this week in security — june 9 2024 edition
THIS WEEK, TL;DR
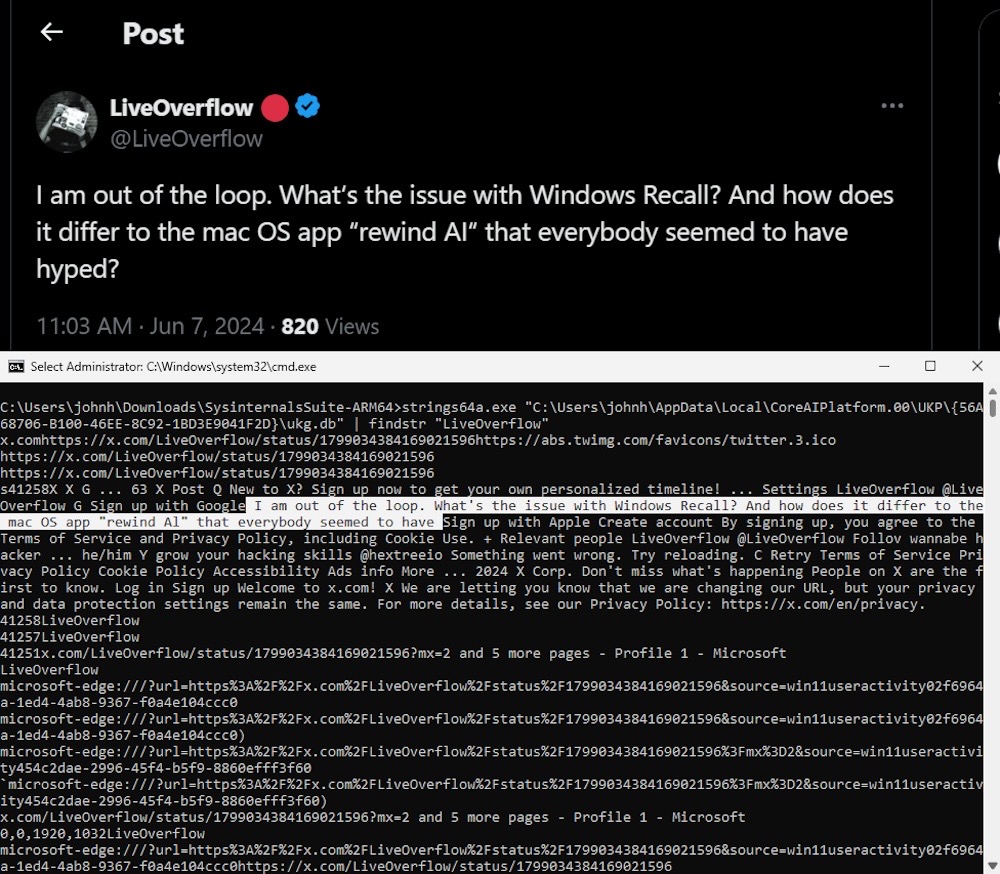
Windows reins in Recall to address security concerns, says it's opt-in
The Verge: Microsoft will make its controversial Recall feature opt-in and beef up its security after researchers found a raft of security flaws in the Windows feature that screenshots everything you do on your computer. It's a move in the right direction (finally) following weeks of extreme side-eye and intense criticism after Recall was likened to spyware for its ability to snapshot everything and make it searchable, security and passwords be damned! The straw that seemed to break Recall's back was that its security features (what little there were) were easily defeated. Recall already saw its first exploit, TotalRecall, which shows how someone with access to a victim's device (like infostealing malware!) can steal sensitive data from Recall. Turns out, speaking up (and loudly) does work, and credit to the folks who've been sounding the alarm on Recall since it was first announced.
More: Windows Experience Blog | Wired ($) | WindowsCentral | DoublePulsar ($)
LendingTree confirms data stolen from Snowflake, as cloud company clams up
TechCrunch: LendingTree is the second company (after Ticketmaster) to confirm it had data stolen from its account on Snowflake. Several other companies are investigating suspected breaches at Snowflake as well, with the potential for more to come. The cloud data giant Snowflake has said little more about its customer data thefts, except to say it's not a breach of its own systems, rather it's the fault of infostealing malware and blamed its customers for not using MFA (which Snowflake is also to blame for not enforcing MFA on its customers' accounts). I found this week that there are hundreds of stolen Snowflake customer credentials online for cybercriminals to use, suggesting the risk to customers could be far greater than the two companies confirming breaches to date. I parsed Snowflake's statement so far and wrote up all the questions I asked the company this week — which customers should also be asking. (Disclosure: I wrote this!) Wired ($) has a really good timeline of events condensing this week's Snowflake-related news.
More: Snowflake | CISA | TechCrunch | Bloomberg ($) | Ars Technica
Google leak reveals thousands of privacy incidents
404 Media ($): A leaked internal Google database that tracks six years of privacy and security incidents shows Google recording childrens' voices, saving license plates from Street View, and many other self-reported incidents. The database itself impacts a small number of users proportionally, but shows the ways that the world's biggest data giant mismanages users' data. In one case, a Google employee "accessed private videos in Nintendo’s YouTube account, and leaked information ahead of Ninendo’s planned announcements," which 404 Media ($) broke out as separate yarn. It comes in the same week that Google's top privacy officer Keith Enright is leaving the company and won't be replaced, a Google spokesperson said.
More: Forbes ($) | Reuters ($)
~ ~
THE STUFF YOU MIGHT'VE MISSED
Hacking millions of modems (and investigating who hacked my modem)
Sam Curry: Curry is back with a new blog investigating a compromise of his home router, and subsequently found a set of vulnerabilities in millions of Cox modems. It's a long read but explains how an external unauthenticated attacker could execute commands on any Cox modem and obtain customers' personal information. "This blog post really aims to highlight vulnerabilities in the layer of trust between the ISP and customer devices," Curry writes.
Another critical bug found in Grandstream's customer control system
Atropos: "Third time's a charm," per @evstykas, who is now onto his third security bug disclosure with networking giant Grandstream of late. According to Stykas, it was possible for an attacker to add themselves as an administrator, which would grant them "complete access to their VoIP infrastructure and all their Wi-Fi."
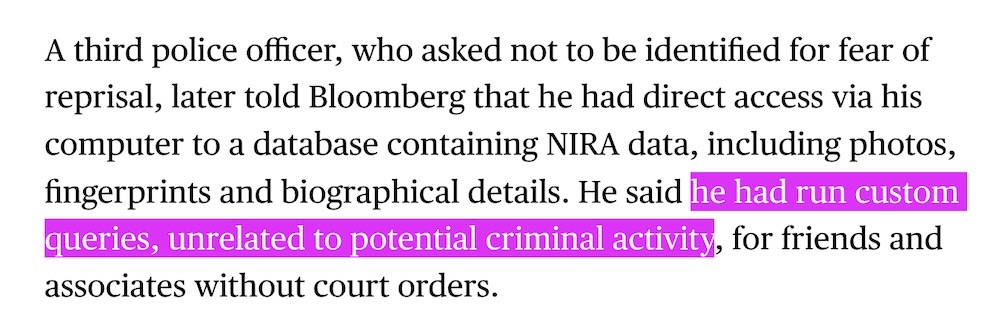
Uganda's national ID system used to target president's critics
Bloomberg ($): An incredible piece by @oliviasolon looking at the dangers and risks of national biometric ID schemes for voting and banking, specifically in Uganda, where the government under President Museveni has used the database to identify and target his opponents. It also reveals abuse of the system by those who use it. In one such case, a targeted human rights activist found his devices stolen from his home in the middle of the night. When he awoke, drowsy from an apparent sedative, he checked the location of one of his devices and found it was located at the headquarters of Uganda's military intelligence agency.
Bangladeshi police accused of selling citizens’ personal information on Telegram
TechCrunch: Two senior police officers in Bangladesh are accused of obtaining the personal information of citizens from classified government databases and selling it to criminals on Telegram, according to a letter written by the country's top intelligence officials, who confirmed the letter in an interview with TechCrunch's @lorenzofb and @ZulkarnainSaer. According to the letter, the police agents "were caught after investigators analyzed logs of the [classified] systems and how often the two accessed it."
~ ~
OTHER NEWSY NUGGETS
London hospitals disrupted by ransomware at Synnovis: A June 3 ransomware attack on a pathology lab called Synnovis is causing massive disruption across the British capital and further afield. Several hospitals in London are redirecting patients, per NHS England. The ransomware gang is believed to be Russian and called Qilin. All this is happening as the U.K. goes to vote in its national elections next month, and cyber doesn't seem to be anywhere on the agenda. (via The Record, BleepingComputer)
TikTok nukes account hijack zero-day: TikTok said a "very limited" number of accounts (which, let's be clear, could be anywhere from a handful to millions) were compromised by a zero-day flaw that was reportedly exploited by a user opening their DMs. Several high-profile accounts, including CNN and celebrities, had their accounts hijacked. (via Forbes ($), BBC)
Apple took three years to fix Screen Time bypass bug: Security researchers reported a bug in Screen Time, the parental controls feature, some three years ago that they say can bypass the content restrictions on a kid's phone by "typing a special string of characters into the Safari browser’s address bar." Apple only fixed the bug after the researchers went to the WSJ. No wonder; it shouldn't take three years to fix a bug like this. (via Wall Street Journal ($))
Hey, it's the FBI, we found your keys: The feds says they have around 7,000 decryption keys obtained from their recent takedown (again) of the prolific ransomware gang LockBit. The gang, which is still active, was hobbled by the feds' seizure of its infrastructure earlier this year. LockBit has been linked to thousands of attacks in recent years. (via Statescoop)
~ ~
THE HAPPY CORNER
And now, it's the happy corner. (Finally.)
For those wondering about their ongoing relationship with Google, now is a better time than any to really consider how to quit the data-hungry giant for good. It's not as easy as just pulling the plug, but Lifehacker has a good look at how that slow, moving-away process could look like. If there's a takeaway here, it's not that Google is inherently bad (although, lately...) but that having all of your eggs data in one big basket — which it can take away from you at any time — probably isn't the safest or smartest way to store your most sensitive data.
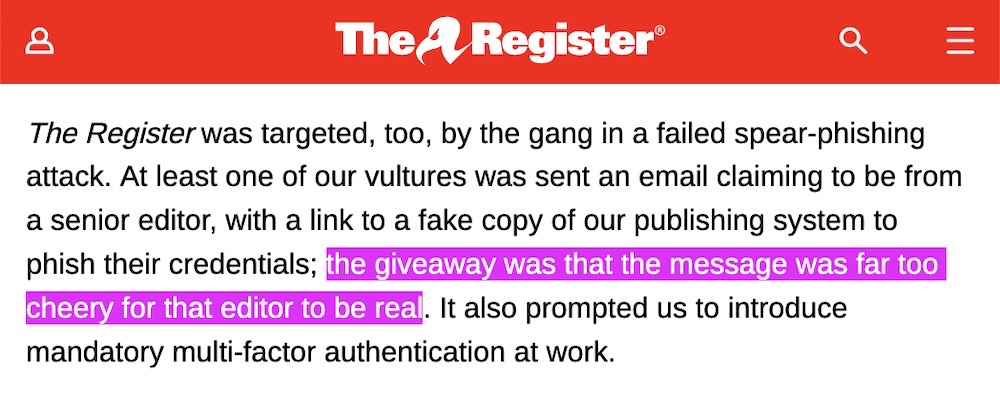
Meanwhile: Buried in this story from The Register is a good reminder to sometimes trust your gut when you get suspiciously upbeat emails from your grumpy coworkers. It reminds me of a news report about how the head of the prestigious St. Andrews University had such disdain for "email guff" (like empty pleasantries) that it actually helped repel a Russian cyberattack, all because the phishing email sent to one of the school's top academics began with the banned phrase, "I hope this finds you well."
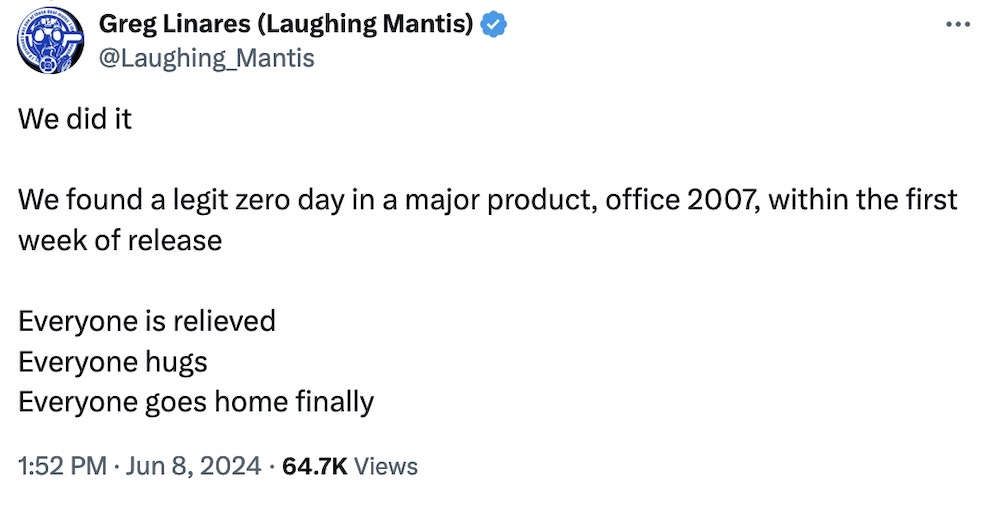
And finally, this week. Grab yourself a beverage and sit down at the bar with this long but excellent tweet-thread by Greg Linares, aka @Laughing_Mantis, about how the very first Microsoft Office 2007 vulnerability was discovered just two days after its release. The storytelling is excellent, not least because Linares frequently self-interrupts with incredibly cheap mojitos.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
~ ~
CYBER CATS & FRIENDS
This week's rare cyber-cat and cyber-dog combo is Baduhenna (left) and Khepri (right), who by all accounts consider each other acceptable roommates. Though, I'm convinced they're actually a secret cybercrime-fighting duo by night. Many thanks to Colin F. for sending in!

Please send in your cyber cats! Drop me a photo of your cyber cat (or non-feline friend!) with their name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
And that's it for this week! Thanks for joining on this muggy morning on the east coast. I'll be back next Sunday with your round-up. Get in touch with anything for the newsletter — news, fun things, and cyber cats (and friends!) are always welcome.
See you next week,
@zackwhittaker