this week in security — june 25 edition
THIS WEEK, TL;DR
Apple fixes iPhone software flaws used in widespread hacks of Russians
Washington Post ($): Apple has fixed two zero-day vulnerabilities that were used to hack thousands of devices in Russia, according to Kaspersky. The Russian government blamed the NSA for exploiting the flaw (with no evidence), and the NSA has said nothing back, and Apple says it doesn't backdoor its products (which we all assume after that incident but thanks for flagging anyway, I guess?) The flaws were used to plant the so-called Triangulation spyware discovered on iPhones of Kaspersky employees, but the malware couldn't survive a device reboot, even if it could pull location data and extract passwords from a device in the meantime. CISA, for its part, told device owners to update ASAP. Apple also sent another batch of threat alerts to spyware victims, but it's unclear if these are related. The chances of being targeted by spyware is slim, but shows the cat-and-mouse game between spyware makers (whoever they are) and device makers rumble on.
More: Apple | SecureList | BBC News | CISA
Microsoft says early June disruptions to Outlook, cloud platform, were cyberattacks
Associated Press: Microsoft's cloud outages in June were the result of several distributed denial-of-service (DDoS) attacks where junk network traffic floods a server or networks. Not by any means sophisticated (usually) but Microsoft eventually admitted the incidents in a blog post after ignoring the press for several days. OneDrive and Outlook were affected, reports the AP, and other cloud services. Normally a DDoS incident wouldn't raise much of an eyebrow, but Microsoft's... not-so-great handling of this non-non-incident left some wondering if the tech giant is able to withstand floods of traffic from Russian-linked hacktivist groups. @malwarejake said that Microsoft's apparent unwillingness to provide an objective measure of customer impact "probably speaks to the magnitude." Good work by @GossiTheDog on getting this out there.
More: Microsoft | Bleeping Computer | The Register

More victims come forward after MOVEit mass-hack
Reuters ($): Progress Software, the maker of the MOVEit file transfer tool that was targeted in a mass-hack and dozens of its customers had data raided by hackers, continues to scramble as millions more victims come to light. @KatrinaManson has a run-down of the latest not-quite-flaw, while Reuters ($) reports that the biggest U.S. pension fund Calpers and insurer Genworth Financial were both hit, saying personal data of members was taken. The Clop ransomware gang took credit for this latest round of mass-hacks (since Clop was also responsible for Accellion and Fortra hacks). We're now looking at about 100 victims, give or take — that includes NYC schools, which had data breached only last year after Illuminate Education was hacked.
More: Gothamist | Bloomberg ($) | @BrettCallow
A year after Dobbs, federal privacy legislation to protect abortion seekers remains stalled
Cyberscoop: A year ago, the U.S. Supreme Court ended the national right to abortion. Since, little has moved in terms of federal legislation aimed at protecting abortion seekers (and others), despite some executive action. States have taken some of the burden, but little federal privacy rules exist for anyone, or anything. Tech Policy Press also looks at where the U.S. is right now, and it's not good — data brokers are still selling vast amounts of data on Americans and there's nothing we can really do about it. ("The need for comprehensive legislation that meaningfully protects all Americans has never been more palpable.") Meanwhile, Wired ($) looks at the gray-market abortion pill market that's growing on encrypted messaging apps like Telegram.
More: @glichfield | @justinhendrix
~ ~
THE STUFF YOU MIGHT'VE MISSED
Voatz website hacked by truth-speaking hacktivists
Kevin Collier: Things aren't going so well for Voatz, the controversial blockchain voting company that's fallen out of favor with states and election officials, which this week had its site hacked, per @kevincollier, who has followed the company for years. @jhalderm and @SEGreenhalgh have screenshots in case you missed it. As @tarah noted, "If Voatz can’t secure their website, they have no business saying they can secure your vote." Preach.
Why malware crypting services deserve more scrutiny
Krebs on Security: They say you can't achieve security through obscurity, but malware developers are relying on that exact principle by using malware crypting services — that is, sites and services offering to scramble the malware's code to make it look less-suspicious (or not flagged at all). A lot of malware authors pay someone else for it. It's these services that should get researchers' attention, Krebs says, since it could help garner fresh intelligence about new malware. Food for thought!
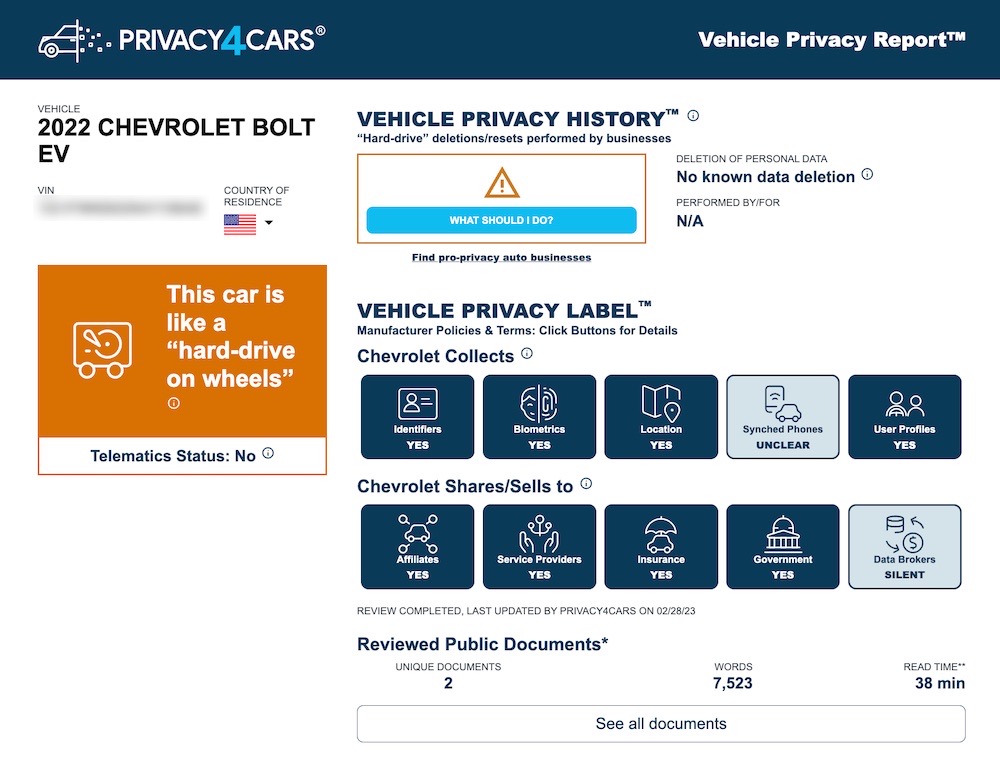
How your new car tracks you
Wired ($): If you have a Toyota, Honda, or Ford vehicle, they can (and do!) collect huge volumes of data about you as you drive, including your location down to "acceleration and speed, steering, and braking functionality, and travel direction." Police can tap into this data — appropriately known as cartapping (and Forbes, separately, has covered this extensively over the years). In some cases, cars can collect 25 gigabytes of vehicle data an hour. Although some of the data isn't used nefariously, it's alarming how much data can and is collected. The Vehicle Privacy Report lets you look at just how privacy-conscious your vehicle is (or isn't).
EU capitals want media law exception to spy on reporters
Politico: They say a free press is good for a healthy democracy. The trouble is that EU state leaders representing their countries at the European Council instead want a free pass to spy on the press. The idea is that EU authorities would be allowed to deploy spyware on a reporter's phone (such as to uncover sources) that's "justified by an overriding requirement in the public interest."(!!) The Guardian has more on the proposal, which still has a way to go — including facing the European Parliament, which overwhelmingly voted (albeit non-binding) in favor of curbing the use of spyware on the continent.
A timeline of top U.S. government data breaches
Metacurity ($): Cynthia Brumfield has a post looking at the last three decades worth of U.S. government data breaches, including who was to blame. It's a fascinating look back at the threat actors involved. (By the way, I'm a huge fan of Cynthia's newsletter, you should definitely sign-up if you haven't already.)
~ ~
OTHER NEWSY NUGGETS
FBI may soon need a warrant for spy database searches: Lawmakers are weighing a plan to compel the FBI to first obtain a warrant before it can access data on Americans in its huge foreign spy database of data collected under Section 702 of FISA. That'd be a huge change to the current rules, since this data can be searched without a warrant. There's been a huge appetite to change the law given the FBI's long-running abuse of the database, including to spy on protesters. The Biden administration says the new rule would stifle intel operations, though so much of what the U.S. has said, though, has been without evidence (as is the nature of intelligence — "sorry, we can't share that with you."). Or — here me out! — it would make the FBI's unsanctioned searches of Americans' data more difficult without a warrant. Sorry, FBI, but if you abuse the tools, you get them taken away. (via Wall Street Journal ($))
Hackers threaten to leak 80GB of data stolen from Reddit: The BlackCat ransomware gang (aka ALPHV) claimed responsibility for the theft of 80GB of confidential data stolen from Reddit earlier this year. Reddit disclosed the incident at the time. Now, BlackCat said it'll publish the stolen data unless Reddit pays $4.5M and for Reddit to withdraw its controversial API pricing changes, which caused uproar and protests in Reddit's communities. (via TechCrunch)
Global Entry revoked? You could be under investigation: If you ever wondered why your Global Entry got revoked (you'll get an email telling you), it could be that you're under criminal investigation. Global Entry is a U.S. government vetting program for pre-approving travelers upon arrival to the U.S., to save you the faff of waiting in line. (via @CurtBarnard)
This isn't how you do data breach notifications, UPS: Shipping giant UPS confirmed a data breach after it exposed customer information as part of a SMS phishing campaign. Read the letter carefully, because it's only in the fourth paragraph that you'll realize this isn't some fluffy advisory — your data was actually compromised. UPS said the SMS phishing attacks happened between February 2022 and April 2023. (via Bleeping Computer, @BrettCallow)
That shiny new smart watch is spying on you: The U.S. Naval Criminal Investigative Service is investigating after several servicemembers across the U.S. reported receiving smartwatches in the mail. It's not clear who's sending the smartwatches, but the Army warned in a public advisory this month that it was aware that these smartwatches have auto-connected to Wi-Fi and tried to access user data. Definitely suss. (via CNN)
Cops would rather drop serious crimes than dox stingray docs: Newly released documents show that the FBI requires non-disclosure agreements with cops who use the controversial cell phone location tracking tools, known as stingrays, before they can be used to track suspects. Those NDAs include stipulations that include the withholding of information, such as how they work and even their deployment, from defendants and their lawyers. ACLU lawyers said the secrecy requirements interfere with a defendant's ability to challenge cases in court. "We deserve to know when the government is using invasive surveillance technologies that sweep up information about suspects and bystanders alike," they said. (via Wired ($))
2020 Twitter hacker sentenced to five years: Joseph James O’Connor, 24, one of the hackers behind the 2020 Twitter breach that hijacked high-profile accounts to spread a cryptocurrency scam, was sentenced to five years in U.S. federal prison. (Disclosure: I wrote this story). Prosecutors asked for seven years, while O'Connor — who apologized for his crimes after pleading guilty — asked to be released. More on the tick-tock of sentencing here. (via TechCrunch, Inner City Press)
~ ~
THE HAPPY CORNER
Welcome back to the happy corner. I'm back after a couple of weeks away and a long-needed vacation. I almost missed my flight out of London to bring you this snap of an unlocked Windows-running airport gate that ran out of memory. Follow the thread for some more in-the-wild display snafus.
Oh look, a rare admin/admin out in the wild.
And, this week take a trip down memory lane and read up on Evi Nemeth, widely regarded as one of the sharpest and most knowledgeable Unix sysadmins in modern computing. Nemeth went missing at sea 10 years ago, but her legacy lives on. Thanks for tooting, @fuzzykb.
Plus — oh, why not — extra cyber cats, aka kitty hash collision.
For new Patreon subscribers: The latest batch of stickers and mugs will go out this week!
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Styx, who can be seen on active threat detection duty. Good job keeping both eyes on the prize. Thanks to Paig C.O. for sending in!

We're running low on cyber cats! Send in a photo and their name, and they'll be featured in an upcoming newsletter. (Cyber cats and their non-feline friends are welcome!)
~ ~
SUGGESTION BOX
And that's it for now! Cheers for reading this week. For those who are out celebrating today, have a wonderful Pride. 🏳️🌈
As always, if you have any newsletter feedback, I'm just an email away. Catch you next week?
Have a good one,
—@zackwhittaker