this week in security — march 16 2025 edition
THIS WEEK, TL;DR
New CISA director nominated amid layoffs and uncertainty
Cyberscoop: Former DOD, NSC and DOE official Sean Plankey will likely be the next director of the U.S. federal cybersecurity agency CISA, following his nomination by the White House this week. Plankey's nomination goes to the Senate for consideration. His appointment comes at a time of considerable flux at CISA (to say the least) amid even more layoffs, including red teamers. Wired ($) estimates between 300 and 400 staffers have been lost so far, or about 10% of its workforce, as remaining staff at the cyber agency say they are "scared" as cuts make it more difficult to protect the integrity of elections, AI and open-source security. The White House ended up instructing agencies to keep cyber staff, per Reuters ($), as DOGE continues to slim down the size of government at any cost (or consequence). Next up, DOGE has its eyes set on the National Security Agency, per the WSJ ($).
More: Congress.gov | Federal News Network | Reuters ($) | Cyberscoop | StateScoop | LinkedIn | @GossiTheDog
Apple encrypted data row hearing begins in secret
BBC News: Let's jump to the U.K. real quick, where the encryption "debate" (the only debate is with the people trying to break it) is hotting up again. With Apple-backdoor-gate: U.K. Edition, we now have Apple reportedly appealing the U.K. government's secret decision to issue the company with a backdoor order, known as a technical capability notice, so British cyber bobbies can access encrypted Apple customers' data anywhere in the world. Apple pulled its encryption feature, ADP, rather than capitulate (though the debate is still going on that one). Appealing the decision isn't easy and requires going through the U.K. spy court, known as the Investigatory Powers Tribunal, which hears cases in secret. U.S. lawmakers and plenty of others, including media outlets, are calling on the hearing to be public, since it's in the public interest. (I agree, but good luck with that one.)
More: Ron Wyden | Bloomberg ($) | The Guardian
Schools use AI to monitor kids. Reporters found security risks
AP, Seattle Times: Do you know what your kids are doing at school? This AI monitoring software called Gaggle does, and it screams of major security issues. The AP and the Seattle Times inadvertently received(!) close to 3,500 sensitive student documents through a public records request. The data was not redacted (was it ever encrypted?) and contained student names and other sensitive data. The documents were also public, since neither firewalls or passwords protected the files, the reporters said. The heart of the story gets even worse — the level of surveillance that these kids experience (and in some cases have no idea the monitoring was going on) is really jaw-dropping. Many of the issues that the system, called Gaggle, are false positives. Throwing AI at teenagers isn't going to make them safer or protect them. And as the report notes, LGBTQ+ kids and students experiencing gender dysphoria are the most affected. AP has a breakdown in a sidebar piece.
More: Seattle Times | The Verge ($)
~ ~
THE STUFF YOU MIGHT'VE MISSED
North Korea caught planting malicious npm packages and spyware
The Register, TechCrunch: Research via open source security firm Socket shows North Korean hackers managed to sneak backdoor code in at least six packages on npm (an open source package manager), which are designed to steal passwords and crypto, and deploy backdoors. It comes in the same week that North Korean hackers were caught dropping a spyware app in Google Play, per Lookout, in what appears to be a highly targeted espionage campaign. You know the drill by now: North Korea's all about stealing as much crypto as it can to fund its nukes.
ICE surveillance contractor monitoring 200+ popular sites
404 Media ($): A surveillance company called ShadowDragon that contracts with ICE is monitoring more than 200 popular websites — from Apple to Amazon and Meta, Microsoft, and TikTok, according to a leaked list provided to 404 Media. By scraping this data (against many of the firms' terms of service — not that it's stopped surveillance vendors in the past) it allows government analysts to more easily pull public data from a wide array of websites.
Undisclosed hacker behind crypto wallet cracking firm Unciphered revealed
Washington Post ($): (⚠️ CW: Story references sexual violence) An important story in the Post this week revealing that one of the undisclosed founders behind the crypto wallet cracking firm Unciphered is Morgan Marquis-Boire, a hacker who is accused of multiple sexual assaults (and has admitted to rape). His role was masked by a pseudonym, and protected by co-founder Eric Michaud. Neither work at the company any more. Never forget the awful people; but always remember the people who speak up.
Apple will soon support E2EE messaging with Android
GSA Association: Soon, Apple devices will be able to send and receive end-to-end encrypted messages to and from Android devices using the newer RCS messaging standard. No clear date on when the E2EE fun will begin, but nevertheless good news. Ars Technica has a tl;dr.
Who does your CISO report to?
Reddit: An interesting thread on /r/cybersecurity this week pooling answers on who CISOs report to in their corporate hierarchy. It's an interesting look at the senior cyber role; ostensibly C-suite but rarely actually is, and often beset with personal risk and liability. A lot of folks say their CISOs roll up to the technology (CTO) or information heads (CIO), but some report to finance or legal. (Although, I did chuckle — then suddenly not — when I read: "What CISO?")
~ ~
OTHER NEWSY NUGGETS
Mo' medical breaches: More than half a million people had personal (and in some cases medical) data stolen in a series of sizable breaches at healthcare organizations across the United States. SecurityWeek has your list. Apparently the easiest way to avoid having your medical data breached is to have never existed to begin with. (via SecurityWeek)
Knock, knock, you've been hacked by Volt Typhoon: "Go f-yourself," one general manager of a power and water facility in Massachusetts told an FBI agent who called him one Friday night to tell him his facility had been hacked by the China-backed hacking group Volt Typhoon. Well, in fairness, the feds were trying to get the guy to click on a link to diagnose the severity of the issue. The general manager took the claim more seriously when the feds turned up the following Monday. A pretty interesting inside look of how the feds notified private industry of the threat from Volt Typhoon, per a case study from ICS security firm Dragos. (via DarkReading)
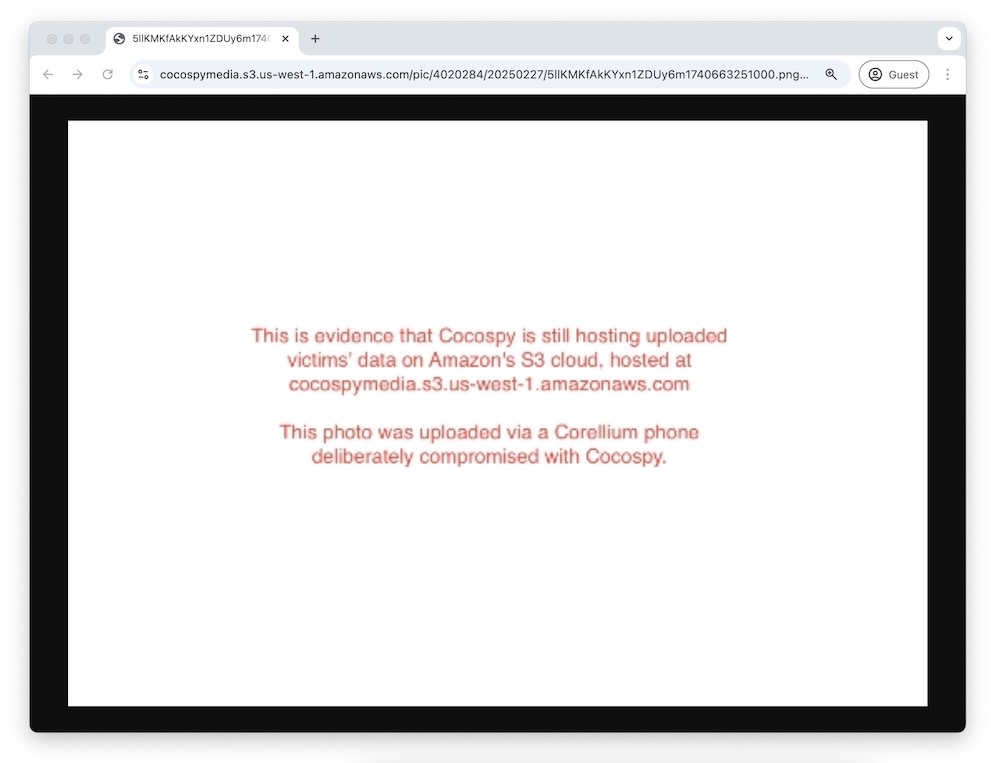
Amazon still hosting spyware data weeks on: Amazon refused to take action against three spyware operations that are hosting gobs of people's phone data stolen via Cocospy, Spyic and Spyzie spyware/stalkerware apps, which have collectively compromised more than 3 million people. TechCrunch (read: me) notified Amazon on February 20 that it was hosting the spyware victims' data and told representatives exactly where to look, but Amazon wouldn't take action because... we didn't fill out a web form? Ultimately, Amazon chose not to act on the information we provided.(Disclosure alert: I wrote this!) (via TechCrunch)
New month, new zero-days: Microsoft is reporting six new zero-days under active attack in this month's Patch Tuesday round-up of security fixes, including three bugs in the NTFS file system. Meanwhile, Apple fixed a fresh zero-day that has reportedly been exploited in an "extremely sophisticated attack" — whatever that means. (via KrebsOnSecurity, TechCrunch)
X DDoS? WTF?: A DDoS attack that briefly knocked the site formerly known as Twiter offline this week was real, data shows, but X owner Elon Musk attributed the blame on IP addresses "originating in the Ukraine area," without providing evidence or specifics. Security experts say that's not how DDoS attacks work. One expert monitoring the situation says botnet traffic in Ukraine's digital space didn't even break the top 20 countries by origin. Thankfully, Wired ($) breaks down what Musk seemingly can't understand. (via Wired ($))
AT&T technician turned whistleblower passes: Mark Klein, who blew the whistle on secret NSA wiretapping in a San Francisco AT&T hub where he worked, has passed on at 79. In 2006, Klein walked into the SF headquarters of the EFF with a question: “Do you folks care about privacy?” Turns out they really, really do. Klein presented them with evidence of wiretapping behind the now-infamous Room 641A, and that set in motion a major milestone in uncovering secret NSA surveillance authorized by laws passed in the wake of the 9/11 attacks in 2001. (via PBS, Washington Post ($))
~ ~
~ ~
THE HAPPY CORNER
Welcome back to the happy corner. It's 20% happier than last week.
Are sharks the squirrels of the sea? I howled with laughter at this post this week.
As usual, Philomena Cunk is asking the right questions:
The EFF continues its daily thread highlighting some of the amazing women in tech, cyber and privacy throughout Women's History Month.
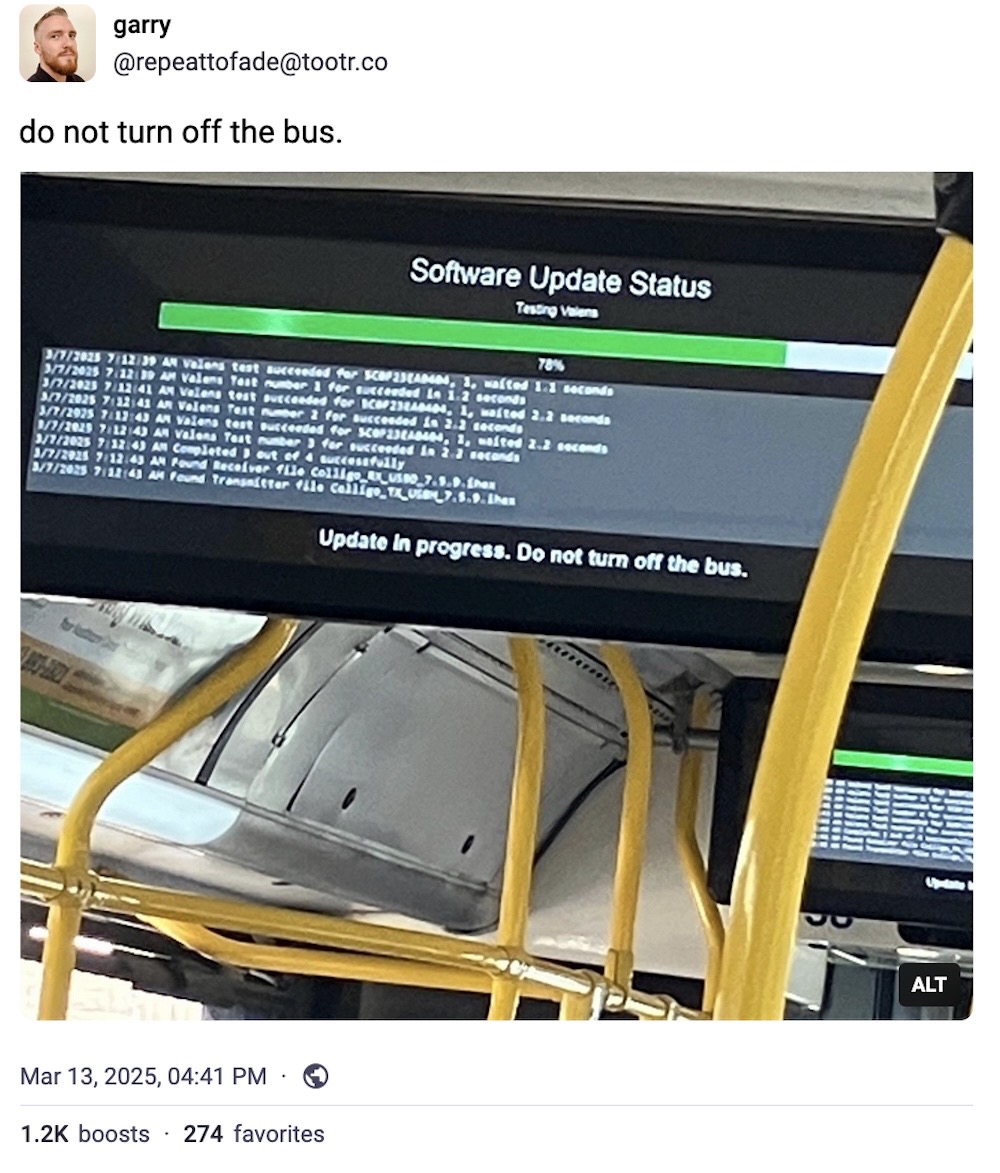
And take a moment of zen while your bus receives a software update. (Wait, can Doom run on this bus?)
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet Shiner, this week's cybercat, who can be seen here studying for his CCNA certification. After all, you can't be an effective white-fur-hat hacker without learning the basics. Thanks so much to Sam M. for sending in!

Keep sending in your cyber-cats! Drop me an email at any time with a photo of your cyber cat (or non-feline friend) along with their name, and they'll be featured in an upcoming newsletter. Please send in updates, too; always love to receive them!
~ ~
SUGGESTION BOX
And that's it for a busy week of ~this week in security~, will you join me next? Expect another firehose of news from the past week.
I love hearing from you so please do get in touch if you have anything to share, especially if it's a cybercat, friend, or update.
Off in search for breakfast,
@zackwhittaker