this week in security — june 29 2025 edition
THIS WEEK, TL;DR
FBI, cyber firms say Scattered Spider is now targeting airlines
CNN: We start this edition with a warning for the airline industry, after the FBI and cybersecurity firms Mandiant and Palo Alto sounded the alarm on Scattered Spider cyberattacks targeting aviation and the transportation sector. The collective of mostly English-speaking teenagers and young adults are highly financially motivated, and synonymous with their tactics of breaking into networks by any means, such as multi-factor bombing, deceiving help desks, and in sometimes even using threats of violence. The feds said "anyone" in the airline industry could be at risk, from vendors to contractors, which makes sense given airlines are by nature an enormous attack surface. This comes as the hackers moved on from U.K. retail to the insurance industry of late. Given that at least two airlines were hacked this month, Hawaiian and WestJet (with the latter linked to Scattered Spider, per media reports), we can probably expect to see more hacks, or previously unreported hacks disclosed.
More: Cyberscoop | Wall Street Journal ($) | Axios | Bleeping Computer | Charles Carmakal (LinkedIn) | @fbi
U.K. man charged with hacking spree; France arrest 'ShinyHunters'
DataBreaches.net: The feds scored a sizable win this week by nabbing a top hacker and administrator of the notorious BreachForums, a former hacking forum known for sharing breaches and selling stolen data sets until the feds seized it (on at least two occasions). The forum's original admin, Conor Brian Fitzpatrick, aka "Pompompurin," was arrested in 2023, but since the site was revived and lived on. French authorities confirmed Thursday that they arrested "IntelBroker," a British national called Kai West, 25, earlier this year in February and since charged by U.S. authorities. West was allegedly behind some major data breaches listed on BreachForums, including a telco, an ISP, and a healthcare provider, stealing gobs of data and causing millions in damages, per the U.S. feds. Several other French nationals, who the authorities believe are BreachForums admins, were also arrested as alleged members of the ShinyHunters group, which was responsible for a ton of breaches, including many across France. With West expected to be extradited to the U.S., we'll likely hear a lot more about the hackers and their activities at his trial.
More: Justice Department | DataBreaches.net | TechCrunch | The Record
Iran's cyber forces may retaliate following air strikes on nuclear sites
Washington Post ($): We're back in Iran after what was a frenetic (and kinetic) few days of missiles, air strikes... and then... pretty much nothing. A ceasefire between the U.S., Israel, and Iran is mostly holding — for now — with the entire situation there largely unresolved over whether Iran can in fact build a nuclear weapon at speed. At least in the short term, the focus is now on Iran's cyber capabilities in retaliation, and... even then, there hasn't been so much on that front either. It seems it's possible that Iran's cyber prowess was overstated, or its hacktivist network was hobbled by the recent strikes. Homeland Security still warned of low-level cyberattacks from Iran targeting the U.S., and for companies to be on guard. The takeaway is that we're not out of the woods yet, and while it's so far so quiet on the threat of retaliation, that could change and now would be a better time than any to button up your perimeters.
More: DefenseScoop | NBC News | Associated Press | WSJ ($)
A new CitrixBleed bug is now believed to be exploited in attacks
Bleeping Computer: Flip the "days since a zero-day was found in enterprise tech" back to zero. Security firm ReliaQuest said it's seeing potential exploitation of a new bug in Citrix gear (CVE-2025-5777), dubbed CitrixBleed 2, for its likeness to the original CitrixBleed bug discovered in 2023. The bug, found in NetScaler ADC and Gateway devices, can be abused to allow remote unauthenticated attackers (read: no passwords needed) to steal memory from a vulnerable device, such as credentials and session tokens — you know, all the fun stuff you need to hack into a network. Citrix says, basically, that there's no evidence of exploitation — but do you really want to take the chance? Update your Citrix tech today, don't delay.
More: Citrix | The Register | DoublePulsar ($)
~ ~
THE STUFF YOU MIGHT'VE MISSED
Scale AI exposed sensitive data about its clients in public Google Docs
Business Insider: Scale AI, which relies largely on an army of hundreds of thousands of freelancers and contractors to train its models for its big tech clients, left much of its Google Docs files public and accessible to anyone with the link — including Business Insider reporters. Some of the files were marked "confidential," while others included details about the contractors themselves. Scale AI said that it takes "data security seriously." Ehhhh...
An AI bot now leads the HackerOne bug bounty charts
Bloomberg ($): AI bot Xbow is now the top ranked "hacker" on HackerOne's bug bounty charts. The tool automates the discovery of security flaws, which the company behind it uses to file bugs with HackerOne and claim the bug bounty prizes. I'm an AI skeptic, no secret, and the framing of this story was odd; to call this AI bot a hacker, let alone a good one, does a real disservice to actual hacking. That said, it's good to see AI weeding out real flaws, but right now it's still tackling low-level bugs that need fixing but don't have the human resources allocated to them.
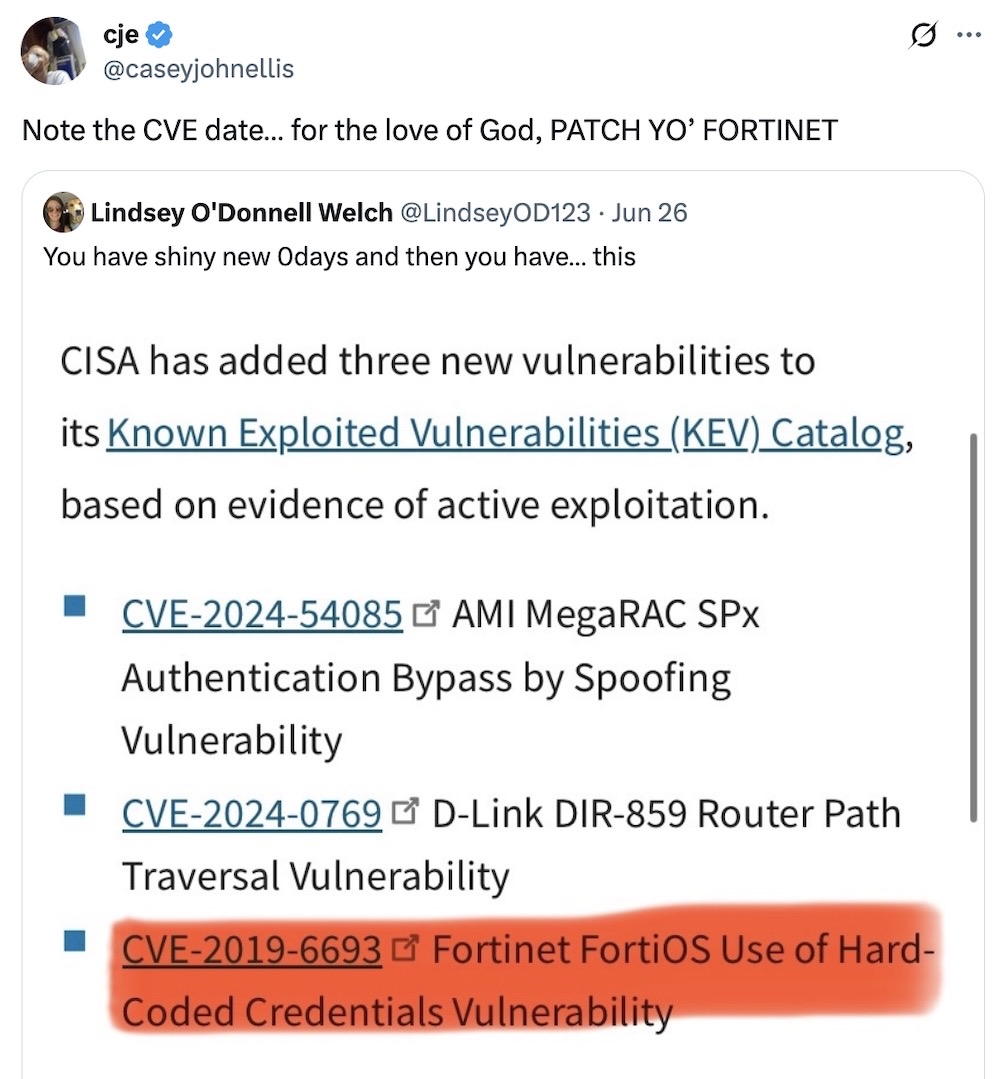
U.S. cyber agency warns of six-year patched bug under attack
CISA: I don't know who needs to hear this but... if you happen to have a Fortinet device on your network that you haven't patched in, oooh, say, six years, you might want to get on that right away. CISA said it has evidence that this Fortinet bug from 2019 is now under attack. The bug involves Fortinet's use of a hardcoded key in some of its products. Listen to @caseyjohnellis!
Microsoft to boot out security firms from the Windows kernel
The Verge: Remember around this time last year when that buggy CrowdStrike update caused a massive Windows outage across the globe? (Time flies... except when the airlines crash.) Microsoft said it will soon boot out cybersecurity firms from accessing the very core of the Windows operating system, aka the kernel, which those firms have long needed to scan the inner workings of your device for malware. It's a long-game process that won't happen overnight, but the cyber firms (and video game makers, which also rely on access to the Windows kernel to detect cheaters) will be part of the ongoing discussion.
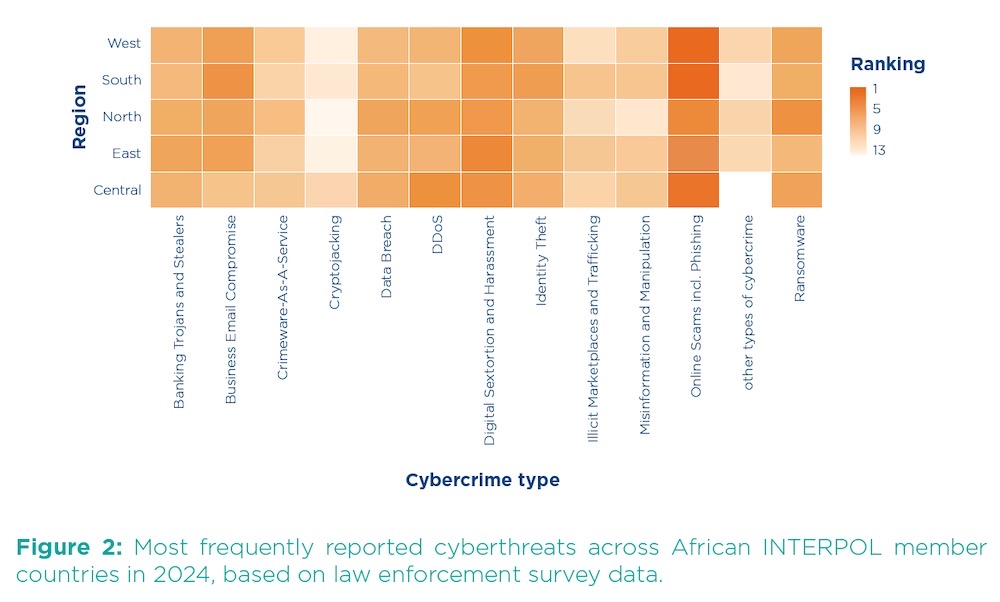
Sharp uptick in cybercrime across Africa
Interpol: Two-thirds of Interpol's African members said cybercrime accounts for about 30% of all crime in Western and Eastern Africa, with scams, ransomware and business email compromise (think breaking into email accounts and rerouting funds) as the top issues. It's worth noting that these cyber issues affect victims globally and are not just a problem in isolation.
Multiple vulnerabilities found in Brother printers
Rapid7: If you have a Brother printer, there's a good chance that it may have a problematic, unfixable bug. The good folks at Rapid7 found eight new flaws affecting more than 700 models of printers from Brother's range (and some others). One of the worst bugs is CVE-2024-51978, effectively an authentication bypass that can turn a device's serial number into the default admin password for the affected printer. Bad news, though — CVE-2024-51978 cannot be fixed in existing models, so you'll have to buy a new printer. Printers can be great for hacking — both as a foothold to the wider network, and for stealing previously printed documents from their memory. SecurityWeek has some yarn on the bugs.
~ ~

~ ~
OTHER NEWSY NUGGETS
Canada warns of Salt Typhoon intrusions: Hot on the heels of last week's disclosure that the Chinese-backed hacking group Salt Typhoon targeted satellite telco Viasat as part of its stealthy espionage campaign snooping on senior American officials, the Canadian government now says its phone networks were compromised by the same hacking group. The China-backed hackers reportedly used a bug in Cisco routers to siphon internal telco network traffic, but that the telco hadn't patched the affected routers at the time. (via Ars Technica, Canadian Government)
SCOTUS OK's porn ID checks: The U.S. Supreme Court has ruled in favor of Texas, allowing state governments to require ID checks before individuals can access adult websites. The decision ultimately means that databases of people's information will be kept and will inevitably become a target for hackers and extortionists. The three Democrat-appointed judges dissented. (via Texas Tribune, @chrisgeidner)
U.K. says ransomware contributed to patient's death: The Qilin ransomware attack on U.K. pathology lab Synnovis in 2024 contributed to the death of a patient, according to the result of an investigation published this week. The long wait for a blood test result was a factor in the death, the NHS hospital trust said. It's a painful and tragic reminder that cyberattacks can and do have real-world consequences. (via Bloomberg ($))
UNFI escapes data breach: United Natural Foods, which was hacked some weeks back and caused widespread food supply chain shortages, said in an 8-K filing that it does not believe it experienced a data breach as part of the cyberattack. Some employees told me that they were concerned their personal information may have been stolen in the attack. UNFI's core systems are now back online. (via U.S. SEC)
Trump's cuts spark cyber disarray: @ericjgeller paints a pretty bleak picture of the U.S. government's cyber power, citing more than a dozen sources. Recent workforce chaos has "seriously weakened" public-private partnerships that protect critical infrastructure, the government has cancelled meetings with infrastructure operators, and coordination projects scrapped. The end result is a "growing national vulnerability to debilitating hacking campaigns," at a time of precarious international stability. (via Cybersecurity Dive)

~ ~
THE HAPPY CORNER
Honestly, we couldn't get to the good news fast enough. Breathe, relax, and soak up the fun stuff. Welcome to the happy corner.
Anyone want a cup of [CLASSIFIED] coffee? I hear the beans are [REDACTED].
Here's a "404 page not found" page that we can all relate to... except if you're under the age of 25, as some of these GIFs won't make any sense to you. (seen via @wendynather).
The EFF has a great guide on covering your OPSEC and identifying what data of yours can get snatched up by the cops. This is a really good at-a-glance look at how these legal processes work, and what you can do to protect your data as best as you can.
File this under harmless hacks: For some reason, apparently you can use a Flipper Zero to give Teslas... wings.

A very happy Pride to everyone. For those who are heading out to marches this weekend, have fun. 🏳️🌈
And finally: here's a bonus cybercat, because we definitely need it.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Arya, who... *taps mic*... [in their best podcasting voice:] will be delivering your Meow FM cyber news digest at the top of the hour, but for now, we'll leave you with some smooth, smooth jazz. Thanks to Joel F. for sending in!

Got a spare minute? Send in a cyber-cat! Drop me an email with a photo and name of your cyber-cat (or non-feline friend!) and they'll be featured in a future newsletter. Sent in a snap before? Updates are very welcome and appreciated!
~ ~
SUGGESTION BOX
Thanks for tuning in and sticking with me for what has been... one busy, slightly crazy, and unpredictable week of cyber. I'll be back next week with what is likely to be a shorter newsletter than usual given the July 4 holiday in the U.S., but don't worry — there's no scrimping on everything that you need to know!
Please do get in touch if you have something or anything you want to share with me or for the newsletter. It's nice to hear from you! In the meantime, I hope you have a great week and I'll catch you next.
Take care,
@zackwhittaker