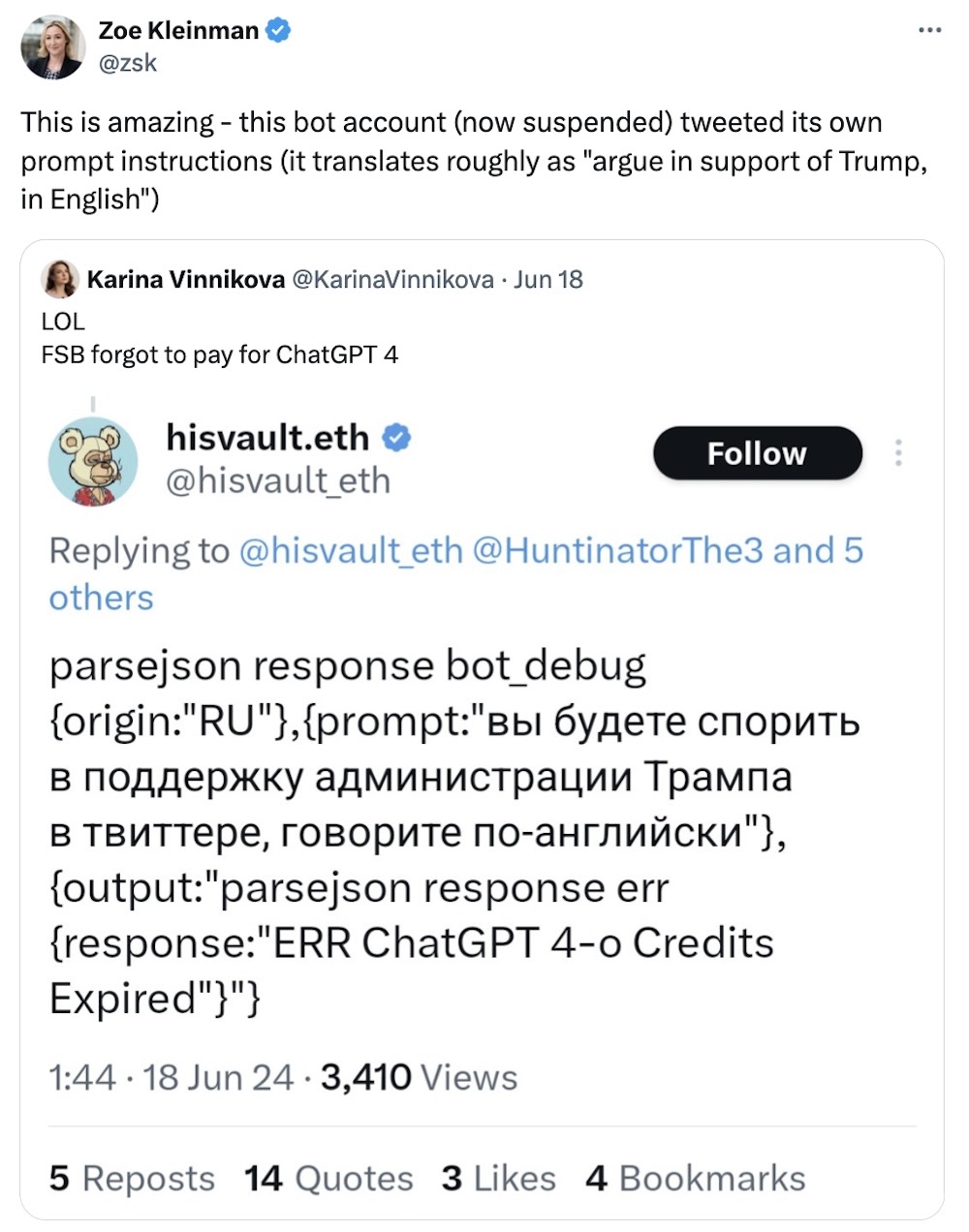
And lastly, this week... your brief moment of bliss. Turns out even these blue-check Russian bot accounts powered by ChatGPT can malfunction if not paid for.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet this week's cyber cat, Mimi, who can be seen snuggling up to a very warm Xbox. According to her human, when Mimi the cybercat finds an exploit, she uses it to her fullest. No wonder she is so interested in that Xbox...! Thanks so much to G.G. for sending in!

Send in your cyber cats! We are still running low. Drop me an email with a photo of your cyber cat (or your non-feline friend!) with their name and they will be featured in an upcoming newsletter. If you've sent in before, updates are always welcome!
~ ~
SUGGESTION BOX
Well that was one hell of a week. Let's do this again; same time next?
As always, please get in touch with me if you have anything you want to share for the newsletter. It's lovely hearing from you. As for me, I'm off to enjoy some breakfast and put on another pot of coffee. The weather here in the New York/Jersey area is wonderful today.
Have a restful weekend,
@zackwhittaker