this week in security — june 26 edition
THIS WEEK, TL;DR
U.S. abortion ruling reversal sparks calls for privacy laws
Cyberscoop: This week saw the U.S. Supreme Court overturn Roe v. Wade, ending guarantees that protect a person's constitutional right to have an abortion. The ramifications are huge — economically, socially, medically, and in terms of human rights alone — for over a hundred million people living in the United States. That's made the need for a privacy law more urgent; the U.S. is left far behind most other Western democracies, since there are reasonable fears that data — including from period trackers — can be now used as evidence against people. Tech companies have been left scrambling to figure out what the overturning of Wade means for their employees, which matters because in the U.S. healthcare is tied (inexplicably) to employment, though much of Big Tech has remained largely silent about the ruling itself (even Apple, which says "Privacy is a fundamental human right," has said nothing.) And now there's renewed focus on what data tech companies collect, especially in light of @motherboard's reporting into the sale of location data that can identify people seeking abortions. As EFF's director of cybersecurity @evacide notes, if companies don't want their data turned into dragnets, "Don’t have it for sale. Don’t have it when a subpoena arrives."
More: NPR | The Register | @motherboard | @kevincollier | @TonyaJoRiley
Russian hackers targeting U.S. and other Ukraine allies
Politico, Microsoft: A report by Microsoft out this week revealed Russian state-backed hackers have attempted to infiltrate networks of more than 100 organizations in the U.S. and 42 other countries allied with Ukraine since Russia invaded in February. The list of targets includes foreign ministries of NATO states but also think tanks, IT groups and energy suppliers. Worse, the hackers successfully broke in about 30% of the time, with data stolen in one-in-four successful intrusions. Estonia was an exception — Microsoft detected "no Russian cyber intrusions" since the start of the war, largely because of its heavy reliance on cloud computing.
More: Microsoft | CNN | Associated Press
Twitter apologizes for abusing user security information after $150M FTC settlement
The Record: If you saw a notice on Twitter this week about Twitter's "use of your personal information for tailored advertising," it's thanks to an FTC settlement to the tune of $150 million, after Twitter was caught using information submitted by users for setting up two-factor authentication — email addresses and phone numbers — for targeted advertising. Twitter ceased the practice, and this week apologized in a blog post.
Background: FTC | Washington Post ($) | More: Twitter | @zackwhittaker
Google warns Hermit spyware is targeting iOS and Android users
Wired ($): An update on the recently discovered commercial-grade spyware by researchers at Lookout, dubbed Hermit, which I mentioned last week. Google has now confirmed Lookout's findings — which were largely focused on Android. Google has also found an iOS version of the spyware, which packs in six exploits, including two zero-days. Google said that it's notifying Android users who were targeted by the Hermit spyware, which is believed to be used by governments, and has been deployed in Kazakhstan and Italy. It's a reminder that NSO isn't the only spyware maker out there. Google said it's tracking at least 30 vendors with "varying levels of sophistication and public exposure selling exploits or surveillance capabilities to government-backed actors."
More: Google Project Zero | Google TAG
Mega says it can’t decrypt your files, a new exploit shows otherwise
Ars Technica: Mega has long been billed as an end-to-end encrypted cloud storage provider, which claims that it can't decrypt the data that it stores. But a new proof-of-concept exploit shows that claim isn't exactly true. According to new research, "Mega uses to encrypt files is riddled with fundamental cryptography flaws that make it trivial for anyone with control of the platform to perform a full key recovery attack on users once they have logged in a sufficient number of times." Mega says it's fixed the security vulnerabilities.
More: Mega-Awry | Mega | @tqbf tweets | @kennyog tweets
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Researcher hacks into backend for network of smart Jacuzzis
Eaton Zveare: A security researcher found a network of thousands of smart Jacuzzis connected to the internet via an admin panel that was leaking user data, albeit briefly, including owner's names and email addresses. A second admin panel was also discovered after a teardown of the Android app. It took the Jacuzzi-maker more than six months to fix. Gizmodo has more, and some choice words from @dcuthbert on Jacuzzi's poor response.
Pegasus used by at least five EU countries, NSO Group tells lawmakers
Politico: A memorable hearing in the European Parliament this week after NSO admitted that five EU countries use the notorious NSO spyware Pegasus — including Poland, Spain, and Hungary — with one country having their agreement terminated following abuse, though NSO wouldn't say which state. But that's about as much as NSO did say during the hours-long hearing, and was roundly criticized by lawmakers for rampant contradictions and for seemingly using made-up scores used to rank governments' human rights records. Dutch MEP and privacy buff @SophieintVeld said NSO's responses were "an insult to our intelligence."
Strava app flaw revealed runs of Israeli officials at secret bases
BBC News: A security flaw in the fitness app Strava allowed a disinformation watchdog to identify and track security personnel working at secretive bases in Israel. By uploading fake running "segments," a user could learn the identities and past routes of others who were active in that particular area, even with the strongest privacy protections on their accounts. Case in point, some 100 individuals who exercised at six secretive Israeli bases were visible. Haaretz ($) has the original report. These latest findings come years after similar security research found that Strava's heatmaps could identify secret bases and sensitive military installations.
~ ~
OTHER NEWSY NUGGETS
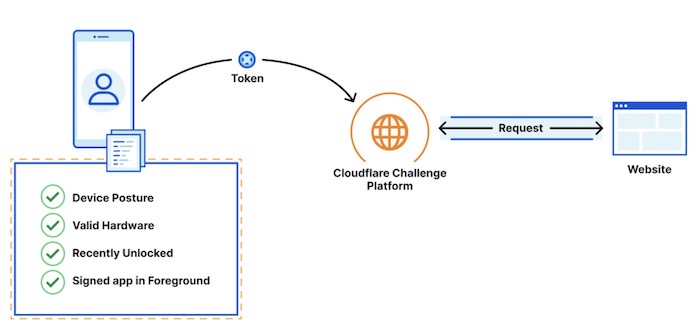
Are you a bot? Not with a PAT: A new feature in iOS 16 and macOS Ventura (out later this year) will allow Apple device owners to bypass CAPTCHAs by automatically telling apps and websites that you're not a bot. Apple is partnering with two content delivery networks, Fastly and Cloudflare. The feature uses private access tokens — or PATs — which automatically work with any app or website that's on Fastly and Cloudflare's network — which is a lot of them. PATs are cross-platform, as Google, Apple, Cloudflare and Fastly all have contributed to developing this protocol. But so far, no love for Android users. Fastly's blog post is here.
Delivery firm Yodel quiet over cyberattack: Yodel, one of the U.K.'s most widely used parcel delivery services, has been down for days, reports Bleeping Computer, after a reported "cyber incident." No word from the company yet — ironic, for a company with that name — but later published a brief statement warning that its order tracking is unavailable and parcels "may arrive later than expected." Not a good look for a company critical to the U.K. supply chain.
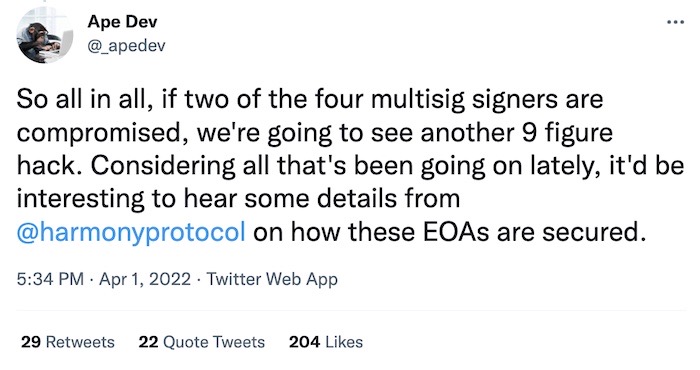
$100M looted after crypto weak-link exploited: An unknown hacker has exploited a vulnerability in U.S. crypto firm Harmony's Horizon Bridge to steal $100 million in Ethereum. Crypto bridges allow users to send cryptocurrency and assets from one blockchain to the other, but are a weak link since they are rarely audited and often built in secrecy. Harmony identified the alleged hacker in a tweet. But Harmony hasn't said exactly how the breach happened. But one investor warned of a potentially massive security flaw weeks earlier, identifying how the Horizon bridge hinged on a multi-signature wallet, which requires just two signatures to take the goods inside. In short, crypto startups need to be more transparent about how technology is built and who audits it.
~ ~
THE HAPPY CORNER
Extra goods for the happy corner this week.
If you ever wondered why Cloudflare has a room full of lava lamps, head over to @mrjasonchoi's Twitter account, who got a rare photo of Cloudflare's so-called Lavarand. The wall is used for generating pseudo-random numbers (used for cryptography and security) by taking photos of the lamps. Cloudflare also has a post about how it works.

Next: experts in CISA's advisory committee are proposing a new 311-style hotline to "provide an emergency call line and clinics for assistance following cyber incidents for small and medium businesses." That's a great idea, especially since CISA (and, well, everyone else) is calling for better incident reporting. The more that's known, the more than can be done — so goes the theory. CISA will respond to the recommendation by September 13, per The Record.
More good news: The U.S. intelligence community will soon be permitted to hire candidates who have used marijuana in the past, reports the Wall Street Journal ($). Weed is still a federally banned substance in the U.S. (even though it's legal in many states), making it tougher for federal recruiters to hire spies and hackers (and to obtain security clearance) — even though those same restrictions seldom apply in the private sector. The move was approved unanimously by the Senate Intelligence Committee, and is set to be proposed in an upcoming intelligence reauthorization bill, which "must pass" every year. Let's hope it makes it through.
And, finally. Spare a thought for one Japanese worker, who was left with one hell of an almighty hangover after losing a USB stick with his entire city's personal details — some 46,000 residents — while he was out on the razz, "before eventually passing out on the the street," reports the BBC. Luckily, the data was encrypted — and, in the end, the drive was found the next day. Phew. Imagine trying to explain that one.
To send in good news for the happy corner, please reach out to: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's cyber cat dog is Snickers, who I am reliably informed is a Dachshund-Yorkie, or a dorkie. (I'm fairly sure that just means Snickers is a lot smarter than the rest of us, which, fair.) A big thanks to Erik J. for the submission!

Please do send in your cyber-cats or their friends. Drop me an email here with their name and photo, and they'll be featured in the newsletter. Repeat submissions are welcome!
~ ~
SUGGESTION BOX
That's it for now, hope you enjoyed this week's newsletter. As always, feel free to drop any feedback in the suggestion box or send me an email. And don't forget to send in your cyber cats, the stars of the show every week!
Back next week,
—@zackwhittaker