this week in security — june 4 edition
THIS WEEK, TL;DR
Amazon's Ring snooped on customers, failed to stop hackers, says FTC
Federal Trade Commission: Ring, the Amazon-owned maker of surveillance devices (including video doorbells), will pay $5.8 million to settle accusations that Ring employees and contractors had unrestricted access to customers' unencrypted videos — for years. In some cases, Ring employees were caught snooping on videos of women without their knowledge. (Ring says they've since been fired.) The FTC threw the book at Ring for egregious security failings, having little to know access controls in place, and not implementing security mechanisms that could have blocked hackers from breaking into users' accounts (which Ring was warned about at the time). Ring has since introduced some security measures. The FTC accused Ring of "putting profit over privacy." The Washington Post ($) breaks down the FTC's allegations in more detail. Ring, meanwhile, was unapologetic and spoke largely in present tense — you can guess why.
More: DocumentCloud (complaint) | Reuters ($) | CNBC
Kaspersky says employees targeted with unknown iOS malware
Securelist: Here's an odd one. Kaspersky says dozens of its employees' iPhones were compromised by new unknown malware, which relies on a zero-click (no interaction needed) iMessage attachment to drop the exploit. Little else is known about the malware, but it sounds like suspected spyware; Kaspersky even suggested using Amnesty's own tools to allow anyone else to check for compromise. The apparent hacks, dubbed Operation Triangulation, were discovered by analyzing devices connected to Kaspersky's corporate Wi-Fi network. The activity was blamed on an APT group — likely a government — but Kaspersky did not say who it believes is behind the surveillance. But things got really weird when Russia's FSB claimed — at the same time — that Apple and NSA were working in cahoots to spy on "thousands" of Russian diplomats. The FSB, notably, did not provide proof — and neither did Kaspersky — which apparently had no idea that the Russian feds were coming out with its own statement. But it did prompt Apple to state that it has "never worked with any government to insert a backdoor into any Apple product and never will." All eyes on Kaspersky if it can (or will) actually produce its findings here. Citizen Lab's @billmarczak provides good analysis in a blog post.
More: Ars Technica | Wired ($) | Motherboard
New MOVEit Transfer zero-day mass-exploited in data theft attacks
Bleeping Computer: A real situation is kicking off with the MOVEit Transfer file transfer tool. If you have one on your organization's network (or its SaaS version), take action now. Some patches are available, and remediation steps are here. Attackers are exploiting a new zero-day bug (tracked as CVE-2023-34362) that allows exfiltration of data from these tools. File transfer systems, like MOVEit, are used by organizations to share huge data sets "securely" (those quotes are doing heavy lifting here) over the internet. But look back at the Clop breaches of Accellion and GoAnywhere tools, and you'll see why it's a big deal. With one exploit, extortion groups can tap into a lot of companies' data. Huntress has a blog post with more details (and more in a Reddit thread), as does Mandiant, which attributes this activity to a "newly created threat cluster." New ransomware group inbound?
More: Progress Software | TechCrunch | Reuters ($) | BankInfoSecurity | @GossiTheDog
~ ~
THE STUFF YOU MIGHT'VE MISSED
Millions of PC motherboards were sold with a firmware backdoor
Wired ($): Eclypsium says it's found a hidden mechanism in the firmware of motherboards sold by Taiwanese tech maker Gigabyte, which invisibly initiates an updater program to keep the motherboard updated. But its implementation is buggy and could be used to plant malicious firmware instead. Wired ($) says this vulnerability is "practically doing hackers’ work for them." Hundreds of motherboard models are affected. Gigabyte posted its own disclosure with... well, let's call it a "positive" spin.
Dozens of malicious Chrome extensions found in Chrome web store
Almost Secure: At least 18 malicious Chrome extensions installed more than 55 million times — including "Autoskip for Youtube" and "Soundboost" — were found injecting JavaScript code into every website that a user visited, likely for ads. It's a reminder not to allow untrusted browser extensions that require broad access to your browser's data. Google started removing the extensions this week. The follow-up post-mortem of what went down is also worth the read. (via @campuscodi)
Barracuda zero-day exploited to deliver for months
SecurityWeek: A newly discovered zero-day flaw in Barracuda's email network appliances (tracked as CVE-2023-2868) has been exploited to deploy malware and steal data from organizations since October 2022. Patches are out, and Barracuda explains more — with a timeline — of what went down. Ars Technica also has more.
~ ~
~ ~
OTHER NEWSY NUGGETS
Toyota apologies (again) for another customer data leak: Two weeks after the carmaker apologized for leaving 2.15 million customer records exposed to the internet for a decade, Toyota is back with another apology — this time for exposing data on at least 260,000 customers since 2015. While the bulk of affected customers are located in Japan, Toyota also confirmed customers from "some countries in Asia and Oceania" are also affected — but a spokesperson declined to say more when reached by email. (Disclosure alert: I wrote this one.) (via TechCrunch)
Lab giant Enzo says millions affected by breach: Clinical test data on some 2.5 million people was stolen from New York-based lab diagnostics company Enzo Biochem on April 6. (Yes, you're just hearing about it now.) The incident is believed to be a ransomware attack. The data includes test information, and about 600,000 Social Security numbers were accessed. (via The Record, SEC)
Dental insurer hacked, ransomed: Enzo isn't even the biggest healthcare breach of the week... the Atlanta-based Managed Care of North America (MCNA) Dental says it was hacked in late-February (yes, same comment as above applies), with some 8.9 million patients affected, according to a data breach notice filed with the Maine attorney general's office. That makes MCNA Dental the biggest breach of the year so far — and we're only in June. The LockBit ransomware gang claimed responsibility and is threatening to publish the data. MCNA Dental has a website dedicated to victims of the breach, featuring a stock photo of a patient, smiling, presumably thrilled their data was stolen. (Who thought that was a good idea?) Remember, only two weeks ago, a ransomware gang stole 5.8 million healthcare-related records held by U.S. pharmacy giant PharMerica, which is now relegated to the second-biggest healthcare breach of the year. These numbers are eye watering. (via TechCrunch)
Iran presidential hack 'likely legitimate': A hack and leak operation revealed a huge trove of information related to the offices of Iran's president, with dissidents and experts telling Cyberscoop that the data is likely the real deal. While much of the information is known, it's an embarrassing slap for a country that seems to pride itself on its own hack-and-leak operations. The materials, which include network topologies for sensitive government networks, were published by a group called GhyamSarnegouni (or "Rise to Overthrow"), which emerged in January and claims to hack the Iranian government as a form of protest. (via Cyberscoop)

~ ~
THE HAPPY CORNER
Welcome to the happy corner — and a very happy Pride Month to all! 🌈
A small but notable victory this week: EFF dives into a federal district judge ruling that found warrants are required in order to search a device at the U.S. border. The ruling bucks the trend, since this landmark decision goes against a long-recognized so-called "border search exception," which argues that the border area is not quite American soil and therefore U.S. legal protections don't apply — therefore device searches are permitted without needing probable cause. (In 2022, more than 45,000 devices were searched at the border without a warrant.) It's just one ruling, and doesn't change much for now, but it's a good step in the right direction, given so many folks are turned away from the U.S. because of spurious reasons.
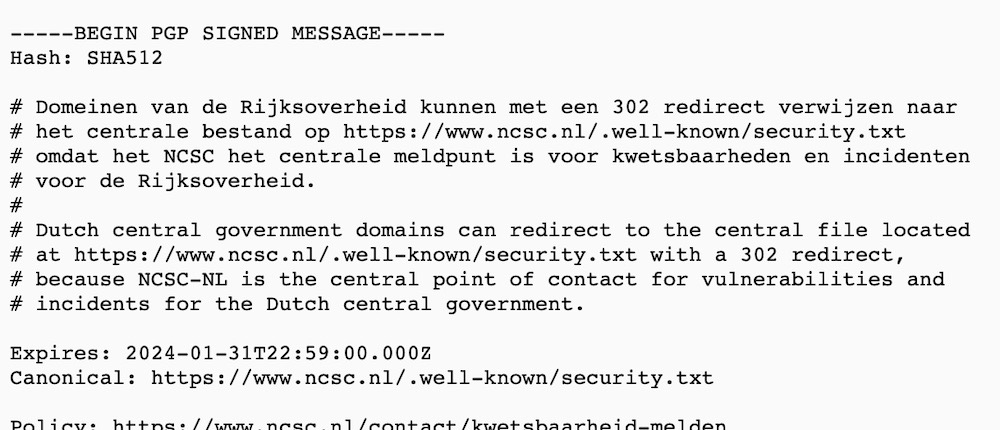
And finally: The Dutch government said this week that security.txt, the proposed standard which allows hackers and researchers to easily find and report security issues, is now mandatory for all Dutch government websites. What a fantastic idea — and popular, too, since some 88,000 Dutch domain names now come with a security.txt as standard. You can see it in action here.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet Lilly, a cyber cat who hails from Little Petra, Jordan. A nice reminder that infosec friends (and cats) can be found in all corners of the world. Thanks, Jason S., for sending in!

Please keep sending in your cyber cats! Send in a photo and their name, and they'll be featured in an upcoming newsletter. (Cyber cats and their non-feline friends are welcome!)
~ ~
SUGGESTION BOX
And that's all for this edition, thanks so much for reading! As always, please drop me a note if you have any feedback. As a reminder, this newsletter also goes out as an RSS feed (available here) in case these emails ever get trapped in the spam filter.
Have a wonderful and peaceful week.
—@zackwhittaker