this week in security — march 10 edition
THIS WEEK, TL;DR
Microsoft says Russia SVR spies are still hacking its network
Microsoft: Let's start off strong by checking in on Microsoft after its massive cyberat... oh. Turns out the Russian spies rooting around Microsoft's internal network are still there, re-using secrets that they stole the first time around (back in November but only detected in January). Also known as APT29 (or Midnight Blizzard), the Russian spies also grabbed data from source code repositories and internal systems in what Microsoft described as an "ongoing attack" against its corporate network. Microsoft characterized the attack as a "sustained, significant commitment of the threat actor’s resources, coordination, and focus." Granted, Russia's SVR are one of the top hacking units in the world, but you have to wonder what Microsoft's playing at when it has more money in the bank than some countries — and still can't seem to secure its network or its customers' data.
More: Washington Post ($) | CNN | TechCrunch
Fears grow that millions of patients' data could soon spill online
TechCrunch: Moving on from one set of Russian hackers to another. This time, very much not a state-backed group, but a Russia-based ransomware gang on the digital run. ALPHV, or BlackCat, claimed responsibility for a huge breach of as-yet-unseen millions of patient records from the ongoing Change Healthcare hack, which is still causing healthcare outages across the United States. (Disclosure: I wrote this story!) But after Change allegedly paid a ransom of some $22 million in bitcoin, ALPHV disappeared in an exit scam, much to the chagrin of one of ALPHV's affiliates that claimed to do the actual hacking of Change Healthcare, which cried foul but said they still had terabytes of medical data. (Clearly no honor among thieves.) Now we have a pissed-off ransomware affiliate with gobs of our medical data, and we're still no closer to knowing what data was actually stolen. Unfortunately as with all things in life, only time will tell. Ask yourself who is truly to blame for this cyberattack — and the answer is the mass commoditization of healthcare and corporate greed. America, baby!
More: New York Magazine ($) | Wired ($) | The Record | Ars Technica | DataBreaches.net | Bleeping Computer | @fwosar
Treasury sanctions Intellexa spyware maker bosses
U.S. Treasury: In some rare good news up top, the U.S. Treasury announced first-of-its-kind sanctions against two individuals and five entities associated with Intellexa, a consortium of spyware companies (including Cytrox) that develops the Predator spyware. Tal Dilian and his associate Sara Hamou are now effectively on a blocklist for the foreseeable future making it illegal for U.S. entities (specifically people and businesses) from transacting with them — aka, "oh look, it's the consequences of your actions." In short, the two are cut off from America, which will make their spyware developing activities so much more difficult, rather than just targeting his companies (which could easily rebrand). The new sanctions are interesting because now other spyware makers are feeling the heat and expressing worry that they could be next. (So sanctions do work!) Not only that, Dilian might have to find somewhere else to live after the Maltese government began the process of stripping the spyware boss of his investor's passport.
More: U.S. Treasury | Cyberscoop | @w7voa
~ ~
THE STUFF YOU MIGHT'VE MISSED
Rapid7 says JetBrains fumbled TeamCity bug report
Rapid7: Security researchers at Rapid7 say JetBrains fixed two authentication bypass vulnerabilities (one with a severity score of 9.7 out of 10) in its TeamCity software, but after initially botching its own disclosure. Rapid7 said JetBrains fixed the flaws without notifying Rapid7 that it had done so (rude), then published a blog post without saying anything either (also rude). You can read JetBrains' justification in its own blog.
Flaws in public records tool let anyone nab sensitive data linked to requests
Nextgov: A bug in a public records management system, GovQA, developed by Granicus, used by hundreds of government departments across the U.S. to handle public records requests, had vulnerabilities that allowed anyone to download unsecured files linked to public inquiries. This included sensitive files like IDs, fingerprints, child welfare reports, and medical files. Granicus fixed the bugs after Jason Parker found and reported the bugs. Parker is the same researcher who found multiple bugs in court records systems last year.
Unpatched Sceiner smart lock allow attackers to open locked doors
Security Week: I love a hackable smart lock story (well, so long as it's not a lock in my house): Sceiner is a tech company in China that manufactures smart locks under their brands Kontrol and Elock. But these locks can be cracked because they use a single AES private key for communication and rely on insecure plaintext processing, effectively allowing anyone to pluck the device's door code from over-the-air. There are no fixes for the bugs yet, despite the researchers at Aleph Security notifying the manufacturer in November 2023.

Behind the doors of a Chinese hacking company, I-Soon
Associated Press: A really interesting deep-dive into I-Soon, the Chinese government contractor hit by a recent leak of files detailing in depth the company's surveillance and hacking activities that it carries out on behalf of Beijing. Turns out spyware makers and hackers-for-hire are just as gross as some of the other tech bros out there. The reporting here was done on the ground. More from @dakekang.
Why Signal turned its architecture 'inside out' for its latest privacy feature
TechCrunch: In case you haven't checked out Signal's new privacy feature — usernames (rather than phone numbers) — you should! Signal president @mer__edith chatted with my TechCrunch colleague Devin Coldewey about the security and privacy protections that go into the new usernames feature.
~ ~
OTHER NEWSY NUGGETS
X turned on calling by default — here's how to turn it off: For those still using Twitter X, maybe it's time to make the leap to literally anything else, after the Elon Musk-owned social hellsite switched on video and audio calling by default. Thankfully you can easily switch off the feature (as you should), since it leaks IP addresses when a caller picks up. That is not unusual, but the fact that this feature is opt-out makes the risk of IPs leaking greater. @lorenzofb and I ran what he described as "nerd tests" to see what was happening at the network traffic level, and the X calling feature is... basically a repurposed version of Twitter's long-shutdown Periscope video streaming app. Don't expect any end-to-end encryption here... (via TechCrunch, Tom's Guide, @jsrailton)
CISA says it was hacked: Hackers breached the U.S. cybersecurity agency CISA's network in February by way of targeting vulnerabilities in Ivanti's products, which the agency uses for things. Ivanti makes a range of remote access tools, but has been plagued by a rash of flaws and bugs of late. "This is a reminder that any organization can be affected by a cyber vulnerability and having an incident response plan in place is a necessary component of resilience,” said CISA, which still hasn't said what systems (or data) was affected, if any, but a source said some of the systems housed "critical information" about the interdependence of U.S. infrastructure. (Behold, our string and sticky tape!) (via The Record, @jgreigj)
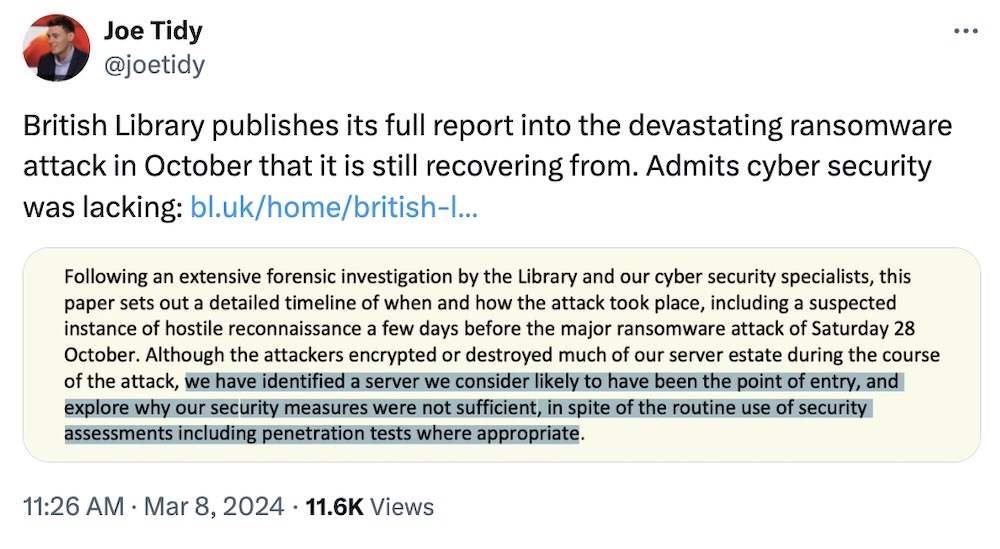
British Library cyber post-mortem: The British Library was hit by a cyberattack in October 2023 that knocked much of the library's systems offline for weeks. The public library finally issued its detailed post-mortem [PDF] exploring what happened. No surprise here: it's cyber posture was lacking and wasn't able to detect the cyberattack fast enough, not before exfiltrating gobs of sensitive data. (via British Library, @gossithedog)
Your Facebook was hacked? Meta doesn't care: A coalition of 41 state attorneys general says Facebook and Instagram parent company Meta is failing to help victims of account hacks (including the Philippines coast guard) — and now they want the tech and advertising giant to take "immediate action." The dozens-of-AGs claim that in some cases Meta profits from these account hacks because threat actors use the hijacked accounts to run ads — which is Meta's bread and butter. You know, aside from selling, sorry — sharing your data and profiting from it. (via Wired ($), New York AG)
Hello, is this Germany? Да: An embarrassing mishap for Germany after Russia's state-run television broadcast leaked audio from a call held by German officials weeks earlier discussing the prospect of sending Taurus missiles to Ukraine. How did the call get leaked? Apparently because the supposed-to-be secure call was held on Webex because a senior official had to join from hotel Wi-Fi. The BBC looks at how the eavesdropping happened... apparently a Russian spy "simply dialled in and sat on the line, without anyone noticing." (via BBC News)
~ ~
THE HAPPY CORNER
Let's see what's in the happy corner this week.
Just a couple of things. First up, Consumer Reports' SecurityPlanner.org got a full redesign. The security planner is a great free resource for helping to stay secure and safe online. Check it out, and share with your friends and family! (via @yaelwrites)
And finally, this week. We all feel like this from time to time.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Calla, who can be seen here serving as the all-important firefurrwall to protect her human against all cyber threats. (Plus, what cute fuzz!) Many thanks to Amy N. for sending in!

Please send in your cyber cats! Drop me a photo of your cyber cat (or non-feline friend!) with their name and they will be featured in an upcoming newsletter!
~ ~

~ ~
SUGGESTION BOX
That's all for this busy week in security (or insecurity, as it often is). Same time, next week? As always you can get in touch with me any time. Don't forget to send in your cyber-cats or their friends!
Take it easy,
@zackwhittaker