this week in security — march 17 edition
THIS WEEK, TL;DR
Automakers are sharing consumers' driving behavior with insurance companies
New York Times ($): The data broker industry is thriving, in large thanks to the booming automotive sector. Legendary privacy journalist @kashhill is back with belter reporting: The location data generated from your vehicle is being shared with data brokers, which is used to analyze driving patterns to hike up insurance premiums, where traditionally there was focus on accidents and parking tickets. Worse, plenty of folks are opting-in to these data sharing services because they aren't clearly explained (aka buried in the privacy policy). And Hill, as usual, brings receipts. At least one senator is warning of the potential of "collusion between automakers and insurance companies." Yes, your trackable location is increasingly a security risk. All that data shared about you, where you go and when, potentially who with (they have other people's location data, too!), it's a hot mess for consumer privacy in a land where there are no nationwide data protection laws. The class action lawsuits have already begun. Check out the end of Hill's story for the "news you can use" section.
More: New York Times ($) | The Auto Wire | @wolfiechristl | @wbm312 | @kashhill
U.S. House votes to ban TikTok; Senate is next
EFF: Speaking of nonexistent nationwide data protection laws... enter TikTok. We have to talk about TikTok because everyone's losing their minds again. Depending on who you ask, TikTok is a national security risk — a hypothetical one, since lawmakers have yet to present any evidence of malfeasance — but a hypothetical risk nonetheless. The fears are twofold: TikTok collects a ton of data (a lot of other companies do as well but that doesn't make it right, so we need to fix that whole issue first), and TikTok's China-based parent company ByteDance could, in theory, switch its algorithm at the mercy of the Chinese government to pump an entire generation of kids with pro-China content. At least, that's the fear. That's why many in the U.S. want ByteDance, TikTok's parent company, to divest the video sharing app away from China or ban it in the U.S. completely. There is no simple solution; alas, lawmakers are looking at this issue with too narrow a focus and not thinking about the broader data collection to begin with. Now with the very real prospect that TikTok could (potentially?) become banned in the U.S. if the Senate agrees with the House, the EFF looks at the consequences and fallout of doing so and whether it's even legal.
More: TechCrunch | The Intercept | CNN
Nevada is trying to block end-to-end encryption across the state
Tech Policy Press: From one silly legislative idea to the next, let's check in on Nevada, the new battleground for the future of end-to-end encryption. (Seriously? Are we doing this again?! How many crypto wars can we have?) U.S. state regulators have largely fallen in the "E2EE is good" camp for its ability to hide our sensitive data and messages from everyone (including bad actors, and not just the government or the companies who provide the tech). But Nevada's attorney general is heading in the other direction by pushing to ban E2EE across the state for all children under the guise of protecting them. (No, that doesn't make any sense!) All of this is in response to Meta's decision to roll out E2EE to its widely popular Messenger app. You can read more about the case on Access Now and @kimzetter's Zero Day. The next hearing is set for March 20. Let's hope for the folks in Nevada that the state doesn't get its way. Because if it does, and as the excellent @riana blogs: "What happens in Vegas won't stay in Vegas."
More: Zero Day | Access Now | Mozilla | @riana
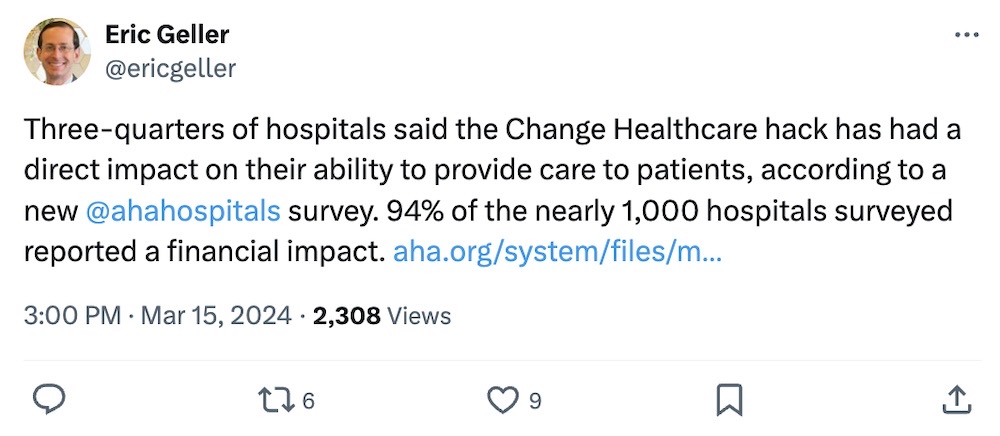
U.S. investigating potential Change Healthcare breach as network recovery drags on
Dept. of Health and Human Services: The U.S. government is investigating the Change Healthcare cyberattack — specifically, and the wording here is important, focusing on "whether a breach of protected health information occurred," and UnitedHealth's compliance with HIPAA rules. All of this to say, the Dept. of Health and Human Services (HHS), which oversees this space, wants to know whether there's been a huge breach of medical and patient data. Don't we all! It's been almost three weeks since the ransomware attack on Change Healthcare began, and much of the U.S. healthcare system has ground to a halt. Per an update on March 13, it sounds like Change finally expelled the hackers (believed to be ALPHV/BlackCat) from its systems. But at least one downstream healthcare provider has run out of money as a result, with more fallout expected to come, all the while patients can't get access to the healthcare and prescriptions they need. We're all just waiting for the next cyber-related 8-K to drop at this point.
More: Change Healthcare | Reuters ($) | Star Tribune | TechCrunch | @brettcallow
~ ~
THE STUFF YOU MIGHT'VE MISSED
Former telecoms manager SIM swapped targets for $1k
Bleeping Computer: A former manager at a U.S. telecoms company pleaded guilty for accepting money to perform unauthorized SIM swaps — where the phone number is transferred to an attacker so they can get access to the victim's online accounts — for $1,000 worth of bitcoin each time. The DOJ says the former telecoms manager faces five years in prison and a fine.
Popular safe locks have secret backdoor codes
404 Media ($): Turns out that some safes aren't actually that safe. At least two of the biggest makers of locks in commercial safes, the U.S.-based S&G and China-based SECURAM, are accused of planting backdoor codes that allow access to the safe's contents. The DOD has also banned these safes for storing classified materials citing these risks... but didn't tell anyone about the backdoor codes.
Onerep CEO founded dozens of people-search firms
KrebsOnSecurity: Throwing more fuel on the fire in hypocrisy corner, now we have the CEO of an ostensible data privacy company linked to running several sketchy people-search services. Onerep claims it will remove your personal information from some 200 people-search sites. But @briankrebs found that Onerep's CEO Dimitri Shelest also registered the same kinds of data hoarding companies that Onerep allegedly helped to protect against.
Some states are fighting to protect voters' data from doxxing, but they're losing
Politico: Voter registration records are public in the United States, thanks largely to a 1993 law that required public disclosure to ensure states maintain an accurate list of registered voters. But given the risks of breaches, leaks, thefts, or companies illegally selling the data, eight states tried to ban the public posting of voter data online while still making the data available on request. A conservative-backed campaign is undoing those efforts, and trying to force every voter's records online, including names, addresses and birthdates. (Thanks, I hate it.) The threats faced to ordinary people are not abstract: @alng found evidence of doxxing campaigns using people's voter registration records against them, and more. This is vital reporting during a critical election year.
~ ~
OTHER NEWSY NUGGETS
LockBit locked up: A dual Canadian-Russian national will spend the next four years in prison after a court convicted him of infecting more than 1,000 victims with the LockBit ransomware and extorting them for tens of millions of dollars. Mikhail Vasiliev, 33, who lived mostly in Canada, pleaded guilty to multiple charges following an October 2022 raid on his house. Authorities offered the convicted LockBit member a key to escape his prison cell, but only in exchange for 20 bitcoin. (I joke; too easy.) (via Ars Technica)
Scotland NHS trust warns of potential data breach: Bad news if you live in Dumfries and Galloway in Scotland, looks like your local health service just got walloped. The local NHS trust was hit by a cyberattack, and warned "there is a risk that hackers have been able to acquire a significant quantity of data." It's unclear of the scope of the cyberattack, but could be messy. Not great for the some ~160,000 or so who live in the Scottish region, especially given the U.K. government in London seems to be completely hashing up its anti-ransomware strategy by burying its head in the sand ostrich-style, according to a senior U.K. lawmaker. (via NHS, BBC News )
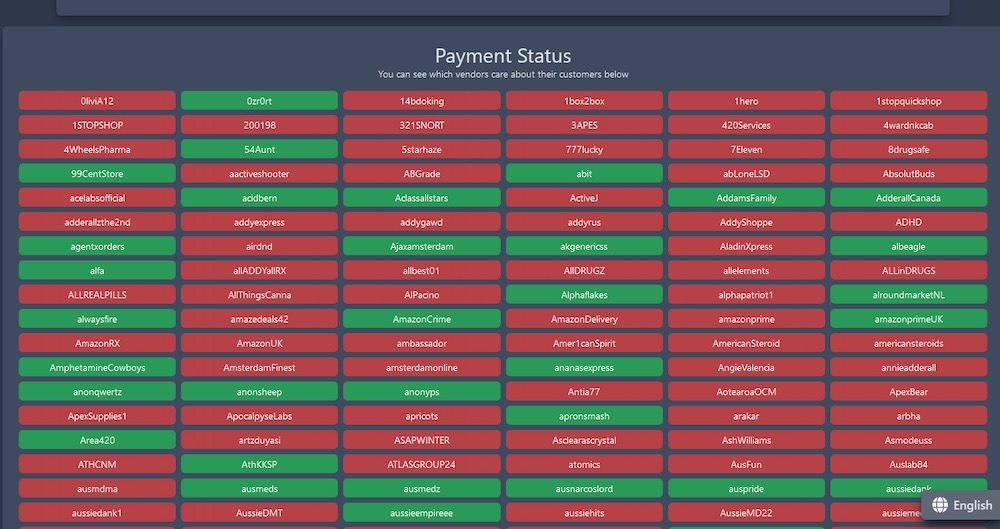
No honor among dark web sellers: In what reads like a page of the ransomware exit scam playbook, the dark web narcotics marketplace Incognito Market is now extorting its vendors and buyers, threatening to publish cryptocurrency transactions and chat records who refuse to pay a fee. The exit scam saw the marketplace admins apparently withholding millions of funds from the platform, and publishing a shame wall-style "payment status" displaying which sellers paid the marketplace's ransom. Wild stuff here. (via KrebsOnSecurity)
What we learned when U.S. spy chiefs testified to Congress: This week, some of the top U.S. spies went to Capitol Hill with their packed lunches and briefing notes, ready to tell the Senate's top intelligence hawks their view of global threats faced by the United States. The hearing was unclassified — so somewhat sanitized — but offered a rare public insight into what was keeping top U.S. intelligence leaders awake at night, including the use of spyware, the inability to counter ransomware, and the U.S. purchasing bulk commercial data. (Disclosure: I wrote this story with my brilliant TC colleague @lorenzofb) More on the hearing from @Olivia_Gazis tweets. (via TechCrunch, @rondeibert)
IMF said 11 email inboxes hacked: The International Monetary Fund, a major funder of the United Nations and other global projects, said 11 of its email inboxes were hacked during a newly disclosed cyberattack in February. The IMF said the inboxes were resecured and there was no evidence of further compromise beyond the inboxes. Since the IMF runs on Microsoft 365 (and Microsoft's had its own email-related cyberattack to deal with), I asked the IMF if the two incidents were linked and... no, apparently not, per an IMF spokesperson. A sounds like an isolated incident at the IMF. (via IMF, @zackwhittaker)
~ ~
THE HAPPY CORNER
At last! It's the happy corner.
Firstly, some friendly security advice. Please, please consider adding a security.txt file to your company or organization's website root directory. It makes it so much easier when friendly hackers (or inquiring reporters!) want to reach out to alert you to security issues. It's always better to hear about it sooner than later, so at least make it easier for folks to contact you. (via @threatresearch)
Next up, congratulations to the handful of cyber reporters sanctioned by Russia this week. Sure, it means those vacation plans are ruined, but at least it's one hell of a badge of honor for doing incredible reporting.
I can't not mention these kick-ass, OG Nazi-hunting centenarians, who celebrated their 100th birthdays together this past month. Gwenfron Picken and Kath Morris served at Bletchley Park during World War II and were part of the codebreaking team that cracked the Nazi's Enigma cipher. Never, ever forget these people, what they stood for, and what they fought against.
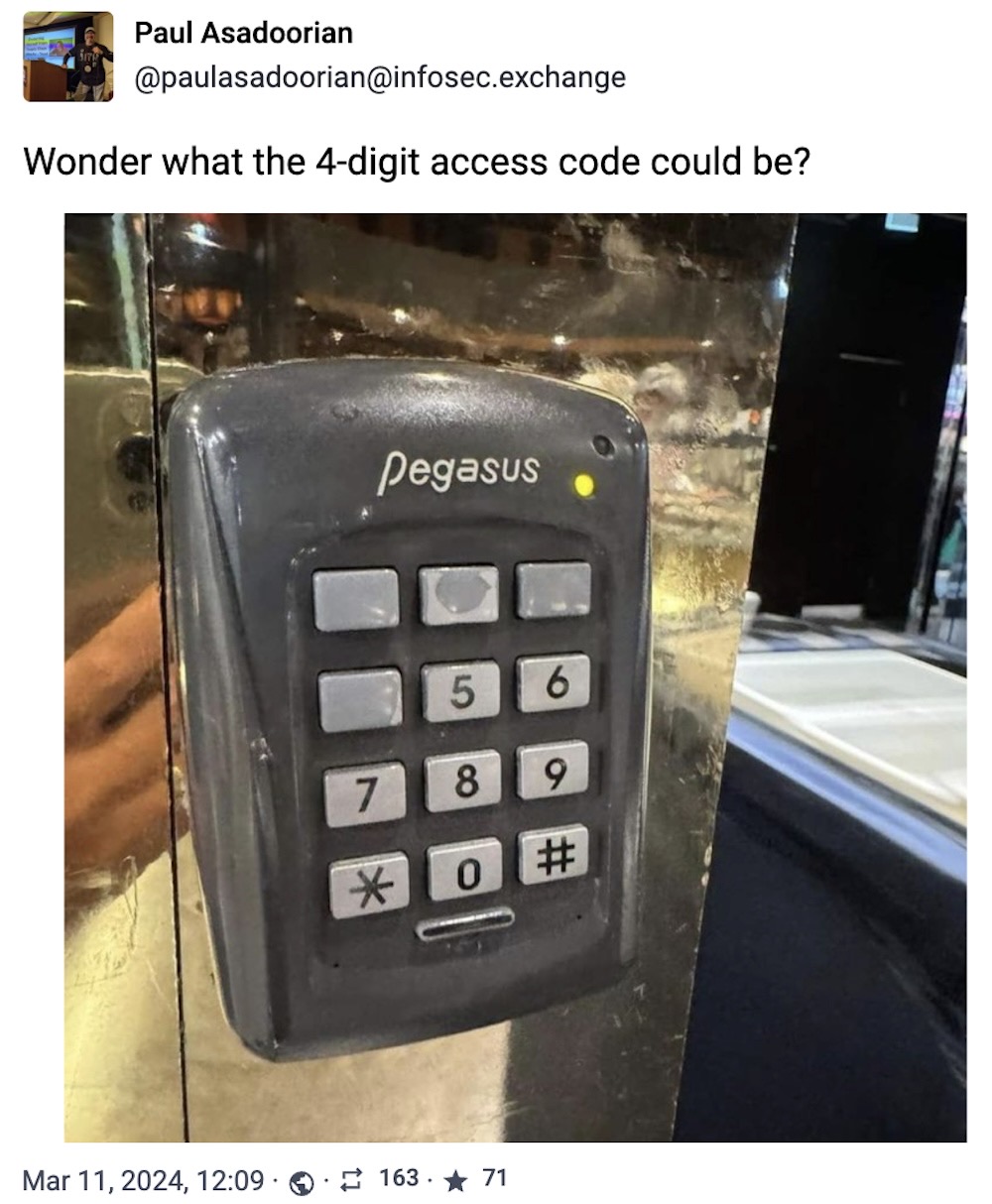
And finally: Can you guess the code? (The joke's on us: it's probably 2-4-3-1.)
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~

~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Deputy Dewey, who c..a.. n.. be.. s... Z z z.. Zzz zz... sleeping...!
Many thanks to Chris B. for sending in!

Please send in your cyber cats! Drop me a photo of your cyber cat (or non-feline friend!) with their name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
Happy to report that this seemed like — dare I say it — a quiet week in security. (D...id we fix all the things?) As always, thanks so much for reading, and if you have any feedback (or cool things you want to share), you can reach out to me any time by email.
Have a great week — catch you next,
@zackwhittaker