this week in security — march 13 edition
THIS WEEK, TL;DR
Chinese spies hacked a livestock app to breach U.S. state networks
Wired ($): China state-backed hackers known as APT41, a group known for espionage but also financial-driven cyberattacks, broke into at least six U.S. state government networks — in two of those cases by using zero-day vulnerability in a web software called USAHERDS, used by 18 states for tracking animal diseases. Other networks were targeted by the Log4j vulnerability, just hours after details of the bug were revealed in December. Mandiant has more in its findings. It's not clear what data, presumably, the hackers were after. Several members of APT41 were indicted by U.S. prosecutors in 2020 after a spate of attacks across Asia and the West, but this most go-around shows clearly that hasn't stopped them. The Register rounds up some of the other threat group activity from the week.
More: Mandiant | CNN | The Register
Mitel devices abused for record-breaking DDoS amplification attack
SecurityWeek: A vulnerability called TP240PhoneHome (tracked as CVE-2022-26143) found in Motel devices, of which tens of thousands are deployed in government and private organizations around the world, can be abused to carry out DDoS attacks with a massive amplification ratio by about 4.2 billion to 1. That means a single spoofed packet can result in massive amounts of traffic to overwhelm systems, knocking them offline. As @campuscodi notes, a single reflected request can crash pretty much any website. Shadowserver, which helped find the bug, said about 2,600 devices need to be patched. The bug has already been abused by advanced attackers for carrying out DDoS attacks, per Cloudflare.
More: @shadowserver | @campuscodi tweets
Linux has been bitten by its most high-severity vulnerability in years
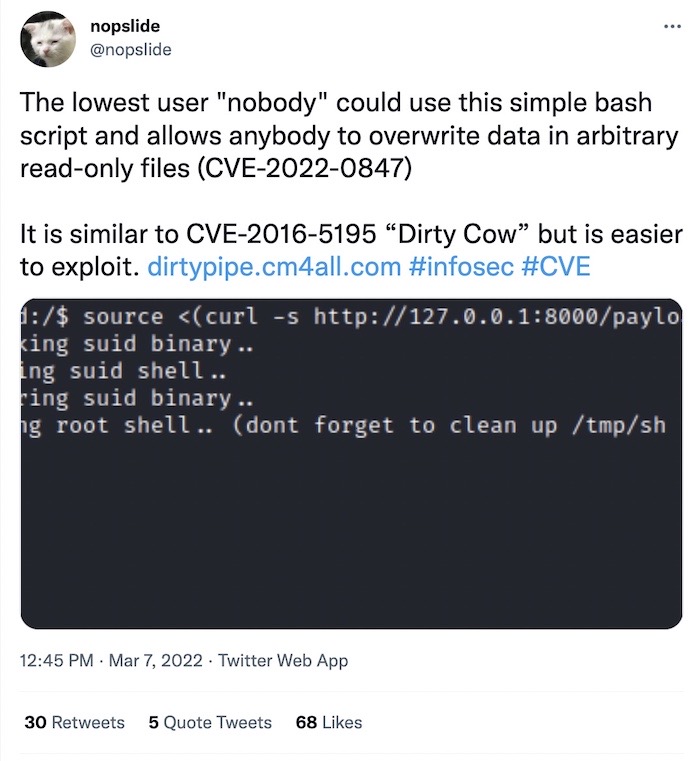
Ars Technica: "Dirty Pipe" is a new vulnerability that has the potential to allow untrusted users to execute code on a vulnerable Linux device or machine, allowing for backdoors or creating unauthorized user accounts. The bug is half-named after Dirty Cow, a Linux flaw that came to light in 2016, which allowed for the privilege escalation and rooting of any Android phone, regardless of its version. Dirty Pipe, meanwhile, is similar in nature but refers to the Linux "pipeline" mechanism for sending data from one process to another. According to @nopslide, Dirty Pipe is easier to exploit than Dirty Cow. Patches have been released. @dangoodin001 explains this well, as usual.
More: Dirty Pipe vulnerability | ZDNet
Google to acquire Mandiant for $5.4 billion
Mandiant: And, this week saw one of Google's biggest acquisitions — almost out of nowhere. Google Cloud will acquire security giant Mandiant for about $5.4 billion, which sits between Google's massive $12 billion acquisition of Motorola (patents, patents, patents!) and Nest Labs at $3.2 billion. Mandiant, the incident response side of things, if you recall, was bundled with FireEye, the product business, until FireEye was spun out and sold off for $1.2 billion. It's going to be a huge deal for Google, allowing it to beef up its cloud security offering, which generates close to $20 billion a year and about 7% of the worldwide cloud market share.
More: Reuters ($) | Ars Technica
Twitter launches Tor onion service making it easier to access in Russia
Motherboard: Twitter has become one of the most significant services to create a Tor onion service to allow users around the world — including countries like Russia where censorship is rife, especially following its invasion of Ukraine — to access the site. Twitter's Tor address can be found on its supported browsers page. @AlecMuffett, who helped Facebook set up its Tor service back in 2014, wrote in a tweet thread and a blog post why a dedicated onion address is better than just browsing over Tor. It comes as big web security companies leave Russia, including Czech-based antivirus company Avast and website certification firm DigiCert. Several other backbone companies have also pulled their business from the country, leaving vast swathes of the Russian population without access to the internet outside of its borders. Some are even taking to "spamming" Russian people to spread information about Russia's military assault on Ukraine.
More: Forbes ($) | BBC News | Alec Muffett | @alecmuffett
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Geofence warrants found unconstitutional in Virginia
NBC News: Authorities in Virginia "violated the Constitution" when they demanded location data from Google to find people who were close to the scene of a 2019 bank robbery, according to a federal judge. That could make the widely used policing tactic, which effectively reverse engineers who were at the scene of a crime based on their Google-collected location data, more difficult for police to use geofence warrants across the state. @elizabeth_joh has more in the tweets.
Inside Conti leaks: The Panama Papers of ransomware
The Record: @NPRDina has a feature (and podcast) out looking at the Conti ransomware leaks, said to be one of the most successful online extortion groups. A couple of weeks ago, Conti declared support for the Russian government's invasion of Ukraine, apparently hitting a nerve with someone on the inside, because they leaked the group's internal Jabber server — with almost two years of their private correspondence. But Conti is already bouncing back, with two new breaches under its belt since the leak.
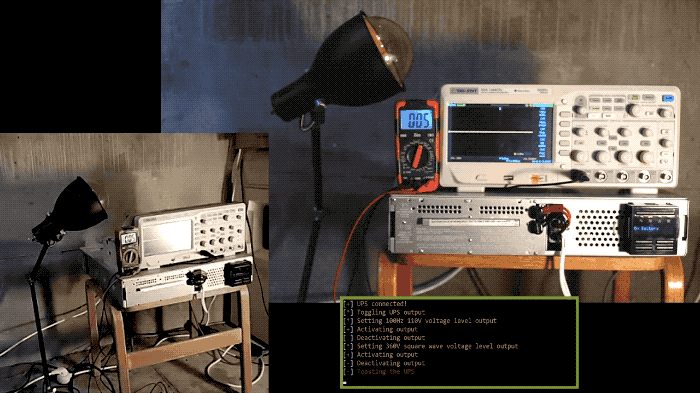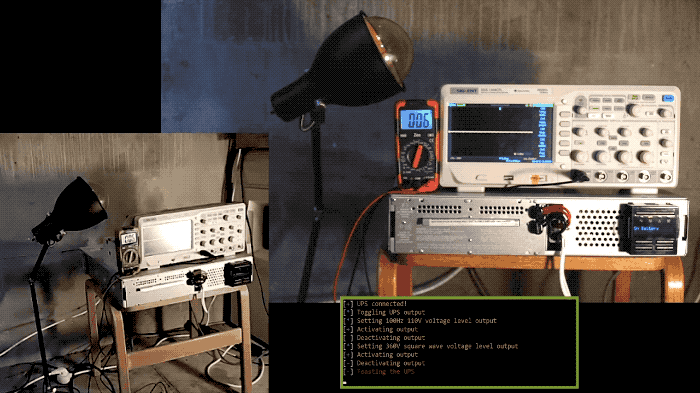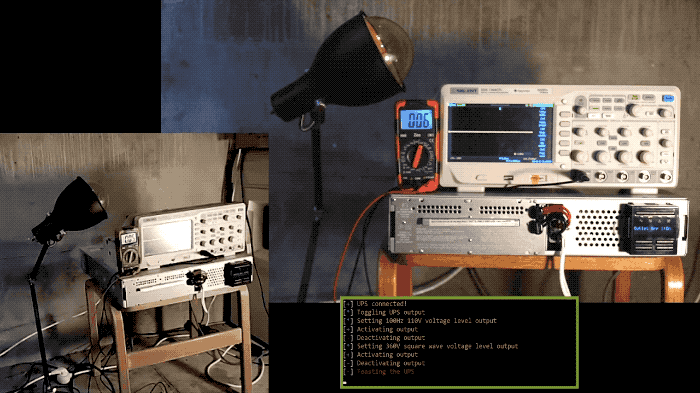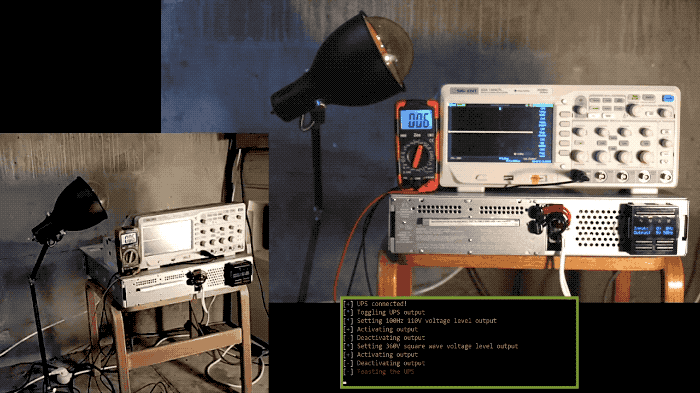
UPS flaws allow for remote code execution and remote fire-based interruptions
ZDNet: After two years of pandemic, a war, and "that whole thing" which we try not to think about, burnout is hitting everyone pretty hard — even inanimate technology. Turns out a trio of vulnerabilities involving a bad implementation of TLS in uninterrupted power devices sold by a Schneider Electric subsidiary could result in remote code execution and literal smoldering of the entire unit. Whoops. Armis explains more about the flaws in a blog post.
NSA probes sabotage of satellite internet during Russian invasion
Reuters ($): Remember last week, we had a story about how satellite Viasat was hacked across Europe, causing widespread outages and communication issues with wind turbines that rely on satellite connectivity. Now there's more: the U.S. National Security Agency is reportedly investigating the attack, which began at the time Russian forces crossed into Ukraine on February 24. Per Reuters, the hack disabled modems that connect with Viasat's European satellite network. Viasat is also a defense contractor for the U.S. and its allies, hence why the NSA is involved.
Inside 'Project Texas,' TikTok's answer To U.S. lawmakers' China fears
BuzzFeed News: TikTok is close to a deal for Oracle to store its U.S. users' information without its China-based parent company ByteDance having access to it, as part of an effort to address U.S. government regulatory concerns about data security and integrity. The agreement would come more than a year after the U.S. told ByteDance to divest TikTok over fears that U.S. user data could be handed to Beijing. It's not known yet if this will appease U.S. regulators. BuzzFeed News has a deeply reported piece on "Project Texas," which aims to decouple TikTok from China and bring U.S. user data back to its territory. More from @ebakerwhite's tweets.
~ ~
OTHER NEWSY NUGGETS
Google blocks China-based phishing campaign targeting U.S. government
Shane Huntley: Google Threat Analysis Group lead Shane Huntley said the company sent out a recent batch of warnings about a China government-backed phishing campaign targeting Gmail users affiliated with the U.S. government. The campaign was blamed on APT31, a group that previously targeted Biden presidential campaign staff in 2020 just before the election. Huntley said TAG doesn't have evidence to suggest this campaign was related to the war in Ukraine.
Secret U.S. surveillance program collects Americans' money-transfer data
The Wall Street Journal ($): Sen. Ron Wyden has revealed that a law-enforcement arm of Homeland Security participated in "a secret bulk surveillance program that collected millions of records about certain money transfers of some Americans without a warrant." The program collected information on domestic and international transfers that exceed $500 to or from several U.S. states. It's not clear how the data is being used (or even if it's legal!) but apparently dates back to at least 2010. A non-profit was set up to host the money-transfer data, which meant authorities could mine the data without needing a court-approved warrant.
Ransomware roundup: REvil, NetWalker ransomware members extradited to U.S.
CSO, Justice Department: The DOJ has extradited an alleged member of the REvil ransomware group, Ukrainian national Yaroslav Vasinskyi, 22, after he was arrested in Poland. He's accused of being "responsible" for the attack on Kaseya, per the DOJ, which left hundreds of its downstream customers also affected by ransomware. He faces up to 115 years in prison if convicted. Meanwhile, a former Canadian government employee was extradited to the U.S. to face charges for his alleged involvement with the NetWalker ransomware group, which resulted in the seizure of $28 million in bitcoin.
Ubisoft reveals "cyber security incident," won't say much
Ubisoft: Gaming giant Ubisoft says it has "experienced a cyber security incident that caused temporary disruption to some of our games, systems, and services" and issued a company-wide password reset, but that there is "no evidence" that any player information was accessed or exposed. (Ubisoft has more than 117 million players worldwide.) But when I asked the company what I thought were basic and reasonable questions like, what was the cyber security incident, or if it had logs or the means to detect improper data access or exfiltration, Ubisoft declined to comment. Classic case of "please disperse" dot gif.
~ ~
THE HAPPY CORNER
As we've covered, things aren't looking great for the millions of Russian people who are caught in the diplomatic and economic fallout following the Russian government's invasion of Ukraine. There are tens of millions of Russians — with no right or ability to speak out — who have effectively been cut off from the outside world and the wider internet because of actions taken by Moscow against its own people, like censorship and disinformation. Many around the world are trying to help those in Russia learn about what's going on about the ongoing Ukraine war by redirecting Russian users to pages with information, rather than blocking them. Jonathan Zdziarski had a good blog post this week, and mentions the UAware project which helps to inform those behind the digital Iron Curtain. "It’s easy to block one website. It’s much harder to keep up with an ever changing sea of websites disseminating information the Russian government doesn’t want their people to see," writes Zdziarski.
I also encourage you to read this blog post by @kiserene, the original creator of Snowflake, about how the anti-censorship technology came to be and how it's helping people today.
And finally, thanks to @SwiftOnSecurity for opening this thread, allowing people to share things that they've learned that they also think might help other people.
To submit good news for the happy corner, reach out: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
Meet Louie, who according to his human is a big a fan of all things cyber — especially sitting on thier CompTIA books. Sure, you could study for your certifications... but this chin won't scritch itself. A big thanks to Kyle C. for the submision!

Keep sending in your cyber cats (and their friends)! Drop your email here with their name and photo, and they will be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's all for this week, a relatively busy one. As always, please drop any feedback you have in the suggestion box or drop me an email.
Same time next week? Have a good one.