this week in security — june 30 2024 edition
THIS WEEK, TL;DR
Polyfill.io JavaScript supply chain attack hits 100,000+ sites
Sansec: Some 100,000 websites that rely on JavaScript code hosted by Polyfill.io are affected by a supply chain attack after the China-based company that acquired the domain modified the code to redirect website visitors to malicious and scam sites. Sansec went public with its findings to warn website owners to remove the code. Thankfully, ad blockers like uBlock Origin helped regular users by auto-blocking the malicious code from loading in user browsers. (Another reminder that using an ad-blocker is good for you and your security!) Namecheap nuked the Polyfill.io domain to prevent downstream attacks (since companies like Hulu were still relying on the code). Even the original creator of the Polyfill project sounded the alarm. The new owner of the Polyfill project , however, responded, well, not well, accusing the many, many security researchers who analyzed this supply chain attack of slander. Yes, it's the many, many security experts who are wrong. Mhm-hmm... (that's very obviously sarcasm).
More: Phylum | Cloudflare | Bleeping Computer | Register | Polykill | @thezedwards
TeamViewer says Russia broke into its corporate IT network
The Register: From one major compromise to another — at least, potentially. TeamViewer said this week that Russian-backed hackers, known as APT29, broke into its corporate network, but that there is no evidence (yet) to suggest compromise of its wider production network. APT29 is Russia's SVR, or foreign intelligence, and probably one of the higher-skilled government hacking groups going today. APT29 has already spent months in Microsoft's internal systems, reading executive emails — and emails of some Microsoft customers, so there's fears that APT29's sophistication could allow it to reach further. NCC Group, which first alerted customers, said customers (and consumer users) should remove the app for the time being given the possible threat to customers. This is definitely one to watch given how prevalent TeamViewer's very wide reach of some 2.5 billion endpoints.
More: TeamViewer | NCC Group | Bloomberg ($) | TechCrunch | @lawrenceabrams
DOJ charges Russian civilian with aiding Russian hackers targeting Ukraine
Justice Department: It took U.S. prosecutors some two years to name their suspect, but they got there in the end. Russian national Amin Stigal is accused of helping Russian hackers working for the GRU (formerly KGB, a sort-of sister agency to the SVR) deploy data-destroying "ransomware" (called WhisperGate) on Ukrainian government systems just weeks before the Russian invasion in February 2022. I say "ransomware" in quotes, because although the attack looked like ransomware, the malware destroyed the device's master boot record, effectively irreversibly (and deliberately) scrambling the data, with no way to recover. Stigal set up servers from a U.S.-based company for the GRU hackers to launch their attacks, using cryptocurrency to (badly) cover (but not really) his tracks. U.S. prosecutors got involved because the same hackers allegedly targeted a U.S. federal agency in Maryland, allowing them to step in and name-and-shame the guy, who remains at large in Russia with a $10 million bounty on his head. More background on this GRU group from @gabby_roncone in the tweets.
More: FBI | Washington Post ($) | ABC News
ID verification service for TikTok, X, Uber, exposed driver licenses
404 Media ($): A company that verifies the identities of users of TikTok, Uber and X exposed a set of admin credentials online for more than a year, which if used could have allowed unauthorized access to user-submitted selfies and driver licenses. The company, AU10TIX, took action in the end — but only after some gentle nudging from @josephcox. The credentials were scraped by info-stealing malware on the AU10TIX employee's computer, which is exactly how more than a hundred companies recently had huge reams of data stolen from data giant Snowflake — including Ticketmaster and Santander. For as long as we have passwords, we'll have ways to exploit them.
More: EFF | Cisco Talos | @josephcox
~ ~
THE STUFF YOU MIGHT'VE MISSED
Indonesia president orders audit after ransomware attack
Reuters ($): A recent ransomware attack attributed to Lockbit 3.0 caused huge disruption across Indonesian government services after targeting the government's main datacenter. The government refused to pay the ransom, but the country's president ordered an audit of its datacenters after it was discovered that much of the stolen (and deleted) data wasn't backed up. Whoops.
Yes, you can switch off Apple Intelligence
Daring Fireball: Apple blogger @gruber has some welcome and confirmable news following Apple's big announcement that it's baking in Apple Intelligence (its version of AI) in its latest iPhones... that you will be able to switch it off.
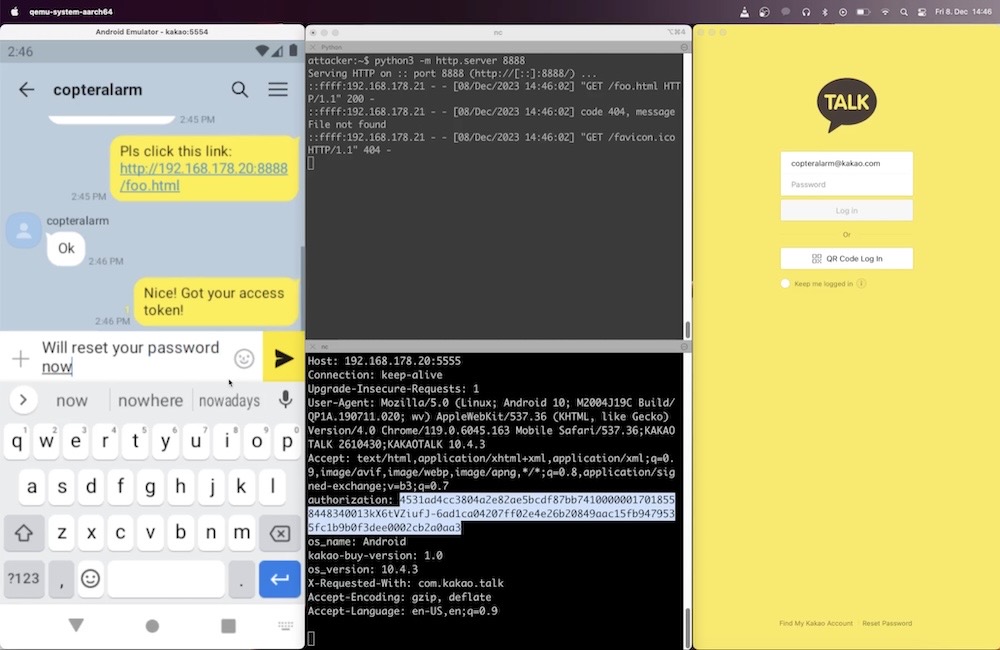
A one-click exploit found in South Korea's top chat app
Dawin Schmidt: Fascinating write-up about how a remote attacker could steal an access token from any user of South Korean messaging app KakaoTalk. The bug, officially CVE-2023-51219 worked by sending a user a malicious link in a chat app, allowing the takeover of any registered user's account. The bug is now fixed.
One million Geisinger patients had data stolen in insider attack
DataBreaches.net: Nuance Communications, a major provider of medical transcription services, says a former Nuance employee accessed and took information on more than one million Geisinger patients back in November 2023 after they were fired. The information varied, but included some personal information. Dissent Doe looks at the court case involving the former employee — and raises questions about whether they had passed a background check prior to their hiring.
Google stops trusting Entrust on HTTPS
Google Security: No trust in Entrust; that's the takeaway from Google's blog this week, as the search giant pulls the plug on supporting Entrust's digital certificates. Citing a series of incidents over the years that Google says forms the basis of why it can no longer trust Entrust, Chrome 127 and later will no longer accept Entrust certificates by default starting around October 31, 2024. Any website or service "protected" (heavy quotes) by an Entrust certificate will flag an error on the user's end. Has anyone told Entrust yet...?
~ ~
OTHER NEWSY NUGGETS
Hands up, it's the Postal Police: U.S. postal inspectors have shared information about thousands of Americans' letters and packages with law enforcement over the years, per the, well, Post. Much of the snooping capacity is found in the mail covers program, which allows the analysis of what's outside a piece of mail, despite efforts to rein in the program. (via Washington Post ($))
MOVEit right outta this server: Progress Software, the maker of the now-infamous MOVEit file transfer software that last year was mass exploited by the Clop ransomware gang, is battling another major flaw in its MOVEit software. This time the bug, known as CVE-2024-5806, allows full authentication bypass on an affected device. watchTowr published a proof-of-concept, and soon after exploitation was reported. (via DarkReading, Tenable)
HubSpot account hacks: Turns out those early rumblings about HubSpot account breaches were true... HubSpot confirmed that it's investigating customer account hacks and working to "remove the unauthorized access" — suggesting there were, in fact, account breaches. HubSpot specializes in customer relationship management and marketing software and is used by practically everyone. (via TechCrunch)
~ ~

~ ~
THE HAPPY CORNER
That was the news... this is the happy corner — and it's flush this week.
First up: OPSEC is important. Especially when you're a cat. That's why the Ukrainian security service blurred the face of this important feline source.

Meanwhile, check out this extremely polite retro error message from the past.
Many congrats to area security boffin @tarah for becoming the latest member of the board of directors for the Electronic Frontier Foundation, an excellent digital defense group that fights for hackers, digital rights, and more. This is excellent news for both the EFF and the wider community it supports, as Tarah brings considerable technical, ethical and academic expertise to help fight for your rights.
Speaking of good people... further congrats to @jerry, the maintainer of Mastodon's favorite infosec space, retired from IBM after on and off 25 years. What a run — and here's to many years of fun (and relaxation) ahead.
And lastly this week: I wanted to say a special thank you to everyone who reads ~this week in security~. Next week will mark the sixth year of running the newsletter, and I can't thank you enough for all of your support, readership, and, of course, cyber-cat submissions. This newsletter started out as a TinyLetter (RIP) in July 2018 and now goes out to close to 13,000 subscribers weekly (and more who read online). It's a real privilege to write for so many people who care so much about security, and hearing from you is one of the highlights of my week. (As an FYI, I'll be taking a week-long hiatus for the July 4 holiday and I'll be back the week after with the usual!)
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cats are (clockwise from top): Cannoli, Pretzel, Toast, and Waffle, aka the best cybersecurity defense team that money (or cat treats) can buy. Who needs expensive AI EDRs when keeping your kitty talent happy is key? You're doing excellent work there, friends. Many thanks to Teresa C.F. for sending in!

Send in your cyber cats! You can drop me an email with a photo of your cyber cat (or your non-feline friend!) with their name and they will be featured in an upcoming newsletter. Have an update? Feel free to send in — updates are always welcome!
~ ~
SUGGESTION BOX
Aaaand that's it for this week... and next! I'll be back after the July 4 holiday refreshed and raring to venture into the depths of the cyber world once more.
Feel free to get in touch any time if you have anything you want to share for the newsletter. And keep your cyber-cats coming, it's so lovely seeing them!
Take care, and back soon,
@zackwhittaker