this week in security — march 19 edition
~ ~
THIS WEEK, TL;DR
Google warns Android users to take action to prevent exploitation of baseband exploits
Google Project Zero: So, not a great week for Android folks. Google's in-house hacking team (and most of them, from the sounds of it) found 18 vulnerabilities — including four critical bugs that could allow skilled attackers to exploit multiple flaws in Samsung Exynos chips. These baseband chips are effectively cellular modems, which are used in a lot of Android models, including Samsung's own devices but also Vivo handsets and Google's Pixel devices. Google sounded the alarm since these bugs can be exploited over the internet/cellular network using just a person's phone number — and can be abused to snoop on calls, text messages, and cellular data. In all, pretty bad. But without fixes, Google warned users to take action, like switching off VoLTE and Wi-Fi calling (effectively rendering some phones to be, well, no longer phones). While folks seem to be annoyed at the situation (or Google, which seems misplaced), let's not forget that Samsung had 90 days to patch the vulnerabilities but didn't. You can always count on @dangoodin to get to the heart of the problem, which he explains in a Mastodon post.
More: Samsung | Ars Technica | SecurityWeek
Dark web BreachForums operator charged with computer crime
Bloomberg ($): Pompompurin, the infamous person behind the notorious BreachForums website, used to host stolen data on close to a thousand companies and websites, was snagged by feds at his Peekskill, New York home. The forum owner was charged with a single count of computer fraud, specifically conspiracy to commit access device fraud. BreachForums was — for a time, at least — where hackers and sellers would brag (and share) stolen data on companies large and small, and became more active after the 2021 seizure and shutdown of Raid Forums. Look, I'm not saying hoarding a ton of stolen or breached information is going to end well for you, but it seldom does. For those wanting to know more about the backstory, check out Krebs on Security, with a reminder why the FBI might have taken this one to heart.
More: News12 Westchester | Flashpoint

Wave of stealthy China cyberattacks hit U.S. and private networks
Wall Street Journal ($): China-backed hackers are targeting both U.S. government networks and private companies and evading detection, in part by targeting network edge devices — like firewalls — to break in. In some cases the hackers have the ability to gain and maintain persistence, even after software updates. Google's Mandiant unit sounded the alarm, and companies — including Fortinet, which has its own blog post out — have patches. According to Mandiant, Chinese hackers are going after government, telecom and technology sectors as part of this broad information-gathering espionage campaign.
More: Mandiant | Fortinet | Bleeping Computer
This is the new leader of Russia's infamous Sandworm hacking unit
Wired ($): If you, like me, were wondering who runs Russia's Sandworm hacking unit, blamed for destructive cyberattacks and power outages across Ukraine and afar, look no further. @agreenberg has the scoop, thanks to Western intelligence and confirmation from Bellingcat. The former hacker, Evgenii Serebriakov, who was arrested (and released) in the Netherlands in 2018, is now the commander of the unit. Wired has the story of how he got there. Turns out it really is a small world!
Archive: Wired ($) | More: France 24 | @a_greenberg tweets

~ ~
THE STUFF YOU MIGHT'VE MISSED
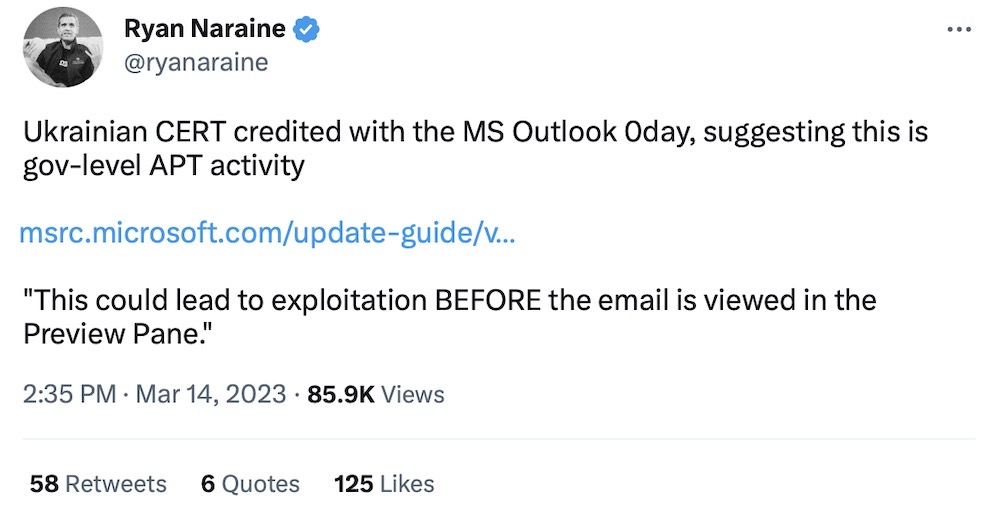
Microsoft fixes Outlook zero-day used by Russian hackers since April 2022
Bleeping Computer: Microsoft has patched an Outlook zero-day vulnerability, tracked as CVE-2023-23397, exploited by APT28 (aka Fancy Bear — yes, that Russia-backed hacking group Fancy Bear). The bug was abused to breach the networks of less than 15 government, military, energy and transportation organizations over a nine-month span. Ukraine's CERT discovered the flaw, and Microsoft has a blog post with more.
Dish customers kept in the dark as ransomware fallout continues
TechCrunch: If you're a Dish customer and still have no idea what's going on at the broadcast and streaming giant after a ransomware attack two weeks ago, well, you probably know as much as Dish employees do, which also isn't much. Dish, with some 10 million customers, is still largely offline after the ransomware attack. Its entire network shifted from in-house to Amazon's AWS, suggesting its entire internal network was hit. Some customers ended up getting cut off because they couldn't pay their bills because its payment systems are still down. Worse, customers have no idea what of their data was stolen in the incident. Given that Dish has yet to appear on Black Basta's website — which sources suggest could be responsible — negotiations may still be under way.
Senate intel chair wants U.S. spies to justify TikTok ban
Wired ($): With all this talk of a TikTok ban (which, by the way, it's probably not going to happen because it would conflict with the First Amendment), Wired's @dellcam asked the one person the one question that so many people seem to have forgotten (including me). Should U.S. spies reveal the reasons for a TikTok ban, given they're basically the ones calling for it? Sen. Mark Warner chairs the Senate Intelligence Committee, which oversees the intelligence community, like the CIA and the FBI, and he wants U.S. spies be held to account for the decisions they influence, "providing not only to Americans but also the world the information it needs to understand how and why this new power is being used" — even though he knows they may not always be at liberty to do so.
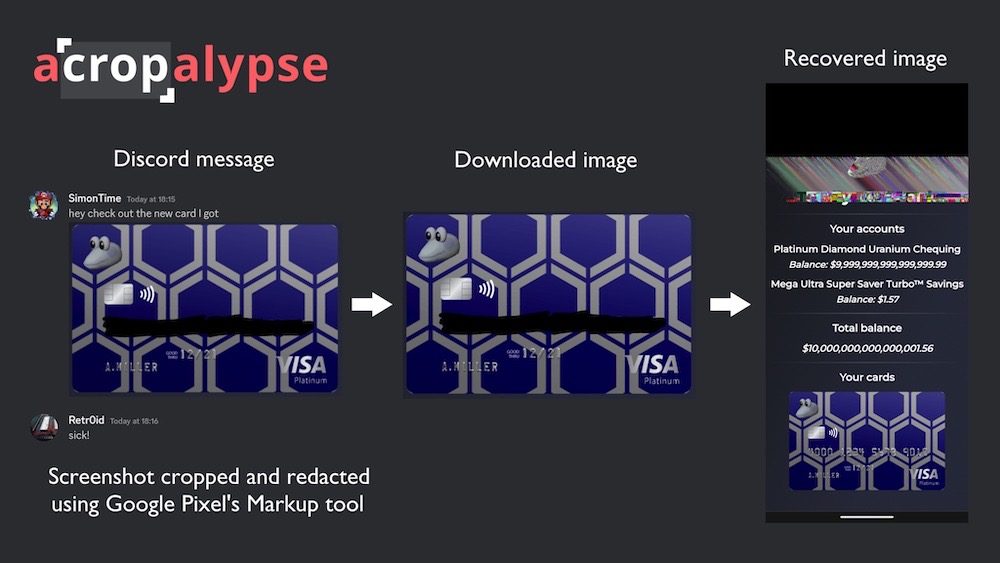
Acropalypse bug exposes Android redacted screenshots
Simon Aarons: This is fascinating. @ItsSimonTime and @David3141593 found a bug in how Google Pixel phones mask or redact information using the in-built screenshot editing tool. There's a full blog post on the details and a demo site where you can try it for yourself. The tl;dr version is: When you crop and save a screenshot, your phone overwrites the image with the new version, but leaves the rest of the original file in its place. Whoops!
~ ~
OTHER NEWSY NUGGETS
Ransomware actors spotted abusing SmartScreen security bypass: Google's government hacker hunters found... something a little different this time. In a blog post this week, Google warned that financially motivated hackers are delivering the Magniber ransomware to victims without any security warnings. It's done this by abusing a now-fixed bug in Microsoft's SmartScreen filter, which typically temporarily blocks files from running that have come from the internet. Per Google, it's witnessed some 100,000 downloads of the malicious ransomware-packed installers since January alone, with most victims in Europe. (via Google's Threat Analysis Group)
CISA to notify unpatched organizations of ransomware risk: Speaking of ransomware, U.S. cybersecurity agency CISA says it'll notify organizations when it detects vulnerabilities that could be exploited by ransomware. It's a new "we'll call you" approach to proactively helping organizations avoid getting hit by ransomware. Organizations can sign-up and enroll if they want. It's a new program authorized under the new CIRCIA 2022 law. It seems like it's working — so far. CISA said the program, dubbed the Ransomware Vulnerability Warning Pilot (or RVWP, an acronym so awkward to say that it almost defeats the point) was already used to notify 93 organizations running Exchange instances vulnerable to ProxyNotShell, which was patched a casual five months ago. (via NextGov, CISA)
Federal agency hacked, thanks to four-year-old bug: OK, so now... speaking of CISA, the agency disclosed this week that another federal civilian branch agency (so — one of these FCEB agencies, basically) failed to fix a critical 9.8 out of 10 vulnerability that was patched... *checks notes*... four years ago. Great! Luckily, CISA found out — but not before it was exploited by an APT group, and apparently also separately by a credit card skimming crew. (via Ars Technica)
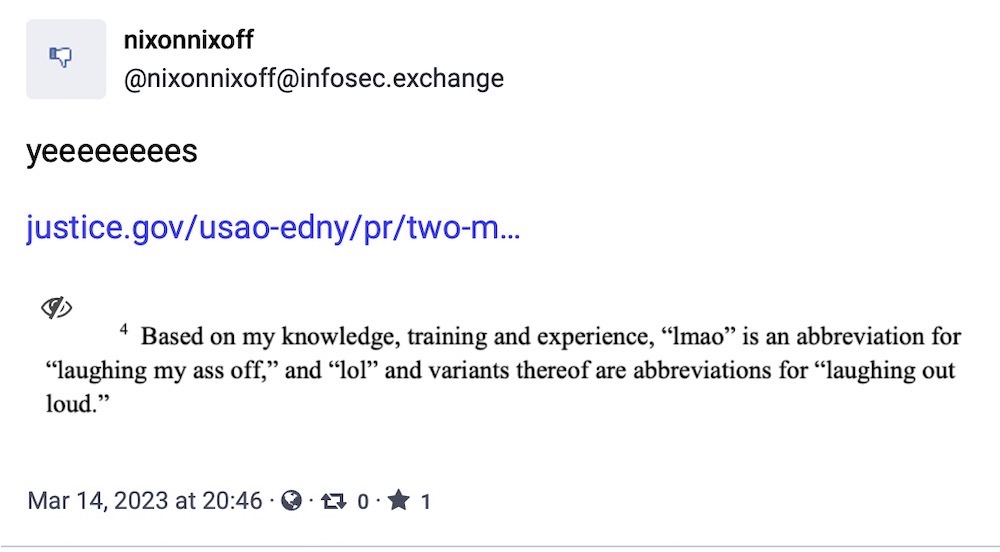
Two men charged with hacking DEA online portal: Two U.S. men have been charged with hacking into a U.S. Drug Enforcement Agency online portal that taps into 16 different federal law enforcement databases. The charges are wild. These two men are accused of breaking into the DEA portal and generating EDRs, or emergency data requests, which are used to pull even more information on individuals from tech companies. Per Motherboard, the hackers could "request information on anyone in the U.S." Or, as the hackers put it, "Nobody is safe." At least we got this incredible footnote from the charge sheet. (via Krebs on Security, Motherboard)
~ ~
THE HAPPY CORNER
A very warm welcome to the happy corner. Don't mind the mess.
First we ask ourselves the all important question. Why did the chicken cross the road?

And is this a buf-fish overflow in the wild?

If you have good news you want to share, get in touch at: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This is Tinkham, this week's strange-looking cat cyber dog! According to her human, she loves identifying risks, especially if it involves finding them in the snow. (My heart is melting, even if the snow isn't.) Many thanks to @moosefish for sending in!

Don't forget to send in your cyber cats! (Non-feline friends are also welcome!) Send in a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
Going once, going twice... and I think that's all for this week. Thanks again for reading! My email is always open for feedback, or feel free to drop a note in the suggestion box.
Be well. Hope you have a great week.
—@zackwhittaker